
![]() Download the full report (PDF)
Download the full report (PDF)
In our last blogpost, Facebook malware: tag me if you can, we revealed a phishing campaign led by Turkish-speaking threat actors who exploited social networks to spread a Trojan that compromises the victim’s machine and captures its entire browser traffic. The report did not address the issue of lateral movement because Kaspersky Lab researchers were still investigating it.
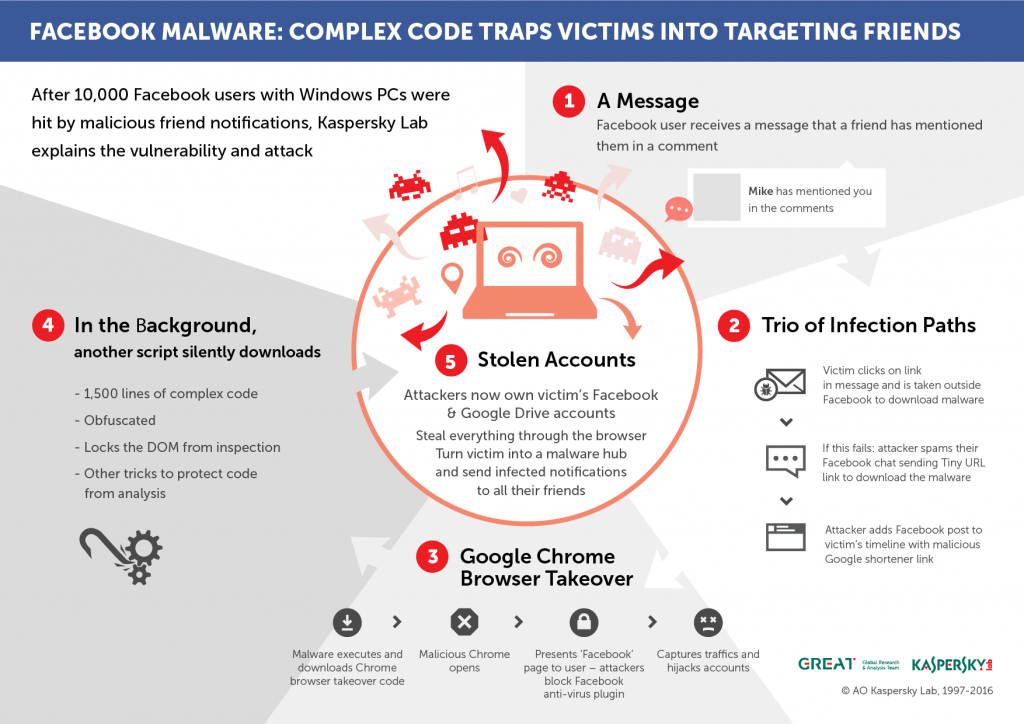
After two weeks of research, Kaspersky Lab researcher Ido Naor, and Dani Goland, the CEO & co-founder of Israel-based company Undot, managed to extract the proverbial needle from a haystack: a Facebook vulnerability that allowed an attacker to replace the comment identifier parameter attached to each web/mobile Facebook comment with an identifier that was reserved for embedded plugins usually located on third-party websites (where they allowed visitors to comment with their Facebook identity).
By tampering with the comment identifier, the attacker was able to create a post on the victim’s Facebook timeline, tag their entire ‘Friends’ list in a comment to the post (which will store the array of tagged users in Facebook servers), and then replace the comment identifier with a third-party Facebook comments plugin identifier (controlled by the attacker) and delete the tagging. Since the notifications were already stored and “shipped” to the tagged friends, the act of replacing the web comment identifier with a Facebook plugin comment identifier resulted in the redirection of the tagged user outside of the Facebook platform, to a malicious link which instantly downloaded a Windows JSE file. And where would be the best place to store such file if not in the victim’s cloud storage – Google Docs / Dropbox? If those were not present, the malware had a fail-safe mechanism that sent a tinyurl link as a Facebook message to the victim’s entire Facebook friends list and, just in case the message wasn’t delivered, a malicious Google short link was posted on the victim’s timeline along with a convincing message that contained pictures of the victim’s friends.
Facebook has now fixed the issue and blocked the vulnerability that was a key feature in spreading the malware.
It is worth mentioning that the code responsible for the vulnerability is filled with strings and variable names in the Spanish language, suggesting that whoever wrote it is not necessarily part of the Turkish-speaking group.
Looking at the complexity of the code puts it in an even more questionable position regarding the author’s identity. In addition, the file is completely dynamic and adaptive to every action made by an analyst, preventing them from fully inspecting the code.
Facebook malware – the missing piece




















Patrick
No, this has not been fixed. I have a few groups in FB and I am now recieving their entire friends list to be added to those groups and their friends list. From time to time one or more will get access without approvals. It then seems to attack those friends computers.
I am a novice and could really use some help.
Sydney Haskell
I am blocked from posting or seeing my cover photo on Facebook as of today. I did refriend two people that I was already friends with not realizing this could be a hack. This is on my tablet which is a Samsung Galaxy S5. I am afraid to login in on this pc to Facebook. What do I do?
bobby Ingram
I believe this article should go viral.