
Mikhail Khodorkovsky, the former head of the Russian oil company YUKOS, was recently released from jail. There is a lot of speculation in Russia as to the reasons for his amnesty, while tabloids around the world are watching the ex-businessman’s every step. For ‘Nigerian’ scammers, the news was used as the basis for a tale of tragedy whose sole aim is to squeeze money out of the gullible users.
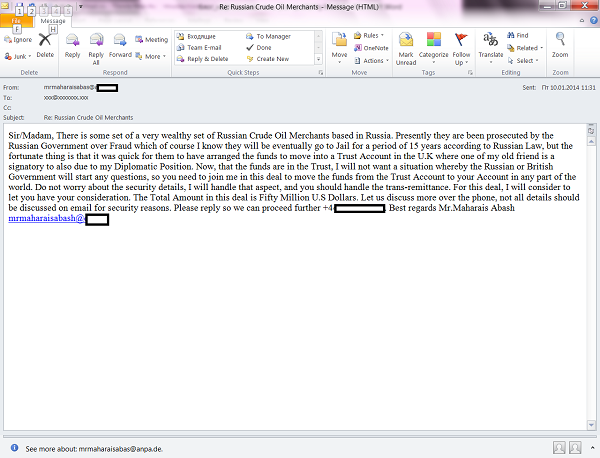
According to the ‘Nigerian’ story, an entire group of Russian oil tycoons (an exaggeration that is intended to justify the huge sum of money referred to in the story) faced trial on fraud charges. Luckily for the recipient, they had time to transfer their fortunes to a trust account with a UK bank. And now a mysterious middleman, Mr. Maharais Abash, is asking people to provide a personal bank account that the $50 million oil fortune could be transferred to. Naturally, the affair is strictly confidential – UK and Russian officials should know nothing about it.
Khodorkovsky’s release from jail triggered a surge in creative scams by these writers of ‘Nigerians letters’ – there can be no other explanation for the claim that an entire group of oil tycoons (rather than just one individual) was supposedly given a 15-year sentence. Fortunately, this makes it easier to spot the scam. A simple online search will quickly reveal that there have been no mass arrests of Russian oligarchs, and that the $50 million is merely a figment of Mr. Maharais Abash’s imagination – if indeed he even exists.





















Black Gold, or a Black Hole in Your Pocket