
As Apple’s popularity grows, so does the desire among fraudsters to make money from the people who own the company’s devices. The cybercriminals are aiming to steal Apple ID data which provides access to users’ personal information stored in iCloud (e.g., photographs, contacts, documents, email, etc.) as well as to the purchases made in the company’s iTunes Store. Many malicious users go further and try to the steal bank card details used to pay for those purchases.
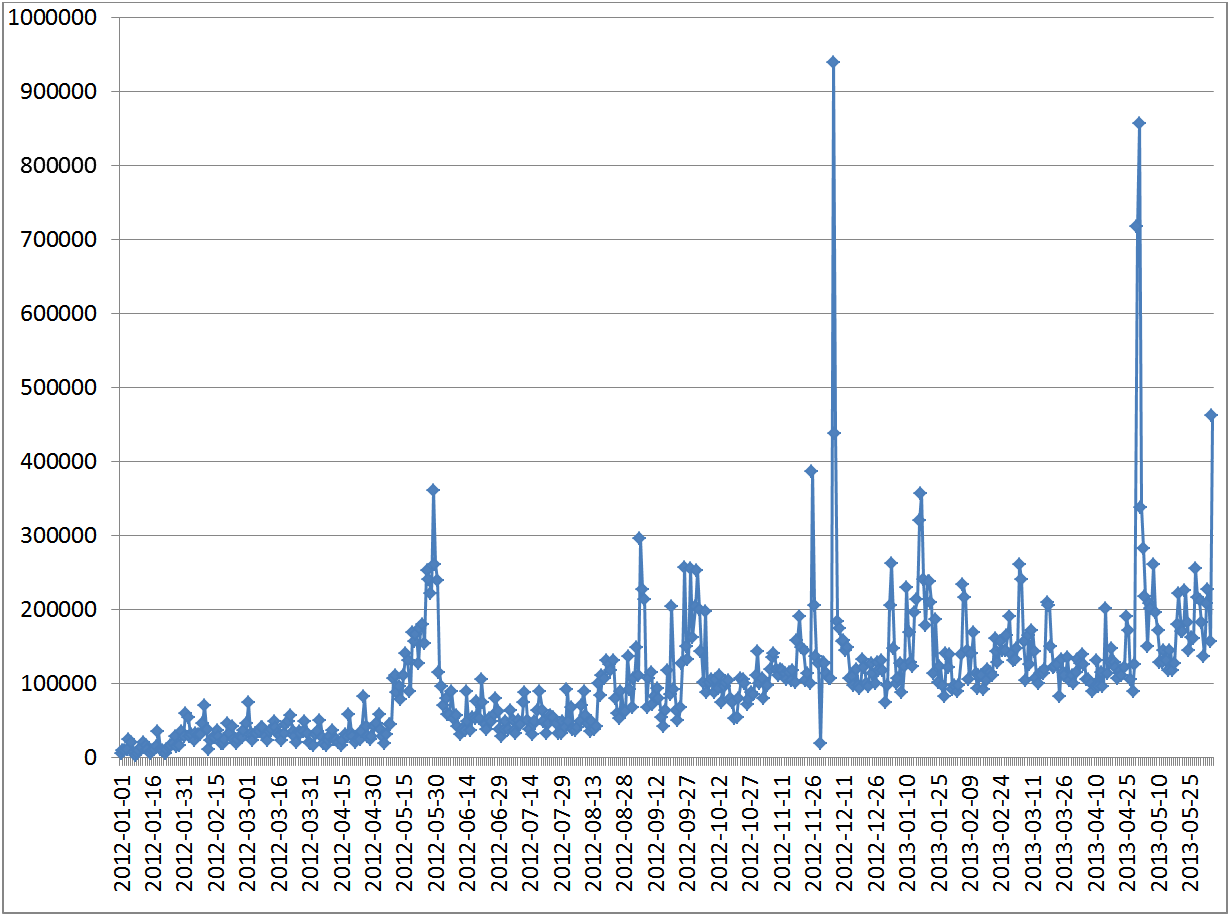
The scammers make use of phishing sites that imitate the official apple.com site. Since the beginning of 2012 until the present time this has resulted in a significant increase in the number of web antivirus detections triggered by users of our products attempting to visit such sites. During that period we have seen on average around 200,000 detections per day. By contrast, in 2011 the figure stood at around 1,000 detections per day.
Heuristic analyzer detections from January 2012 to May 2013 (detections per day)
On some days the number of web antivirus detections for fake apple.com phishing sites exceeded the daily average by several times. There were a number of peaks, the most significant of which occurred on December 6, 2012 (939,549 detections) and May 1, 2013 (856,025 detections). This periodic surge in cybercriminal activity and the resulting increase in web antivirus detections can be put down to important events in the life of Apple. For example, December’s peak occurred immediately after the iTunes Store opened in Russia, Turkey, India, South Africa and 52 other countries around the world.
How do users end up on fake sites? One of the most popular methods is to use spam to spread links to phishing sites. For example, cybercriminals send out emails on behalf of Apple in which they ask the recipient to confirm their account by following a link in the message. The link leads to a fake website where users are asked to enter their Apple ID and password – this data is then stolen by the cybercriminals and used for their own ends.
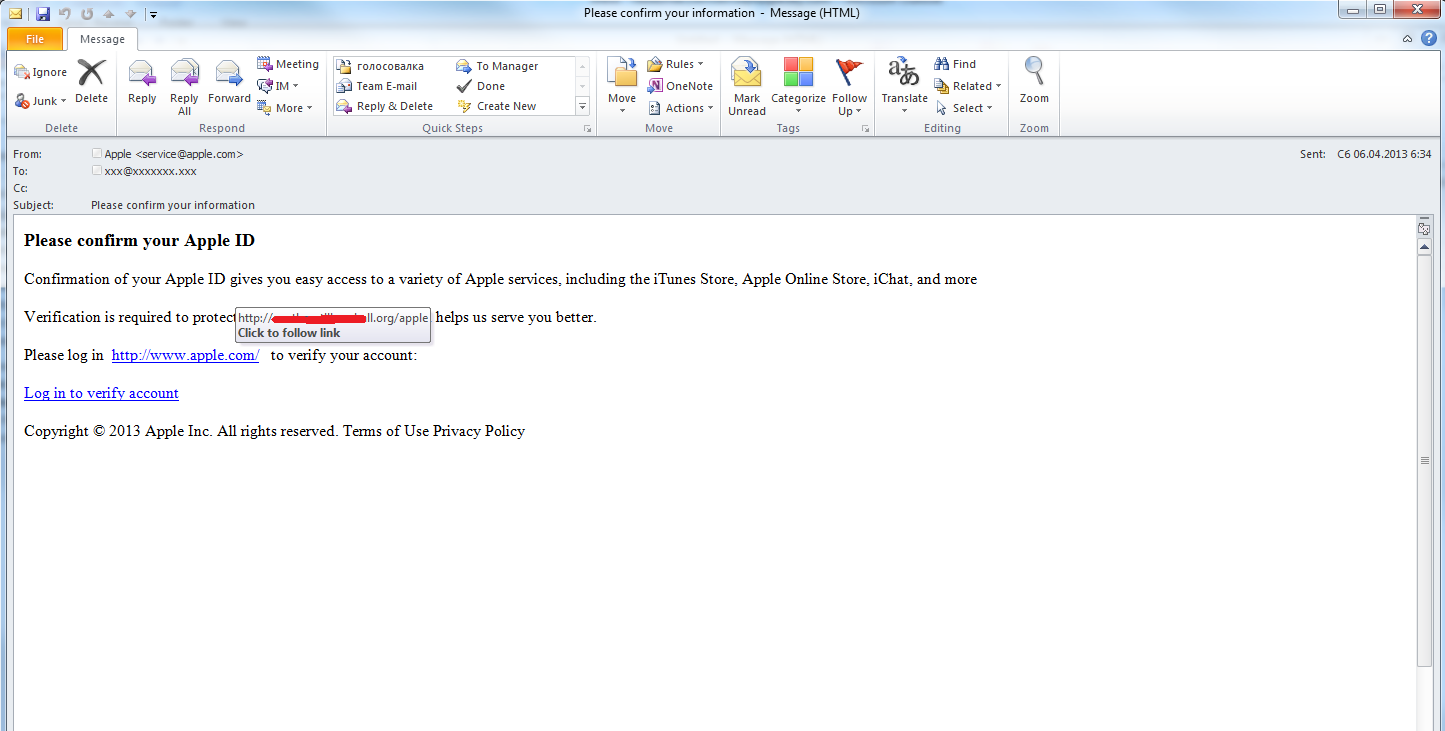
Here’s one example of a fraudulent message containing a link to a phishing site:
As you can see, the scammers have made a pretty good job of it – the language of the message sounds official and the ‘sender’ field contains the fake address service@apple.com. The email was actually sent from another address that is hidden from the recipient. When the cursor is placed over the link you can see that it clearly does not direct to apple.com
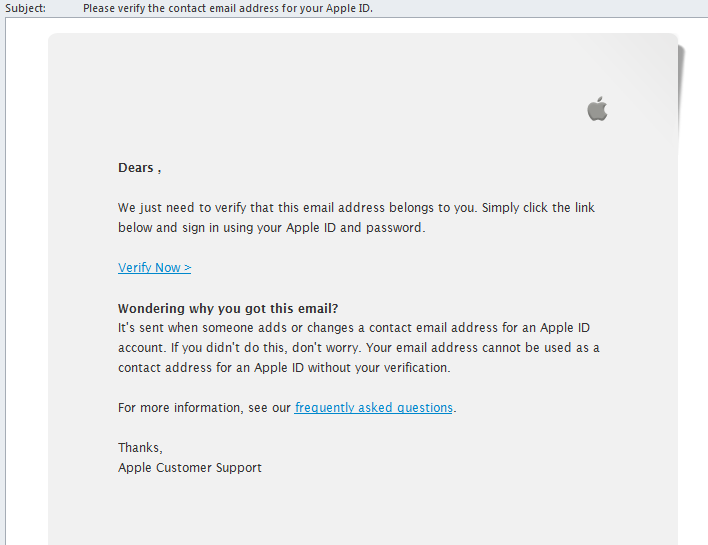
Here’s another example of a phishing email in which the senders have passed themselves off as Apple customer support:
The authors of this scam letter have been even more thorough in their approach: they have added a background with the Apple logo, a link to an FAQ and even signed as ‘Apple Customer Support’. The only thing that marks it out as a fake is the lack of the recipient’s name at the beginning of the letter.
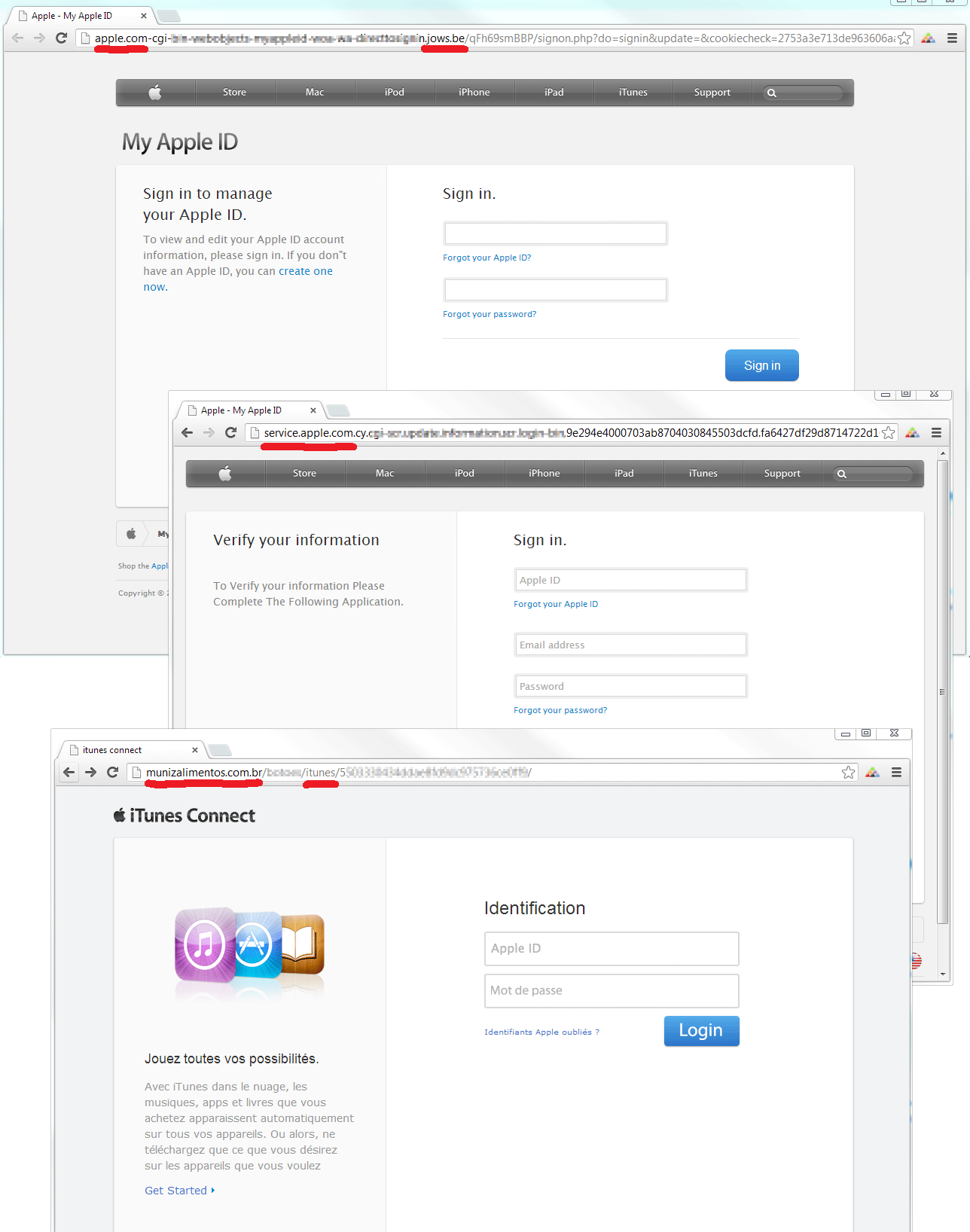
The page that the recipient is directed to from these phishing messages usually imitates the official pages of the Apple website very accurately, and all the contents in the fake page’s links redirect to apple.com pages.
Sample phishing pages showing the tricks used by cybercriminals – those tricks and the real domains are underlined in red
In the examples above the address line is the giveaway: it may contain ‘apple.com’ in one form or another, but even a less experienced user could spot the fake address. However, if the site is opened in a Safari mobile browser on an iPhone or iPad, the user may not look at the address line as it is hidden from view once the page is downloaded. The scammers can also add additional elements to a page such as an image showing an address line with the legitimate address. This element takes the place of the real address line and is meant to trick recipients.
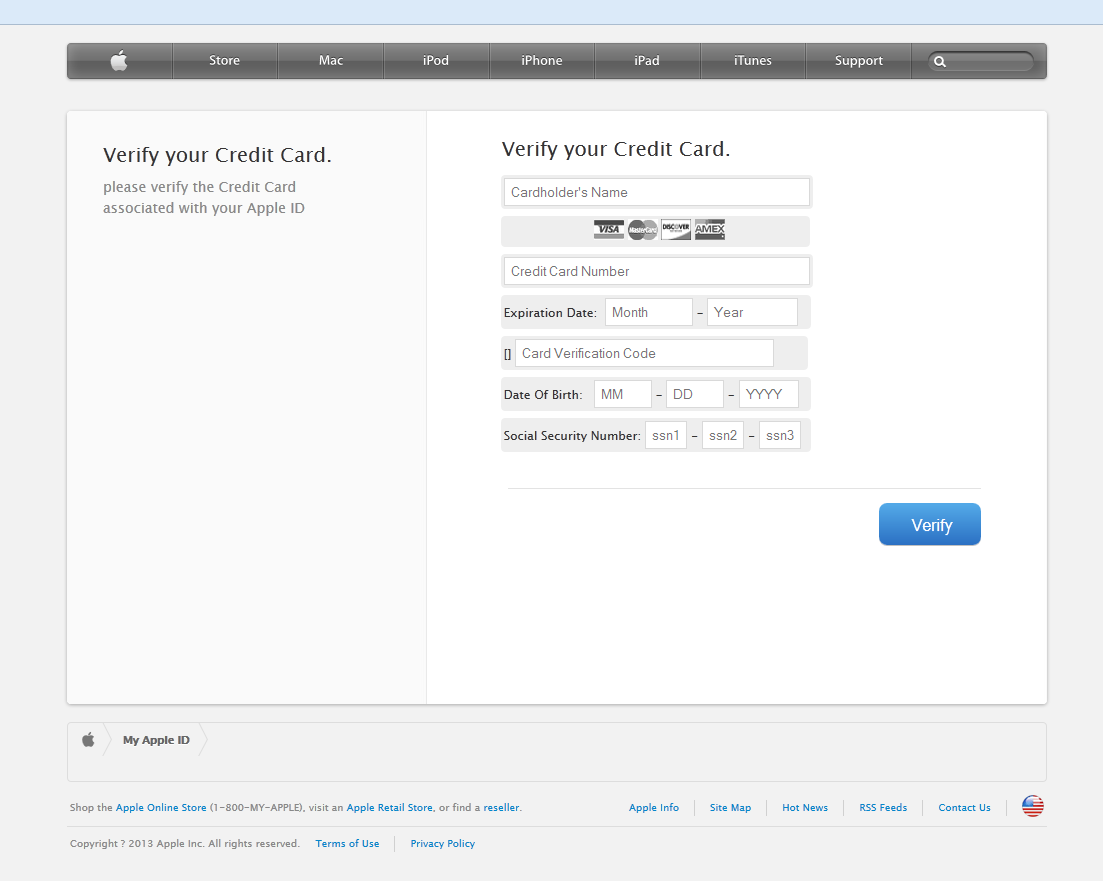
The following image shows a fake page that tries to steal bank card details on the pretext of linking your card to your Apple ID:
As you can see, the fraudsters were looking to get as much info as possible – from the card number to the CVC. With those details they can conduct just about any transaction with your card.
To safeguard your account you can activate two-factor authentication for Apple ID, with a four-digit verification code sent to one or more trusted devices. This two-step verification process makes unauthorized access or account modifications impossible on the My Apple ID site and prevents any purchases being made via your account by third parties. However, it doesn’t protect you from losing money if you provide the cybercriminals with your bank details. Therefore, if you receive a message in the name of Apple or one of its employees, be careful: it’s worth calling the technical support people at the company to make absolutely sure it is legitimate. Also, you should avoid following any links included in such messages; it’s best to enter the relevant address into the address line yourself. And if you do follow the link, carefully check the page contents and check the address that appears in the browser. By following these simple rules you can keep your data safe and avoid falling victim to the scammers.






















Apple of discord