
Introduction
The festive holiday shopping season, which covers Thanksgiving, Black Friday and Cyber Monday in late November as well as Christmas in December, now accounts for a significant share of annual sales for retailers, particularly in the U.S., Europe and APAC.
Those selling clothing, jewellery, consumer electronics, sports, hobbies and books can make around a quarter of their sales during the holiday period. In 2017, holiday sales in the U.S. alone are expected to be up by 3.6 to 4.0 per cent on the same time in 2016.
For brands looking to make the most of this annual spending spree, the desire to sell as much as possible at a time of intense competition is leading to ever more aggressive marketing campaigns – particularly online.
Promotional emails, banner ads, social media posts and more bombard consumers over the holiday months; generating a great deal of noise. Tactics such as one-click buying are designed to making the purchase process ever easier and faster. Further, up to three quarters of emails received on Black Friday and Cyber Monday are now opened on a mobile device. People are becoming used to making instant decisions – and that has significant security implications. They may miss vital signs that things are not what they seem and their data could be at risk.
All this makes this time of year an ideal hunting ground for hackers, phishers and malware spreaders; disguising their attacks as offers too good to refuse, a concerned security message from your bank requiring urgent attention, a special rate discount from your credit card service, and more. All you have to do is enter your personal details, card numbers or bank account credentials.
Not surprisingly, messages or links designed to look as if they come from well-known, trusted brands, payment cards and banks account for many of the malicious communications detected by Kaspersky Lab’s systems in the last few years.
Methodology and Key Findings
The overview is based on information gathered by Kaspersky Lab’s heuristic anti-phishing component that activates every time a user tries to open a phishing link that has not yet been added to Kaspersky Lab’s database. Data is presented either as the number of attacks or the number of attacked users. It updates the 2016 Black Friday overview report with data covering the fourth quarter of 2016 through to 18 October, 2017.
Key Findings:
- Following a decline in 2015, financial phishing abusing online payment systems, banks and retailers increased again in 2016.
- Financial phishing now accounts for half (49.77 per cent) of all phishing attacks, up from 34.33 per cent in 2015.
- Mobile-first consumers are likely to be a key driver behind the rise in financial phishing: the use of smartphones for online banking, payment and shopping has doubled in a year, and mobile users will have less time to think and check each action, particularly if they are out and about.
- Attack levels are now fairly consistent throughout the year; and Q4 data shows they are also more evenly spread in terms of the brand names the phishers make use of.
- Data for both 2015 and 2016 shows a clear attack peak on Black Friday, followed by a fall. In 2016 the number of attacks fell by up to 33 per cent between Friday and Saturday, despite Saturday being the second biggest shopping day over the holiday weekend in the U.S.
- Financial phishers are exploiting the Black Friday name in their attacks, as well as consumer awareness of, and concerns about online security – disguising their attack messages as security alerts, implications that the user has been hacked, or adding reassuring-sounding security messages.
Phishing – a universal threat
As earlier editions of the Black Friday overview have shown, phishing is one of the most popular ways of stealing personal information, including payment card details and credentials to online banking accounts. The schemes are fairly easy to set up, requiring limited investment and skills – and are mainly reliant on encouraging people to voluntarily part with their personal and financial information.
Originally spread mainly through emails – phishing attacks are now also carried out through website banners and pop-ups, links, instant messaging, SMS, forums, blogs and social media.
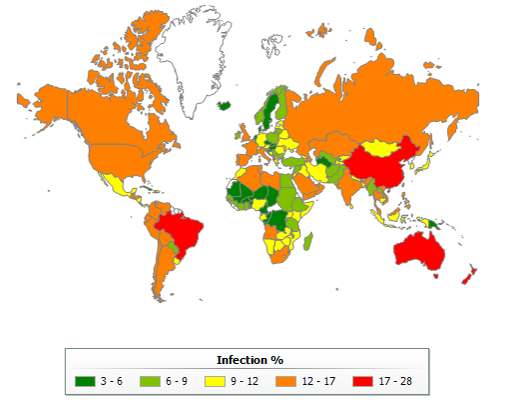
Percentage of users on whose computers Kaspersky Lab’s heuristic anti-phishing system was triggered as a proportion of the total number of Kaspersky Lab users in that country, Q1-Q3 2017
Phishing has a global reach. Kaspersky Lab data on attempted attacks shows that in 2017, China, Australia, Brazil were particularly vulnerable – with up to a quarter or more (28 per cent) of users targeted. Followed by North America., large parts of Western Europe, the Russian federation, Latin America, India and elsewhere – where up to one in six (17 per cent) were affected.
A new pool for phishers
During the holiday period, consumers can become more exposed online. An onslaught of promotional emails, offers and ads, the pressure to buy gifts, and a growing tendency to use their smartphone for everything, can mean that people are browsing and buying through a relatively small screen and often while out and about surrounded by distractions. Taken together, the can make them easier to mislead and manipulate through social engineering and high quality spoofed web interfaces.
The 2017 Kaspersky Cybersecurity Index shows how important smartphones have become for online banking, payment and retail transactions.
Between the first six months of 2016 and the same period in 2017, online shopping on smartphones increased from 24 per cent to 43 per cent; online banking from 22 per cent to 35 per cent; and the use of online payment systems from 14 per cent to 29 per cent. Further, the use of smartphones to send and receive emails grew from 44 per cent to 59 per cent over the same period.
The Kaspersky Lab phishing data used in this report focuses on the attack rather than the device the messages/links are received or opened on, but the trend towards mobile-first behavior among consumers is creating new opportunities for cybercriminals that they will not hesitate to capitalize on.
Financial phishing on the rise
As more people adopt online payment and shopping, the theft of financial information or credentials to online bank accounts is a growing target. The proportion of phishing attacks focused on financial data has risen steadily over the last few years and now accounts for half of all phishing attacks.
This popularity means that attack levels now remain fairly consistent throughout the year. The gap that previously existed between the number of attacks experienced during the high spending holiday period, and those registered in the rest of the year, seemed to close in 2016.

The proportion of phishing that was financial phishing over the whole year, and during the holiday period
However, when you dig deeper into the data it becomes clear that the holiday season continues to represent a time of significant and greater risk of falling victim to financial phishing – mainly because of clear localized attack peaks, but probably also because of the increased vulnerability of distracted mobile shoppers and the surge of marketing noise.
Types of financial phishing
We define three categories of financial phishing, depending on what is being exploited: online banking, online payment or online shopping. Each type has evolved at a different, and not always consistent rate over the last few years.
| 2013 | Full year | Q4 |
| Financial phishing total | 31.45% | 32.02% |
| Online shop | 6.51% | 7.80% |
| Online banks | 22.20% | 18.76% |
| Online payments | 2.74% | 5.46% |
| 2014 | Full year | Q4 |
| Financial phishing total | 28.73% | 38.49% |
| Online shop | 7.32% | 12.63% |
| Online banks | 16.27% | 17.94% |
| Online payments | 5.14% | 7.92% |
| 2015 | Full year | Q4 |
| Financial phishing total | 34.33% | 43.38% |
| Online shop | 9.08% | 12.29% |
| Online banks | 17.45% | 18.90% |
| Online payments | 7.08% | 12.19% |
| 2016 | Full year | Q4 |
| Financial phishing total | 47.48% | 48.14% |
| Online shop | 10.41% | 10.17% |
| Online banks | 25.76% | 26.35% |
| Online payments | 11.55% | 11.37% |
| 2017 | Q1-Q3 | |
| Financial phishing total | 49.77% | |
| Online shop | 9.98% | |
| Online banks | 24.47% | |
| Online payments | 15.31% |
The change in the share of different types of financial phishing in 2013-2017
Attackers follow consumer adoption trends
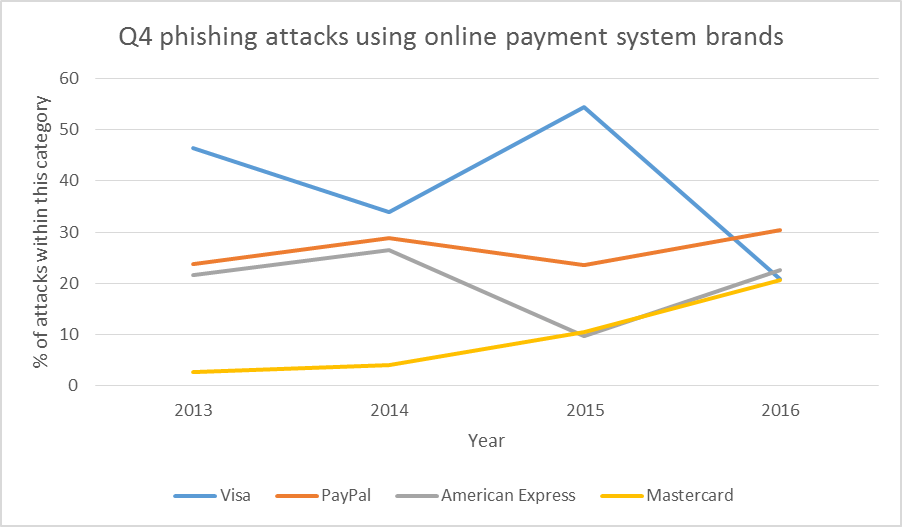
Data for the first three quarters of 2017 shows a slight drop in all financial phishing categories with the exception of online payment systems.
Looking at the dynamics of Q4 attacks using the names of leading payment systems it is clear that cybercriminals are adapting to reflect the growing use of online payment methods such as PayPal. But overall, there seems to be a disappearance of extremes, with attacks spread more evenly across the different brand names.
Multi-brand retailers remain a top choice for financial phishing
In terms of retail brand, the leading names used by attackers over the last few years have barely changed – but the number of attacks in Q4 using each brand have also become more evenly spread. This could reflect growing consumer adoption of online shopping. Most of the top names supply multiple brands (Amazon, Alibaba, Taobao, eBay).
In short, financial phishing is no longer focused on one or two brands to the exclusion of all others, the attackers are widening their net – and this has far-reaching security implications. No brand can be assumed to be safe, or even safer.
Further, looking at the daily spread of attacks during the week leading up to Black Friday it can be seen that there are some major red flag days when consumers are more vulnerable than ever.
Black Friday attacks
The following chart shows how the number of financial phishing attacks peak on Black Friday (November 25 in 2016, and November 27 in 2015), followed by a decline – particularly in 2016 when attacks detected fell by 33 per cent within a day (from around 770,000 to 510,000 detections). Weekends generally see lower levels of attacks and fewer people online, but in the U.S. the day after Black Friday is the second biggest shopping day of the year.
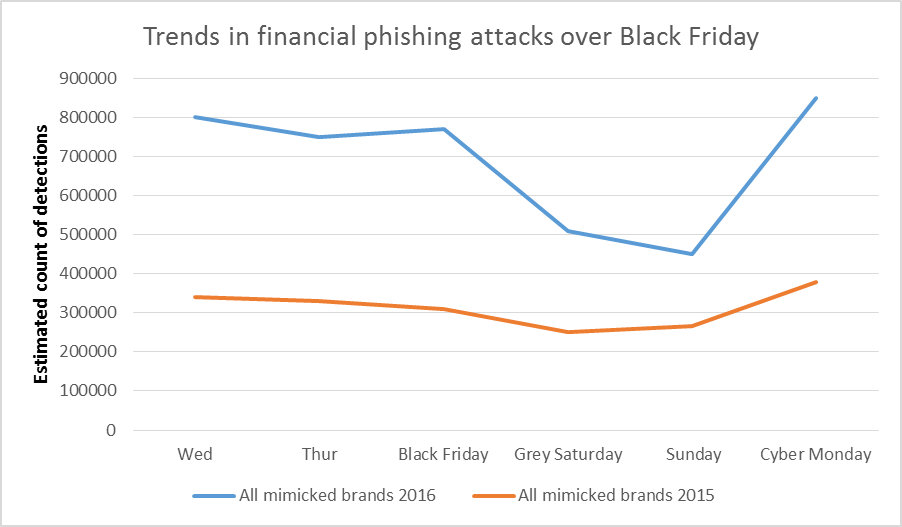
The change in the number of phishing attacks using names of popular retail, banking and payment brands during Black Friday week 2015 and 2016 (data from all Kaspersky Lab security components – heuristic, offline and cloud detections)
Conclusion and advice
The main purpose of the report is to raise awareness of a threat that consumers, retailers, financial services and payments systems may encounter over the holiday season. Cybercriminals out for financial information and account details – and ultimately money – are increasingly adept at hiding in the noise, targeting their attacks and exploiting human emotions, such as fear and desire. For further information and advice, please see the full overview.
Kaspersky Lab – Beyond Black Friday Threat Report, November 2017




















Frank H. Watanabe
This is just to let you know that I’ve been using your product for years and love it. Of all the anti-virus products out there you people are the best. Very informative etc. Keep up the excellent work of protecting.