
Cybercriminals cash out money using stolen digital identities
Carding exists for over 20 years. And it is not dead yet. It is alive, and even more – it is being actively developed by cybercriminals. The “good” old method of entering stolen credit card information into online store forms to buy goods and services or using online payment system accounts for the same purpose still works like a charm. Of course, the process has become more sophisticated, and it is certainly not so easy to do as it used to be 10 years ago, but unfortunately it is still possible.
The modern financial cyberfrauds, sophisticated targeted attacks on banks like Carbanak and Silence, hundreds of families of banking Trojans, etc. It had all started with carding forums many years ago. Carding is the cradle of modern financial cybercrime. As before, bank cards, payment systems and online banking frauds are the most valuable criminal sources of wealth.
A study by Juniper Research estimates that losses from online payment frauds will reach 43 billion USD by 2023, up from 22 billion USD in 2018, making anti-fraud and cybersecurity measures a top concern for the industry. And this is not surprising – every day cybercriminals develop new methods and tools to bypass anti-fraud protection systems, they develop malware to help them in their activities, create services and stores, discuss ways to defeat protection mechanisms on Darknet forums and channels. From the famous Cardingplanet forum to Darknet stolen card stores – financial cybercrime schemes were not dead at all during all these years. They have evolved and become more dangerous than ever.
Digital fingerprint protection
How do modern anti-fraud systems protect users from online fraud? They employ various models and combinations of multiple technical and analytical methods. But in simple terms, any anti-fraud system must identify a fraudster and block his attempt to accomplish an illegal transaction involving a bank card or payment system account. To identify fraudsters and separate them from legitimate buyers the anti-fraud system uses various mechanisms designed to verify the user’s digital identity mask, and if it knows this mask to be legitimate or the mask is a new and unique one, it will not throw the “red flag”. As a result, the user behind the mask is recognized to be a legitimate one, and his query, such as an attempt to make a purchase using the provided bank card details, will be approved. If the user’s digital identity appears suspicious, the transaction will be canceled or put on hold for an additional manual check. Additional authentication typically includes a request to provide extended information like bank card expiry date or CVV number, or possibly also a verification call from the online store or payment system operator for voice verification.
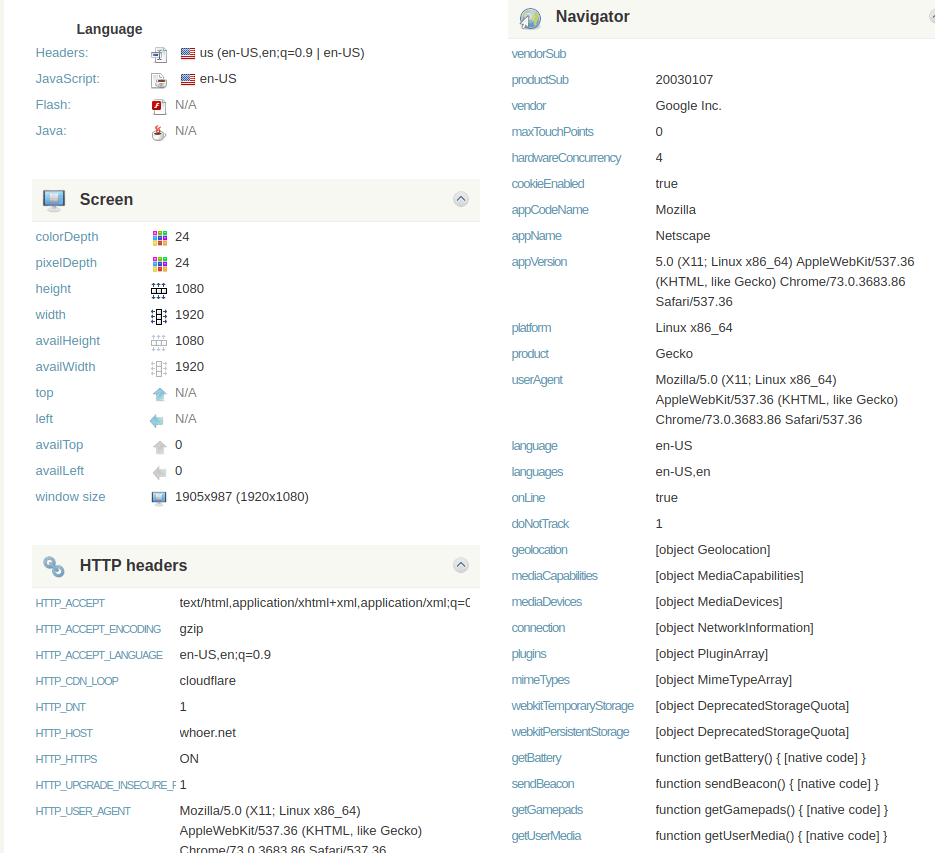
As such, the user’s digital identity is a digital fingerprint – a combination of system attributes that are unique to each device and personal behavioral attributes of the user himself. The first part, the device fingerprint, includes:
- IP address (external and local)
- Screen information (screen resolution, window size)
- Firmware version
- Operating system version
- Browser plugins installed
- Timezone
- Device ID
- Battery information
- Audio system fingerprint
- GPU info
- WebRTC IPs
- TCP/IP fingerprint
- Passive SSL/TLS analysis
- Cookies
- and many more
The device may have over 100 attributes used for browsing.
The second part of the digital identity is the behavioral analysis. Modern anti-fraud solutions analyze the user’s social network accounts (third-party cookies check) and various aspects of his/her behavior, including:
- Time spent at online store website
- Clicks on website location
- Interest-related behavior (items of interest, typical amount of money spent, digital or real merchandise, etc.)
- Mouse/touchscreen behavior
- System configuration changes
The anti-fraud system may “red flag” various tricks, but the main idea is to make sure that the user’s collected digital identity had been used for transactions before, such transactions had been legitimate, or that the digital fingerprint is completely unique and used for the first time. This is why, if a cybercriminal uses the same machine for multiple attempts to buy from the same online shore using different bank cards details or stolen payment system login/password pairs, such illegal transactions will be declined. Anti-fraud systems can check the user’s collected fingerprint against the local database of fraudster device fingerprint patterns and, if any of them should match the one being used for the online purchase attempt, the transaction will be immediately blocked.
Fingerprint example
But the bad guys are always looking for ways to defeat the anti-fraud safeguards. They do in-depth research work to find out how anti-fraud systems work, they analyze browser traffic using different local analysis proxy tools to understand protection system scripts and queries. They study the information gathered from devices to create unique digital fingerprints of its users.
The next thing they do is try to substitute the system’s real fingerprint with the fake one. They try to manipulate queries and supply unique values in response to every query from the anti-fraud mechanism. Or, as a more advanced alternative, they substitute the requested values with the already existing ones – stolen from someone else’s PC.
Genesis Store
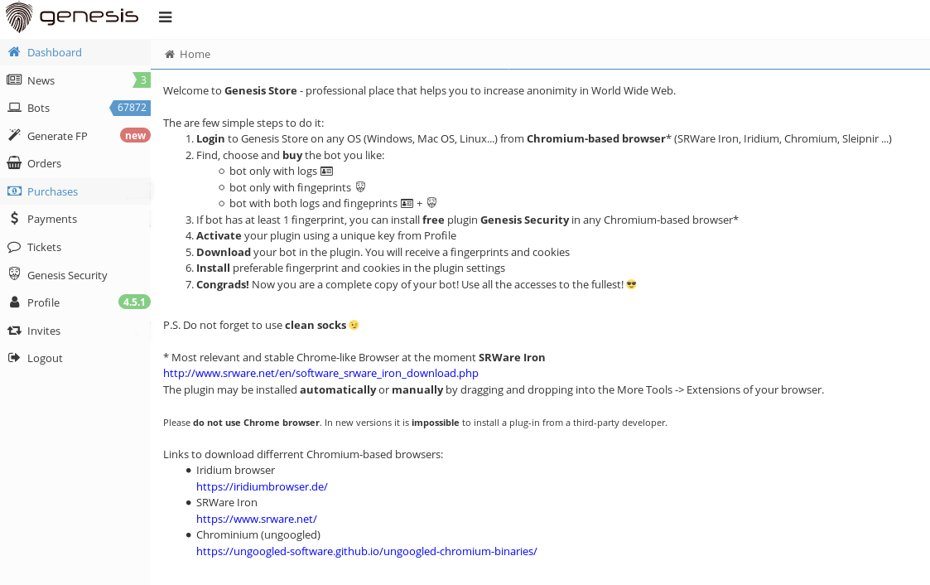
Cybercriminals soon became aware that unique fingerprints from users’ PCs make valuable information useful to many of their own kind. They began devising malware to steal fingerprints from users’ machines and selling such fingerprints along with other stolen data from the same machines, including user accounts, logins, passwords and browser cookies collected from various online services – from stores and payment systems to bank accounts. With our cybercrime threat intelligence technologies we were able to identify and analyze the biggest marketplace for this kind of data – the Genesis Store.
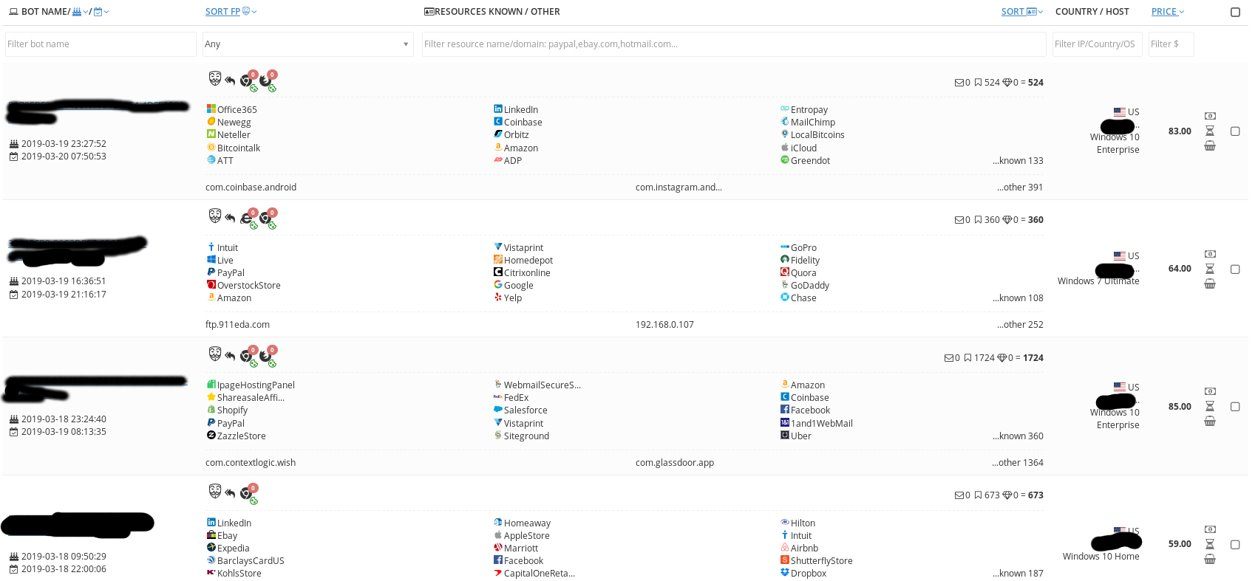
Genesis Store is an online cybercriminal invitation-based private market for stolen digital fingerprints. At the moment it offers more than 60k+ stolen bot profiles. The profiles include: browser fingerprints, website user logins and passwords, cookies, credit card information. The price varies from 5 to 200 dollars per profile – it heavily depends on the value of the stolen information. For example, if the bot has a login/password pair from an online bank account, the price is higher. As the marketplace owners have explained in their Darknet forum thread, the price is calculated automatically using a unique algorithm.
Genesis Store homepage
Bots for sale
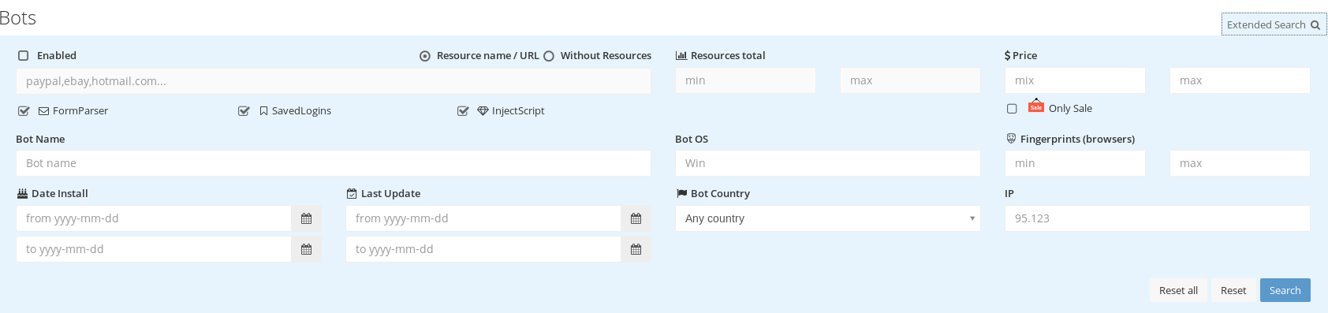
Genesis Store has a configurable search panel that allows searching for specific bots. Logins and passwords from a particular website, the victim’s country, operating system, date the profile first appeared at the market – everything is searchable.
Genesis search panel
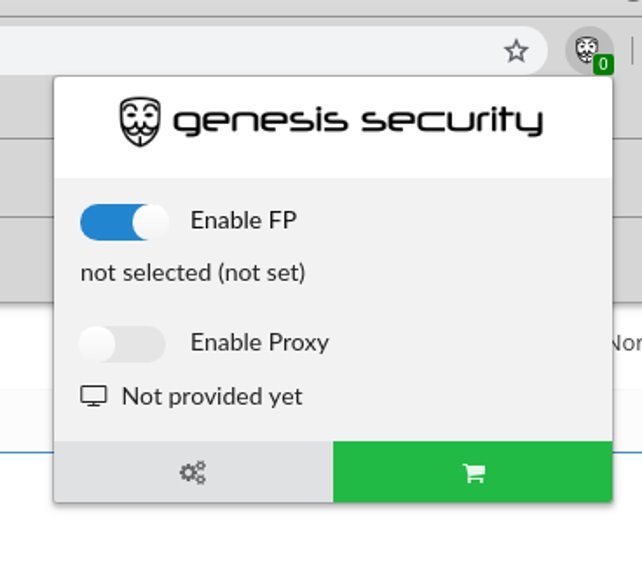
Genesis Store owners want to make the use of stolen profiles as easy as possible, so they have developed a special .crx plugin for Chromium-based browsers. The plugin allows installing stolen digital profiles into the cybercriminal’s own browser with a single mouse click for him to become a doppelganger of the victim. After that the bad guy only needs to connect to a proxy server with an IP address from the victim’s location and he can bypass the anti-fraud systems’ verification mechanisms, pretending to be a legitimate user.
Genesis plugin
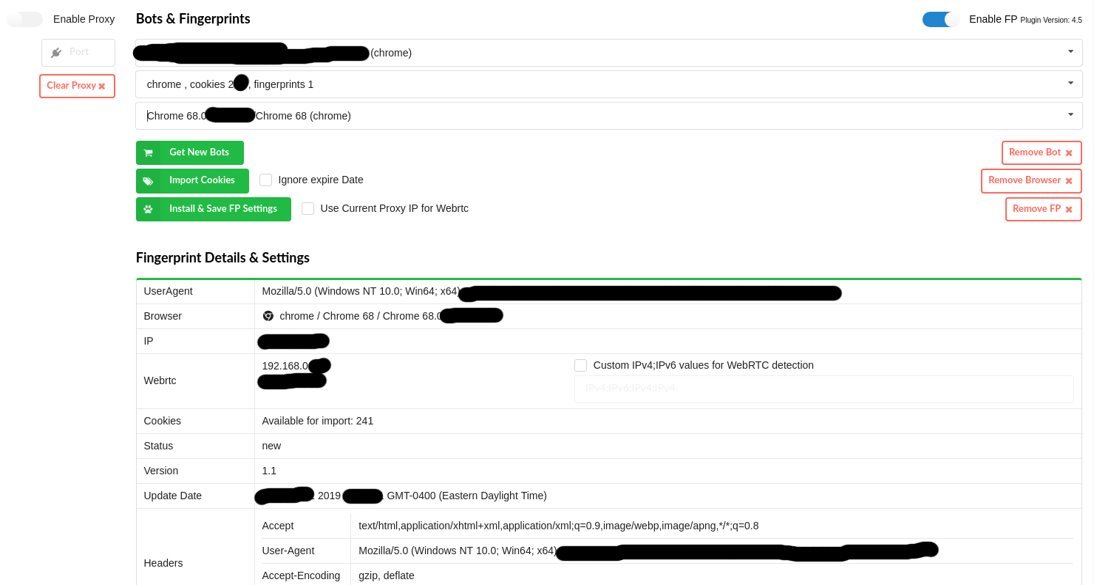
Fingerprint settings in Genesis plugin
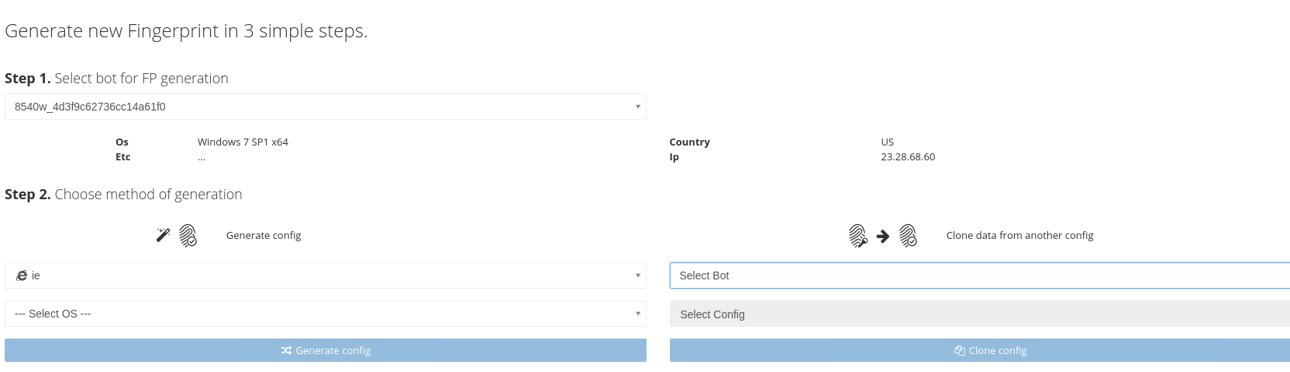
For the customers who don’t want to buy real fingerprints, there is also an option to generate unique ones. Genesis Store gives its customers an opportunity to use Genesis algorithms and the plugin to generate random fingerprints that can be used, for example, to enter stolen bank card information into online store forms: such unique browser fingerprints will be properly configured, so the anti-fraud system will not be alarmed.
Genesis fingerprint generator
The dark sphere
Another tool widely used to bypass anti-fraud systems is the Tenebris Linken Sphere browser. Its developers position it as the perfect browser for anonymity, and in fact it has been used for carding for years. Unlike the Genesis plugin, Sphere is a fully functional browser with advanced fingerprint configuration capabilities, automatic proxy server validity testing and usage options, etc. It even features a user activity emulator – cybercriminals can program it to open the desired websites, follow links, stay on websites for a given length of time, etc. Simply put, to trick the anti-fraud systems’ behavior analysis modules. The Tenebris Linken Sphere developers have also created a marketplace of unique fingerprints that can be used with Sphere browsers.
Tenebris website
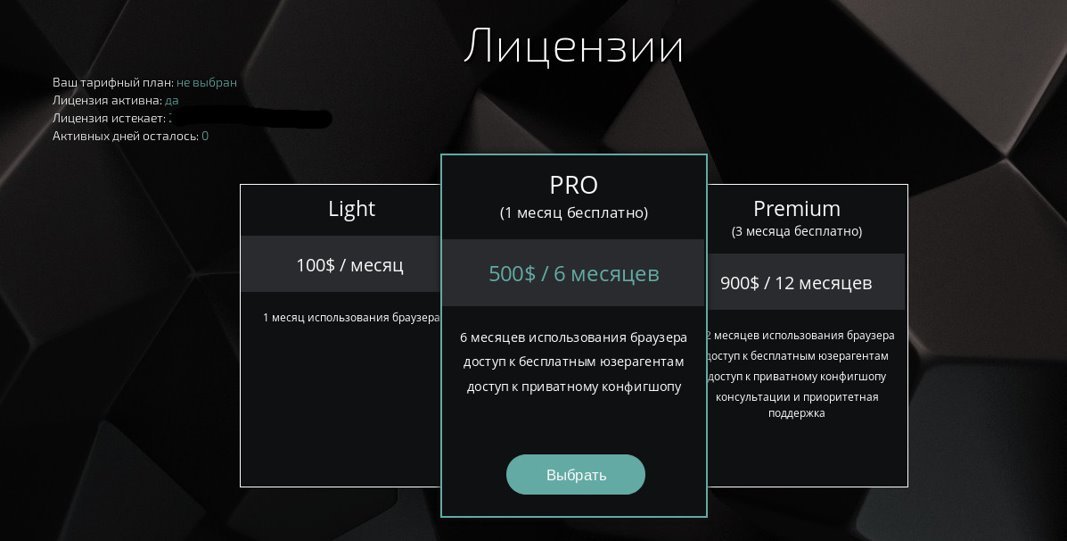
Unlike Genesis, Sphere uses a subscription-based licensing system. One month’s worth of the browser usage costs 100$. With the fingerprints market access thrown in, the price is 500$ per month.
Tenebris Sphere licenses
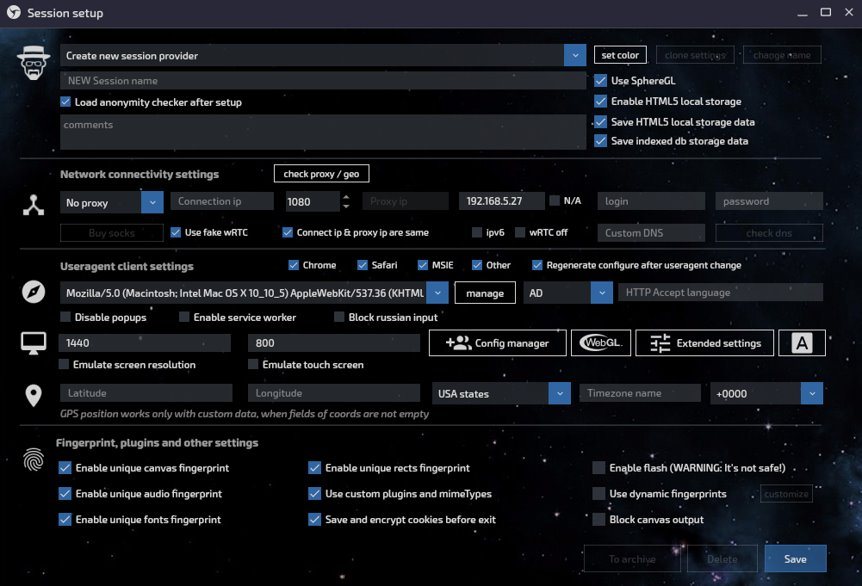
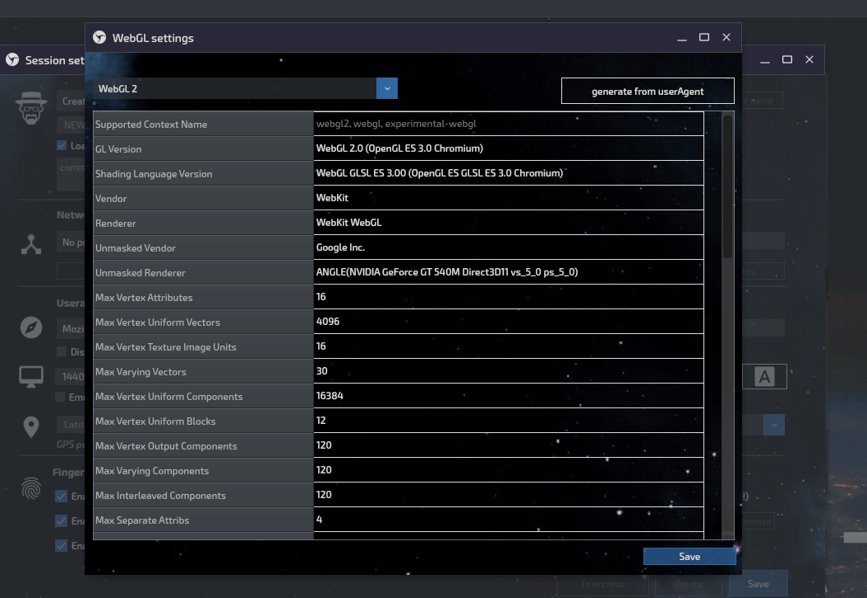
Sphere has much deeper fingerprint configuration options for generated fingerprints. Most of the parameters are fully adjustable for an opportunity to create exactly the fingerprint one needs to mimic a real user.
Configuration panel
Configuration panel
Conclusion
Antifraud systems are rapidly developing. They introduce new protection mechanisms to fend off fraudsters, while fraudsters develops new tools to break through the protection layers. The sums of money lost to carding attacks are huge, and cybercriminals are most certain to scale up these malicious activities.
The security departments of financial organizations must always look for ways to counter such threats. Extra two-factor authentication for any transaction initiated using a bank card or payment system is an absolute necessity these days, even if the user’s digital profile appears legit to the protection system. Even though it is not very convenient for users to complete the extra authentication routine each time they want to buy online, it is the most effective safeguard against carding attacks for the present.
In addition, new user behavior analysis methods must be developed and implemented together with custom fingerprinting technologies that may include hardware-based fingerprint collection arrangements operating on a deeper level than currently available. Additional biometric authentication should be considered as well.
Kaspersky Lab continuously researches financial cybercrime to provide timely protection against the hostile activities.
Digital Doppelgangers





















Ye Man Aung
supporting and secure issues protect for my account for feature support.