
Several days ago, our products detected an unusual sample from the Destover family. The Destover family of trojans has been used in the high profile attacks known as DarkSeoul, in March 2013, and more recently, in the attack against Sony pictures in November 2014. We wrote about it on December 4th, including the possible links with the Shamoon attack from 2012.
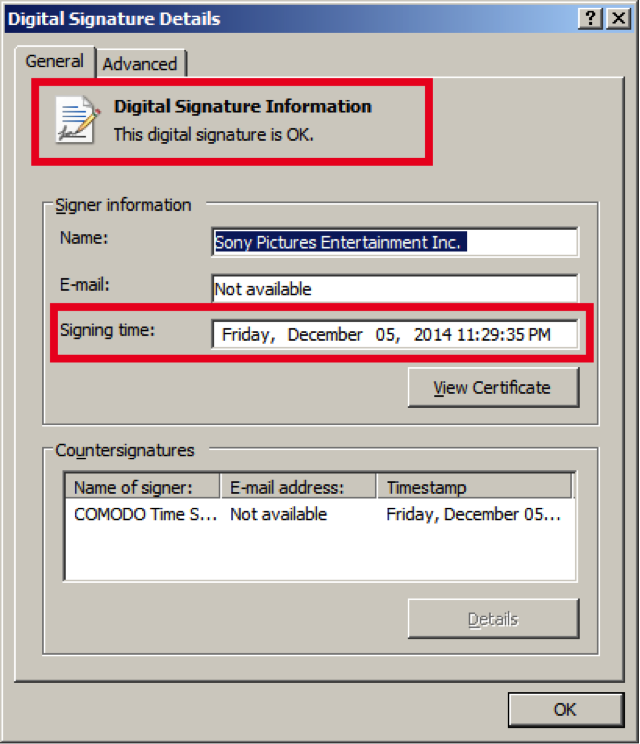
The new sample is unusual in the sense it is signed by a valid digital certificate from Sony:
The signed sample has been previously observed in a non signed form, as MD5: 6467c6df4ba4526c7f7a7bc950bd47eb and appears to have been compiled in July 2014.
The new sample has the MD5 e904bf93403c0fb08b9683a9e858c73e and appears to have been signed on December 5th, 2014, just a few days ago.
Functionally, the backdoor contains two C&Cs and will alternately try to connect to both, with delays between connections:
- 208.105.226[.]235:443 – United States Champlain Time Warner Cable Internet Llc
- 203.131.222[.]102:443 – Thailand Bangkok Thammasat University
So what does this mean? The stolen Sony certificates (which were also leaked by the attackers) can be used to sign other malicious samples. In turn, these can be further used in other attacks. Because the Sony digital certificates are trusted by security solutions, this makes attacks more effective. We’ve seen attackers leverage trusted certificates in the past, as a means of bypassing allowlisting software and default-deny policies.
We’ve already reported the digital certificate to COMODO and Digicert and we hope it will be denylisted soon. Kaspersky products will still detect the malware samples even if signed by digital certificates.
Stolen certificate serial number:
- 01 e2 b4 f7 59 81 1c 64 37 9f ca 0b e7 6d 2d ce
Thumbprint:
- 8d f4 6b 5f da c2 eb 3b 47 57 f9 98 66 c1 99 ff 2b 13 42 7a
UPDATE (December 10, 2014)
Since the publication of this blog, news has emerged that this sample may have been the result of a “joke” by a group of security researchers. This has prompted questions from journalists and others in the community so we decided to address them with this update:
1. Did you find the signed sample in the wild?
So far, we have not encountered the signed sample in the wild. We’ve only seen it submitted to online malware scanning services. However, the existence of this sample demonstrated that the private key was in the public domain. At that point we knew we had an extremely serious situation at hand, regardless of who was responsible for signing this malware.
Reports indicate the “researcher” reached out to the certificate authorities to get the certificate revoked after submitting the malware online. The certificate would have been revoked without the creation of new malware. There really was no need to create new malware to prove that the certificate hadn’t been revoked yet.
2. Do you know how many Sony certificates were leaked?
So far dozens of PFX files have been leaked online. PFX files contain the needed private key and certificate. Such files are password protected, but those passwords can be guessed or cracked. Not all of these PFX files will be of immediate value to attackers.
3. What is the danger of a code-signing certificate from a major corporation leaking online?
The importance of leaked code-signing keys cannot be overestimated. Software signed by a trusted publishing house will generally be trusted by the operating system, security software and first responders. It’s an extremely powerful way for attackers to stay below the radar.
Certificate revocation needs to be a top priority when responding to a major malware and breach incidents.
4. Do anti-malware products “trust” signed programs more those that are not signed?
Trust in files is based on their reputation and digital signatures play a big role in gauging reputation. But a digital signature by itself is not enough to create trust. We look at the reputation of the entities that issued and requested the certificate.
Kaspersky Lab products detect digitally signed files. Our products detected the signed Destover variant with the detection routine created for the first Destover variant.
‘Destover’ malware now digitally signed by Sony certificates (updated)
























Zulgrib
How do we add the certificat to untrusted certs ?
Byron Acohido
One has to question the maturity level of the security researcher responsible for this spoof, for adding to the level of obfuscation, instead of helping to foster useful understanding. Not terribly funny.
Joe D
@Byron: +1 Indeed. About as funny and displaying the maturity level of one who tells fart jokes.
Michael Moltke
Just goes to show, that one should always assert the feeds of any source prior to jumping to conclusions.