
Since June 2011 we have seen a substantial decrease in the number of fake antivirus programs. Right now we are observing 10 000 daily attempts to infect users with Trojan-FakeAV; back in June the figures were 50-60,000.
The daily number of attempted infections using Trojan-FakeAV in the past 5 months
Nevertheless, new versions of this type of malware continue to emerge. As a result, the new Trojan-FakeAV.Win32.OpenCloud family has recently been added to the malware hit list.
A screenshot of Trojan-FakeAV.Win32.OpenCloud.h in action
The above screenshot shows how some standard Windows files – including notepad, wmplayer, paint, calc, explorer etc. – were identified as “malicious” by a fake antivirus. In this way the fake antivirus makes itself conspicuous. Interestingly, it also mentions cloud protection, apparently trying to take advantage of a fashionable new concept. If the user is conned into buying this fake software, there’s another scam in store. In the center of the screen the price is quoted at $52.95, but in the small print this creeps up to $72.85 for so-called “lifelong” protection.
Trojan-FakeAV.Win32.OpenCloud.h’s payment window
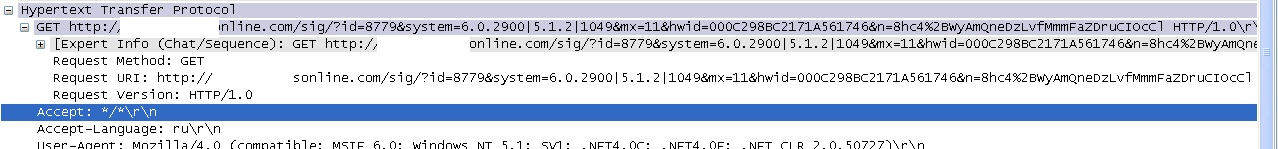
We used WireShark to monitor the payment site for the fake antivirus. The screenshot below demonstrates that data is sent to the URL ******online.com. It includes information about the operating system installed (6.0.2900), the ID (8779) of the partner who will take a cut, and other info.
A screenshot from WireShark – a traffic interception tool
According to the service Whois, the payment site ******online.com was registered in Russia in the name of Denis Verdanskiy on 10 May 2011.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 |
Domain name: *******ONLINE.COM Name Server: dns1.*******online.com 64.191.**.*** Name Server: dns2.*******online.com 64.191.**.*** Creation Date: 2011.10.05 Updated Date: 2011.10.22 Expiration Date: 2012.10.05 Status: DELEGATED Registrant ID: 2AOTCR9-RU Registrant Name: Denis Vernadskiy Registrant Organization: Denis Vernadskiy Registrant Street1: Moscow, B.Polyannaya 23, kv11 Registrant City: Moscov Registrant Postal Code: 109881 Registrant Country: RU |
We discovered an affiliate program called “Money Racing AV” at the IP address specified in the information about the NS server of the host in question. Using a search engine, we found some information about this affiliate program on a Russian underground forum.
An announcement in Russian about the Money Racing AV affiliate program
In this announcement, the cybercriminals invite users to distribute FakeAV for $25 every time the fake antivirus is installed and paid for. The proposed deal is a just over one third of the total price paid by the user. The rest of the money seems to go to the owners of the affiliate program, who provide the fake antivirus, the online payment interface and handle the transaction.
It’s clear that successful cybercrime gangs are still distributing rogue AVs, even though this market is experiencing a sharp decline. So, if you see notifications about “Windows errors” or “system infections”, proceed with caution. Don’t pay for any solution arriving unannounced over the Internet and make sure you install a genuine security product.

























Fake AV business alive and kicking