
How easy is it for bad guys to buy valid digital certificates from CAs using fake data and then start signing Trojan bankers with them? In Brazil it appears to be very easy.
Today most software developers digitally sign their programs. The process involves Certification Authorities (CAs) that must verify the authenticity of the files and issue a certificate to the developers.
As we know, valid or stolen digital certificates are used by some malware authors to create files that can go undetected for some time and be recognized as legitimate. Now Brazilian cybercriminals have started using this technique in their malware in an attempt to gain more time to spread files undetected. Recently we found a Trojan banker signed with a valid digital certificate issued by a CA. It appears that fake company data was used to obtain the certificate.
How easy is it for a CA to check if the data they receive is legitimate or not? Brazilian cybercriminals registered a domain called gastecnology.org, copying the name of a well-known and trusted local software company. This is the data used to register the domain:
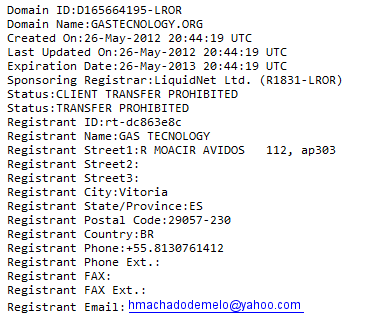
The data is totally fake. The domain was registered using a free webmail (Yahoo). The address, in the beautiful city of Vitória, is for a residential build:
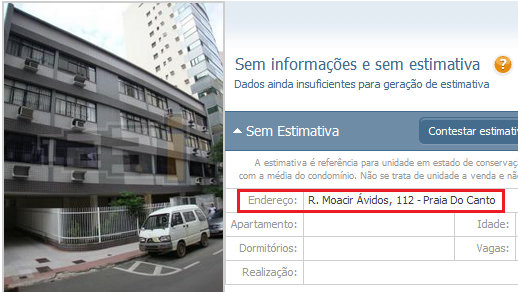
The telephone number used to register the domain is also fake; it’s not located in Vitória (where the area code is 27), but in Pernambuco state (area code 81). But even using the forged data in the registered domain, the criminals were able to buy digital certificates from Comodo, issued on 28 May, and valid until 29 May 2015:

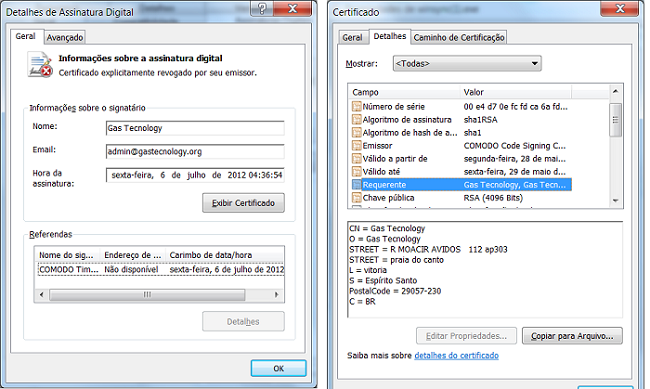
After this easy step, they started signing their Trojans:
After a mass mailing campaign that requested Brazilian Internet banking users to install an “update”, some users were infected.
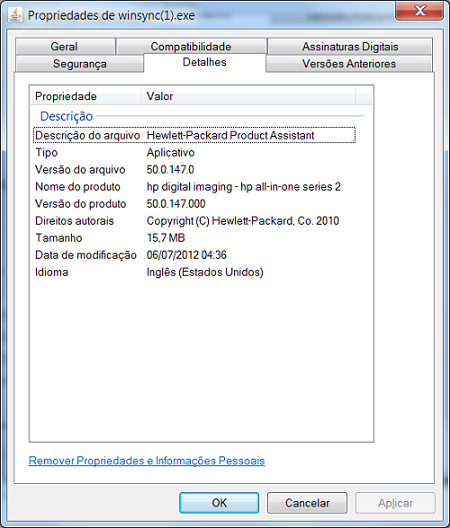
One of the Trojans, besides being digitally signed, used another trick that is common among malware authors: HP was mentioned in the file description in an attempt to trick users into believing it was a legitimate file.
The digital certificates were revoked by Comodo 15 days after being issued following an alert from a local security company. Kaspersky detects it as Trojan-Banker.Win32.Banbra.atfl.




















Brazilian Trojan Bankers Now Digitally Signed