
This report covers 2005, and provides an overview of the evolution of malware targeting platforms other than Windows. It includes information on trends; information based on statistics collected throughout 2005, and concludes with forecasts as to how malware for non-Windows platforms is likely to evolve in the near future.
Introduction
Computing history and computer virology did not begin with Windows. Nor did they begin with DOS. The first computer virus, a worm which appeared in 1988, was written for Unix. However, computer virology only really started to evolve with the appearance of millions of machines running under DOS, and then under Windows. Malware evolution reflects the evolution of the computer industry as a whole: the popularity of a platform can be gauged by the number of viruses found in the wild which target the specific platform.
The leading platform is, of course, intel + Win32 (Win32 as a software platform, intel as a hardware platform). More specifically, 32 bit intel is currently the most widely targeted platform. However, the situation is likely to change in the near future as 64 bit platforms become more widely used. Indeed, several proof of concept viruses for Win64 have already been created.
However, where there’s a mainstream, there’s always an alternative. At one point in time, the main alternative to Windows was OS/2. Today, the alternatives are Linux, FreeBSD and other flavours of Unix. Linux, with its wide variety of implementations, is the undoubted leader. Slowly but surely Linux is being chosen over Windows not only for servers, but also for desktops. MacOS X’s start may also rise; since Apple has switched to intel processors, Macintosh is rapidly gaining popularity.
End user machines are the main target for malware attacks. Trojan programs such as Trojan-Spy, Trojan-Downloader and Trojan-Dropper make up the majority of malicious programs for Win32. In contrast to this, most malicious programs targeting systems running Linux are backdoors. These programs provide remote malicious users with full access to the compromised machine, which can then be used as a launch pad for attacks on other machines.
As soon as a platform starts becoming more popular, viruses and other malicious programs for this platform will begin to appear. Initially, such programs will be proof-of-concept (PoC); they are designed to show that it is possible to infect a machine in a particular way, and do not, as a rule, have a malicious payload. Firstly, information about a specific vulnerability in an operating system or an application will be made public. This information is then used to create exploits or backdoors which target the vulnerability. Of course, software developers issue patches for known vulnerabilities, but this results in virus writers searching for new methods and weak spots to attack. Overall, malware gains momentum in a snowball like fashion. This is what is currently happening with Win32; although this has not yet happened with malware for other platforms, the key phrase here is almost certainly ‘not yet’.
In spite of the relative peace enjoyed by non-Windows users, alternative platforms are also subject to attack by malicious programs. The following sections of this report cover certain features of alternative platforms and evolutionary trends.
Statistics
The process of malicious code evolution has been described above in detail to enable better understanding and interpretation of the data presented below.
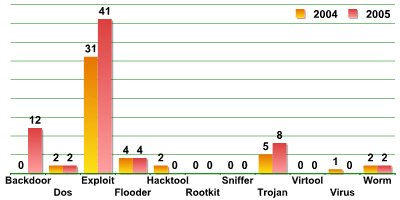
Information in this section covers the evolution of malware for unix type systems. The graph below shows that in comparison with 2004, there was a significant increase in all types of malicious program classified by Kaspersky Lab as MalWare.
 |
The almost 100% increase on last year’s figures shows that virus writers are almost overwhelmingly targeting systems running Linux.
This is not at all surprising as Linux is the most popular Unix-type system. It should be mentioned that in spite of the fact that Linux functions on a variety of RISC platforms, binary files which differ from x86 occur very rarely. Under other RISC platforms, such as SPARC, it would be more common to encounter binary files for SunOS. As a rule, such samples are usually a collection of small utilities which are written and compiled for specific versions of an operating system, and designed to target a specific server; for example, a sniffer, backdoor, logcleaner, and kernel modules to mask the attacker’s actions – such a collection is called a rootkit. Rootkits are designed for an attack on a particular machine; such a specific attack is far harder to combat than a Trojan launched by a script kiddie.
The major difference between malware targeting Unix and malware targeting Win32 MalWare is the absence of packers. Packers are frequently used to hinder the detection and analysis of malicious programs. However, we have only seen UPX and a few modified versions used in Unix malware.
Overall, in terms of types of malicious code, the Unix picture mirrors that on the Win32 front. The number of viruses which infect files on the local disk is decreasing. Such viruses are usually created for research interest only, and do not have a malicious payload; however, viruses with buggy code may deliver an unintentional malicious payload in that they corrupt the file when injecting their code. There have been no epidemics caused by Unix viruses, and in general they are viewed as ‘collection’ viruses. Nevertheless, some Unix malware is interesting: one example is Virus.Linux.Grip, which uses the brain fuck interpreter to generate key codes. The codes are then used for TEA (Tiny Encryption Algorithm) encryption.
However, this is only really of interest to researchers, and has no practical application. Those who write such viruses are, perhaps, acting on the Linus Torvalds philosophy of ‘just for fun’.
Programs which are written in order to compromise servers, so that they can then be used as platforms for future attacks, are a different matter. There are many such programs, including backdoors, exploits, sniffers, flooders and other hacktools. The number of such programs is increasing exponentially with the popularity of Linux itself.
Last year, a number of worms for Linux were detected, including Net-Worm.Linux.Lupper and Net-Worm.Linux.Mare, a variation on the theme introduced by Lupper. Both these worms exploit the same vulnerability, and have similar propagation methods. One component which the worms included was the Tsumani backdoor. As the worm evolved (i.e. as new variants were created), new functionality was added. The most recently detected variant of Net-Worm.Linux.Mare downloaded an ircbot, which acted as a backdoor.
Another malware incident in the Linux world in 2005 occurred in September, when a Korean Mozilla distribution placed on a public server was found to be infected. The distribution contained binary files infected with Virus.Linux.Rst.
These were the only significant events caused by Linux malware in 2005. In comparison with the epidemics caused by Scalper and Slapper in 2002 and 2003, it was a quiet year.
Rootkits are a hot topic for the media; however, in contrast to the extensive activity in the Win32 world, there has been no really new rootkits for Linux, simply variations on old themes.
As for other Unix platforms, the situation is even quieter. However, this is understandable; after all, other Unix platforms cannot compete either with Linux or Windows in terms of popularity.
The data presented below has been compiled from repeated analysis of the Kaspersky Lab antivirus databases at varying points in time. Some categories contain no data; this means that the Kaspersky Lab collection does not contain any malware targeting the designated platform from these families.

|

|

|
|
| . |
The future
It’s well known that making predictions is a risky game, as anything can happen in the course of six months. However, we’re going to take that risk.
Above all, the era of 64 bit architecture is dawning; once such architecture is firmly entrenched on users’ machines, virus writers will react to this fact. There are of course complications here, such as the fact that binary code for AMD64 and for IA64 are different, and this means that separate versions will have to be compiled for each platform.
Apple gives even more scope for development and malware evolution; the move to intel processors may be revolutionary. The fact that Apple computers have excellent design, and that OS X could be called ‘Unix with a human face’ may make it a hit among PC users.
The OS X kernel is based on FreeBSD, and the experience and ideas applied to the creation of malware for FreeBSD may also be applied to create OS X malware. In addition to this, the operating system developers have also made errors. Over the past few weeks, we’ve seen two proof of concept worms for OS X, and these clearly illustrate errors in the system architecture. There has also been an exploit for the Safari web browser, which makes it possible to launch a script and execute commands on the user’s computer. It therefore seems clear that OS X may be fertile soil for security researchers.
Another rapidly developing arena is mobile devices. Here Linux is also offered as an alternative to Symbian and Windows Mobile. Many major manufacturers have either already developer, or planning to offer devices with Linux. The only thing that is needed to encourage the evolution of Linux mobile malware is a critical mass of users.
It may be that the development of some, as yet unknown or little used, technology will also act as a stimulus for malware evolution. Technologies and propagation methods which seem exotic today – – such as Bluetooth a few years ago – may shortly become industry standard for mobiles and PCs alike.


















2005: *nix Malware Evolution