
A long time has passed since the infamous virus writer Benny from the 29A group released to the world his proof of concept malware ‘Donut‘, targeting .NET executables and written in a combination of assembly and Microsoft intermediate language (MSIL). Even though his creation wasn’t noticeably revolutionary nor harmful, it demonstrated the effectiveness and simplicity of relying on Microsoft’s newly released .NET framework for nefarious purposes. It wasn’t until we met ‘Sharpei’ that we were presented with malware truly written in a .NET compliant language such as C#. Opening Pandora’s box, the evils of the .NET and PowerShell ecosystems began in quite an innocent manner, gradually evolving into the convoluted cybercrime scene that we’ve come to know nowadays.
We recently had the privilege of presenting our .NET and PowerShell malware research at the emblematic Virus Bulletin conference, held once again in the fascinating city of Prague. Interestingly enough, in the year 2001 at this very same conference and location, researchers Richard Wang and Philip Hannay presented on a thought provoking topic: ‘MSIL For the .NET Framework: The Next Battleground?’, proposing a future in which the .NET Framework would enable a whole new breed of cybercrime. Also depicted in Péter Ször’s must read book ‘The Art of Computer Virus Research and Defense’, the prediction that JIT Dependency and Microsoft .NET Viruses would become a worrisome and ever-evolving threat slowly but surely became a reality. Nowadays, we are constantly talking about malware and not simply ‘viruses’ anymore, mainly due to the amount and variety of malicious code that we have to deal with and analyse everyday. The diversity of quality of malware is undoubtedly increasing, enough to warrant the usage of new terminology to refer to each malicious creation by its behavior and demonstrable characteristics. However, how much has this particular threat evolved in recent years?
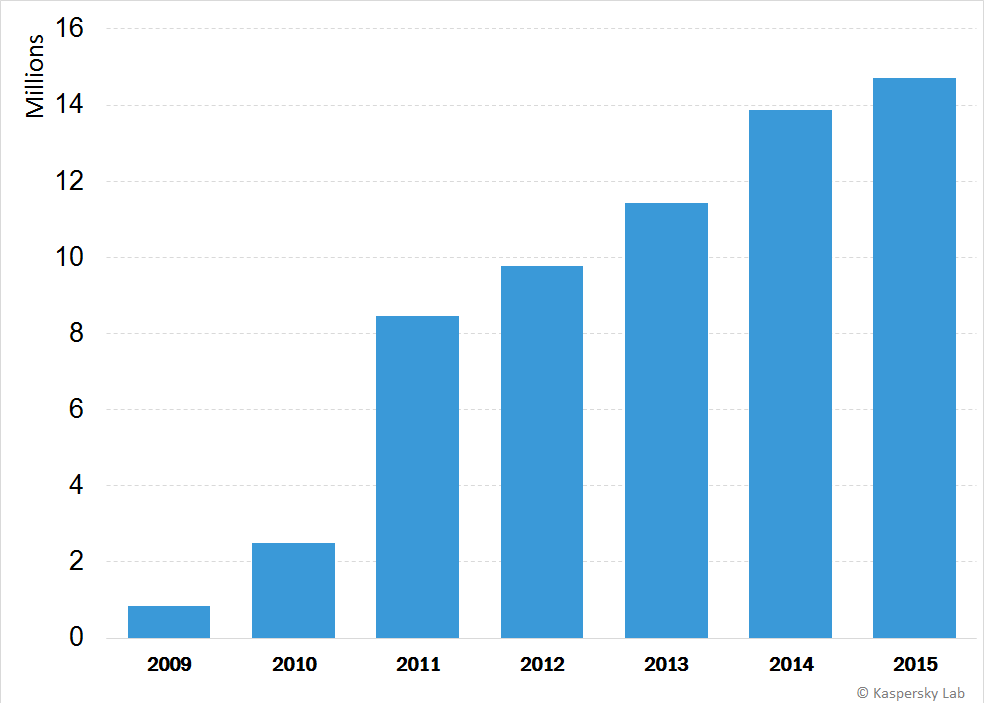
From the year 2009 until 2015 there has been a 1600% growth in the number of .NET malware unique detections.
Gone are the days where a programming-savvy malware writer would lock herself up in a dark basement, looking at a glaring screen filled with assembly code. A challenge to the status quo has succeeded and now the self-titled cybercrime industry has become a booming business with criminals all around the world wanting to jump on the bandwagon and get a piece of the action. With a greater availability of high-level programming languages each day, some even taught in high school and university-level courses thanks to their simplicity, lots of curious ‘wannabe criminals’ with dubious intentions find themselves surprisingly equipped to reach into the depths of the Internet and pull out examples of source code and step-by-step tutorials to create their next malicious campaign. Instead of wanting to showcase their technical expertise or intellectual capacity, criminals have adopted proven practices from agile software development and business administration that focus on maximizing profits while minimizing the development time and maintenance cost of these dreadful concoctions.
In 2002, Microsoft released a game-changing framework that revolutionized the software development industry and unwittingly provided malware writers with an unimaginable arsenal of weapons. While ‘script kiddies’ resorted to builders and automated environments to cobble together variations of already-available malware samples, seasoned malware writers now had access to forums with approachable lessons on how to write fresh pieces of malicious code, all with an eye to the most desirable feature of all: avoiding antivirus detection for as long as possible. Aimed to compete directly with Oracle’s JAVA platform, the .NET framework provided not only a comprehensive library of built-in functions but also an accompanying development environment capable of supporting several high-level programming languages including Microsoft’s soon-to-be-flagship C# and the evolution of Visual Basic dubbed VB .NET.
Available by default in most Windows installations, the .NET framework has become the de-facto standard for software development in Microsoft’s family of operating systems. Moreover, with the 2006 addition of the increasingly powerful PowerShell scripting framework, the interaction between .NET’s supported programming languages and scripting automation has given software developers and system administrators an easy way to interface not only with the operating system but nearly all Microsoft software, ranging from the Office suite to their crown jewel, the SQL Server database engine.
Vast amounts of ready-to-use functionality make .NET and PowerShell a deadly combination at the hands of cybercriminals. The straightforward value is immediate: developing simple yet effective applications to send spam, brute forcing credentials for virtually any service, or creating the next global malicious campaign. The added benefit: PowerShell being ubiquitously allowlisted due to its importance in everyday Windows system administration and other recurring management activities translates into increased difficulty to prevent attacks reliant on these deeply ingrained operating system components.
With access to a powerful integrated development environment (IDE) such as the newly-free Visual Studio, even application lifecycle management and rapid application development practices have gotten easier and increasingly adopted by today’s cybercriminals with aspirations of forming part of an organized industry. Clearly designated separations between programmers, designers, testers, command and control server administrators, and everyone involved in cybercriminal operations translates to maximum efficiency and, in turn, maximum profits. Computer-enabled crime and fraud have become a faithful reflection of their ‘real-life’ counterparts. With cybercrime gangs stealing millions of dollars from institutions (examples include Carbanak and gangs like the recently apprehended Svpeng), we are witnessing a paradigm shift in computer crime away from the ‘one man show’ to that of an earnest team effort. On the other side of the table, we find cooperation between private security research companies and law enforcement agencies proving paramount in combating these borderless threats.
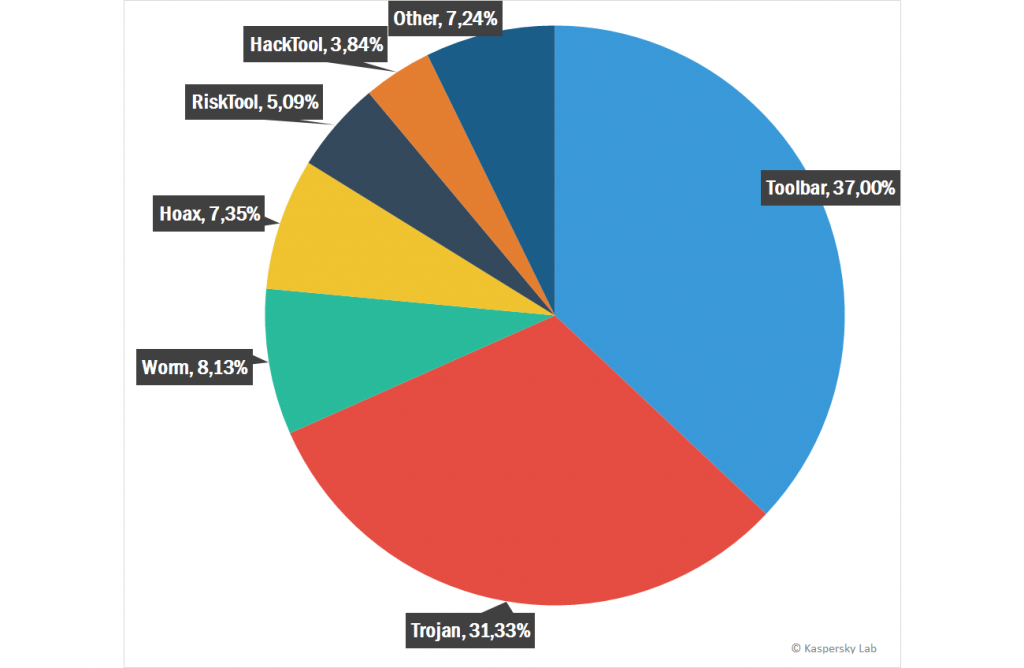
.NET malware classification by behavior.
Choosing a representative set of malware samples of the .NET and PowerShell ecosystem is a daunting task. For this opportunity we have chosen to analyse and share with our audience a Mexican ATM malware sample named ‘Ploutus’, an APT campaign found in Syria, and the latest .NET ransomware making the news, ‘CoinVault’.
Ploutus allowed criminals to extract money without authorization, stealing the amount they wanted directly from the machine without needing access to any special banking information. In a world where most of the scams are targeted at end-users, finding one that affects the banking institutions directly is not very common. This malware eventually spread out of Mexico, with variants appearing in the wild using a graphical user interface in English and even adding functionality such as sending an SMS to the ATM to make remote withdrawals.
In the case of the Syrian malware APT campaign, the usage of high level programming languages (i.e. C#) has been proven popular among attackers as they need to modify their malicious creations more rapidly to keep their ongoing attempts at infecting more and more victims. This brings the added benefit of leveraging already available source code from the underground scene. The possibility of embedding remote administration tools into the malware used for distribution enables extreme customization of the code, making this type of threat seemingly interesting for cybercriminals already proficient in the usage of social engineering for massive distribution of their contraptions.
Our ‘usual suspects’ lists wouldn’t be complete without a ransomware case, and what better than CoinVault, a malware that infected more than 1500 Windows PCs in over 20 countries. .NET malware still has a long way to go to become king of the hill, it’s relatively easy to disassemble and reverse engineer a newly detected threat, making the analysis process quicker than with other types of malware. So, are we reaching the end of the ransomware nightmare? Fortunately, there’s one less ransomware to worry about for now, but the bigger problem still requires a lot of work for every party involved. An effective cooperation between private companies and law enforcement is a must when dealing with borderless cybercrime such as digital extortion and here we have taken a step in the right direction.
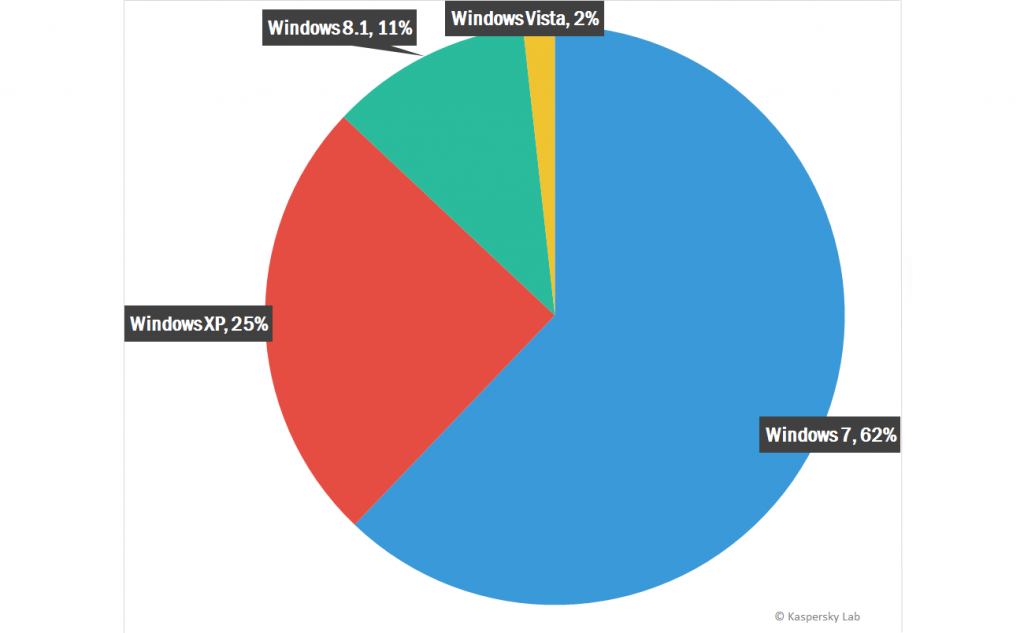
Most attacked operating systems by malware written in any .NET compatible language.
The number of malware samples created either in any CTS compliant .NET language or PowerShell is increasing, and while it’s currently being used solely to target Windows systems, we could soon be witnesses of a reality where a cross-platform infection is not just an academic proof-of-concept but a possible and dangerous threat. With the timely release of the source code for core components of .NET, alternative frameworks such as the Mono Project could easily be providing an extensively cross-platform mean to execute .NET applications. Even in the burgeoning .NET for mobile ecosystem, an interesting malicious sample was recently spotted in the wild. Supported by the Android version of the Mono framework, it shows that the bad guys never stop testing new fertile grounds for business opportunities.
Targeted malicious campaigns and advanced persistent threats are being announced non-stop nowadays and with the easiness provided by high level programming languages such as C# and VB .NET, the coordination between a large group of developers focused on compromising a specific set of targets could reap the benefits of software engineering practices applied to cybercrime. Even if a persistent threat needs an “advanced” component in order to be considered as such, the definition might become more flexible considering that not only one technology would be used in order to compromise a desired mark, making the combination of high level programming languages, scripting, and any other available means a recipe for true malware development modularization. From code versioning directly available in the developer’s IDE to continuous build automation, the organized cybercrime industry can give a whole new definition to the phrase ‘malware as a service’.
As security researchers and malware analysts, the extensive amount of source code available from the analysis of in-the-wild malware samples and ‘hacking’ tools, will allow us to get a glimpse at the previously hidden internals of the malware world, one that was purely written in assembly and now is becoming available for the entire community to learn from. With each new malicious sample representing a challenge in itself, a common set of characteristics arise between them all, shaping our job into a puzzle solving reality where we abstract from any technology used in the conception of malware until we are ready to act, analyze and defend. As the poet, novelist, and natural philosophy Johann Wolfgang von Goethe expressed, “Knowing is not enough; we must apply. Willing is not enough; we must do.”
We would like to kindly thank the Virus Bulletin conference organizers (especially Martijn Grooten) for giving us the opportunity to share our research with the community and to publish it here for a broader audience.
Santiago Pontiroli and Roberto Martinez, ‘The TAO of .NET and PowerShell Malware Analysis’, October 2015, Virus Bulletin. Copyright is held by Virus Bulletin Ltd, but is made available on this site for personal use free of charge by permission of Virus Bulletin.
You can download the full PDF paper here.
The rise of .NET and Powershell malware






















Jeffrey P Snover
For information about how PowerShell addresses these concerns and many others, please check out the team blog:
PowerShell Loves the BlueTeam at: http://blogs.msdn.com/b/powershell/archive/2015/06/09/powershell-the-blue-team.aspx
Cheers!
Jeffrey Snover
MSFT Technical Fellow