
It happens that malware writers and other miscreants in the digital world put messages in their malware. Sometimes they do it just for the “lulz”, sometimes to insult a person who hampers their criminal business, sometimes to deliver information to the guys on the other side who oppose them. We hope the case described in this blogpost falls into the first category, i.e. funny message. At least it seemed funny for us.
Our first research into PlugX was published in 2012 – since then this remote access tool (RAT) has become a well-known instrument used in a series of attacks all over the globe targeting multiple industry verticals. PlugX has been detected in targeted attacks not only against military, government or political organizations but also against more or less ordinary companies. In 2013, we discovered that the Winnti group responsible for attacking companies in the online gaming industry has been using the PlugX remote administration tool since at least May 2012.
This time, looking through some anomalous PlugX samples, we stumbled upon one specimen that had an RC4 encoded resource inside. Actually, it turned out to be a test sample with stub settings. Luckily, it was quite easy to find the initial builder that generates such samples.
Basically, the builder compiles a handful of different PlugX droppers, including the notorious SFX RAR archives containing the PlugX trinity – a legitimate signed executable susceptible to a DLL side-loading attack, a DLL that is picked up by an executable and the payload file that maintains all the juicy stuff – the PlugX functional library, C2s and other settings.
One such trinity includes Lenovo’s RGB LCD Display Utility for ThinkPad: tplcdclr.exe, wtsapi32.dll (loaded by the application) and the “payload” file wts.chm (loaded by the DLL).
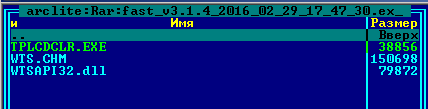 First PlugX trinity from the builder
First PlugX trinity from the builder
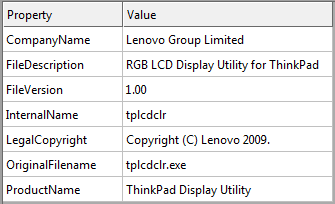 Legitimate executable from the first PlugX trinity
Legitimate executable from the first PlugX trinity
Another set of three includes a signed version of Steve Gibson’s Domain Name System Benchmarking Utility sep_NE.exe, the winmm.dll file, which the application is dependent on, and the “payload” file sep_NE.slf.
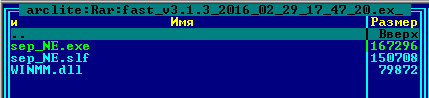 Second PlugX trinity from the builder
Second PlugX trinity from the builder
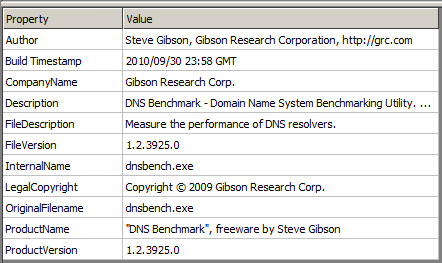 Legitimate executable from the second PlugX trinity
Legitimate executable from the second PlugX trinity
But among all the droppers that the builder generates there are two templates posing as executables, with the data maintained usually in a separate “payload” file, embedded in the initial body of the file as a resource.
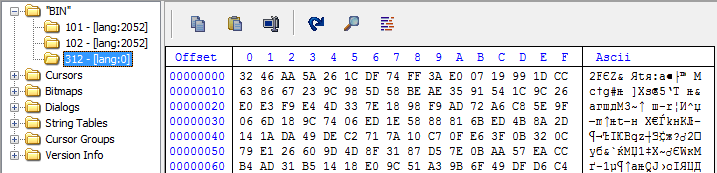 Encrypted “payload” stuff as a resource in the dropper
Encrypted “payload” stuff as a resource in the dropper
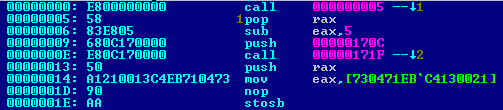
The “payload” stuff is kept in encrypted form in the file body. After decryption, this stuff looks like one of the usual PlugX “payload” files, those with easily recognizable shellcode at the beginning:
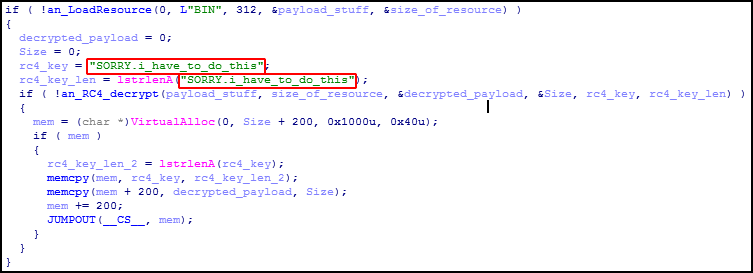
The algorithm used to encrypt the payload resource is RC4. And finally (and this is what impelled us to write this blogpost) – the RC4 key for the resource decryption – “SORRY.i_have_to_do_this“.
Hmm, interesting… That’s not the message one might expect to find in APT malware that has swamped almost every vertical in nearly every corner of the world. There have been investigations into the infamous PlugX developer in the past. We also have found a number of malware families that are related in some way to PlugX and have likely been developed by the same person. All together it seems that this person has been quite busy in generating malware for different Chinese-speaking APT groups for a long time. That’s obviously a job, already work with no room for sentiment. That’s why the text looks inappropriate here. Unless the malware writer was in a playful mood and had put this in for trolling.
There’s a second option that occurs. Since this is a dropper feature, the dropper for the PlugX could have been developed by another person, not the PlugX developer. In an ordinary cybercriminal hierarchy there are, for example, developers of a bot, ransomware, etc. and packers who create wrappers/droppers to try and allow the core malware to evade AV detection.
Probably some other person, who is not yet such a veteran in the Chinese-speaking APT world and still sees the malware writing practice as some sort of game, was just kidding around.
If you use your imagination, we’re sure you’ll be able to come to your own interesting or quirky conclusions as to how that message ended up in these PlugX droppers. In any case, we really hope this was a bit of fun and not a cry for help from some desperate person forced by circumstances to do bad things.
We detect samples generated by the builder and the builder itself with following modifications of the Gulpix family:
Backdoor.Win32.Gulpix.ajp
Backdoor.Win32.Gulpix.ams
Backdoor.Win32.Gulpix.axe
Backdoor.Win32.Gulpix.axf
Backdoor.Win32.Gulpix.axg
Backdoor.Win32.Gulpix.axi
Backdoor.Win32.Gulpix.axj
Backdoor.Win32.Gulpix.axm
Backdoor.Win32.Gulpix.axn
Backdoor.Win32.Gulpix.axo
And two heuristic verdicts:
HEUR:Trojan.Win32.Generic
HEUR:Trojan.Win32.Invader
The builder MD5 hash is 534d28ad55831c04f4a7a8ace6dd76c3.
Legitimate executables included in PlugX trinities mentioned in the blog-post:
ce2ae795117e54ca8403f86e7a3e19a7 – DNS Benchmark Utility;
d9978f95ce30e85943efb52c9c7d731b – Lenovo’s ThinkPad Display Utility tplcdclr.exe.
PlugX malware: A good hacker is an apologetic hacker




















Patrick Hunter
What made me click this is just yesterday I came across some apologetic sample myself (MD5: d146a2887e1e9b7508608fd94f777035):
The command prompt displays “Relax! Calm down. I was just checking if you belong to the FBI. Sorry for that but safety first. I know that we can trust each other now.”
Darshan G. Parab
Guys. How do you come to know about the keys used to encrypt the code and what type of algorithm is used?
Nathan
I know this offers no insight but i found it cute in a made me smile way that steve is more well known than i initially thought and as an avid listener to sn, this made me smile that one of his tools would be used in such a way. If he knows im sure he had a smile at this too.
xyz軟體
Very good!
Maria da Conceição Gíria
You are almost the better one.