
Every year, Kaspersky releases an annual Black Friday alert to highlight how fraudsters may capitalize on increased levels of online shopping at this time of year when many brands are offering their customers appealing discounts. In the rush to get a big discount or, even more panic-inducing, a limited time offer, many shoppers lose all sense of vigilance. Caution goes out the window and consumers start tapping on links and email vouchers without their usual care and attention.
Spam and Phishing
Unfortunately, online shopping at this time of year needs more security-awareness, not less. It is the peak season for phishers and spammers. Along with many genuine offers, there also lurk phishing scams ready to reel in an unwitting bargain hunter’s bank details. By clicking on a too-good-to-be-true discount link online without checking it’s genuine, you could find yourself at a fake marketplace, that may look indistinguishable from the real website. On these sites, entering your bank details could result in money leaving your account, but no package arriving at your door.
Since Kaspersky has been analyzing financial phishing activity, which began in 2013, there has been a steady rise in threats – peaking at 54% in 2017. However, last year this trend did slow down and decrease. The figure dropped to 44.70%. Financial phishing attacks are still expected to be a big risk around the upcoming Black Friday event, and there will be close analysis to see if the figure rises once more.

Share of financial phishing attacks from all phishing decreased for the first time in four years in 2018
Social Engineering in the Retail Sector
How do phishing scams work?
In order to make these scams a success, fraudsters need to lure their potential victims to fake webpages and obtain their bank details. To do this, attackers register website domains, often containing the magic phrase ‘Black Friday’ and keep their registration data hidden.
Their sites are usually well designed and appear to be genuine and of a high quality. Unlike many old typo-filled spam emails, phishing web pages are relatively easy to make look authentic – scammers can simply copy the source code from the real store’s website and make theirs appear to be a near perfect match.
Domain addresses are usually hidden until the event itself, so they are not blocked in advance by antivirus software vendors. The scam website is then activated immediately before the phishing mail goes out, just as shown in these screenshots.
Occasionally, these attacks appear to be sent by large banks or payment systems, allegedly partners of the Black Friday sales campaign, while in fact these are carefully crafted copies of legitimate pages and mailshots made by criminals. Emails or warnings may threaten to block the user’s account or promise some financial benefits by clicking on the email. These phishing emails make it seem like all you have to do is follow the link and log in to your account.
However, if you do log in to these sites with your credentials, all your bank account or payment card data — such as card numbers or usernames and passwords — will be leaked to the scammers.
Once they have this data, scammers could be able to withdraw money from your account, sell your bank card details on the dark web, or spend your money in various ways. This is often carried out by teams in other countries.
These scams come in a variety of forms. In one example, scammers offer goods at crazy discounts, encouraging the victim to share their bank card details, thereby risking losing all of their account funds and of course, not receiving their order. In another scheme, the victim might be tricked into transferring money to the attacker’s account, after which the fraudster breaks off all contact and the funds are lost.
There is also another widespread and very successful phishing scheme which asks users to complete a survey and fill in a large registration form, along with bank card details to take part in the promotion. After completing the form, you’re asked to send a link to the website to 10 friends via a messenger app.
Of course, victims of this scam won’t ever receive any prizes but instead end up bombarded with various links and emails for more useless surveys. Any additional clicks on these survey usually mean that scammers receive even more money. Because the survey is shared through messenger apps, more users, who often trust links that come from their friends, might also fall for the trick. And so the cycle continues.
Where are phishing scams occurring?
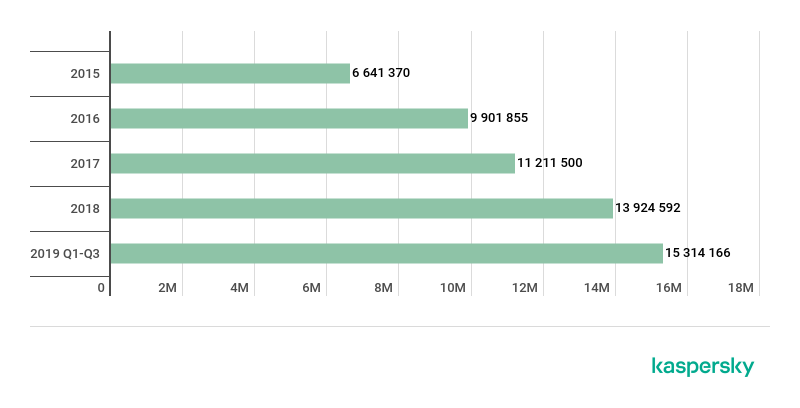
According to our statistics, more than half of phishing attacks carried out in the digital retail space are in the payment sector – online stores, payment systems and banks. Frequently, criminals use brands of Amazon, eBay and Alibaba to trick users. Amazon was used as a disguise in more than a million attacks in the first three quarters of 2019 alone, as the graph below shows.
Notably, the share of phishing incidents in the online retail space during the peak sales period significantly increased compared to what happens during the rest of the year. For instance, attacks that were using the eBay brand reached nearly 25,000 during the week of November 4th, 2018, two weeks before Black Friday, after experiencing minimal disruption in the preceding days. The Amazon disguise was also a key target for scammers too – facing more than 20,000 phishing attacks during the week of November 19th, 2018, which was the week of Black Friday last year.
These 2018 findings allow us to predict that in 2019 the situation may repeat.
Banking trojans
Similarly to phishing scams, Banking Trojans also target e-commerce brands so that they can track down user credentials – like banking login details, passwords, bank card numbers or phone numbers.
But with Trojans, the malware can intercept data fields on targeted websites. This means they can modify online page content and steal credentials entered, while the victim will keep thinking that they enter login and password to legitimate fields on the website. Because of this, cybercriminals can monitor a hacked user’s online behavior, such as which sites they visit while on the infected device.
Once the user browses to one of the targeted e-commerce websites, the Trojan activates its form-grabbing functionality and saves all the data a user inputs on the website. On an e-commerce website, this means a credit or debit card number, expiration date and CVV, as well as your site login credentials.
If the site or user’s bank doesn’t feature two-factor authentication, then the criminals behind the Trojan will have access to all this data and can use it to empty the user’s bank account or use their card details for purchases.
In the first three quarters of 2019, Kaspersky discovered 15 families of financial malware targeted at users of popular brands. In addition to the already known banking families such as Zeus, Betabot, Cridex and Gozi, this year, we have also seen two mobile banking Trojans joining our list: Anubis and Gustuff.
Last year’s report saw a 10% increase in the detection rate of financial malware between 2017 and 2018[1], but over the course of the full year that growth was a far more significant 24%. More than 15 million attacks by banking Trojans have been registered in the first three quarters of 2019. This means we have already seen a nine percent increase on what was found during 2018.
Mobile Trojans are also able to steal user credentials. The common scenario for user account theft on mobile devices is an overlay-attack, which overlays windows from the hacker’s program on top of the app, or window the user is browsing. Often the overlayed window or data input form is identical to the real one and the user enters their data believing that they are dealing with the original program.
Targeted e-commerce categories
In 2019, we found those 15 malware families were targeting a total of 91 consumer e-commerce sites and mobile apps across the world.
Of those, consumer goods websites such as fashion and clothing, or toys and jewelry, were the most commonly targeted, with 28 websites falling into this category. Also popular with phishing scams are entertainment websites with 20 examples found and travel bookings with 15 in that category.
Surprisingly, sites which sell big ticket items, such as consumer electronics (two websites found) and telecoms (12 websites), which are popular purchases on Black Friday, are at the bottom of the list.
| Consumer apparel (fashion, shoes, gifts, toys, jewelry, department store) | 28 |
| Entertainment (cinema, games etc.) | 20 |
| Travel (Flights, taxi, hotels, etc.) | 15 |
| Online retail platform (eBay, Alibaba group etc.) | 14 |
| Telecoms | 12 |
| Consumer electronics | 2 |
Proportion of e-commerce categories targeted by malware in 2019, by number of targeted brands
Advice and recommendations
As shown in this overview, Black Friday offers a golden opportunity for fraudsters and scammers to steal consumers’ cash. Sometimes a deal can seem too-good-to-be-true, but retailers still offer great discounts at this time of year, so it’s important to examine every deal closely. Shopping around for a bargain can still be enjoyable, it just needs extra vigilance to make sure you can tell the difference between the must-have offers and fake promotions. With incidents of phishing and banking Trojans on the rise, it’s important to stay safe from cyberthreats during the peak Black Friday shopping season.
To stay safe and keep your hard-earned money secure while shopping online, Kaspersky recommends taking the following security measures:
If you are a consumer:
- Avoid shopping from websites that appear suspicious or flawed, no matter how great their Black Friday deals are
- Don’t click on unfamiliar links you receive in emails or social media messages, even from people you know, unless you were expecting the message
- Double check the email address of the sender. If it not the official brand’s website domain, do not click on the link
- Hover over the linked text in the email or message and see which URL it will actually open
- Invest in a robust cybersecurity solution to protect all your devices you use to shop online
- Think about how much money you wish to spend in an online payment transaction account at any one time
- Reduce the amount of funds you have in your bank and online accounts. The greater the balance, the more can be lost to fraudsters
- Restrict the number of attempted transactions on your bank card
- Turn on and always use two-factor authentication (Verified by Visa, MasterCard Secure Code, etc.)
If you are an online brand or retailer:
- Use a reputable payment service and keep your online trading and payment platform software up to date. Every new update may contain critical patches to make the system less vulnerable to cybercriminals
- Use a tailored IT and cybersecurity solution to protect your business and customers
- Pay attention to the personal information used by customers who buy from you. Use a fraud prevention solution that you can adjust to your company profile and the profile of your customers
All research used in this report is based on user data obtained with consent and processed using the Kaspersky Security Network (KSN). All referenced banking Trojan malware were detected and blocked by Kaspersky security solutions.
























Black Friday Alert 2019: Net Shopping Bag of Threats