
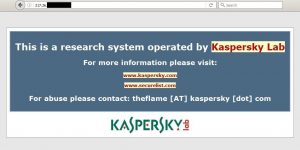
Earlier today we became aware of a malicious website delivering Petya through the Hunter exploit kit. While there is nothing special about yet another exploit kit page, this one caught our attention because it mimics the index page of our sinkhole systems.
A malicious webpage faking one of our research systems
With cybercriminals increasingly trying to exploit trust relationships in cyberspace, it’s easy to get fooled by such attempts. We believe the criminals attempted to mimic our sinkhole systems in order to avoid being shut down by other researchers.
Just last week we were investigating a case of a serious attack that potentially breached a company. When we collected proof of the attack, we had to contact the company to help them isolate compromised systems and remediate. This brought us to a problem we commonly see today: the problem of trust.
The first reaction you normally have when someone calls you and attempts to convince you must arouse suspicion. In our investigations we normally deal with security personnel, who are highly paranoid people and do not trust anyone by nature. So far, the reaction of the company’s security staff was spot on: get the name of the caller, the company and department name, look up the company contacts using an independent, trusted, verifiable source, contact the company and confirm the facts, asking to connect to the researcher in the office immediately to do additional voice recognition. When that is done, the conversation can be resumed. Such a reaction and verification process is what we consider standard in our business. Unfortunately, we haven’t seen the same level of cautiousness among regular users.
A typical strategy for cybercriminals is to try to hide their tools, exploit kits and other malicious files on a compromised legitimate website or inject a malicious payload into a hijacked banner network account. Attackers also will rip entire websites, or just replace links to redirect visitors to attacker controlled sites, as we observed with the StrongPity watering holes. In this case, they simply counted on the confusion caused by visual appearance.
The fake webpage looks exactly the same as the original one from our research server and there is no point in finding even minor differences. Every webpage on the web can be copied and made to look identical to the source, except for the page’s original address or validated SSL certificate. PGPHtml is an alternative possibility, with each page explicitly stating its host domain or IP and then signed and verified with a public key. The server in question has been reportedly serving the Pony Trojan, hosting the Hunter Exploit Kit and distributing Petya ransomware.
We believe that this was the act of Russian-speaking cybercriminals, who send messages to our side every time their activities are affected by the work we do. We are bringing this to your attention to make you a little bit more cautious. Having said that, our first reaction was laughter, because it brought back some memories of an excellent short video on this matter shot by our colleagues from the security industry. And, because of this history of receiving messages from malware authors in their code and on sites, we think it is unlikely that this site is a watering hole targeting security researchers.
Unfortunately, this game of shadows is a well-known method not only in the criminal world but also in the world of advanced targeted attackers. We have seen in the past that some APT groups use deceiving tactics in order to try to confuse security researchers into wrong attribution. We have seen malware samples in the past where attackers from one group implanted decoys, trying to mimic the behaviour of their rivals. This is done to harden the research process or consume extra time. The attribution process, being the hardest part of any computer investigation, can easily be driven in the wrong direction. However, we have been looking at these attempts for a long time and learned to recognize such false flags. Now we would like you to be cautious and verify everything you see.
Related to this topic, our colleagues recently presented a more in-depth analysis of these techniques at VB 2016. You can read their entire paper here: Wave your false flags!





















Trust me, I have a pen