
We all know that cybercriminals will target anything and everything they can reach. And at Kaspersky, we also know that a lot of IT admins don’t look after their Internet resources. Sad but true – ask an admin if their servers are protected, and you’ll often get the answer, “Oh, come on, who needs my SQL server?”
A few months ago we set up a new honeypot (http://www.mwcollect.org) in our Japanese research centre in Tokyo. The honeypot is mainly used to collect malicious Windows executables, which it does pretty well by emulating shellcode when it finds network exploits. A side effect of using the honeypot to listen on all ports is that we get statistics (as well as unexpected data) coming in on various network ports of the host, which has a global IP address.
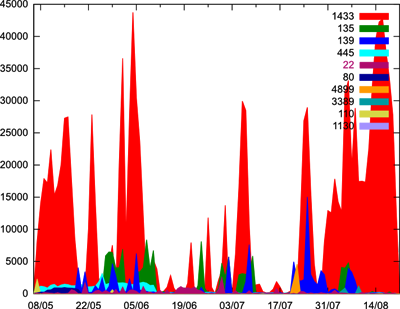
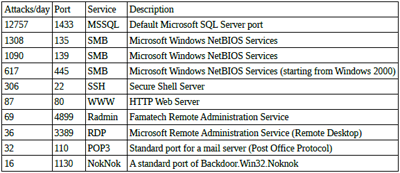
This graph shows the number of attacks and unwanted connections on specified ports of our server. It shows the ten ports most commonly used, but even the least commonly targeted port (in this case, port 1130) gets about 16 connections a day.
Here’s a table of the common services using each port:
Hopefully, this proves what seems to us to be obvious – there’s someone on the Internet who wants your SQL server! (And a few other things besides…) And the data above shows that there are a lot of bad guys looking for backdoored orphaned hosts on the internet. Some of them are trying to find Backdoor.Win32.Noknok, while others are trying to break in through legitimate services like Radmin and Windows Remote Desktop.
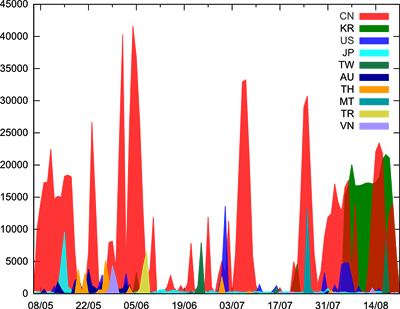
Maybe you’re wondering just who it is who is looking for badly protected resources? Here’s another graph with those details, showing how many connections different countries make to our honeypot every day:
Take a minute to compare it to the previous graph! You can see that the number of MSSQL attack attempts is mirrored by attacks coming from China. And recently, South Korean hosts have joined this massive attempt to exploit the service.
Running a honeypot helps us get valuable data; we’re kept busy analyzing it and crunching the numbers, and finally, it’s a cheap form of entertainment. Our honeypot is running on 500MHz Pentium III CPU with 384 Mb RAM, which nowadays probably costs less than $100. So if you’re thinking of throwing out some really old, slow hardware, consider setting up a honeypot! 😉





















Who needs my SQL server?