
- Why Bluetooth? Bluetooth Technology
- Security Mechanisms
- Types of Bluetooth Attack
- Research, or New Year War-nibbling
- Protection
- Further Reading
Why Bluetooth? Bluetooth Technology
New technologies are swiftly becoming part of every aspect of human life. It’s now impossible to imagine life without devices which a few years ago were only to be seen in sci-fi films.
Bluetooth technology first started being developed by Ericsson in 1994. In 1998 Ericsson, IBM, Nokia, Intel and Toshiba formed the SIG consortium, which developed the Bluetooth standard. Many mobile phones and computer peripherals are now equipped with Bluetooth, and some household appliance manufacturers have also adopted this technology as well.
Transceivers which make it possible to use Bluetooth with devices that were designed without Bluetooth capability are now available. They make it possible to connect a telephone to a stereo system in order to download MP3 files to the handset or to listen to MP3 files in the phone’s memory. Bluetooth earphones, handsfree devices and car kits are just a few examples of the ways in which Bluetooth can be used.
Bluetooth is now widely implemented; this, combined with the novelty of the technology meant that hackers started to target Bluetooth and its potential vulnerabilities at the beginning of the new millennium. After all, hackers are always attracted to new, unresearched technologies. Groups such as @stack and shmoo were involved in Bluetooth research.
Bluetooth is also an object of interest for the antivirus industry, as worms can use this technology to spread. For example, Cabir, Lasco, Comwar — all these worms run under Symbian OS and spread via Bluetooth. Because of the ability to transmit files (including potentially malicious ones) Bluetooth vulnerabilities are of real interest.
Bluetooth was originally designed to eliminate wires connecting devices. For example, if you connect a mouse, a printer, a mobile phone and, say, a GPS receiver to a laptop using wires, the laptop is no longer really portable. In addition, the machine may not have enough ports to connect all the devices.
However, at some stage Bluetooth began to make inroads into the world of wireless local area networks. Some people believe that it could become a viable alternative to Wi-Fi. In my opinion, the technologies are complementary and although similar, they have different applications.
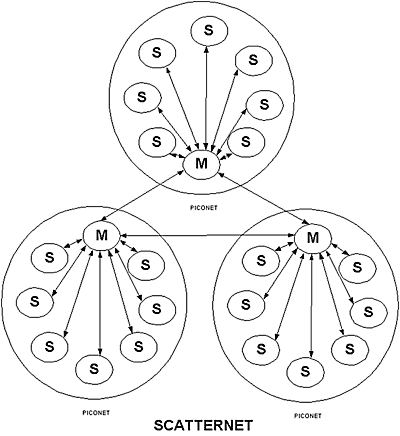
Bluetooth technology is based on piconets consisting of a primary unit and up to seven secondary units located within 10 meters of the primary unit. Piconets can be united into scatternets. The primary unit communicates with the secondary units; there is no direct communication between secondary units.
Fig. 1
Bluetooth devices operate on an unlicensed frequency band between 2.4 to 2.4835 GHz. To avoid interference with other devices operating on the same band, the technology uses a frequency hopping algorithm with 1600 frequency hops per second.
The time during which devices operate in a certain frequency is called a time slot and is 625 microseconds in duration. Units in a piconet change frequency at the same time on command from the primary unit, based on a pseudo-random hopping sequence. The frequency band is broken up into 79 channels spaced 1 MHz apart. Data is transmitted in frames, which can span 1, 3 or 5 slots.
There are two types of connection: ACL (asynchronous connectionless) and SCO (synchronous connection-oriented).
The first type of connection is used to transfer data that can be handled at any time. A secondary unit can have only one ACL connection to the primary unit.
The second link type is used for transferring data in real time, e.g. for transmitting voice data. A secondary unit can have up to 3 SCO links with the main unit, each with a rate of 64 kb/sec.
The Bluetooth specification divides Bluetooth devices into three groups:
- Class 1 100 mW 100m
- Class 2 2.5 mW 10m
- Class 3 1 mW 1m
Most Bluetooth devices are Class 2 or Class 3.
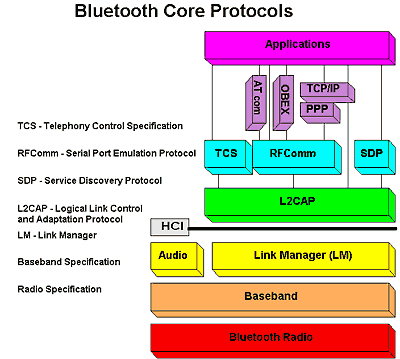
The protocol stack looks like this:
Further details can be found in the Bluetooth core specification.
Security Mechanisms
According to the specification, user information can be protected by encrypting transmitted data, while the access code and the packet header are transmitted over an unencrypted channel. Data is encrypted using the E0 stream cipher.
Attacks at the communication link level are therefore clearly possible.
Bluetooth can operate in one of three Security Modes:
Security Mode 1 – unprotected (no security)
In this mode, no encryption or authentication is used, while the device itself operates in a non-discriminating, i.e. broadcasting (promiscuous) mode.
Security Mode 2 – application/service based (L2CAP)
In this mode, once a connection is established, Security Manager performs authentication, thereby restricting access to the device.
Security Mode 3 – link-layer PIN authentification/ MAC address encryption.
Authentication is performed prior to a connection be established. Although transparent encryption is used, even in this mode the device can be compromised.
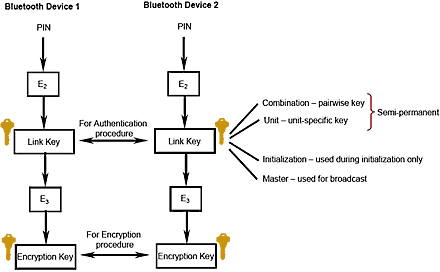
Bluetooth security is based on the generation of keys using a PIN code, which can be 1 to 16 bytes in length. Most devices currently use 4-byte PINs.
First, the E2 algorithm is used to generate a 16-byte Link Key based on the PIN code.
Then an Encryption Key based on the Link Key is calculated using the E3 algorithm.</p.
The first key is used for authentication, the second for encryption.
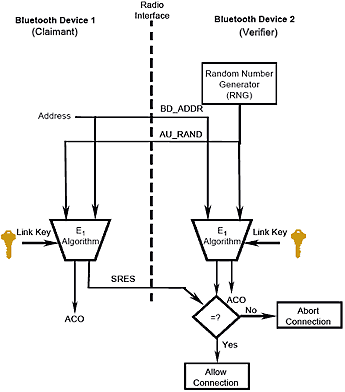
The authentication process is as follows:
- The device initiating the connection sends its address (BD_ADDR). This 48-bit address is unique, like a network adaptor’s MAC address. A device’s manufacturer can be determined by this address.
- In response a random 128-bit challenge sequence is sent (AU_RAND).
- Both devices generate an authentication response string called SRES based on BD_ADDR, Link Key and AU_RAND.
- The device trying to establish the connection sends its SRES.
- The other device compares the SRES received with its own and if the two strings match, establishes a connection.
Although the PIN code is not transmitted openly, it can be cracked if BD_ADDR, AU_RAND and SRES are intercepted.
Types of Bluetooth Attack
BlueBug
This vulnerability allows an attacker to perform unauthorized actions on a Bluetooth-enabled device.
Under ideal conditions, a BlueBug attack takes only a few seconds. The distance from the victim’s device to the attacker’s device during the attack is limited by the transmitting power of class 2 Bluetooth radios, which is, as mentioned above, 10-15 meters. A directional antenna can be used in order to increase the range.
Since some telephones allow for the issue of AT commands, an attacker can perform the following actions:
- initiate a phone call
- send SMSs to any number
- read SMSs from the phone
- read and write phonebook entries
- configure call forwarding
- etc.
Blueprinting
Blueprinting can be used for accessing the details of Bluetooth-enabled victim devices. As mentioned above, each Bluetooth device has a unique address. This address consists of 6 bytes (usually given in a form similar to that of MAC addresses MM:MM:MM:XX:XX:XX). The first three bytes of this address (the M-bytes) refer to the manufacturer of the chipset. Unfortunately, in the case of the remaining three bytes (the X-bytes), the situations is not as simple and it’s not possible to identify the device model 100%.
All Bluetooth-enabled devices have a range of services. The list of services can be obtained via the service discovery protocol (SDP). The device can be queried which results in information in a specific format which can then be used to identify the device model.
BlueSmack
BlueSmack is a DoS attack that can be conducted using standard tools that are shipped with Linux Bluez.
BlueSmack is similar to a well-known attack which was used to attack early versions of Microsoft Windows 95. At L2CAP level it’s possible to request an echo from another Bluetooth device.
As with the ICMP ping, the idea of the L2CAP ping is also to check connectivity and to measure roundtrip time on an established link. With the help of the l2ping utility that ships with the standard BlueZ distributive, he user can specify the length of packets to be sent. To achieve the desired result, the -s option can be used to specify a size of about 600 bytes.
BlueSnarf
This is is probably the best known type of Bluetooth attack. The attacker uses the OBEX Push Profile (OPP), originally developed for exchanging business cards and other objects. In most cases this service does not require authentication. The BlueSnarf attack conducts an OBEX GET request for known filenames such as ‘telecom/pb.vcf’ (the phone book) or ‘telecom/cal.vcs’ (the calendar file). If firmware on the victim device has been incorrectly implemented, the attacker is able to gain access to all files on the victim device.
BlueSnarf++
This attack is very similar to BlueSnarf. The main difference is the method used by an attacker to gain access to the victim device file system. BlueSnarf++ gives the attacker full read/write access via the OBEX Push Profile. If an OBEX FTP server is running on the device, a connection can be established via the OBEX Push service without pairing.
The attacker can view all files in the file system (using the ls command) or even delete files (the rm command). The attacker is also able to perform actions on any memory installed in the device, including memory extension cards such as Memory Stick or SD cards.
HelloMoto
This is a combination of BlueSnarf and BlueBug.
This attack exploits incorrect processing of ‘trusted device’ handling on some Motorola phones.
The attacker initiates a connection using the OBEX Push Profile and mimics sending a vCard. The send process is then interrupted, but the attacker’s device remains on the trusted device list on the victim’s phone. Using this entry on the trusted device list, the attacker is able to connect to the headset profile without authentication. Once a connection is established, the attacker is able to take control of the device by using AT commands.
BlueBump
This attack utilizes social engineering. The idea is to establish a trusted connection with the victim device. This can be achieved by sending a business card in order to make the recipient perform authentication. The attacker keeps the connection open but asks the victim to delete the link key for the attacker’s device. The victim is not aware that the connection is still active. The attacker then requests re-generation of the link-key. As a result, the attacker’s device gets a new entry on the list without authentification. The attacker then has access to the victim device until the key is deleted.
BlueDump attack
In this case the attacker needs to know the BDADDR of a set of paired devices. The attacker spoofs the address of one of the devices and connects to the other. Since the attacker has no link key, when the victim device requests authentication, the attacker’s device will respond with an ‘HCI_Link_Key_Request_Negative_Reply’, which will, in some cases, cause the target device to delete its own link key and go into pairing mode.
BlueChop
The purpose of this attack is to disrupt an established piconet by using a device that is not part of the network. This attack is based on the fact that the primary unit supports multiple connections that can be used to create an extended network (a scatternet). The attacker spoofs the address of a random device that is part of the piconet and links to the primary unit, disrupting the piconet.
Research, or New Year War-nibbling
The run-up to New Year, the most important Russian holiday, is an excellent time to conduct Bluetooth research. Shopping centers are crammed with customers looking for presents for their loved ones. This makes shopping centers an ideal arena for investigating how many Bluetooth devices are in open (discoverable) mode, and which of these devices have vulnerabilities. Best of all, this can be combined with present shopping!
My friend and I went shopping, and took a laptop with a Bluetooth adaptor with us. The equipment we used for our research is listed below:
- A Sony Vaio fxa 53 laptop computer.
- SuSE 10.0 OSS.
- a PCMCIA Bluetooth adapter
- btscanner 2.1
We visited several shopping centers and collected the data below.
Devices (mobile phones and PDAs) can operate in discoverarable or non-discoverable mode. It is possible to scanning non-discoverable devices using a brute force approach (trying a large number of different addresses). However, we did not do this, and scanned only devices in discoverable mode.
In total, 194 devices were detected, mostly mobile phones. Figure 6 shows a breakdown of these devices by manufacturer. Nokia and Sony-Ericsson dominate, and this is borne out by other studies.
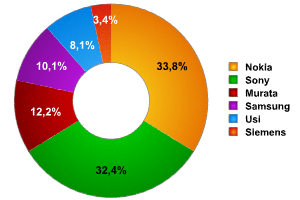 Fig. 6
Fig. 6
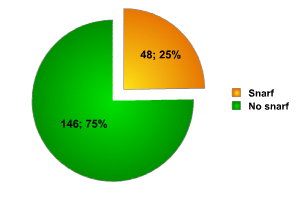 Fig. 7
Fig. 7
These devices which are most commonly used are also the most vulnerable to the commonest Bluetooth attacks. The Btscanner program showed that 25% of all devices scanned were vulnerable to the snarf attack.
Additionally, 25% of users of the devices detected accepted files transmitted to their devices.
This brings us to the sad conclusion that most users don’t even think about security, and only realize that it is an issue when they fall victim to an attack.
Failure to consider security issues could lead to serious safety problems. Bluetooth-enabled cars are already on the market; if a car’s on-board computer was penetrated, this could put the lives of driver, passengers and the surrounding public at risk.
Additionally, unprotected mobile devices make it possible for malicious code to spread extremely quickly, which could, in turn, lead to an epidemic.
Protection
- Set the device to non-discoverable mode.
- Enable PIN-based authentication.
- Use antivirus software
Leading antivirus vendors already have products for mobile devices. Kaspersky Lab itself offers products such as Kaspersky Mobile for Symbian smartphones (available in the near future) and Kaspersky Security for PDA.
Use additional software(Blooover, Blooover II, BT Audit)
Blooover is a free application written in Java. It can be used only if the phone supports J2ME MIDP 2.0 VM with JSR-82 API. Such devices include Nokia 6600, Nokia 7610, Sony Ericsson P900 and Siemens S65. Essentialy, Blooover is a vulnerability scanner that can be used to check a mobile phone for vulnerability to certain attacks. Blooover was first released in December 2004 and has since been downloaded 150,000 times. Blooover II, which is able to detect additional attacks, was released in December 2005.
BT Audit scans open RFCOMM channels and L2CAP PSM and generates reports on their status.
Further Reading:
- www.trifinite.org
- www.shmoo.com
- www.bluetooth.org
- www.bluez.org
- www.atstake.org



















Bluetooth, Bluetooth Security and New Year War-nibbling