
News overview
In early January, it was reported that an amateur hacker had come close to pulling off a botnet attack using “improvised” materials. Armed with information gleaned from hacker forums, the DIYer created a Trojan using a zero-day exploit in Huawei routers and released it online. The attack was soon nipped in the bud, but the wannabe cybercriminal could not be traced.
Other slightly weightier news: first, experts reported growth in the Reaper (or IoTroop) botnet (not to be confused with North Korean hacker group The Reaper), first discovered last quarter; second, IT security resources hinted at the emergence of new “strains” of Mirai and Satori (the latter, known as Okiru, is intended for ARC processors), but so far without details. Moreover, in early February a platform selling JenX botnet services was detected and neutralized. JenX was found to be using a fan server for the video game GTA: San Andreas as its C&C. In terms of power, JenX was nothing to write home about, but the originality of its creators deserves a mention. On the topic of original botnets, another worth noting is DoubleDoor: the first known piece of “wild” malware to bundle two IoT vulnerabilities together.
As for new methods and vulnerabilities, besides the multiget hole in Memcached, last quarter news broke of a vulnerability in WordPress that makes it easy to down a web server. Fortunately, no in-the-wild attacks were observed.
The attack targets for this new weaponry remained largely the same. Profit is still the main motive behind DDoS attacks (the number of attacks on business in Russia alone doubled in 2017), although high-profile “commercial” attacks in the last three months were not so numerous. Within the space of three days in early February, players of Final Fantasy encountered problems signing into certain services. At roughly the same time, BusinessWire experienced similar difficulties lasting more than a week, during which period neither editors nor readers could access the news portal. There was no reported ransom demand, so the motive behind the attack can be assumed to be competition-related.
It would be amiss not to mention a series of attacks that hit GitHub and an unknown service provider in early March, which produced record volumes of garbage traffic — over 1 TB/s. This capacity was achieved by leveraging Memcached, a popular caching service for Linux servers. Interestingly, in some of these attacks the garbage traffic itself contained ransom demands in Monero.
Political motives are less common, but often more visible due to their topicality. The most headlining incident of late was, of course, the threat to sabotage the opening ceremony of the Winter Olympics in early February, most likely through a DDoS offensive. Even before that, in late January, the US Department of Defense repelled an influx of spam, and in late March their Russian counterparts had to survive a DDOS attack. In addition, experts reported that North Korean group The Reaper was extending its reach. Despite not showing any DDoS activity, it could soon start moving in that direction.
Another hard-hitting DDoS attack on major financial institutions in the Netherlands was initially thought to be political, but on closer inspection turned out to be pure hooliganism: Dutch police arrested a teen suspect for causing week-long mayhem at several banks simply to prove that it was possible.
DDoS is also becoming more popular as a means of personal revenge. California, for instance, witnessed the case of David Goodyear, who was found guilty of trying to launch a DDoS attack against an amateur astronomy forum when it denylisted him for using bad language. True, he can’t be accused of not trying other methods before turning his hand to cybercrime: Goodyear repeatedly registered on the forum under different chat names, but each time earned himself a ban for boorish behavior.
Quarter trends
Due to its capacity and relative accessibility, Memcached was the springboard for last quarter’s most sensational attacks. However, it could prove to be a short-lived trend, and here’s why.
In late February, Kaspersky DDoS Protection support was contacted by a company reporting an unusually high load on its communications channel in what it suspected to be a DDoS attack.
At first glance, the picture did indeed resemble a typical DDoS attack: the channel was clogged up, and users couldn’t access the company’s services. However, our investigation revealed that a CentOS Linux server with a vulnerable Memcached service was installed on one of the client servers. This service, used by the cybercriminals during the attack, generated large amounts of outgoing traffic, overloading the channel. In other words, the client was not the target, but an unwitting accomplice in the DDoS attack: the attackers used its server as an amplifier. After Kaspersky Lab’s recommendations were implemented, the malicious parasitic traffic stopped.
This situation is typical for Memcached attacks: owners of vulnerable servers hijacked during attacks notice the load increase and rush to patch any vulnerabilities not to suffer even more downtime losses. As a result, the number of vulnerable servers that can be utilized for this type of attack is rapidly declining, for which reason Memcached attacks will likely dry up soon.
Still, the picture in Q1 shows that “amplified” attacks, which were on the wane, have again picked up momentum. NTP and DNS-based boosting has practically disappeared, since most vulnerable services have already been patched. Cybercriminals will likely seek out other non-standard amplification methods besides Memcached. Last quarter, for instance, we registered a quite rare (yet effective) type of amplification attack, in which the LDAP service was used as an amplifier. Alongside Memcached, NTP, and DNS, this service has one of the biggest amplification factors. Despite the relatively small number of LDAP servers available, this type of attack could be a hit on the shadow Internet in the coming months.
Statistics for botnet-assisted DDoS attacks
Methodology
Kaspersky Lab has extensive experience of combating cyber threats, including DDoS attacks of various complexity types and ranges. Company experts track the actions of botnets by using the DDoS Intelligence system.
As part of the Kaspersky DDoS Protection solution, the DDoS Intelligence system intercepts and analyzes commands sent to bots from C&C servers; it does not require any user devices to be infected or cybercriminals to execute any actual commands.
This report contains DDoS Intelligence statistics for Q1 2018.
In the context of this report, it is assumed that an incident is a separate (single) DDoS-attack if the interval between botnet activity periods does not exceed 24 hours. For example, if one particular web resource was attacked by the same botnet in two waves with an interval of 24 hours or more, the incident is considered as two attacks. Bot requests originating from different botnets but directed at one resource also count as separate attacks.
The geographical locations of DDoS-attack victims and C&C servers used to send commands are determined by their respective IP addresses. The number of unique targets of DDoS attacks in this report is counted by the number of unique IP addresses in the quarterly statistics.
DDoS Intelligence statistics are limited to botnets detected and analyzed by Kaspersky Lab. Note that botnets are just one of the tools for performing DDoS attacks, and that the data presented in this report do not cover every single DDoS attack that occurred during the period under review.
Quarter results
- In Q1 2018, DDoS attacks were registered against targets in 79 countries (84 in the previous quarter). As ever, the vast majority (95.14%) occurred in the top ten countries.
- As for attack targets, as usual about half were located in China (47.53%), although the share was somewhat lower against the previous quarter.
- The number of attacks and targets rose significantly, as did the number of long-duration attacks. The most sustained DDoS attack lasted 297 hours (more than 12 days), making it one of the longest in recent years.
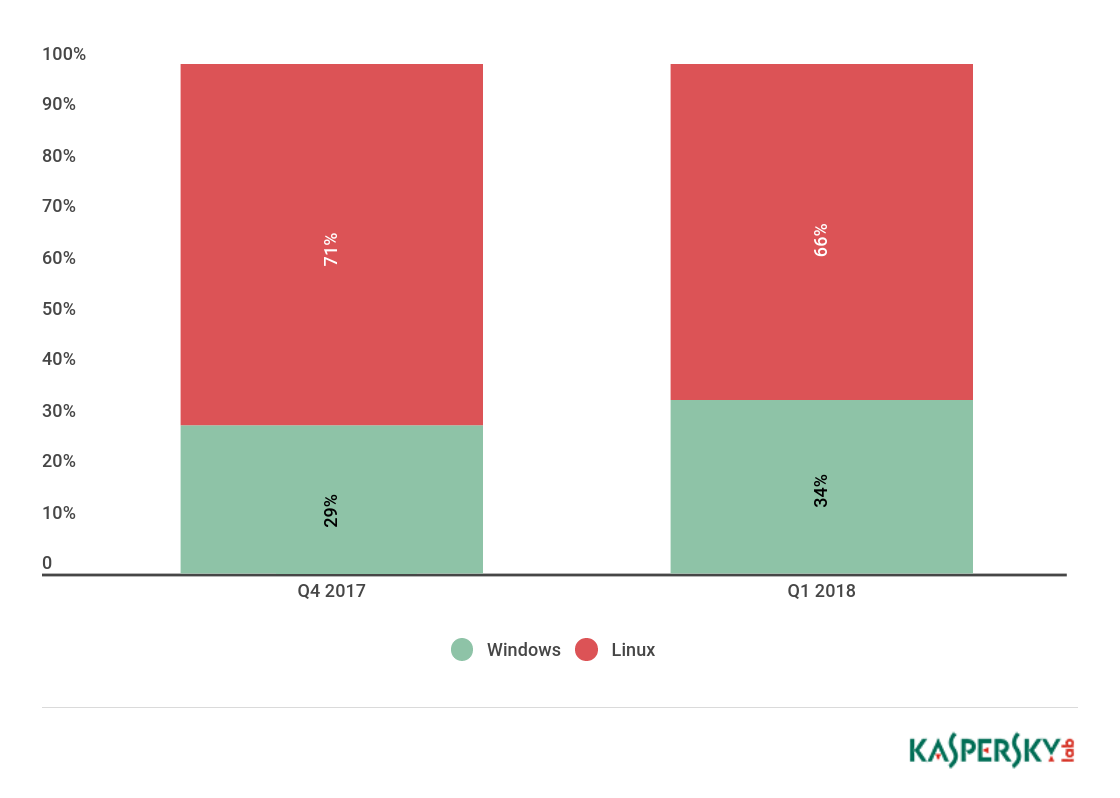
- The share of Linux botnets fell slightly to 66% against the previous quarter’s 71%.
- Significant peaks in the number and power of cyberattacks were observed in mid-January and early March, while the mid-quarter period was relatively calm.
Geography of attacks
China easily retained pole position by number of attacks: its share remained almost unchanged, up from 59.18% to 59.42%. The US share (17.83%), the second largest, increased by a more noticeable 1.83%. South Korea again took bronze, but its share fell by more than 2%, from 10.21% to 8%.
Britain (1.30%) moved from fourth to fifth. Tenth place in Q1 2018 went to Russia, whose share decreased from 1.25% to 0.76%. The Netherlands and Vietnam dropped out of the top ten, but Hong Kong (with a solid 3.67% against 0.67% in Q4 2017) and Japan (1.16%) reappeared.
As regards the distribution of attack targets, top spot again belongs to China, although its share declined from 51.84% to 47.53%. Meanwhile, the still second-place US saw its share increase from 19.32% to 24.10%. Third position was taken by South Korea (9.62%). France’s ranking changed significantly: shedding just 0.65% this quarter, it dropped from fifth to ninth place.
The list of top ten most attacked countries said goodbye to Russia and the Netherlands, but welcomed Hong Kong (4.76%) straight into fourth place, and Japan (1.6%) into sixth. Overall this quarter, the total share of top ten countries increased slightly to 94.17% against 92.9% at the end of 2017.
Dynamics of the number of DDoS attacks
Most Q1 activity occurred in the first and last third. The number of attacks peaked on January 19 (666) and March 7 (687 attacks). This is probably linked to the end of the New Year holidays (the number of attacks began to rise around the second week of January) and the March sales (in connection with International Women’s Day). The quietest days were observed at roughly the same time: January 16 and March 11. The mid-quarter period passed relatively smoothly without significant peaks or noticeable declines.
The calmest day of the week in the latest quarter was Sunday, accounting for just 11.35% of all attacks.
Types and duration of DDoS attacks
The share of SYN-DDOS attacks increased slightly (from 55.63% to 57.3%), but there was no repeat of the situation seen in previous quarters. The share of ICMP attacks almost doubled, from 3.4% to 6.1%. Accordingly, UDP, TCP and HTTP floods were forced to cede some ground: their shares dropped by 1-2% against the previous quarter.
After some respite at the end of 2017, we saw a return of sustained attacks: the longest lasted 297 hours (12.4 days). And although that falls short of the world record, the magnitude is still considerable. We have to go back to late 2015 for a longer attack.
The share of all other sustained attacks (50 hours or more) increased by more than six times, from 0.10% to 0.63%. At the other end of the spectrum, the share of the shortest attacks (9 hours or less) also grew: if last quarter they accounted for 85.5% of all attacks, now the figure stands at 91.47%. Meanwhile, the number of attacks lasting between 10 hours and three days in the latest quarter almost halved from 14.85% to 7.76%.
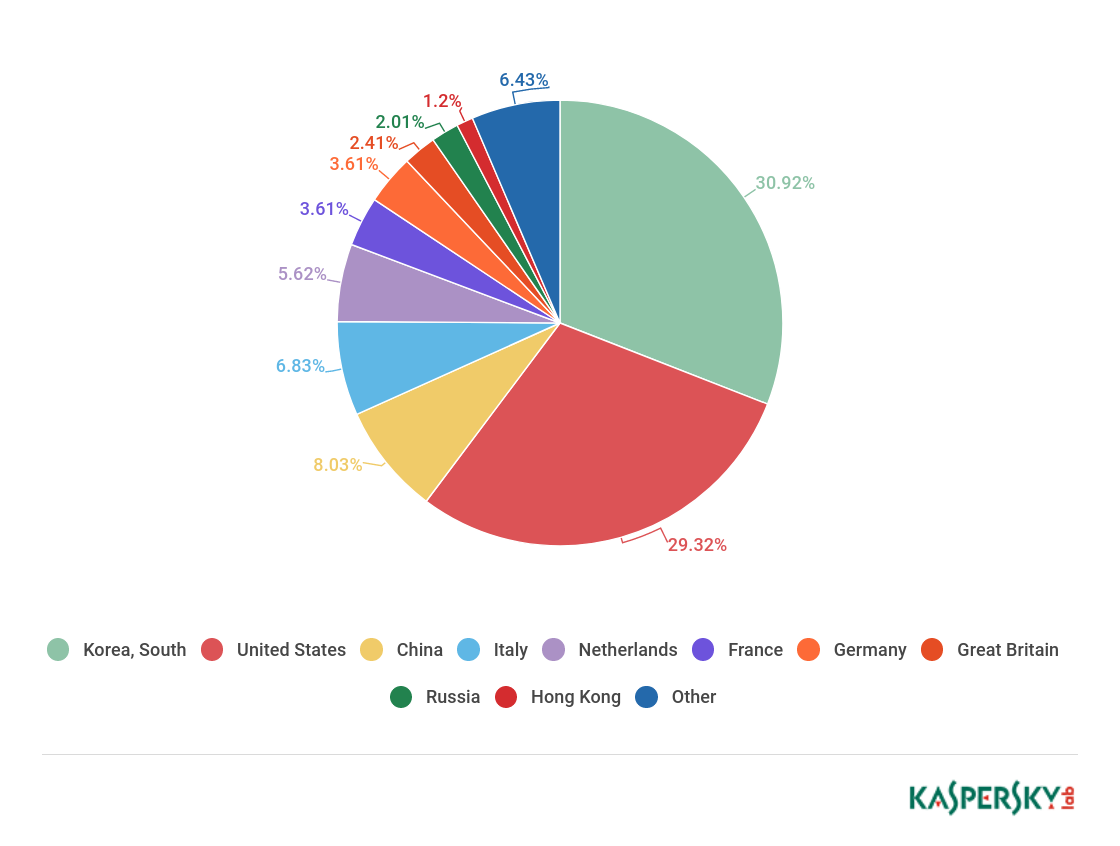
The top ten countries by number of C&C servers last quarter underwent a major reshuffle: Canada, Turkey, Lithuania, and Denmark dropped out, while Italy, Hong Kong, Germany, and Britain climbed upwards. The top three remained practically unchanged: South Korea (30.92%), the US (29.32%), China (8.03%). Only Russia (2.01%), having shared bronze with China in late 2017, slid down to ninth place.
The US share almost doubled, bringing it within touching distance of this ranking’s perennial leader South Korea. In addition, the shares of Italy (6.83%), which last quarter did not even make the top ten, the Netherlands (5.62%), and France (3.61%) increased significantly. This jump was due to a sharp rise in the number of C&C accounts for Darkai (in the US, Italy, the Netherlands, and France) and AESDDoS (in China) bots.
The share of Linux botnets last quarter fell slightly compared to the end of 2017, down to 66% from 71%. Accordingly, the share of Windows-based botnets climbed from 29% to 34%.
Conclusion
In Q1 2018, we observed a significant increase in both the total number and duration of DDoS attacks against Q4 2017. The new Linux-based botnets Darkai (a Mirai clone) and AESDDoS are largely responsible for this hike. The number of now familiar Xor attacks also rose. Neither did Windows-based botnets remain idle, making some headway against Linux in the total number of attacks. The old Yoyo botnet was particularly lively, almost five times as active.
The number of mixed attacks involving several botnet families also increased. This is a clear continuation of the trend that we spoke about at the end of last year: to optimize outlays, attackers utilize unused parts of botnets to generate garbage traffic, redeploying them across targets.
Amplified attacks returned to the cyber arena, particularly through the Memcached service. However, we expect that server owners will quickly spot the abundance of garbage traffic and patch up the vulnerabilities, which will dent the popularity of attacks of this type. That being the case, DDoS masterminds will likely seek out other amplification methods, one of which could be LDAP services.
DDoS attacks in Q1 2018

























mike matlack
Great information. Do you provide the data behind the report? I would like to learn, of the number of attacks ON the US, how many of them originated in the US and how many originated outside the US. Thank you!