
The year in figures
In 2015, Kaspersky Lab detected the following:
- 2,961,727 malicious installation packages
- 884,774 new malicious mobile programs – a threefold increase from the previous year
- 7,030 mobile banking Trojans
Trends of the year
- Rise in the number of malicious attachments the user is unable to delete.
- Cybercriminals actively using phishing windows to conceal legitimate apps.
- Growth in the volume of ransomware.
- Programs using super-user rights to display aggressive advertising.
- Increase in the quantity of malware for iOS.
Main methods of monetization
Mobile malware continues to evolve towards monetization, with malware authors trying to ensure their creations are capable of making money from their victims.
Stealing money from user bank accounts
Mobile Trojans targeting user bank accounts continue to develop – in 2015, we detected 7,030 new mobile banking Trojans. Some malicious mobile programs work in combination with Windows-based Trojans to capture mTAN passwords (one-time passwords used in two-factor authentication) that are used for authorizing bank transactions. Many of the other mobile programs used to steal money from user bank accounts operate independently.
Some mobile malware is capable of overlaying the on-screen display of a legitimate banking app with that of a phishing window that imitates the app. The most notable examples of this type of program are Trojan Trojan-SMS.AndroidOS.OpFake.cc and the representatives of the Trojan-Banker.AndroidOS.Acecard family. One of the OpFake.cc modifications can imitate the interface of more than 100 legitimate banking and finance apps. The Acecard family can imitate at least 30 banking apps and also has functionality to overlay any app that the C&C server commands.
In 2015, Kaspersky Lab detected 2.96 mln malicious installation packages #KLreport
Tweet
In Q2 2015, we wrote about Trojan-Spy.AndroidOS.SmsThief.fc whose malicious code was embedded in a legitimate banking app without affecting its performance. This meant it was highly unlikely a user would notice the malware.
The authors of mobile malware are taking an increasingly integrated approach to stealing money: it is no longer limited to special banking Trojans targeting banking apps.
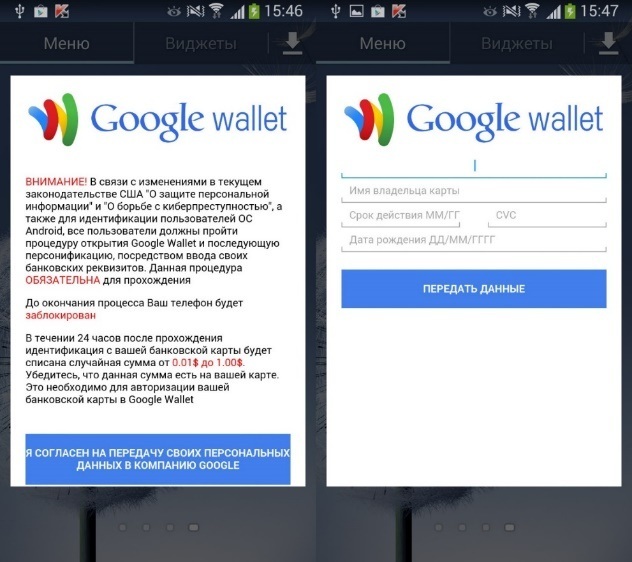
An example of this approach is Trojan-SMS.AndroidOS.FakeInst.ep. What the users see is a message, purportedly from Google, demanding that they open Google Wallet and go through an ‘identification’ procedure that involves entering their credit card details (one of the reasons given is the need to combat cybercrime). The window cannot be removed until the victim enters their credit card details.
Once users enter the required data, it is sent to attackers, and the window closes. Meanwhile, the Trojan continues to steal information and send additional information to its owners about the smartphone and its user.
Against a background of slowing growth in the number of specialized banking Trojans, the total number of apps that can steal money from users is growing. This comes at a time when banking Trojans are becoming more sophisticated and versatile – they are often capable of attacking customers of dozens of banks located in a variety of countries. This means cybercriminals do not need lots of different files to attack the customers of different banks.
Ransomware
The amount of Trojan-Ransom families doubled in 2015 compared to the previous year, while the number of detected modifications increased 3.5 times. This means some criminals are switching to ransomware to steal money, and those who were already doing so are continuing to create new versions of the malware. Yet another key indicator confirming the importance of this class of threat is the number of people who were attacked: in 2015, this figure increased fivefold.
In most cases when these Trojans block a device, the user is accused of committing some alleged misdemeanor, and has to pay to unblock the device – the ransom can range from $12 to $100. The blocked device is rendered inoperable – the user only sees a window with the ransom demand. Some Trojans are capable of overlaying system dialog boxes, including those used to switch off the phone.
The window opened by Fusob
At the end of the year we detected several Trojan downloaders that downloaded Trojan-Ransom.AndroidOS.Pletor in the system. These Trojan downloaders exploit vulnerabilities in the system to gain super-user privileges on the device and install Trojan-Ransom malware in the system folder. Once installed, this Trojan is almost impossible to remove.
SMS Trojans remained a serious threat, particularly in Russia. These programs send paid text messages from an infected device without the user being aware. Although their share in the overall flow of mobile threats continues to decline, the number of SMS Trojans in absolute terms remains substantial.
Some SMS Trojans are not limited to the sending of text messages to premium numbers; they can also connect the user to paid subscriptions. In 2015, we kept track of how Trojan-SMS.AndroidOS.Podec – still one of the most popular Trojans among cybercriminals – was developing. This Trojan boasts an unusual feature: its main method of monetization is paid subscriptions. It is capable of bypassing Captcha, and its latest modifications have “lost” the ability to send text messages as its creators have focused on subscriptions.
Aggressive advertising
In 2015, we recorded an increase in the number of programs that use advertising as the main means of monetization. The trend of the year was Trojans using super-user privileges. In the first quarter of 2015, the mobile malware TOP 20 contained just one Trojan of this type; by the end of the year they made up more than half of the rating. Despite the fact that these Trojans are designed to download and install advertising applications without the user’s knowledge, they can cause a lot of problems. Once installed, they try to root the device and install their own components in the system making them difficult to remove. Some of them remain on a smartphone even after resetting to factory settings. As a result, the user is inundated with annoying ads on the device. They can also install lots of other programs, including malware, on the device without the user being aware. There have been cases of this type of program being distributed in the official firmware of devices or being pre-installed on new phones.
Malware in official stores
In early October 2015 we came across several Trojans in the official Google Play Store that stole user passwords from the Russian social network VKontakte. These were Trojan-PSW.AndroidOS.MyVk.a and Trojan-PSW.AndroidOS.Vkezo.a. About a month later we detected a new modification of the Trojan Vkezo which was also distributed via Google Play Store. The attackers published these Trojans 10 times in the official app store under different names over a period of several months. The number of downloads for all versions of these Trojans was put at between 100 000 and 500 000. Yet another Trojan detected in Google Play Store was Trojan-Downloader.AndroidOS.Leech; it was also downloaded between 100 000 and 500 000 times.
Malware for iOS
In 2015, the number of malicious programs for iOS increased 2.1 times compared to 2014.
The recent emergence of malicious apps in the App Store once again demonstrated that, contrary to popular belief, iOS is not invulnerable to malware. The attackers did not hack App Store, but instead posted a malicious version of Apple’s Xcode, a free set of tools that developers use to create applications for iOS, on the Internet.
Apple’s Xcode is officially distributed by Apple, but it is unofficially spread by third parties. Some Chinese vendors prefer to download the development tools from local servers. Someone posted an Xcode version containing malicious XcodeGhost on a third-party server in China. Malicious code is embedded in any application compiled using this version of Xcode.
In 2015, Kaspersky Lab detected 885K new mobile malware – a 3x increase from the 2014 #KLreport
Tweet
XcodeGhost infected dozens of applications. Initially it was thought that 39 infected apps had bypassed the Apple testing procedure and had been successfully downloaded to the App Store. The most popular of them was WeChat, a free messenger installed on more than 700 million user devices. Apple removed the infected apps. However, the hacked version of Xcode was available for about six months, so the total number of infected applications might be much higher, not least because the source code for XcodeGhost was published on Github.
In early June, Trojan.IphoneOS.FakeTimer.a, a malicious program for iPhone, was detected. The Trojan targets users in Japan and can be installed on any iPhone because the attackers used an enterprise certificate to sign the Trojan. The malicious program uses phishing techniques to steal money. A similar version of the Trojan for Android – Trojan.AndroidOS.FakeTimer.a.that – has already been around for several years.
Statistics
In 2015, the volume of mobile malware continued to grow. From 2004 to 2013 we detected nearly 200,000 samples of malicious mobile code. In 2014 there were 295,539 new programs, while the number was 884,774 in 2015. These figures do not tell the whole story because each malware sample has several installation packages: in 2015, we detected 2,961,727 malicious installation packages.
From the beginning of January till the end of December 2015, Kaspersky Lab registered nearly 17 million attacks by malicious mobile software and protected 2,634,967 unique users of Android-based devices.
The number of attacks blocked by Kaspersky Lab solutions, 2015
The number of users protected by Kaspersky Lab solutions, 2015
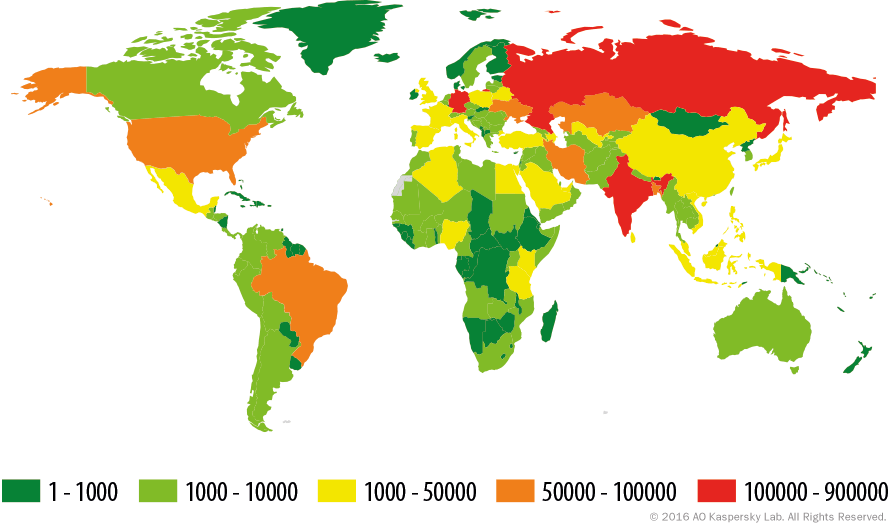
Geography of mobile threats
Attacks by malicious mobile software were recorded in more than 200 countries.
The geography of mobile threats by number of attacked users, 2015
The number of recorded attacks greatly depends on the number of users in a country. To evaluate the danger of infection by mobile malware in various countries we calculated the percentage of our users who encountered malicious applications in 2015.
TOP 10 countries by the percentage of attacked users
| Country | % of attacked users* | |
| 1 | China | 37 |
| 2 | Nigeria | 37 |
| 3 | Syria | 26 |
| 4 | Malaysia | 24 |
| 5 | Ivory Coast | 23 |
| 6 | Vietnam | 22 |
| 7 | Iran | 21 |
| 8 | Russia | 21 |
| 9 | Indonesia | 19 |
| 10 | Ukraine | 19 |
* We excluded those countries in which the number of users of Kaspersky Lab mobile security products over the reported period was less than 25,000.
** The percentage of attacked unique users as a percentage of all users of Kaspersky Lab mobile security products in the country
China and Nigeria topped the ranking, with 37% of users of Kaspersky Lab mobile security products in those countries encountering a mobile threat at least once during the year. Most of the attacks on users in Nigeria were carried out by advertising Trojans such as the Ztrorg, Leech, and Rootnik families that make use of super-user privileges, as well as by adware.
In China, a significant proportion of the attacks also involved advertising Trojans, but the majority of users encountered the RiskTool.AndroidOS.SMSreg family. Careless use of these programs can lead to money being withdrawn from a mobile account.
Types of mobile malware
Over the reporting period, the number of new AdWare and RiskTool files detected grew significantly. As a result, their share in the distribution of new mobile malware by type also increased noticeably – from 19.6% and 18.4% to 41.4% and 27.4%, respectively.
Distribution of new mobile malware by type in 2014 and 2015
When distributing adware programs, rather primitive methods are used to attract the attention of users to the advertisements: apps are created using the icons and names of popular games or useful programs. Of course, there are lots of popular games and legitimate applications, so a lot of fake advertising apps can be generated. The more fake applications that are used, the more effective the monetization of click activity is. Yet another way of distributing adware is by embedding an advertising module in a legitimate application. This can be done by the author of the application as well as by those who want to make money by exploiting an app’s popularity: when the advertising module is embedded in a clean app without the author’s knowledge, the profits from advertising go to those who added the advert, not the author. Unlike fake apps, this complex app contains some useful functionality.
The growth in the volume of adware is caused by the increasing competition among developers of these programs. The legitimate programs that use various advertising modules are often too aggressive. Increasingly, advertising modules are delivering as much advertising as possible to the user in a variety of ways, including the installation of new adware programs. Sometimes the adware programs installed on a device can make it almost impossible to use because the user is constantly fighting with advertising windows.
In 2015, Kaspersky Lab detected 7,030 mobile banking Trojans #KLreport
Tweet
RiskTool programs are especially popular in China. This is because SMS payments for content are very popular in the country. Almost any game that includes so-called internal purchases (for additional levels of a game, for example) contains an SMS payment module. In most cases, the user is notified about the potential risks associated with such purchases, but we also consider it necessary to inform our users about the risks. Because the games in question are popular, the number of RiskTool applications is constantly increasing. The main contributor to that growth was the RiskTool.AndroidOS.SMSReg family of programs.
Although AdWare and RiskTool programs do not cause direct harm to users, they can be very irritating, while RiskTool programs installed on mobile devices can lead to financial losses if used carelessly or manipulated by a cybercriminal.
The proportion of SMS Trojans in the overall flow of mobile threats decreased almost 2.4 times – from 20.5% to 8.7%. However, in 2015 we detected even more new SMS Trojans than in 2014. Activity by this type of malicious program dropped drastically in mid-2014. This was the result of an AoC (Advice-of-Charge) system being introduced by Russian operators that led to a reduction in the number of so-called affiliate programs distributing SMS Trojans, the majority of which targeted users in Russia.
Top 20 malicious mobile programs
Please note that the ranking of malicious programs below does not include potentially unwanted programs such as RiskTool or AdWare.
| Name | % of all attacked users* | |
| 1 | DangerousObject.Multi.Generic | 44.2 |
| 2 | Trojan-SMS.AndroidOS.Podec.a | 11.2 |
| 3 | Trojan-Downloader.AndroidOS.Leech.a | 8.0 |
| 4 | Trojan.AndroidOS.Ztorg.a | 7.6 |
| 5 | Trojan.AndroidOS.Rootnik.d | 6.9 |
| 6 | Exploit.AndroidOS.Lotoor.be | 6.1 |
| 7 | Trojan-SMS.AndroidOS.OpFake.a | 5.6 |
| 8 | Trojan-Spy.AndroidOS.Agent.el | 4.0 |
| 9 | Trojan.AndroidOS.Guerrilla.a | 3.7 |
| 10 | Trojan.AndroidOS.Mobtes.b | 3.6 |
| 11 | Trojan-Dropper.AndroidOS.Gorpo.a | 3.6 |
| 12 | Trojan.AndroidOS.Rootnik.a | 3.5 |
| 13 | Trojan.AndroidOS.Fadeb.a | 3.2 |
| 14 | Trojan.AndroidOS.Ztorg.pac | 2.8 |
| 15 | Backdoor.AndroidOS.Obad.f | 2.7 |
| 16 | Backdoor.AndroidOS.Ztorg.c | 2.2 |
| 17 | Exploit.AndroidOS.Lotoor.a | 2.2 |
| 18 | Backdoor.AndroidOS.Ztorg.a | 2.0 |
| 19 | Trojan-Ransom.AndroidOS.Small.o | 1.9 |
| 20 | Trojan.AndroidOS.Guerrilla.b | 1.8 |
* Percentage of users attacked by the malware in question, relative to all users attacked
First place is occupied by DangerousObject.Multi.Generic (44.2%), used in malicious programs detected by cloud technologies. Cloud technologies work when the antivirus database contains neither the signatures nor heuristics to detect a malicious program, but the cloud of the antivirus company already contains information about the object. This is basically how the very latest malware is detected.
Trojan-SMS.AndroidOS.Stealer.a, which was the TOP 20 leader in 2014, came 28th in 2015.
Four places in the TOP 20 are occupied by Trojans that steal money from mobile or bank accounts as their main method of monetization. They are Trojan-SMS.AndroidOS.Podec.a, Trojan-SMS.AndroidOS.OpFake.a, Trojan.AndroidOS.Mobtes.b and Backdoor.AndroidOS.Obad.f. Trojan-SMS.AndroidOS.Podec.a (11.2%) is in second place. This Trojan remained among the top three most popular mobile threats throughout 2015. To recap, the latest versions of this Trojan no longer send paid text messages. The Trojan is now fully focused on paid subscriptions, making use of CAPTCHA recognition. Trojan-SMS.AndroidOS.OpFake.a (5.6%) in 7th place is another long-term resident of the TOP 20. In 2014 it finished in 8th place and remained in the rating throughout all of 2015.
Yet another Trojan – Trojan-Ransom.AndroidOS.Small.o (1.9%) – blocks the victim’s phone and extorts money to unblock it. This mobile Trojan-Ransom program was very popular at the end of 2015 and became the only ransomware program to make the TOP 20. It first appeared in the ranking in the third quarter of 2015 in 11th place; it came 19th in the overall TOP 20 for 2015. The Trojan mostly spreads as a porn video player and targets Russian-speaking audiences.
Trend of 2015: programs using super-user rights to display aggressive advertising #KLreport
Tweet
More than half (12 out of 20) of the entries in the ranking are Trojans that use aggressive advertising as their primary means of monetization. They are Trojan-Downloader.AndroidOS.Leech.a, Trojan-Spy.AndroidOS.Agent.el, Trojan-Dropper.AndroidOS.Gorpo.a, Trojan.AndroidOS.Fadeb.a, and two modifications each of Trojan.AndroidOS.Guerrilla, Trojan.AndroidOS.Rootnik, Trojan.AndroidOS.Ztorg and Backdoor.AndroidOS.Ztorg. Unlike the usual advertising modules, these programs do not contain any useful functionality. Their goal is to deliver as many adverts as possible to the recipient using a variety of methods, including the installation of new advertising programs. These Trojans can use super-user privileges to conceal their presence in the system folder, from where it will be very difficult to dislodge them. We have come across such Trojans before, mostly in China. There was a burst of activity by these programs in 2015: most of them targeting users in China, although these Trojans have started being actively distributed worldwide. The code of the Trojans often contained the word oversea.
The other two places in the TOP 20 are occupied by Exploit.AndroidOS.Lotoor modifications used to obtain local super-user privileges.
Mobile banking Trojans
In 2015, we detected 7,030 mobile banking Trojans, which is 2.6 times less than in 2014 when 16,586 were detected. It should be noted that although the number of new malware programs fell from the previous year, these programs have become more adept and malign, and the areas of interest among cybercriminals now includes banks in numerous countries. Many mobile banking Trojans act independently, without any computer component, and target customers of dozens of banks around the world.
Number of mobile banking Trojans detected by Kaspersky Lab solutions in 2015
56,194 users were attacked by mobile banking Trojans at least once during the year.
Geography of mobile bankers
The number of attacked countries is growing: attacks by mobile banking Trojan were registered in 137 countries and territories worldwide vs 90 countries in 2014.
Geography of mobile banking threats in 2015 (number of users attacked)
Top 10 countries attacked by mobile banking Trojans (ranked by number of users attacked):
| Country | Number of users attacked | |
| 1 | Russia | 45690 |
| 2 | Germany | 1532 |
| 3 | Ukraine | 1206 |
| 4 | US | 967 |
| 5 | Kazakhstan | 804 |
| 6 | Australia | 614 |
| 7 | South Korea | 527 |
| 8 | France | 404 |
| 9 | Belarus | 380 |
| 10 | Poland | 324 |
As in the previous year, Russia topped the rating of countries attacked by mobile banking Trojans. Among the newcomers were South Korea, Australia, France and Poland. Lithuania, Azerbaijan, Bulgaria and Uzbekistan left the TOP 10.
Just how popular mobile banking Trojans are with cybercriminals in each country can be shown by the percentage of users who were attacked by these Trojans during the reporting period, relative to all attacked users.
TOP 10 countries by the percentage of users attacked by mobile banking Trojans relative to all attacked users
| Country | % of all attacked users* | |
| 1 | South Korea | 13.8 |
| 2 | Australia | 8.9 |
| 3 | Russia | 5.1 |
| 4 | Austria | 3.0 |
| 5 | Belarus | 1.9 |
| 6 | US | 1.8 |
| 7 | Tajikistan | 1.7 |
| 8 | Ukraine | 1.6 |
| 9 | France | 1.6 |
| 10 | Uzbekistan | 1.6 |
* Percentage of users attacked by mobile banking Trojans, relative to all attacked users of Kaspersky Lab’s mobile security products in the country.
A substantial portion of mobile banking attacks in South Korea were caused by representatives of the Trojan-Banker.AndroidOS.Wroba family. These Trojans are designed to steal mobile bank accounts of the largest Korean banks as well as mTans.
In Australia, the Trojan-Banker.AndroidOS.Acecard family was responsible for most infection attempts. This family is a new stage in the evolution of Backdoor.AndroidOS.Torec.a, the first Trojan for Android that made use of Tor. We detected this Trojan at the beginning of 2014, while the first banking modifications appeared in mid-2014. At that time the Trojan was distributed mainly in Russia, and only in 2015 did it begin to spread actively in Australia. One modification, which we detected in November 2015, is able to overlay the interfaces of 24 banking apps with a phishing window. Five of those apps belong to Australian banks, another four each belong to banks based in Hong Kong, Austria and New Zealand, three each to banks in Germany and Singapore, plus the PayPal app. In addition, there are modifications which target banks in the US and Russia.
Phishing windows of the Acecard Trojan
Stealing user logins and passwords by displaying a phishing window instead of the genuine app interface is not a new trick. We first came across it back in 2013 in Trojan-SMS.AndroidOS.Svpeng. In our IT threat evolution in Q1 2015 report we mentioned Trojan-SMS.AndroidOS.OpFake.cc which was capable of attacking at least 29 banking and financial apps. The latest modification of this Trojan can now attack 114 banking and financial apps. Its main goal is to steal the login credentials for bank accounts. It also overlays the windows of several popular mail applications.
In Russia, which ranked third in the TOP 10, Trojan-Banker.AndroidOS.Faketoken and Trojan-Banker.AndroidOS.Marcher were the most popular programs used by attackers. Starting in April, we saw a sharp drop in the number of attempts to infect users with representatives of the Trojan-Banker.AndroidOS.Marcher family. During the five months from April to August, the number of attacks using this Trojan decreased fivefold. It is possible that the cybercriminals were preparing attacks on users in other countries during that time, because until September 2015 activity by this family was limited almost exclusively to Russia. From September, however, about 30% of the attacks using this Trojan targeted users in Australia, Germany and France.
The aforementioned Trojan-Spy.AndroidOS.SmsThief.fc was distributed in Russia. The attackers added their code to the original banking app without affecting its performance, making this Trojan more difficult to detect.
Mobile Trojan-Ransom
In 2015, the amount of the Trojan-Ransom families doubled compared to 2014. The number of modifications detected during the same period increased 3.5 times and accounted for 6,924.
Over the reporting period, mobile ransomware attacked 94,344 unique users which is five times more than in 2014 (18,478). The share of unique users attacked by Trojan-Ransom programs relative to all users attacked by mobile malware increased from 1.1% to 3.8% during the year.
Mobile ransomware attacks were registered in 156 countries and territories at least once during the year.
Geography of mobile ransomware threats in 2015 (number of users attacked)
TOP 10 countries attacked by Trojan-Ransom malware by the number of attacked users:
| Country | Number of attacked users | |
| 1 | Russia | 44951 |
| 2 | Germany | 15950 |
| 3 | Kazakhstan | 8374 |
| 4 | US | 5371 |
| 5 | Ukraine | 4250 |
| 6 | UK | 2878 |
| 7 | Italy | 1313 |
| 8 | Spain | 1062 |
| 9 | Iran | 866 |
| 10 | India | 757 |
Russia, Germany and Kazakhstan were the countries attacked most often by ransomware.
In Russia and Kazakhstan, the Trojan-Ransom.AndroidOS.Small family was most active, in particular the modification Trojan-Ransom.AndroidOS.Small.o, the most popular Trojan-Ransom program in 2015.
The Trojan-Ransom.AndroidOS.Pletor family also remained very popular in 2015. Interestingly, this first mobile encryptor Trojan was developed by the same group of cybercriminals as Trojan-Banker.AndroidOS.Acecard.
In Germany, Trojan-Ransom.AndroidOS.Fusob was the most actively distributed family.
Windows opened by the Fusob Trojan
The US came fourth in the ranking. The Trojan-Ransom.AndroidOS.Fusob family was especially popular in the country, although the Trojan-Ransom.AndroidOS.Svpeng family was also actively used.
Trend of 2015: cybercriminals actively using phishing windows to conceal legitimate apps #KLreport
Tweet
This ranking depends to a large extent on the number of users in each country, so it is interesting to view a rating that shows the proportion of users attacked by Trojan-Ransom malware relative to all attacked users in the country.
TOP 10 countries attacked by Trojan-Ransom malware – share of users relative to all attacked users in the country.
| Country | % of all attacked users* | |
| 1 | Kazakhstan | 15.1 |
| 2 | Germany | 14.5 |
| 3 | US | 10.3 |
| 4 | Canada | 8.9 |
| 5 | Netherlands | 8.8 |
| 6 | UK | 8.3 |
| 7 | Switzerland | 6.9 |
| 8 | Austria | 6.4 |
| 9 | Ukraine | 5.9 |
| 10 | Australia | 5.5 |
* Percentage of users attacked by Trojan-Ransom malware, relative to all attacked users of Kaspersky Lab’s mobile security products in the country
Russia, which accounted for the largest number of attacked users, was not in the TOP 10. The leaders of the ranking were Kazakhstan, Germany and the US.
Conclusion
Despite the fact that the first advertising Trojans exploiting super-user privileges for their own purposes appeared a few years ago, in 2015 their number increased substantially and started spreading rapidly. In the first quarter of 2015 the most popular threats included just one Trojan of this type, but by the end of the year these programs accounted for more than half of the TOP 20. They are distributed using all available means – via other advertising programs, via app stores and can be even pre-installed in some devices. The number of advertising Trojans using super-user privileges will most likely continue to grow in 2016.
We have already seen cases when advertising Trojans were used to spread malicious mobile programs. There is every reason to believe that attackers will increasingly use these Trojans to infect mobile devices with malware.
We also came across cases where super-user privileges were utilized by other types of malware, especially ransomware.
Trojan-Ransom malware is likely to continue evolving in 2016. We expect the popularity of these programs among attackers to grow and their global reach to increase.
Another type of Trojan that we intend to continue monitoring closely in 2016 is Trojan-Banker. There are already lots of banking Trojans that do not require additional software on the victim’s computer. These Trojans operate independently, and only need to infect the user’s phone to steal his money. They are able to steal logins and passwords for mobile banking accounts by overlaying the legitimate banking app interfaces with a phishing window. The Trojans can also steal credit card data using phishing windows. In addition, they have functionality to intercept communications between a client and a bank – stealing incoming text messages and forwarding calls to the attacker. In 2016, banking Trojans will attack even more banking institutions and will use new distribution channels and new data theft technologies.
As the functionality of mobile devices and mobile services grows, the appetite of cybercriminals who profit from mobile malware will grow too. Malware authors will continue to improve their creations, develop new technologies and look for new ways of spreading mobile malware. Their main aim is to make money. In these circumstances, neglecting to protect your mobile devices is extremely risky.




























Mobile malware evolution 2015