
We had a lot of responses after we published our research into wireless networks in China (specifically, in Peking and Tianjin – see here for more details). Companies with an interest in information security contacted us, as did a lot of readers of our site, www.viruslist.com. Some Kaspersky Lab local offices invited us to perform similar research in their countries. All the responses clearly indicated that wireless network security is a topic of great interest.
Our latest research was undertaken at CeBIT 2006. CeBIT, held in Hannover, Germany, is largest information security trade fair in the world, and we had good reason for choosing it as an arena for research.
Firstly, trade fairs don’t only attract users, software and hardware manufacturers. Hackers are also attracted by the opportunity to break into the networks of companies taking part in such fairs. Almost all firms which participate in such events set up their own local networks, which often connect to the company’s main server. These local networks usually have low security settings, and are set up quickly; these factors increase the risk of hacker attacks. Naturally, one of the main ways of attacking such networks is via Wi-fi.
Secondly, hackers use trade fairs not just as an opportunity to attack companies; they also target visitors. One notorious example took place at InfoSecurity London last year, when a group of scammers installed several fake access points, which provided a fake interface to connect to the public network. Unsuspecting users connected, and entered their passwords and other confidential data, and this information was sent directly to the hackers themselves.
We conducted our research on 9th and 10th March 2006, at CeBIT 2006 in Hannover. We collected data on approximately 300 access points. We did not attempt to connect to the networks we found, nor to intercept or decrypt traffic.
Wi-Fi networks
Transmission speed
During the research we detected an almost equal number of networks operating at 11Mbps (over 47%) and 54Mbps (over 51%). We also detected a small number of access points using less common transmission speeds (22, 24 and 48Mbps).
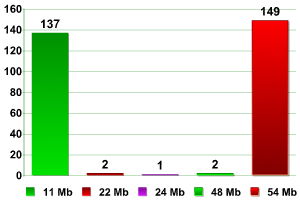
Transmission speed
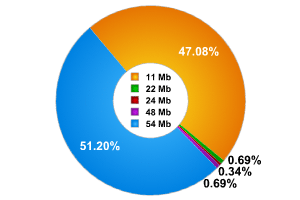
Transmission speed, %
Equipment manufacturers
We detected 18 different equipment manufacturers. 7 manufacturers were the most popular, with their equipment being used in 28% of the access points at CeBIT2006. An additional 5.5% of access points used equipment from 11 other manufacturers.
| Manufacturer | Percentage |
| Symbol | 16.15% |
| Intel | 5.50% |
| Linksys | 1.72% |
| D-Link | 1.37% |
| Netgear | 1.37% |
| Cisco | 1.03% |
| Proxim (Agere) Orinoco | 1.03% |
| Other manufacturers | 5.51% |
| Unknown, Fake, User Defined | 66,32% |
Equipment used as a percentage of the number of networks detected
These figures differ significantly from the data collected in China and Moscow. In China, the most commonly used equipment was manufactured by Agere and Cisco (Linksys), while in Moscow, Cisco and D-Link were the most common manufacturers. However, at CeBIT2006, the most commonly used equipment came from Intel (5.5%) and Symbol (16.5%). It’s likely that this discrepancy is caused by the market share which companies hold in different countries. When equipment for Wi-Fi networks is chosen, the choice is often influenced to some extent by the manufacturer’s reputation on the domestic market.
Unfortunately, in a great number of cases, we couldn’t determine the equipment manufacturer.
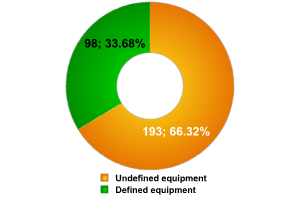
Defined / undefined equipment
It’s likely that the high percentage of cases where the manufacturer could not be determined is due to new equipment being used; such equipment is not recognized by current Wi-Fi scanners.
Encrypted traffic
War-driving research in towns around the world shows that the number of Wi-Fi networks which do not use any type of data encryption is approximately 70%. Our research in China showed a significantly lower number, with only 59% of networks having no encryption.
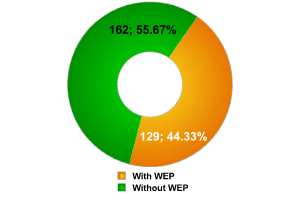
Encrypted / unecrypted networks
Less than 56% of networks have no encryption protection; this is an improvement both on international statistics, and on the statistics we collected in China. However, even if we subtract public network access points (which we detected as being available at CeBIT2006), the number of unprotected access points is unacceptably high. It should again be stressed that these points provide access to the local networks of companies participating in CeBIT – a prime target for hackers.
Types of network access
The vast majority of wireless networks throughout the world (approximately 90%) are based on ESS/AP access points. As has already been mentioned, networks at CeBIT differ significantly in terms of network infrastructure from standard networks, as the data below shows.
Among the connections we detected, more than 40% were IBSS/Peer connections. This is undoubtedly because of the temporary nature of the networks, requiring a large number of computers to be connected to each other without network cables. Such access points can be regarded as part of the companies’ internal networks.
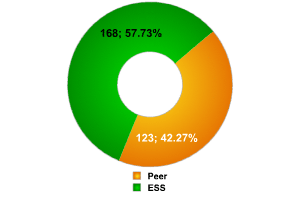
Types of network access
Default configuration
One of the most effective ways of protecting networks against war-driving is disabling SSID (Service Set Identifier). Our research showed that approximately 8% of wireless access points at CeBIT2006 had SSID disabled. Out of these, 89% used WEP encryption. There’s no question that these wireless access points are the best protected against malicious attack.
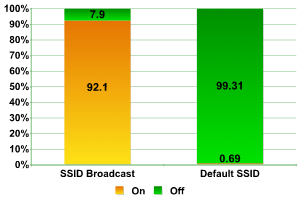
Default configuration
Another interesting result was the default SSID. As a rule, this signifies that the administrator of the access point has not changed the router’s name. It may also indicate that the administrative account uses the default password – both factors which make networks potentially vulnerable to attack. We were encouraged that only 2 access points out of nearly 300 used the default SSID, showing that administrators were aware of security issues.





















War-driving in Germany – CeBIT2006