
A trojan called Bohu that was spreading earlier this year caught people’s attention: it has the ability to block cloud-based anti-virus services, which is kind of a new thing. The malware spreads via social engineering and mostly targets China. The guys over at MMPC have published a nice blog post with more details here.
First off, our products already detected and blocked Bohu based on its behavior profile even before we had any signatures out for it. On the contrary, if a system was already infected before the installation of a scanner, you might be in trouble…
Amongst other things, Bohu also prevents access to a Kaspersky server that hosts virus signature updates by hooking the DNS resolver in order to filter out resolution attempts for the corresponding domain name. Consequently, an infected system is prevented from automatically updating its Kaspersky signature databases, so it cannot detect and remove the threat.
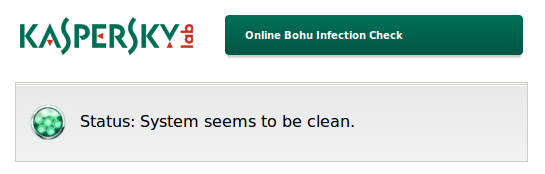
However, the domain name filter can also be turned into an infection check! We have prepared a little web page that takes advantage of Bohu’s blockade and displays different messages depending on whether a system can access the blocked domain or not. Users can now simply surf to this page to find out if they are infected with the trojan. If the page shows the above message, the trojan is not present.
But if the web page shows a warning message, the system is most likely infected:
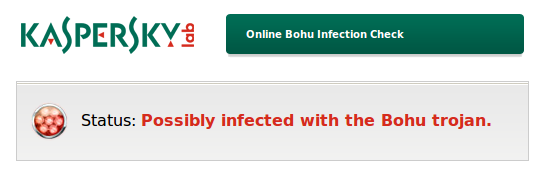
In any case, if you see the message above, you should manually scan and clean your system. To do so, you can download our freely available rescue disk image and burn it to a CD or USB drive, then boot into it. As the scanner on the rescue system is not affected by the trojan’s domain filter, it can still update its signatures and detect and remove the malware. More information on how to use the rescue system is available online on this link.





















Checking for infections with the Bohu trojan