
Symbiosis of PowerShell and EternalBlue for cryptocurrency mining
Recently, an interesting miner implementation appeared on Kaspersky Lab’s radar. The malware, which we dubbed PowerGhost, is capable of stealthily establishing itself in a system and spreading across large corporate networks infecting both workstations and servers. This type of hidden consolidation is typical of miners: the more machines that get infected and the longer they remain that way, the greater the attacker’s profits. Therefore, it’s not uncommon to see clean software being infected with a miner; the popularity of the legitimate software serves to promote the malware’s proliferation. The creators of PowerGhost, however, went further and started using fileless techniques to establish the illegal miner within the victim system. It appears the growing popularity and rates of cryptocurrencies have convinced the bad guys of the need to invest in new mining techniques – as our data demonstrates, miners are gradually replacing ransomware Trojans.
Technical description and propagation method
PowerGhost is an obfuscated PowerShell script that contains the core code and the following add-on modules: the actual miner, mimikatz, the libraries msvcp120.dll and msvcr120.dll required for the miner’s operation, a module for reflective PE injection and a shellcode for the EternalBlue exploit.
The malicious program uses lots of fileless techniques to remain inconspicuous to the user and undetected by antivirus technologies. The victim machine is infected remotely using exploits or remote administration tools (Windows Management Instrumentation). During infection, a one-line PowerShell script is run that downloads the miner’s body and immediately launches it without writing it to the hard drive.
What the script does after that can be broken down into several stages:
- Automatic self-update. PowerGhost checks if a new version is available on the C&C. If there is, it downloads the new version and launches it instead of itself.
- Propagation.With the help of mimikatz, the miner obtains the user account credentials from the current machine, uses them to log on and attempts to propagate across the local network by launching a copy of itself via WMI. By “a copy of itself” here and below we mean the one-line script that downloads the miner’s body from the C&C.
PowerGhost also tries to spread across the local network using the now-notorious EternalBlue exploit (MS17-010, CVE-2017-0144). - Escalation of privileges. As the miner spreads via mimikatz and WMI, it may end up on a new machine with user rights. It will then attempt to escalate its privileges in the system with the 32- or 64-bit exploits for MS16-032, MS15-051 and CVE-2018-8120.
- Establishing a foothold in the system. PowerGhost saves all the modules as properties of a WMI class. The miner’s body is saved in the form of a one-line PowerShell script in a WMI subscription that activates every 90 minutes.
- Payload.Lastly, the script launches the miner by loading a PE file via reflective PE injection.
In one PowerGhost version, we detected a tool for conducting DDoS attacks. The malware writers obviously decided to make some extra money by offering DDoS services.
It’s worth pointing out that this is the only one of the miner’s functions that copies files to the hard drive. This is quite possibly a test tool that will later be replaced with a fileless implementation. Also supporting the assertion that this function was added to this version as an afterthought is the peculiar way the DDoS module is launched: the script downloads two PE modules, logos.png and cohernece.txt. The former is saved to the hard drive as java-log-9527.log and is an executable file for conducting DDoS attacks. The file cohernece.txt is protected with the software protection tool Themida, complete with a check for execution in a virtual environment. If the check does not detect a sandbox, then cohernece.txt launches the file java-log-9527.log for execution. In this curious way, the ready DDoS module was supplemented with a function to check for execution in a virtual environment.
Statistics and geography
Corporate users bore the brunt of the attack: it’s easier for PowerGhost to spread within a company’s local area network.
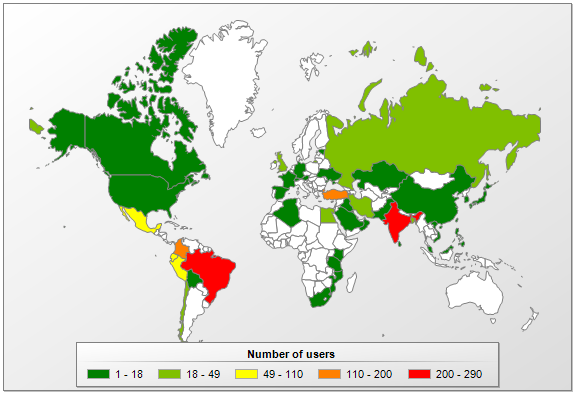
PowerGhost is encountered most often in India, Brazil, Columbia and Turkey.
Kaspersky Lab’s products detect the miner and/or its components with the following verdicts:
- PDM:Trojan.Win32.Generic
- PDM:Exploit.Win32.Generic
- HEUR:Trojan.Win32.Generic
- not-a-virus:HEUR:RiskTool.Win32.BitMiner.gen
E-wallets at nanopool.org and minexmr.com:
43QbHsAj4kHY5WdWr75qxXHarxTNQDk2ABoiXM6yFaVPW6TyUJehRoBVUfEhKPNP4n3JFu2H3PNU2Sg3ZMK85tPXMzTbHkb
49kWWHdZd5NFHXveGPPAnX8irX7grcNLHN2anNKhBAinVFLd26n8gX2EisdakRV6h1HkXaa1YJ7iz3AHtJNK5MD93z6tV9H
Indicators of compromise
C&C hostnames:
- update.7h4uk[.]com
- 185.128.43.62
- info.7h4uk[.]com
MD5:
AEEB46A88C9A37FA54CA2B64AE17F248
4FE2DE6FBB278E56C23E90432F21F6C8
71404815F6A0171A29DE46846E78A079
81E214A4120A4017809F5E7713B7EAC8























A mining multitool