
The evolution of malware targeting Steam accounts and inventory
![]() Download the full report (PDF)
Download the full report (PDF)
With astonishing annual revenues of over a hundred billion dollars, the gaming industry has in the past been compared to Hollywood’s burgeoning business, repeatedly demonstrating the influence behind its ever expanding and loyal fan base. Having an endless list of “big hit” video-games coexisting peacefully with humble but still fun-filled “indie” productions makes digital platforms not just a convenient means of purchasing new games, but also a fair one.
With over 140 million registered users and more than seven thousand games available for download, Valve’s multi-OS digital distribution platform, Steam, offers a myriad of possibilities for gamers. This includes the latest games from an always-on cloud-environment, as well as an ever-growing community of like-minded enthusiasts. Steam experiences steady growth in the number of active users registered on the platform, many of them using a credit card to buy content; willingly providing personal information and exchanging items with other network participants via in-game trades or traditional auctions. Security research has tragically ignored gaming malware in the mistaken assumption that nothing of any real value is traded there. This blind spot is being abused by cybercriminals to steal money and affect real damage!
It’s all fun and games until someone’s account gets hijacked
Organized criminal crews from all over Eastern Europe have been paying close attention to Steam’s growing user base and the security techniques and procedures offered to users by the company; waiting patiently for their opportunity. As in the majority of social networks, many profiles don’t reveal their true nature, hiding personal details and payment information behind a carefully crafted identity or digital persona; or, as Jung would put it: “A kind of mask, designed on the one hand to make a definite impression upon others, and on the other to conceal the true nature of the individual.” However, what happens when that mask unexpectedly slips? When your account and all its related, sensitive information stored becomes the ill-gotten gains of an unknown third party? Surprisingly, this nightmare turns to reality for almost 77 thousand unsuspecting users every month, according to Steam’s own statistics. Estimating the financial impact, however, is quite difficult, given that Steam is not obliged to make this information public. While several community websites exist (such as SteamSpy or SteamCompanion) to calculate how much money you have spent on your account, we couldn’t find a single one that kept historical records in order to calculate an average value. An educated guess based on available password dumps makes the value for the credentials a mere $15 USD on the black market.
However, that’s just for accessing the victim’s profile; what the bad guys do afterwards could yield even higher gains, depending on the user.
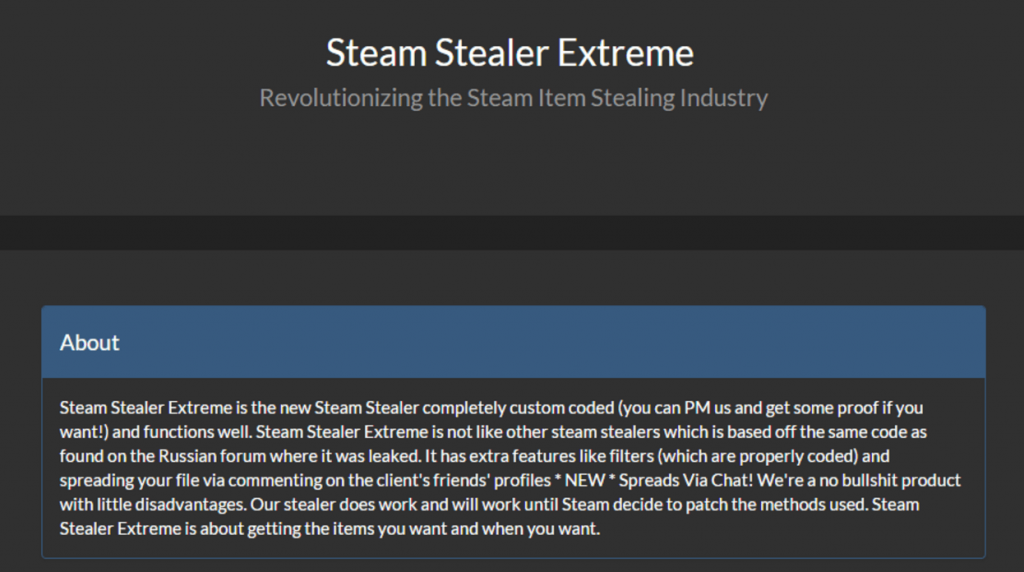
A characteristic stealer that claimed to “revolutionize” the Steam Item Stealing Industry, its website has been offline for a while now and its Twitter account is basically dead. Yet, its legacy carries on with the malware still being distributed in the wild.
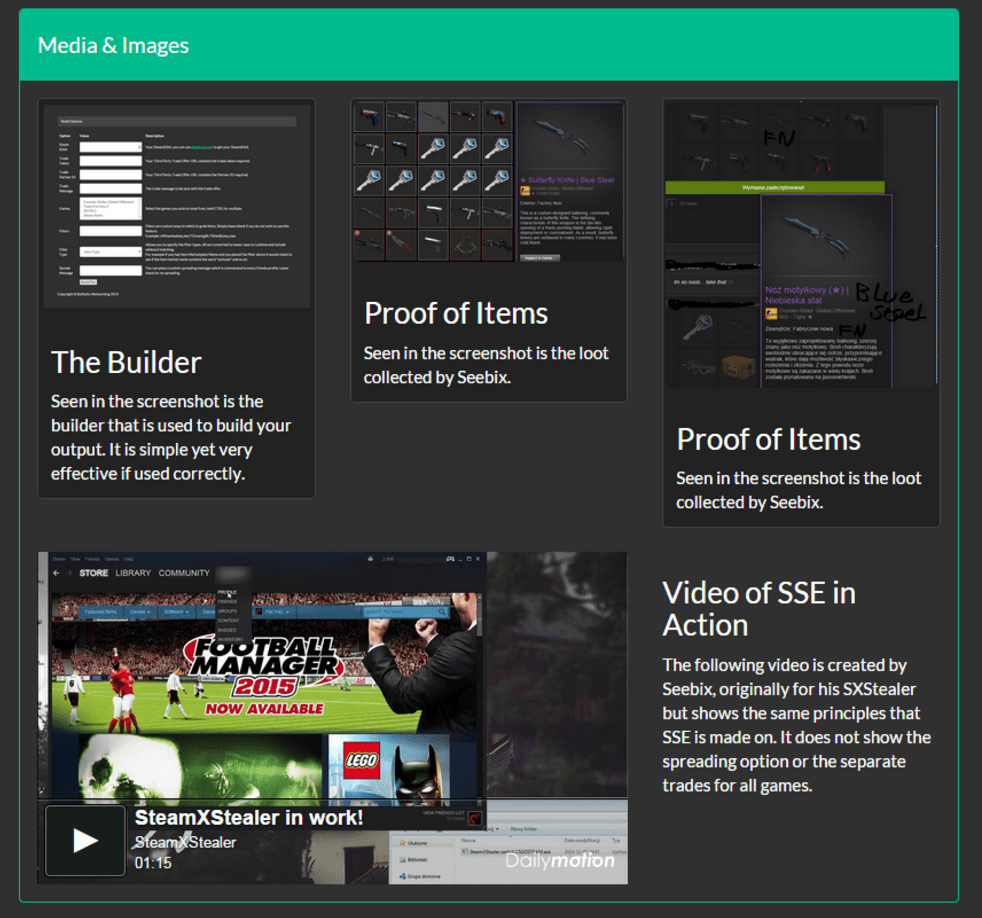
Even though phishing and spear-phishing attacks are always popular among the most active social engineers in the dark corners of the Internet, a new breed of malware, known innocently as a “Steam Stealer” is the prime suspect in the pilfering of numerous user accounts from Valve’s flagship platform. Evolving bit-by-bit from a leaked source on a remote Russian forum, stealers took off once they were proven to be extremely profitable by criminals all around the globe. Available for sale in different versions, with distinct features, free upgrades, user manuals, custom advice for their distribution, and more, stealers have turned the threat landscape for the entertainment ecosystem into a devil’s playground.
An almost perfectly-cloned website for the gaming messenger Razer Comms, which, together with TeamSpeak is one of the most popular baits used by cybercriminals.
One of the reasons behind the growth of specific malware targeting gamers has been the simplicity behind its operation and the ubiquity of its offering. The focus on selling stealers to anyone with money to spend means that a staggering number of script-kiddies and technically-challenged individuals resort to this type of threat as their malware of choice to enter the cybercrime scene.
Everything in one simple package, ready to use and with plenty of documentation for its use. Different functionality is offered as part of each Steam Stealer package, starting from $15 USD.
Adding new features is simple. The average developer just needs to select their favorite programming language and know just enough about Steam’s client design and protocol. There are many APIs and libraries available that interface seamlessly with the Steam platform, significantly reducing the effort required. It’s not uncommon for the bad guys to repurpose legitimate tools and open source libraries for their nefarious campaigns, although in this case the possibilities are just too tempting to pass on to others.
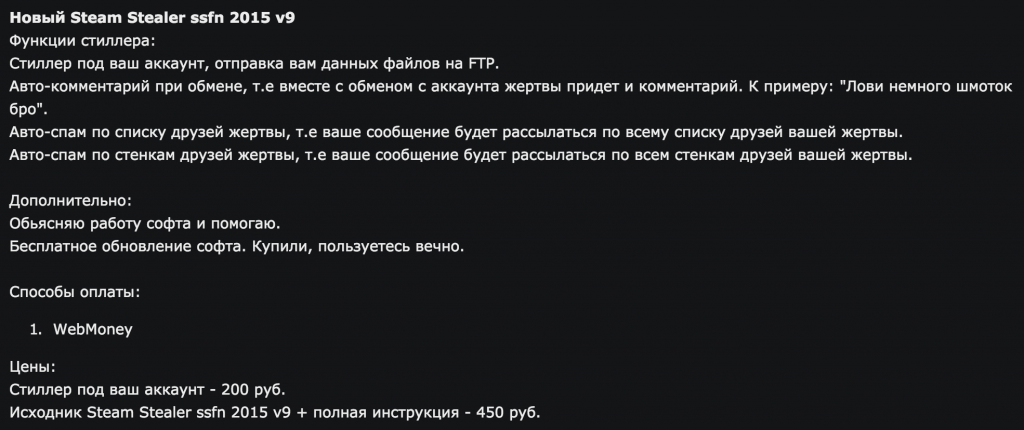
A starting price of 200 rubles ($3 USD) would get you usage rights for a credential stealer for the Steam platform. Paying 450 rubles ($7 USD), would add source code and a user manual.
Every step of the process, from the initial malware distribution to obtaining a profit after the infection is completed, is documented in one of several guides available online (at a cost, of course). In this business model everything has a price and every individual goes above and beyond to make their offer more attractive to potential customers. Malware-as-a-service is not a revolutionary practice. However, when it comes to these types of malicious campaigns we usually see prices starting in the range of $500 dollars (taking as a reference earlier ransomware-as-a-service markets).
A strong focus on Marketing is evident in the “stealing industry”.
With Steam Stealers, a ludicrously low price is usually asked of wannabe criminals for the use of the malware. For an extra cost, the full source code and a user manual is included in the package, making this scheme laughable and terrifying at the same time. Of course, the aforementioned prices represent the low end of the “industry” spectrum, but it would be hard to find any stealer being sold for more than $30 dollars. With so much competition in this niche market, it’s tough making a living as a stealer-seller without daring to go the extra mile.
Past and current trends
Reviewing how Steam Stealers have evolved from “simple” malware to flooding all corners of the Internet, we can assume that this is indeed a booming business.
In the past, there was no obfuscation whatsoever, and sometimes FTP or SMTP credentials were sent over in plain text. Gradually, improvements were introduced to the stealers as well as to the social-engineering aspect: screenshots got better, duplicate sites improved, delivery methods were more diverse and bots got better in mimicking human behavior.
A short rundown of past trends:
- Use of obfuscators to make analysis and detection harder.
- Use of file extensions hidden by default by Windows (fake ‘screensaver’ files).
- Use of NetSupport added (providing remote access to the attacker).
- Use of fake TeamSpeak servers.
- Use of automatic Captcha bypass (DeathByCaptcha and others).
- Use of fake game servers (Counter-Strike: Global Offensive most notably).
- Use of Pastebin to fetch the actual Steam Stealer.
- Use of fake screenshot sites impersonating Imgur, LightShot or SavePic.
- Use of fake voice software impersonating TeamSpeak, RazerComms and others.
- Use of URL shortening services like bit.ly.
- Use of Dropbox, Google Docs, Copy.com and others to host the malware.
Current trends are as follows:
- Use of fake Chrome extensions or JavaScript, scamming via gambling websites.
- Use of fake gambling sites, including fake deposit bots.
- Use of AutoIT wrappers to make analysis and detection harder.
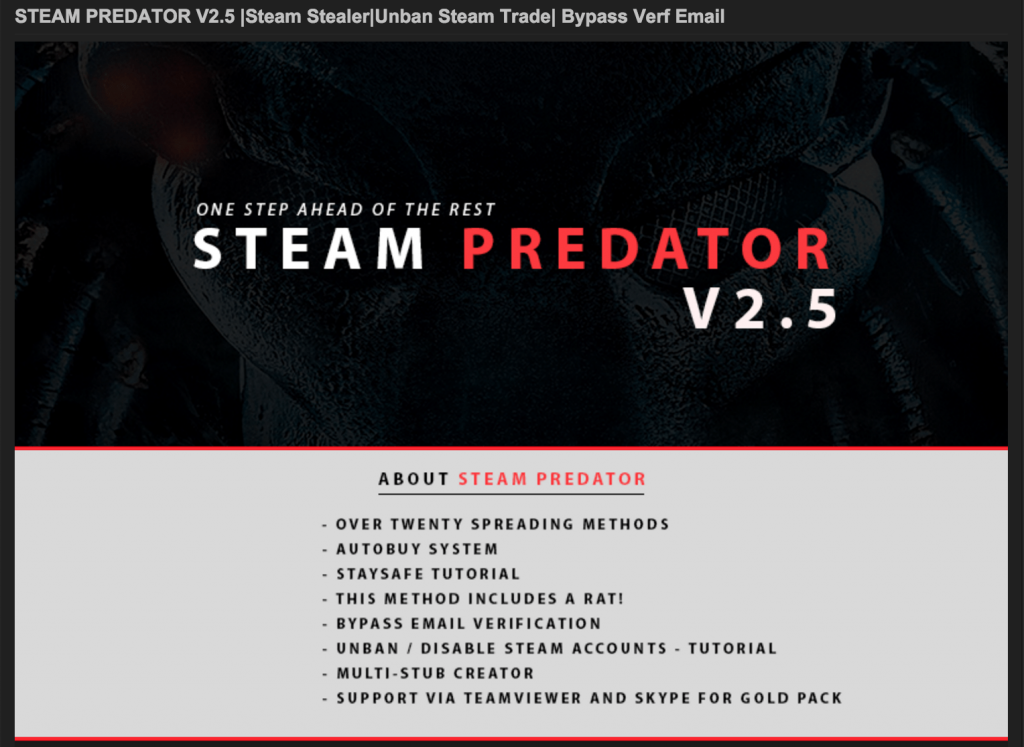
- Use of RATs (Remote Access Trojans) such as NanoCore or DarkComet.
This list may grow, as 2016 has only just begun.
![]() Download the full report (PDF)
Download the full report (PDF)
The Steam Stealing industry in numbers
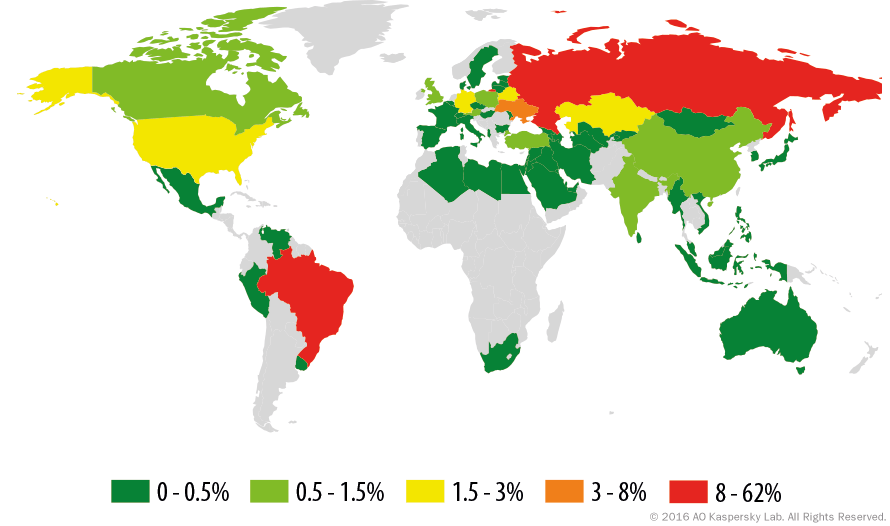
The statistics included in the following section reflect the period between January 1st 2015 and January 1st 2016, concentrating on the most prevalent malware families for Steam Stealers. However, since many detections are made by heuristics or different generic verdicts, the problem is actually much worse and it is hard to get an exact measure. The percentage of infected users is calculated only for countries with over 1,000 detections in the specified period (baseline).
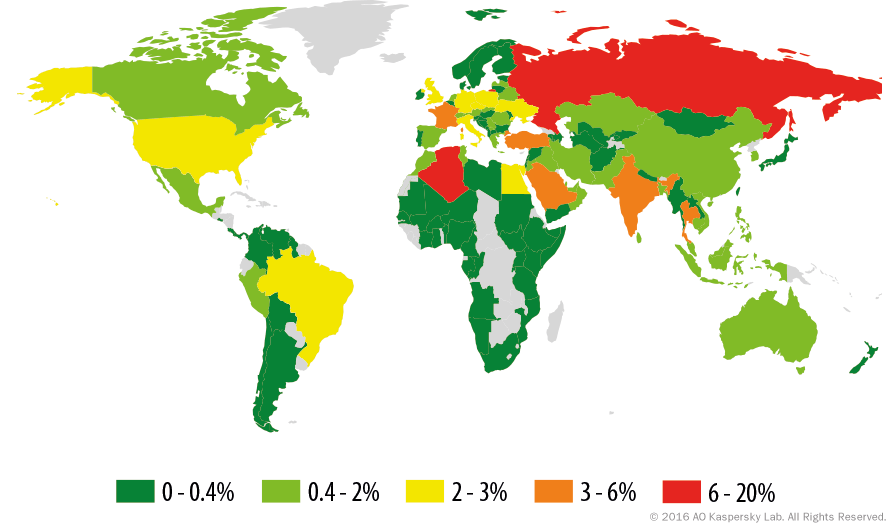
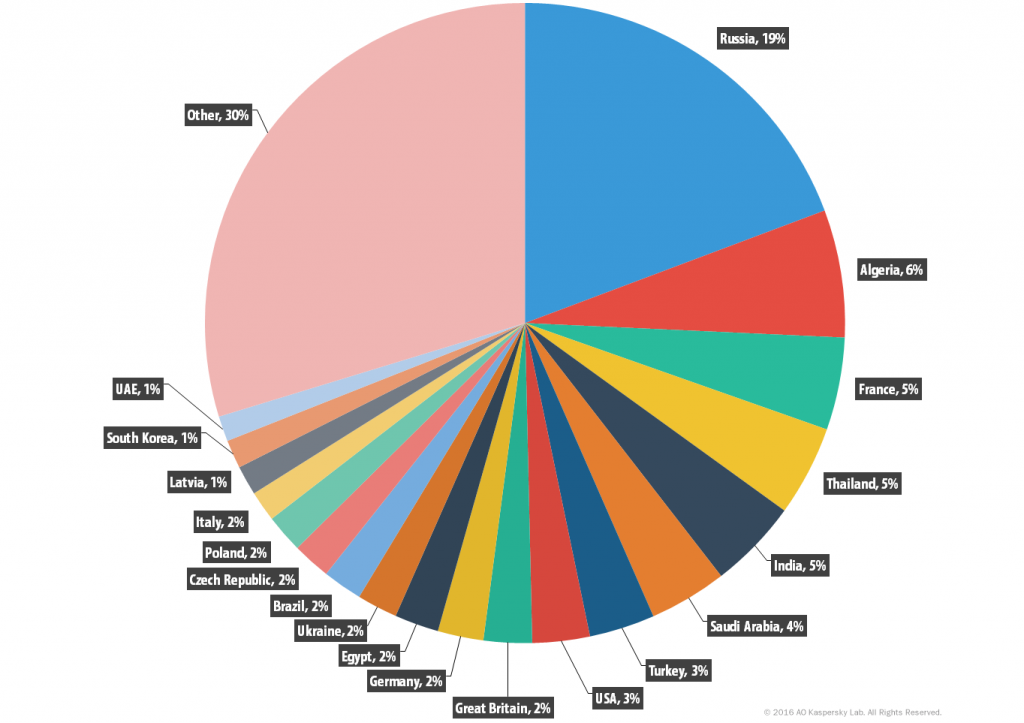
Statistics for Trojan-Downloader.MSIL.Steamilik
Trojan-Downloader.MSIL.Steamilik geography
Trojan-Downloader.MSIL.Steamilik, % of infected users
Trojan-Downloaders can download and install new malicious programs onto the user’s computer – including other Trojans, or the ever annoying adware. This two-stage infection process allows the bad guys to modularize their components and create an initial downloader with reduced functionality which can then gather the malicious contents once the environment has proved worthy.
Statistics for Trojan.MSIL.Steamilik
Trojan.MSIL.Steamilik geography
Trojan.MSIL.Steamilik, % of infected users
This broad category of Trojans contains all malicious programs that perform actions that have not been authorized by the user, such as reading information form the registry key and copying files from the system in order to send them to a command a control server owned by the cybercriminal. It’s worth noting the MSIL sub-category which represents a .NET assembly. The rise of Trojans and the increased use of Microsoft’s flagship development framework go hand in hand, making the lives of all developers (including those with a not so white hat) easier.
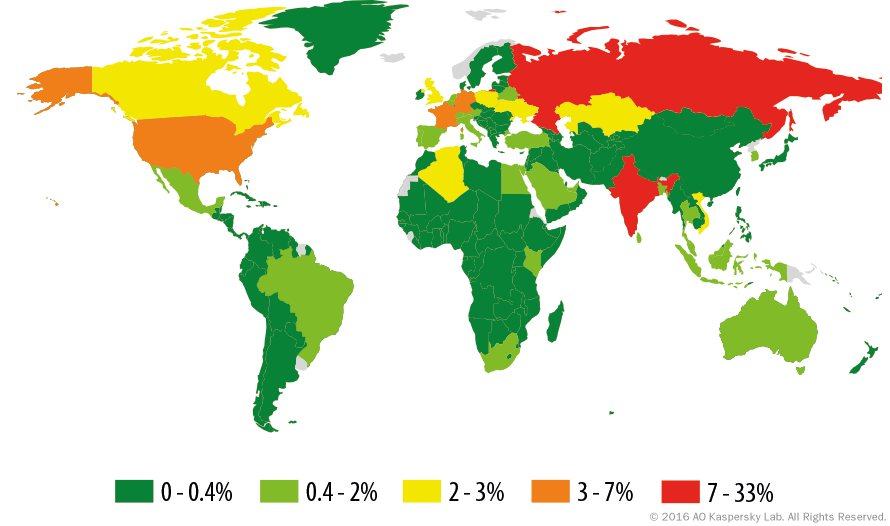
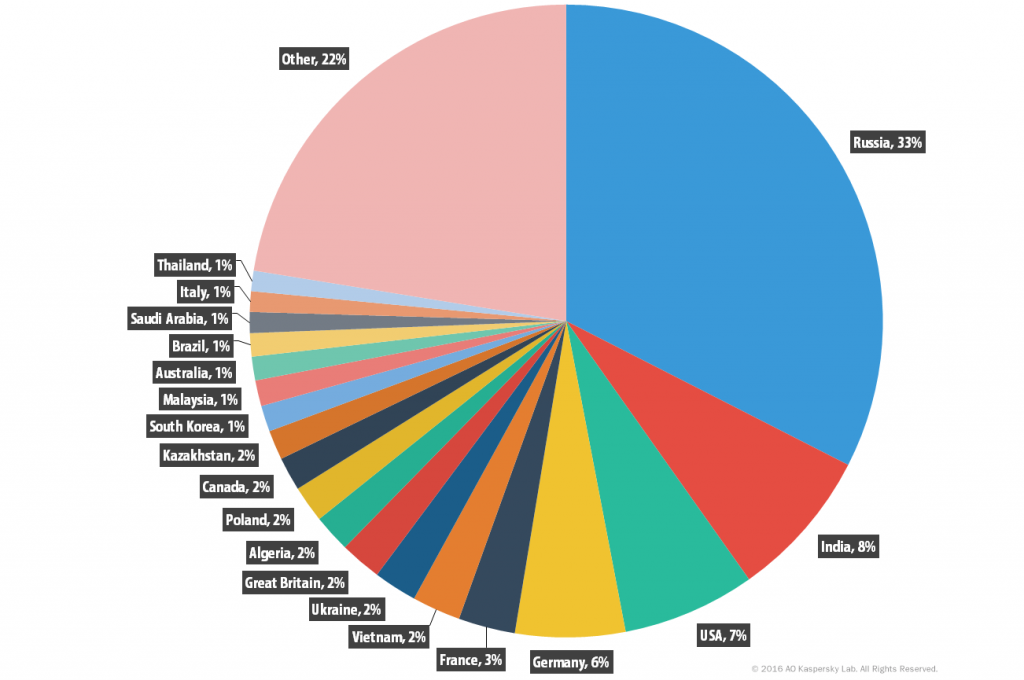
Statistics for Trojan-PSW.MSIL.Steam
Trojan-PSW.MSIL.Steam geography
Trojan-PSW.MSIL.Steam, % of infected users
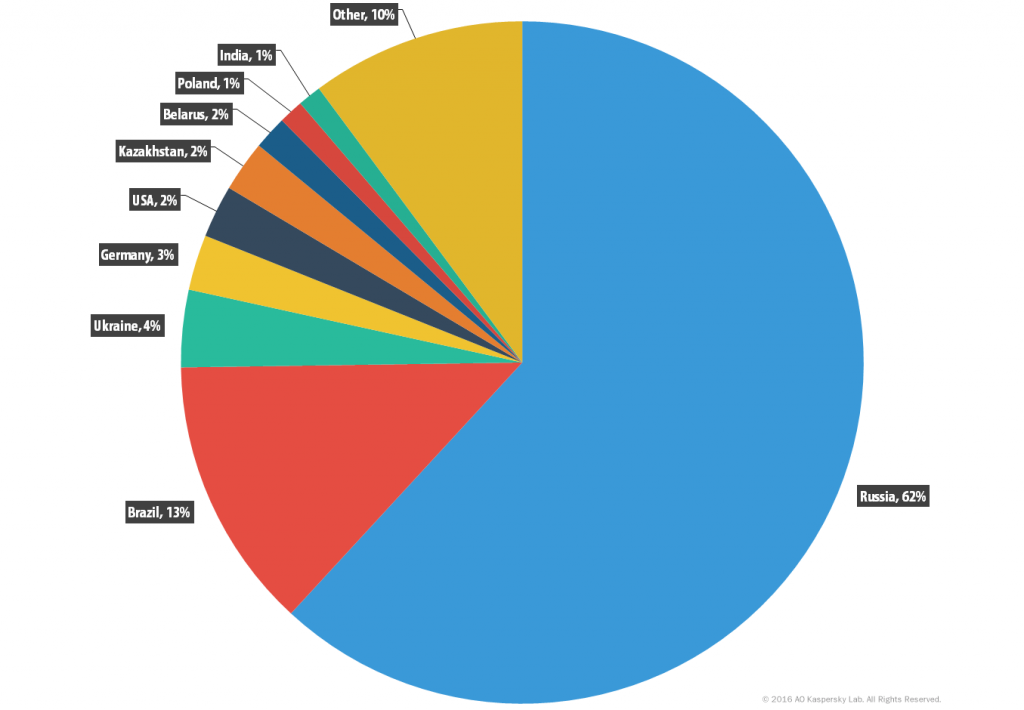
Trojan-PSW programs are designed to steal user account information such as logins and passwords from infected computers. PSW or Password Stealing Ware, when launched, searches specific files which store a range of confidential data or crawl the registry for specific keys. If such data is found, the Trojan sends it to its “master.” Email, FTP, HTTP (including data in a request), or other methods may be used to transmit the stolen data. Brazil caught our attention by taking the second place in this malware category after the Russian Federation. Latin America is certainly a growing malware ecosystem and gamers are not forgotten.
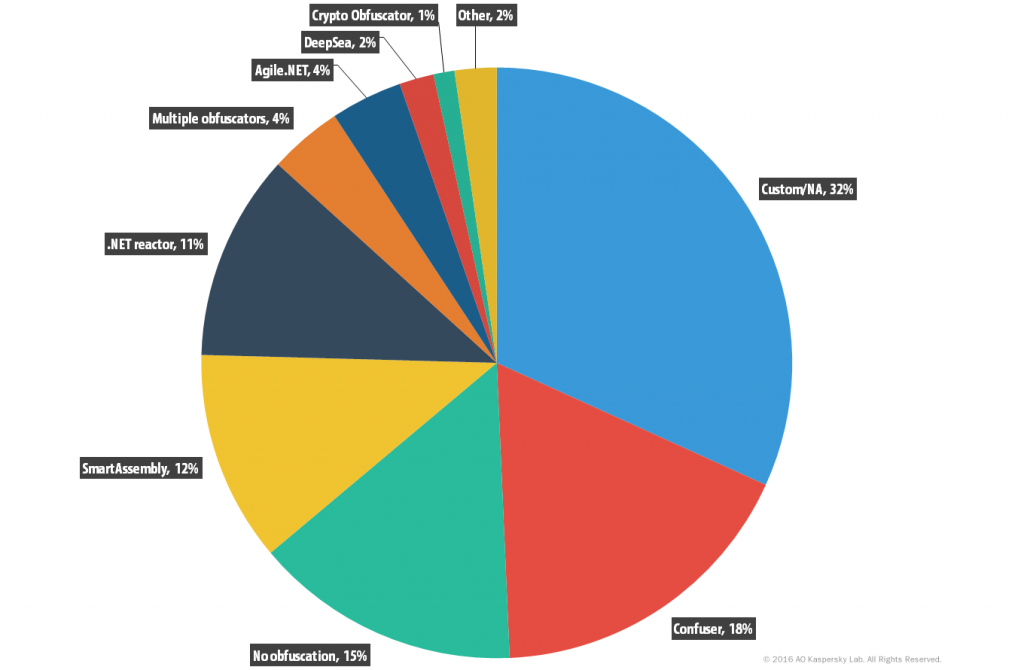
With an extensive range of obfuscators used to protect their intellectual property, together with a decline in detection by security solutions, cybercriminals resort to open source projects such as ‘ConfuserEx’ (the successor of the infamous Confuser project) or even commercially available obfuscators for the .NET Framework such as SmartAssembly. For calculating the previous statistics regarding obfuscators, a group of over 1,200 samples collected via different means was used. All the hash values for this collection will be uploaded to our publicly available IOC repository.
Valve’s counter-measures
Valve has acknowledged the problem, but even if there has been a progressive improvement in the number of protective measures implemented, Steam Stealers are still rampant and many users will at some point find themselves wondering what went wrong. Among the new security measures there are several that have been adopted network-wide and others which you can easily configure for your account to prevent this type of incident and enjoy a secure gaming session:
- Two-factor authentication either by email or mobile application.
- Blocking URL’s throughout Steam.
- Nickname censorship (Steam/Valve).
- Captcha on trades (briefly), and then bypassed.
- Limited accounts introduced.
- Steam e-mail confirmations for utilizing the market and trading items.
- Verifying e-mail address.
- $5 USD purchase to combat ‘free abuse’ accounts (expanded on limited accounts).
- Information about who you are trading with (record).
- Market will become blocked when logging in from new devices, changing your profile password etc.
- Steam mobile trade confirmations.
- Steam account recovery via phone number.
- Restrict chat from users who do not share a friends, game server, or multi-user chat relationship with you.
- More restrictive block referral of spam and scam sites.
- Trade hold duration (15 days).
In terms of preventive measures, we recommend users familiarize themselves with Steam’s updates and new security features, and enable two-factor authentication via Steam Guard as a bare minimum. Bear in mind that propagation is mainly (but not solely) done either via fake cloned websites distributing the malware, or through a social engineering approach with direct messages to the victim. Always have your security solution up to date and never disable it; most products nowadays have a “gaming mode” which will let you enjoy your games without getting any notifications until you are done playing. We have listed all the options Steam offers users to protect their accounts. Remember that cybercriminals aim for numbers and if it’s too much trouble they’ll move on to the next target. Follow these simple recommendations and you will avoid becoming the low hanging fruit.
And if you think the current state of steam stealers is bad, we get the shivers imagining what we will face after Gaben releases Half Life 3. Stay safe, game on, and enjoy Steam!
“All your creds are belong to us”























David Westlake
Even as a paying customer, I would still like to express my gratitude for the good work you do at Kaspersky. You guys rock!!
Vercingetorix
Interesting, and the advice on using Steam two-factor authorization is important. However, when I somehow got a Steam password stealer on my PC the Kaspersky tools couldn’t find it. To be fair, neither could those of any other anti-malware vendor.
SO – an article on how to identify such malware would be a lot more useful.