
Yesterday I looked into a case where somebody had gotten a nice Christmas present – a new MP3 player. However this MP3 player contained a bit more than the person asked for. The device was infected with Worm.Win32.Fujack.aa. All the evidence clearly indicates the device was infected before the user opened the gift.
This is unpleasant, but infected removable storage media is nothing new. There was the case of infected Maxtor drives and Aleks recently blogged about his purchase of an infected Kingston flash card.
Of course, we’ve contacted the company concerned. They told us they were aware that a few months ago there was a partially infected batch of these MP3 players, and that they’d taken steps to fix the problem. It was only this particular model – the Victory LT-200 that was affected.
I’ve noticed there seems to be a lack of clarity about how Windows behaves with USB media, so this seems like a good opportunity to clear up a few points.
Most malware that spreads to removable media exploits the Windows autorun functionality: Windows checks any drive to see if it has a file named autorun.inf in the root directory.
If it does, Windows checks the contents of the file and take appropriate action. In most cases the file contains a command saying that a file should be automatically run. It will do this automatically for any local hard drive and the same goes for cd-roms.
Microsoft’s made some security improvements since XP/SP2, causing Windows to check if the device is connected via USB. If it is, the commands in autorun.inf won’t be automatically followed, but the user will be shown a pop-up asking for action. This is good, but it’s not perfect. In XP, Windows still automatically follows the commands in autorun.inf if the user accesses the drive via explorer.
This means that although infection isn’t 100% automatically, it’s still a significant threat.
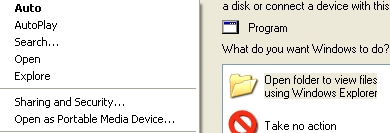
The bold “Auto” means that Windows’ default action is to perform autorun when the drive is double-clicked.
So I decided to have a look to see what further improvements Microsoft made in Vista.
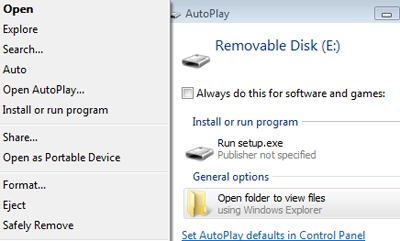
As the screenshot shows, the default action is changed to “open”, which means that Windows will just show the directory listing.
A very clear improvement. However Vista also makes it easier for the user to manually run setup.exe (Fujack.aa).
In terms of user friendliness versus security Vista is superior to XP. It’ll be interesting to see if Service Pack 3 for XP will bring further changes – I can only hope it will.
This case shows clearly that you should always exercise caution when handling unknown external storage media, whether it’s fresh out of the box or passed to you by a friend or colleague. One of the best precautions against getting infected is to make sure that your virus scanner is on. In most cases it takes a while for an infected device to be shipped from the factory to the store, so antivirus software is very likely to detect the malware that’s caused the infection.

















Another usb-media infection