
We previously wrote several times about Man-in-the-Mobile attacks which aim to steal mTANs sent via SMS. For a long time, only two families of such malware have been known: ZeuS-in-the-Mobile (ZitMo) and SpyEye-in-the-Mobile (SpitMo). ZitMo and SpitMo work together with their Windows ‘brothers’. Actually, without them, they would look like trivial SMS spy Trojans. It is necessary to mention that during the last two years such attacks have been observed only in some European countries like Spain, Italy, Germany, Poland and few others.
But when the mobile version of Carberp Trojan appeared (we detect it as Trojan-Spy.AndroidOS.Citmo, Carberp-in-the-Mobile) such attacks became real in Russia as well. There is no secret that online banking is becoming more and more popular in Russia; and banks are very active in promoting online banking with various authorization methods.
Carberp for Windows works in a similar way to the ZeuS Trojan. If a user tries to login into his online banking account using a machine infected by Carberp, the malware will modify the transaction so that user credentials are sent to a malicious server rather than a bank server.
In addition to the login and password, cybercriminals still need mTANs in order to confirm any money transfer operation from a stolen account. That is why one of the Carberp modifications (we call it Trojan-Spy.Win32.Carberp.ugu and we’ve added detection for it on 11th of December) alters the online banking web page on the fly, inviting the user to download and install an application which is allegedly necessary for logging into the system. And the user can get this link via SMS message by entering his phone number or by scanning a QR-code:
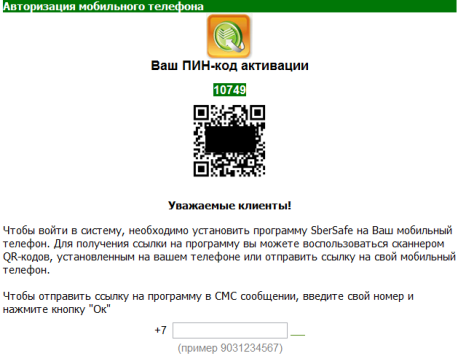
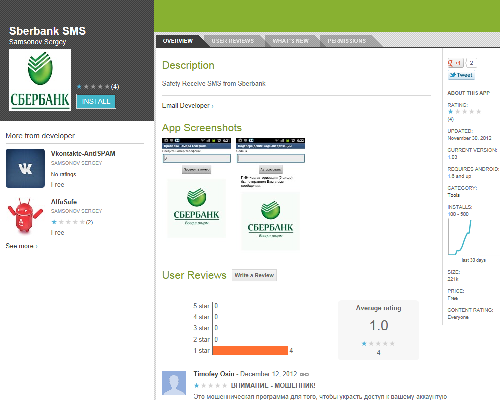
According to this screenshot, users of one of the most popular Russian banks, Sberbank, are under attack. ‘Sberbank’ updated its web page on 12th of December with information about the attack. The link in the QR-code led to the fake ‘SberSafe’ application (Trojan-Spy.AndroidOS.Citmo) which has been in Google Play since 30th of November.
The same developer (‘SAMSONOV SERGEY’) has uploaded two more apps into Google Play: ‘AlfaSafe’ (possibly for AlfaBank users) and ‘VkSafe’ (for Vkontakte). These apps have exactly the same functionality as ‘SberSafe’ (stealing online banking-related SMS messages).
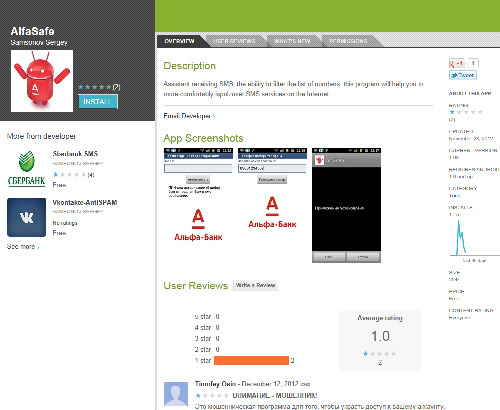
The ‘SberSafe’ app has been downloaded at least 100 times, ‘AlfaSafe’ has been downloaded at least once and ‘VkSafe’ – 50 times.
The CitMo Android Trojan works in almost the same way as ZitMo. It is able to hide particular SMS messages and resend them to the attacker’s command server. Some versions of ZitMo resend SMS messages to particular cell phone numbers in addition to various web servers. Known versions of CitMo and the Windows module of Carberp (Trojan-Spy.Win32.Carberp.ugu) work only with the remote server ‘bersta***.com’.
If a potential victim launches the malicious app, he or she will see a window inviting them to enter a cell phone number. If they type it in, this number will be written to the ‘auth.txt’ file and sent to a remote server. After some time the user will receive an SMS message containing a five-digit code which must be entered in the app window. This code will be written to the ‘authcode.txt’ file and used together with the cell phone number as an identifier for data sent to remote server.

After this, CitMo downloads configuration data from the server, which is written to ‘hide.txt’ and ‘view.txt’ files. The file ‘hide.txt’ will contain information about the numbers which must be hidden if an incoming SMS message is received from it. The file ‘view.txt’ will contain information about numbers which must be shown on the screen if an incoming SMS message is received from it. These actions are performed in order to hide all the activities related to the transfer of money stolen from a user’s account.
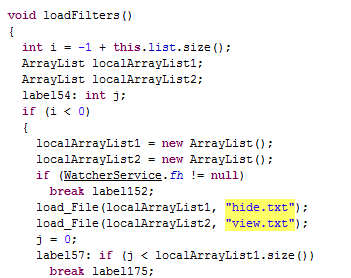
After this, the malware waits for incoming SMS messages, checks the sender number, and if matches a number in ‘hide.txt’ hides the message and writes it to the ‘messages.txt’ file, which is sent to the remote server.
It is necessary to mention that despite the fact that Google does a lot of things in order to prevent the appearance of malware in Google Play, the official app market continues to suffer from various types of malware. This attack is not the first Man-in-the-Mobile attack with a mobile component stored inside Google Play. We contacted Google on 12th of December and on 13th of December all CitMo variants were deleted from the market.
There is no surprise that attacks like ZitMo and SpitMo are now being seen in Russia as well. As we see more financial services and these services evolve, cybercriminals become more active as well. And virus writers won’t stop in the nearest future. Such types of malware will evolve as well and continue to be a problem for users not only from Europe but from Russia and perhaps other countries.





















Carberp-in-the-Mobile