
.one ransomware decrypted
While we have previously written on the now infamous XPan ransomware family, some of it’s variants are still affecting users primarily located in Brazil. Harvesting victims via weakly protected RDP (remote desktop protocol) connections, criminals are manually installing the ransomware and encrypting any files which can be found on the system.
Interestingly, this XPan variant is not necessarily new in the malware ecosystem. However, someone has chosen to keep on infecting victims with it, encouraging security researchers to hunt for samples related to the increasing number of incident reports. This sample is what could be considered as the “father” of other XPan ransomware variants. A considerable amount of indicators within the source code depict the early origins of this sample.
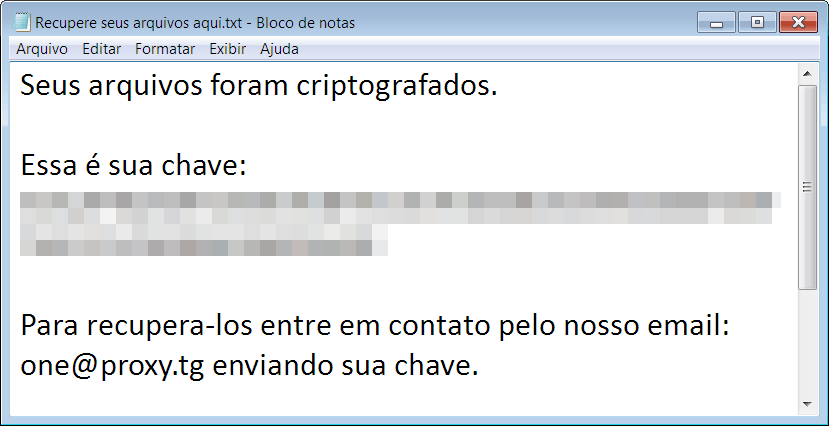
“Recupere seus arquivos aqui.txt” loosely translated to “recover your files here” is a phrase that not many Brazilian users are eager to see in their desktops.
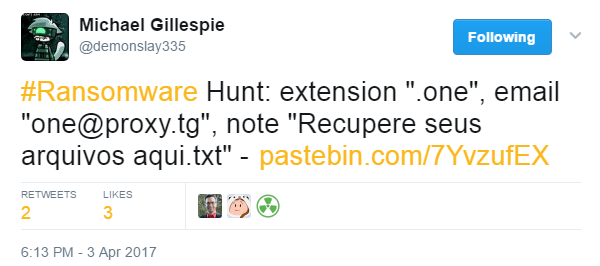
The ransomware author left a message for Kaspersky in other versions and has done the same in this one, with traces to the NMoreira “CrypterApp.cpp” there’s a clear link between different variants among this malware family.
NMoreira, XPan, TeamXRat, different names but same author.
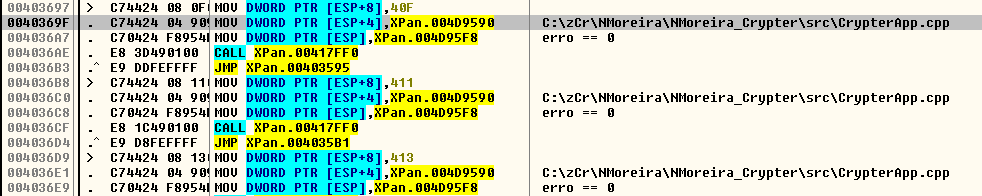
Even though many Brazilian-Portuguese strings are present upon initial analysis, there were a couple that caught our attention. Firstly, the ransomware uses a batch file which will pass a command line parameter to an invoked executable file, this parameter is “eusoudejesus” which means “I’m from Jesus”. Developers tend to leave tiny breadcrumbs of their personality behind in each one of their creations, and in this sample we found many of them.
A brief religious reference found in this XPan variant.
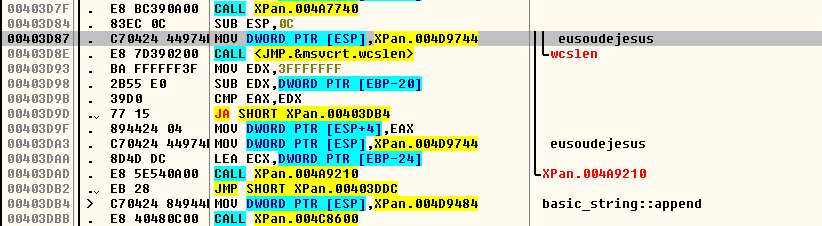
Secondly, a reference to a Brazilian celebrity is done, albeit indirectly. “Computador da Xuxa” was a toy computer sold in Brazil during the nineties, however it’s also a popular expression which is used to make fun of very old computers with limited power.
This is what cybercriminals think of your encrypted computer: just a toy they can control.
“Muito bichado” equals to finding a lot of problems in these type of systems, in this case meaning that the environment in which is XPan is executing is not playing fair and the execution is quite buggy.
Lastly, we have the ransomware note demanding the victim to send an email to the account ‘one@proxy.tg’. Considering that the extension for all the encrypted files in this variant is ‘.one’ this seems like a pretty straightforward naming convention for the criminals’ campaigns.
The rescue note in Portuguese.
Upon closer inspection, we discovered that this sample is nearly identical to another version of Xpan which used to be distributed back in November 2016 and used the extension “.__AiraCropEncrypted!”. Every bit of executable code remains the same, which is quite surprising, because since that time there were several newer versions of this malware with an updated encryption algorithm. Both samples have the same PE timestamp dating back to the 31st of October 2016.
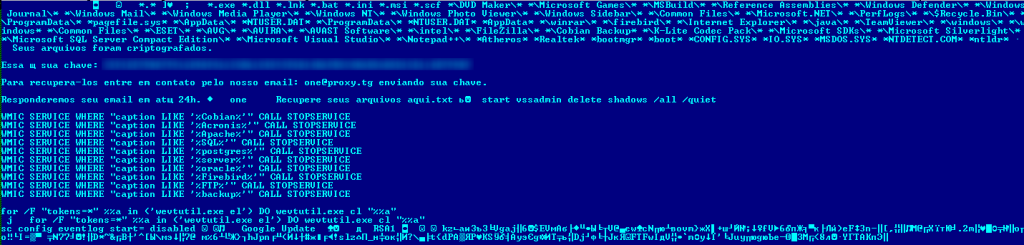
The only difference between the two is the configuration block which contains the following information:
- list of target file extensions;
- ransom notes;
- commands to execute before and after encryption;
- the public RSA key of the criminals.
The decrypted configuration block of Xpan that uses the extension “.one”.
The file encryption algorithm also remains the same. For each target file the malware generates a new unique 255-byte random string S (which contains the substring “NMoreira”), turns it into a 256-bit key using the API CryptDeriveKey, and proceeds to encrypt the file contain using AES-256 in CBC mode with zero IV. The string S will be encrypted using the criminals’ RSA public key from the configuration block and stored in the beginning of the encrypted file.
According to one of the victims that contacted us, criminals were asking for 0.3 bitcoin to provide the recovery key, using the same approach as they did with before: the user sends a message to a mailbox with his unique ID and patiently awaits for further instructions.
The victims so far are small and medium businesses in Brazil: ranging from a dentist clinic to a driving school, demonstrating once again that ransomware makes no distinctions and everyone is at risk. As long as there are victims, assisting them and providing decryption tools whenever possible is necessary, no matter the ransomware family or when it was created.
Victims: we can help
This time luck is on the victims’ side! Upon thorough investigation and reverse engineering of the sample of “.one” version of Xpan, we discovered that the criminals used a vulnerable cryptographic algorithm implementation. It allowed us to break encryption as with the previously described Xpan version.
We successfully helped a driving school and a dentist clinic to recover their files for free and as usual we encourage victims of this ransomware to not pay the ransom and to contact our technical support for assistance in decryption.
Brazilian cybercriminals are focusing their efforts in creating new and local ransomware families, attacking small companies and unprotected users. We believe this is the next step in the ransomware fight: going from global scale attacks to a more localized scenario, where local cybercriminals will create new families from scratch, in their own language, and resorting to RaaS (Ransomware-as-a-service) as a way to monetize their attacks.
MD5 reference
dd7033bc36615c0fe0be7413457dccbf – Trojan-Ransom.Win32.Xpan.e (encrypted file extension: “.one”)
54217c1ea3e1d4d3dc024fc740a47757 – Trojan-Ransom.Win32.Xpan.d (encrypted file extension: “.__AiraCropEncrypted!”)
XPan, I am your father






















Paulo Braga
Hi, I’m a vicim of this ransomware. I click on support but you have many tools for decrypt! What is the correct tool for this .one ransomware decrypt? Thanks!!!
SK
check out nomoreransom.org
Dylan666
My PC was infected by the decembre variant of NMoreira
Any news about a tool to decrypt?
Thanks in advance
gmart
my network was entire infected by .nm4 extensions. it may be a nmoreira 4 variant, any solution?