Venezuela is a country facing an uncertain moment in its history. Reports suggests it is in significant need of humanitarian aid.
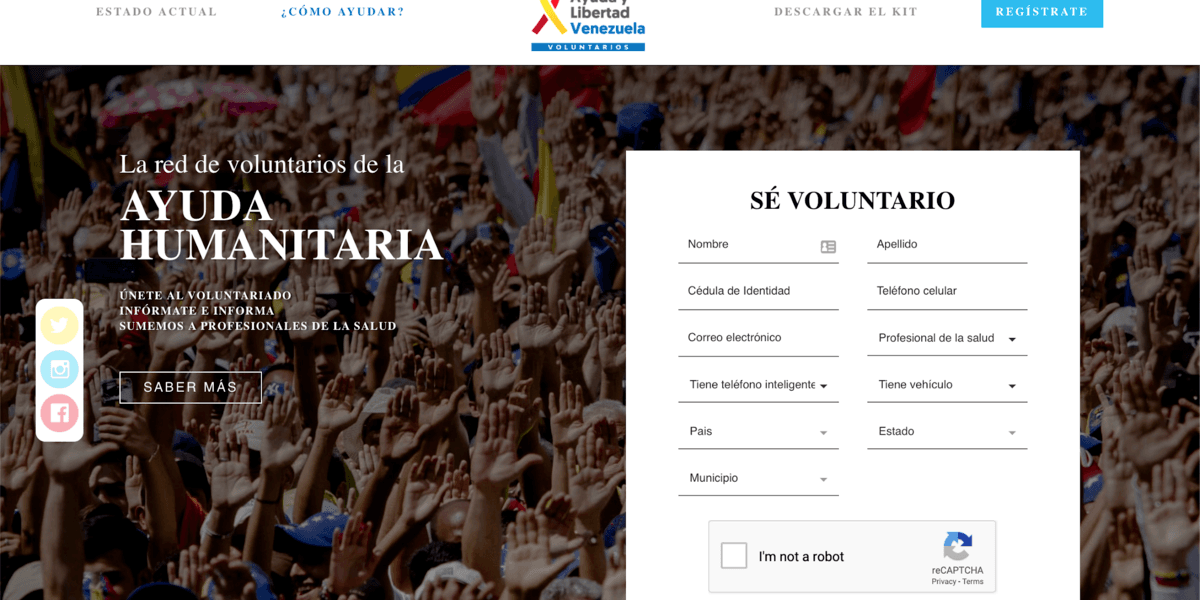
On February 10th, Mr. Juan Guaidó made a public call asking for volunteers to join a new movement called “Voluntarios por Venezuela” (Volunteers for Venezuela). According to the media, it already numbers thousands of volunteers, willing to help international organizations to deliver humanitarian aid to the country. How does it work? Volunteers sign up and then receive instructions about how to help. The original website asks volunteers to provide their full name, personal ID, cell phone number, and whether they have a medical degree, a car, or a smartphone, and also the location of where they live:
This website appeared online on February 6th. Only a few days later, on February 11th, the day after the public announcement of the initiative, another almost identical website appeared with a very similar domain name and structure.
In fact, the false website is a mirror image of the original website, voluntariosxvenezuela.com
Both the original and the false website use SSL from Let’s Encrypt. The differences are as follows:
| Original voluntariosxvenezuela.com website | Deception website |
| First day on the Internet, Feb 6th | First day on the Internet, Feb 11th |
| Whois information:
Registered on the name of Sigerist Rodriguez on Feb 4, 2019 |
Whois information:
Registered via GoDaddy using Privacy Protection feature on Feb 11, 2019 |
| Hosted on Amazon Web Services | Hosted first on GoDaddy and then on DigitalOcean |
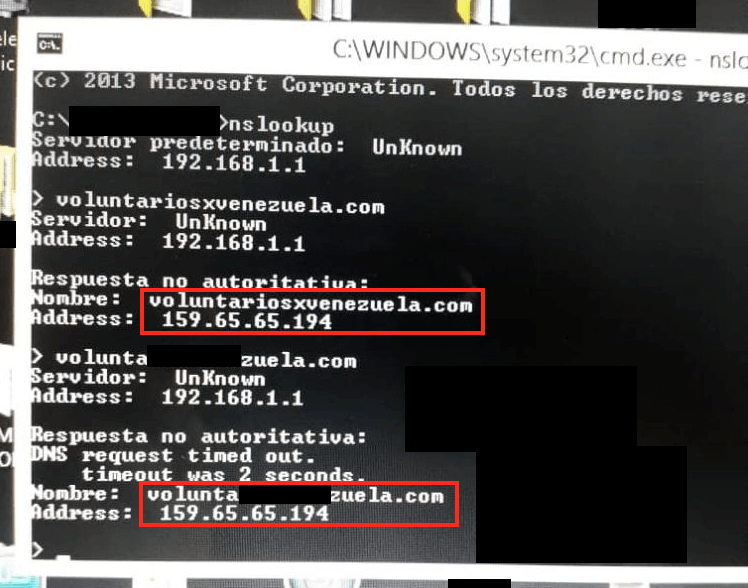
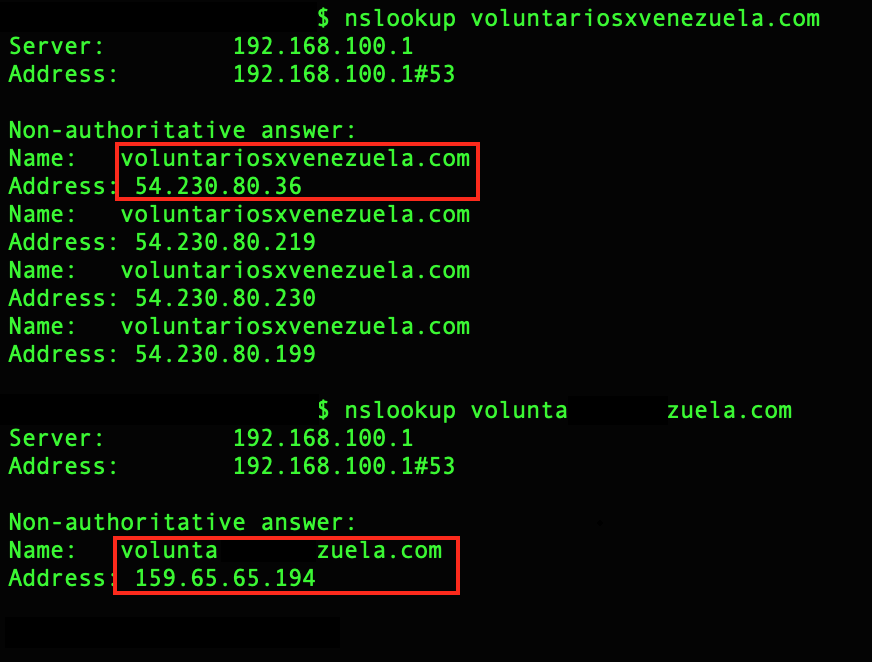
Now, the scariest part is that these two different domains with different owners are resolved within Venezuela to the same IP address, which belongs to the fake domain owner:
That means it does not matter if a volunteer opens a legitimate domain name or a fake one, in the end will introduce their personal information into a fake website.
Both domains if resolved outside Venezuela present different results:
Kaspersky Lab blocks the fake domain as phishing.
In this scenario, where the DNS servers are manipulated, it’s strongly recommended to use public DNS servers such as Google DNS servers (8.8.8.8 and 8.8.4.4) or CloudFlare and APNIC DNS servers (1.1.1.1 and 1.0.0.1). It’s also recommended to use VPN connections without a 3rd party DNS.
DNS Manipulation in Venezuela in regards to the Humanitarian Aid Campaign






















John Todd
Using a public DNS service like Quad9 (9.9.9.9) which supports TLS, DOH, and DNSCrypt encryption methods is also suggested to prevent manipulation of DNS data in flight.
Pseudorogue
It would be great if you guys would say what exactly are the dns servers that are making this modification. Any particular Venezuelan ISP?
anon
cantv, their dns servers are 200.44.32.12 and 200.44.32.13