
It is often the case that something new is just a reincarnation of something old. We have come across a series of clipboard injection attacks on cryptocurrency users, which emerged starting from September 2022. Although we have written about a similar malware attack in 2017 in one of our blogposts, the technique is still very relevant today as it doesn’t have any perfect solution from the perspective of operating system design. The only way to prevent such attacks is to be extremely cautious and attentive, or use a decent anti-malware solution to detect a piece of malicious code. As long as such attacks continue to thrive in the modern ecosystem of the cryptocurrency world, it’s worth explaining how they work and where the danger lies.
In a nutshell, the attack relies on malware replacing part of the clipboard contents once it detects a wallet address in it.
Past attacks
This technique of replacing clipboard contents is more than a decade old. It all started from banking trojans focused on specific banks and replacing bank account numbers in the clipboard. Here is a report from CERT Polska that warned Polish users about such a threat targeting users of local banks in 2013. However, such attacks required detecting a particular internet banking environment, and their success depended also on other fields being filled correctly (i.e. bank SWIFT code, branch name, etc). Focusing on something global and provider-independent, such as a cryptocurrency wallet, made it much more efficient for cryptothieves. Adding increased value of cryptocurrencies made it a very lucrative target. So, this is where we started seeing the first clipboard attacks on cryptocurrency owners. They were replicated and reused in other malware too. We even made a generic detection for some of such families, naming them Generic.ClipBanker.
Why it is dangerous
Despite the attack being fundamentally simple, it harbors more danger than would seem. And not only because it creates irreversible money transfers, but because it is so passive and hard to detect for a normal user. Just think of it, most malware is only efficient when there is a communication channel established between the malware operator and the victim’s system. Backdoors require a control channel, spying trojans require a way to pass stolen data, cryptominers need network communication too, etc. It’s only a small fraction of malware that exist on their own and do not require any communication channel. But this is the most dangerous and harmful kind: self-replicating malware, such as destructive viruses and network worms; ransomware that silently encrypts local files, and so on. While worms and viruses may not connect to the attacker’s control servers, they generate visible network activity, or increase CPU or RAM consumption. So does encrypting ransomware. Clipboard injectors, on the contrary, can be silent for years, show no network activity or any other signs of presence until the disastrous day when they replace a cryptowallet address.
Another factor is detection of the malware payload. While most malware is discovered through an association with known bad infrastructure (IPs, domains, URLs), or when it automatically activates a malicious payload, clipboard injectors do not run their evil payload unless an external condition (the clipboard contains data of certain format) is met. This further lowers the chances of new malware being discovered through automatic sandboxing.
Trojanized Tor Browser installers
Some recent developments in the use of this type of malware seek to abuse Tor Browser, a tool to access the dark web using the Onion protocol, also known as the Tor network. We relate this to the ban of Tor Project’s website in Russia at the end of 2021, which was reported by the Tor Project itself. According to the latter, Russia was the second largest country by number of Tor users in 2021 (with over 300,000 daily users, or 15% of all Tor users). The Tor Project called to help keep Russian users connected to Tor to circumvent censorship. Malware authors heard the call and responded by creating trojanized Tor Browser bundles and distributing them among Russian-speaking users. The first variants appeared in December 2021, but only since August 2022 have we seen a larger wave of torbrowser_ru.exe malicious executables. The trojanized installers offered Tor Browser with a regional language pack, including Russian, as the file name suggests:
Supported languages in the trojanized installer
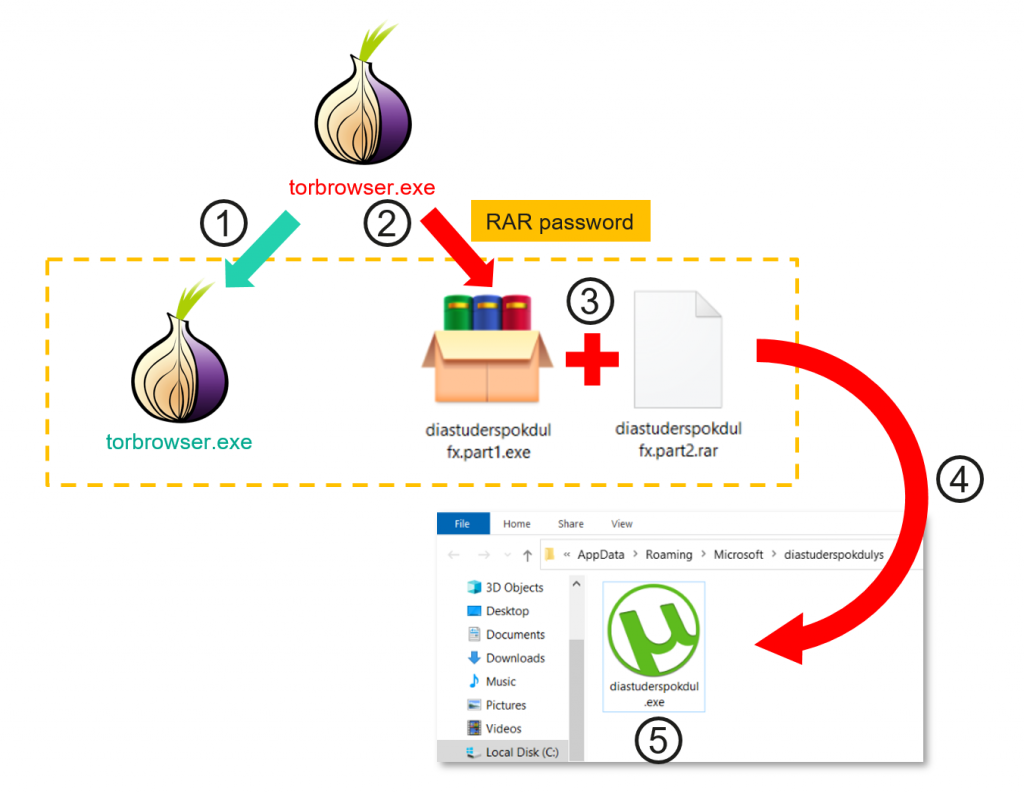
We have come across hundreds of similar installers that all behaved according to the following scenario:
Trojanized Tor Browser extracting and launching a malware payload
The target user downloads Tor Browser from a third-party resource and starts it as torbrowser.exe. The installer is missing a digital signature and is just a RAR SFX (self-extracting executable) archive. It contains three files:
- The original torbrowser.exe installer with a valid digital signature from the Tor Project.
- A command-line RAR extraction tool with a randomized name.
- A password-protected RAR archive (random password).
The SFX starts the original torbrowser.exe as a disguise, while also running the RAR extraction tool on the embedded password-protected RAR archive. The purpose of protecting it with a password is to evade static-signature detection by antivirus solutions. It doesn’t protect the malware from sandbox-based detection. The password and the destination for the extraction are part of the trojanized torbrowser.exe executable, and may be extracted via manual analysis. Once the file is dropped inside one of the current user AppData subdirectories, the dropped executable is started as a new process and registers itself in the system autostart. Most of the time, the executable is disguised with the icon of a popular application, such as uTorrent.
Clipboard-injector malware
The payload of this installer is passive and communicationless clipboard-injector malware.
The malware is protected with the Enigma packer v4.0, which complicates analysis. Enigma is a commercial software protector. The malware authors likely used a cracked version of the packer lacking any license information. However, if this or another instance from the same malware authors appears in the hands of law enforcement officers, we would like to leave a reference to their system drive serial number, which we extracted from the malware sample: 9061E43A.
The payload of this malware is rather simple: the malware integrates into the chain of Windows clipboard viewers and receives a notification every time the clipboard data is changed. If the clipboard contains text, it scans the contents with a set of embedded regular expressions. Should it find a match, it is replaced with one randomly chosen address from a hardcoded list.
Hexdump of the malware data with regular expressions and replacement wallet IDs
We identified the following regular expressions inside the sample.
bc1[a-zA-HJ-NP-Z0-9]{35,99}($|\s) – Bitcoin
(^|\s)[3]{1}[a-km-zA-HJ-NP-Z1-9]{25,34}($|\s) – Litecoin/Bitcoin Legacy
(^|\s)D[5-9A-HJ-NP-U]{1}[1-9A-HJ-NP-Za-km-z]{32}($|\s) – Dogecoin
(^|\s)0x[A-Fa-f0-9]{40}($|\s) – ERC-20 (i.e. Ethereum, Tether, Ripple, etc)
(^|\s)[LM]{1}[a-km-zA-HJ-NP-Z1-9]{25,34}($|\s) – Litecoin Legacy
((^|\s)ltc1[a-zA-HJ-NP-Z0-9]{35,99}($|\s) – Litecoin
(^|\s)8[0-9A-B]{1}[1-9A-HJ-NP-Za-km-z]{93,117}($|\s) – Monero
(^|\s)4[0-9A-B]{1}[1-9A-HJ-NP-Za-km-z]{93,117}($|\s) – Monero
Each sample contains thousands of possible replacement addresses for Bitcoin. Including thousands of addresses makes it harder to denylist them or to trace the theft. However, we collected all of them and would like to share them with researchers and investigators in an attachment to this blog.
The malware authors also preserved a feature to disable their creation: a special hotkey combination (Ctrl+Alt+F10). Pressing it causes the malware to unregister all handlers and stop running. The purpose was likely to disable the malware during the testing stage.
Victimology
Among the roughly 16,000 detections, the majority were registered in Russia and Eastern Europe. However, the threat spread to at least 52 countries worldwide. Here are the TOP 10 countries affected, according to our own data:
- Russia
- Ukraine
- United States
- Germany
- Uzbekistan
- Belarus
- China
- Netherlands
- United Kingdom
- France
Detections of the malicious Tor Browser worldwide, January 2022 – February 2023 (download)
Given that we only see a fraction of the real picture, the global number of infections may well be several or even tens of times higher.
Impact
To measure the impact, we collected hundreds of known malware samples, unpacked them from Enigma, and extracted the cryptowallet replacement addresses. Then we walked through the respective blockchains and calculated the total inputs to the wallets, assuming they all came from compromised users. This is how we measured the total loss caused by this single malware developer.
Stolen cryptocurrencies (converted to USD at the exchange rate valid at the time of writing) (download)
Due to its advanced technology that anonymizes transaction data to achieve maximum privacy, the Monero public ledger doesn’t reveal the transferred amount, so we couldn’t really look into it, but it is likely to be very small compared to the Bitcoin theft.
We believe that the actual theft is bigger because this research is focused on Tor Browser abuse. There may be other campaigns, abusing different software and using other means of malware delivery as well as other types of wallets.
Countermeasures
A mistake likely made by all victims of this malware was to download and run Tor Browser from a third-party resource. We haven’t managed to identify a single website that hosts the installer, so it is likely distributed either via torrent downloads or some other software downloader. The installers coming from the official Tor Project were digitally signed and didn’t contain any signs of such malware. So, to stay safe, in the first place, download software only from reliable and trusted sources.
However, even if you do download a rogue file masked as something else, using a decent antivirus solution or uploading the file to VirusTotal could help identify any malicious intent. Despite all attempts to evade detection, the malware will get discovered, it’s only a matter of time.
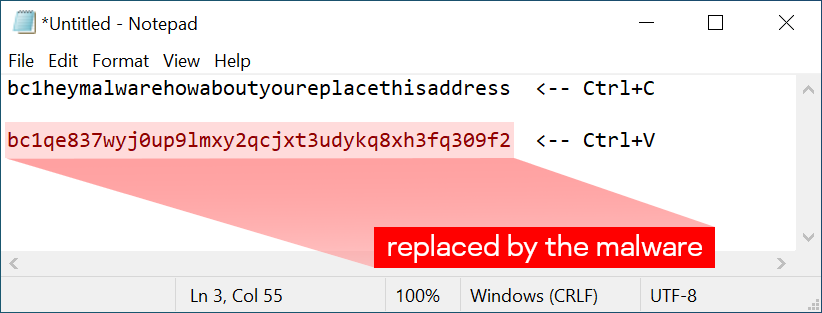
Lastly, if you would like to check if your system is compromised with malware from the same class, here is a quick Notepad trick. Type or copy the following “Bitcoin address” in Notepad: bc1heymalwarehowaboutyoureplacethisaddress
Now press Ctrl+C and Ctrl+V. If the address changes to something else — the system is likely compromised by a clipboard-injector type of malware, and is dangerous to use. At this stage we recommend scanning your system with security software for any malware presence. But if you want to have full confidence that no hidden backdoors remain, once a system is compromised, it should not be trusted until rebuilt.
Bitcoin address replaced by malware after pasting in an infected system
Stay safe and don’t let your coins fall into the hands of criminals.
Appendix (indicators of compromise)
Examples of clipboard injectors:
0251fd9c0cd98eb9d35768bb82b57590
036b054c9b4f4ab33da63865d69426ff
037c5bacac12ac4fec07652e25cd5f07
0533fc0c282dd534eb8e32c3ef07fba4
05cedc35de2c003f2b76fe38fa62faa5
0a14b25bff0758cdf7472ac3ac7e21a3
0b2ca1c5439fcac80cb7dd70895f41a6
0c4144a9403419f7b04f20be0a53d558
0d09d13cd019cbebf0d8bfff22bf6185
0d571a2c4ae69672a9692275e325b943
Examples of Tor Browser installers:
a7961c947cf360bbca2517ea4c80ee11
0be06631151bbe6528e4e2ad21452a17
a2b8c62fe1b2191485439dd2c2d9a7b5
53d35403fa4aa184d77a4e5d6f1eb060
ad9460e0a58f0c5638a23bb2a78d5ad7
cbb6f4a740078213abc45c27a2ab9d1c
eaf40e175c15c9c9ab3e170859bdef64
89c86c391bf3275790b465232c37ddf5
1ce04300e880fd12260be4d10705c34f
c137495da5456ec0689bbbcca1f9855e
Replacement addresses for Bitcoin wallets:
Download address list (PDF)
Copy-paste heist or clipboard-injector attacks on cryptousers
























Clouseau
Tsk tsk! Hopefully the malware authors are not checking up on the opposition.
However, the string ‘bc1heymalwarehowaboutyoureplacethisaddress’ could be better able to fool a simplistic check for a legitimate wallet address?
How about ‘bc1heyma1wareh0wab0uty0urep1aceth1saddress’ ?
Securelist
Hi Clouseau!
Thank you for you question! We’ve tested the sample address on the investigated threat, and it worked. However, if cybercriminals will detect and ignore this address, it is definitely worth using alternatives.