
Some months ago we wrote a blog post about CoinVault. In that post we explained how we tore the malware apart in order to get to its original code and not the obfuscated one.
So when were contacted recently by the National High Tech Crime Unit (NHTCU) of the Netherlands’ police and the Netherlands’ National Prosecutors Office, who had obtained a database from a CoinVault command & control server (containing IVs, Keys and private Bitcoin wallets), we were able to put our accumulated insight to good use and accelerate the creation of a decryption tool.
We also created a website and started a communications campaign to notify victims that it might be possible to get their data back without paying.
To build the decryption tool we needed to know the following:
- Which encryption algorithm was being used?
- Which block cipher mode was being used?
- And, most importantly, what malware are dealing with?
There was obviously no time for “hardcore” reverse engineering, so the first thing we did was run the malware sample to see what it was doing. And indeed, just as we thought, it was another CoinVault sample. The next thing we did was open the executable in a decompiler, where we saw that the same obfuscation method was used as described in the post. So CoinVault it is. However, we still didn’t know which encryption algorithm and block cipher mode it was using.
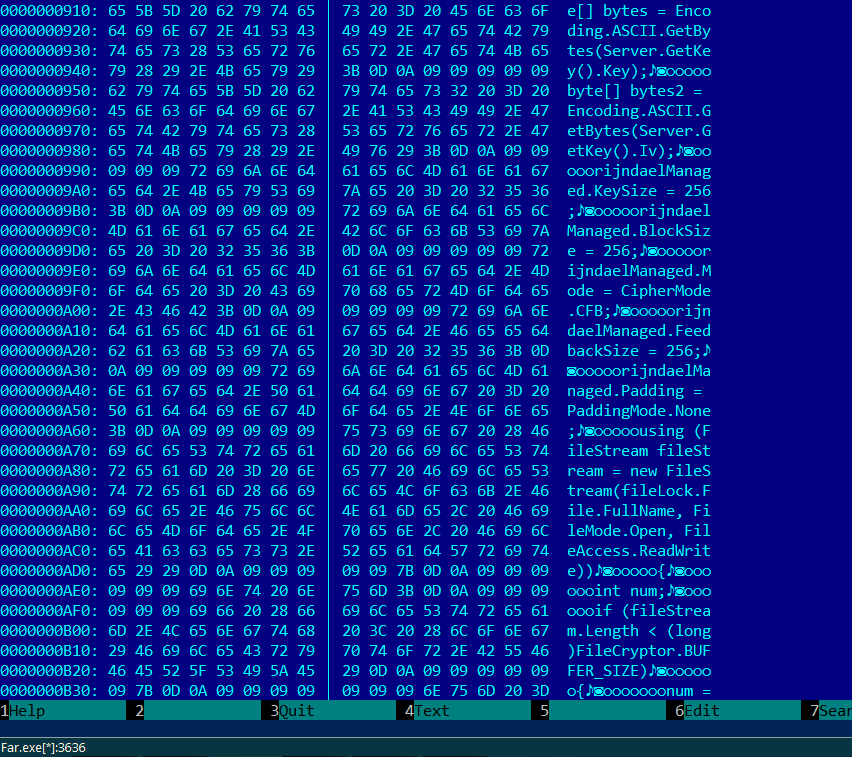
But luckily we have a sandbox! The nice thing about the sandbox is that it executes the malware, but also has the ability to trace virtually anything. We can dump files and registry changes but in this case the memory dumps were the most interesting. We knew from the previous CoinVault samples that the malware was using the RijndaelManaged class, so all we had to do was search in the memory dump for this string.
And here it is. We see that it still uses AES, although not the 128-bit block size anymore, but the 256-bit one. Also the block cipher mode has changed from CBC to CFB. This was all the information we needed to write our decryption tool.
To see if you can decrypt your files for free, please go to https://noransom.kaspersky.com
Challenging CoinVault – it’s time to free those files





















H Verduijn
My laptop has a new windows 7 install. My encrypted files have been backuped on a external harddisk. How can i decrypt those files?
Guenard
Hi,
If you want to decrypt your files, you must have the “Bitcoin wallet adress” like for exemple “128Xofjjkshfggso8dhh7hshsh7” display on the bottom-right of the CoinVault window.
unfortunately, if you have re-install Windows without noted these “Bitcoin wallet adress”, you can’t decrypt the files.
See the description for decrypt the files here : https://noransom.kaspersky.com/static/convault-decrypt-manual.pdf
Rob
I had to reinstall windows and unfortunately i did not save the bitcoin adress.
Will there be a way in future to decrypt the files without the bitcoin adress?
rb29
same here, didn’t think to save a screenshot of the ransom note but I still have all of the files. They should make a tool to scan a single file and try all known keys.
Darkstar
I second the idea of a tool to try all known keys. I still have my files but not the bitcoin address.
Guenard
Hi !
I have my files which are crypted by CoinVault v1.0.1.1 so I’m happy about this article.
I used your decryption tool to decrypt my files but when the files is higher than 2048Ko, the tool doen’t decrypt totally the file…
After decrypting, we have a new file with a 2048ko size and we can’t open it…
It work perfectly with the others files under 2048ko sizes.
There is a tip to decrypt files higher than 2048ko ? could you modify the tool for decrypt these files ?
THank you for your help !
Thierry
Geoff
I have been hit by the virus which encrypted all my files with an .ECC extension. On each folder is a file with the same details inside as below:- Ive blocked the Public Key out but thought there might be something in the message that might help . My timer has run out, I’ve eliminated the virus but will not be able to use the key now to restore my files through their site. Plus the cost has escalated to 1000 bitcoins. What is the likelihood that an decryption tool will be available for all these viruses at some point, is it possible to reverse engineer the encryption or will it be possible in future. I understand you have Coinvault decrypter but I am not sure which virus I was hit by specifically so no idea if this will help.
All your documents, photos, databases and other important files have been encrypted
with strongest encryption RSA-2048 key, generated for this computer.
Private decryption key is stored on a secret Internet server and nobody can
decrypt your files until you pay and obtain the private key.
If you see the main encryptor red window, examine it and follow the instructions.
Otherwise, it seems that you or your antivirus deleted the encryptor program.
Now you have the last chance to decrypt your files.
Open http://tkj3higtqlvohs7z.asowbu3g24.com or http://tkj3higtqlvohs7z.kkfriw9425.com ,
https://tkj3higtqlvohs7z.s5.tor-gateways.de/ in your browser.
They are public gates to the secret server.
Copy and paste the following Bitcoin address in the input form on server. Avoid missprints.
……………………………………………………………..
Follow the instructions on the server.
If you have problems with gates, use direct connection:
1. Download Tor Browser from http://torproject.org
2. In the Tor Browser open the http://tkj3higtqlvohs7z.onion/
Note that this server is available via Tor Browser only.
Retry in 1 hour if site is not reachable.
Copy and paste the following Bitcoin address in the input form on server. Avoid missprints.
……………………………………………………………
Follow the instructions on the server.
CryptoVictim
Today one of my colegues received by email a file and infected all the files on a NAS with cryptolocker. I tried the tool to decrypt but it says that “Currently we do not have any records for this Bitcoin wallet.” Is posible to send you a test file to find out the key for this new version of the virus?
David De Vl.
My files are also encrypted by Coinvault and still have the cv-lock file. With this new decryption tool released I restarted the cv-lock.exe file. But the program no more shows the window where I can find the bitcoin wallet. How can I start this executable that it shows the windows. Would it be possible to retreive the bitcoin walletnumber by opening the cv-lock.exe file with a hexeditor? Or is there another manner how to retreive this number?
Jaap
I have the same issue. When I start the cvlocker file, I see a flash of the ransomwarescreen and then it disappears. The flash is very short, I don’t even see any text. Any thoughts on resolving this?
Lex
Hello,
First of all, great job! When i enter the adress i get the message “Currently we do not have any records for this Bitcoin wallet.” is there anything else what i can try or should i send you more information?
Thanks in advance
Lex
Maybe it’s because i am infected with Bitcrypto? This has almost the same UI as Coinvault…!
ASM Ashrafuzzaman
I’m from Bangladesh. My computer had been infected by the ransomware virus. I have been successful in removing the virus from my computer but now require to recover my encrypted files.
The bitcoin address provided to me is 137VhRn25CUPELu8AYoG14VCv1C6Sy8DGP
Please help me to recover all my encrypted files.
Barry
Thank you for taking the time to make this tool. Unfortunately for me, my key isnt available in your database yet. I’m wondering if the investigation is still ongoing? I’m hoping new keys will be found and added… but it has been a while since the last update… so just “bumping” this topic
Thanks again
jan
Became a victim the day before yesterday. key not jet available. Do you know when they will be updated?
Joost
Hi there,
i also have removed the program but dont have the bitcoin wallet adress anymore. Is there anyway that i can decrypt my files?
Jack Ziv
Is there any way to receive the RansomWare bitcoin address list in a readable format?
Thank you!
Martijn de Haan
Hello, my PC is unfortunately infected with Coinvault. I’ve just been stupid and have the pop-up where the important information is such that the files are closed. Is there a way to find out?
Martijn de Haan
Décio
Quando será feita uma nova atualização das chaves ? Sou do Brasil e também fui infectado.
wgn
hello. all files encrypted in my laptop from virus. then they save one picture in every folders.
they tolld about their secret server and give link to access my personal page. they ask 500$ for discrypt my files.
my bitcoins address have in my secret page of their created.
if you can give a advice for search my secret key i appreciate your support.
this picture has every folder in my laptop.
http://imgur.com/x3G6HmU
(sorry for my poor english)