
Today Adobe put out an advisory for a previously unknown zero-day in its PDF Reader/Acrobat software.
This vulnerability is actively being exploited in the wild.
The exploit is pretty basic. What’s interesting about it is that it makes use of Return Oriented Programming to bypass the ASLR and DEP mitigation technologies in Windows Vista and 7.
More widespread usage of ROP for exploits is something I’ve been expecting for a while. Why? Because Windows 7 is gaining more and more traction in both the consumer and corporate space.
While most malicious PDFs download their payload, this time the PDF has malicious content embedded. The PDF drops an executable into the %temp% directory and tries to execute it.
The file it drops is digitally signed with a valid signature from a US-based Credit Union!
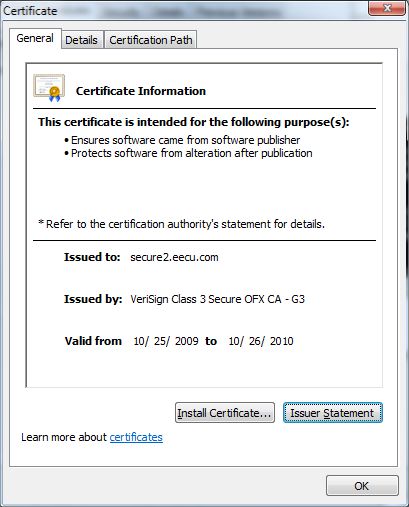
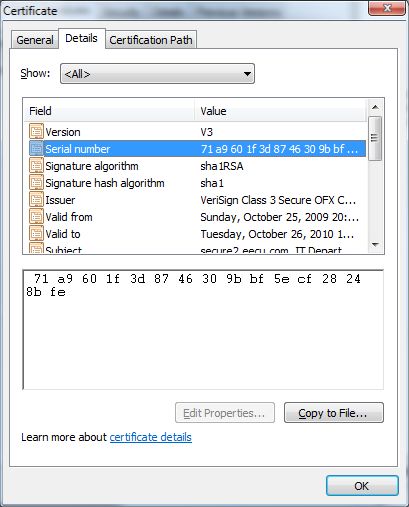
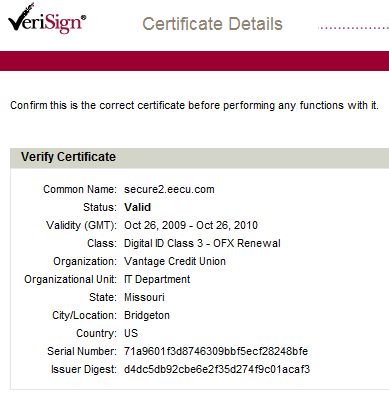
Take a close look at the screenshots and you’ll see that not only is the certificate valid, but it really does belong to Vantage Credit Union. This means that the cybercriminals must have got their hands on the private certificate. Remind you of anything? If you say Stuxnet (where compromised Realtek and JMicron certificates were used to sign files) then we’re clearly thinking on the same lines.
It’ll be interesting to see if Stuxnet has started a trend or if these cases are just a flukey coincidence. I suspect they’re not – I think the use of valid, stolen certificates to sign malware will really take off in 2011.
Both Verisign and Vantage Credit Union have been notified so that they can take action.





















Adobe Reader zero-day attack – now with stolen certificate