
The H1 2021 ICS threat report at a glance
Percentage of ICS computers attacked
- During the first half of 2021 (H1 2021), the percentage of attacked ICS computers was 8%, which was 0.4 percentage points (p.p.) higher than that for H2 2020.
Numbers per country varied from 58.4% in Algeria to 6.8% in Israel.
Percentage of ICS computers on which malicious objects were blocked (download)

Top 15 countries and territories with the largest percentages of ICS computers on which malicious objects were blocked in H1 2021 (download)
When we look at regional numbers, Africa led with 46.1%, followed by Southeast Asia at 44.1%, East Asia at 43.1% and Central Asia at 42.1%.
Top 10 countries and territories with the lowest percentages of ICS computers on which malicious objects were blocked in H1 2021 (download)

Percentage of ICS computers on which malicious objects were blocked, by region (download)
- The largest increases in the percentage of attacked ICS computers during H1 2021 were as follows:
- Over 10 p.p. in Belarus (50.4%) and Ukraine (33.1%);
- 7.4 p.p. in the Czech Republic (20.2%) and Slovakia (24.3%);
- 6.5 p.p. in Hong Kong (20.8%);
- 6 p.p. in Australia (23%) and Cameroon (45.2%).
The internet was the main source of threats causing these increases.
- The percentage of ICS computers on which threats were blocked decreased in all monitored industries. This was especially noticeable in the oil and gas (36.5%) and building automation (40.3%) sectors (-7.5 p.p. and -6.3 p.p., respectively).

Percentage of ICS computers on which malicious objects were blocked in selected industries (download)
Major threat sources
The internet, removable media and email continue to be the main sources of threats to computers in ICS environments.
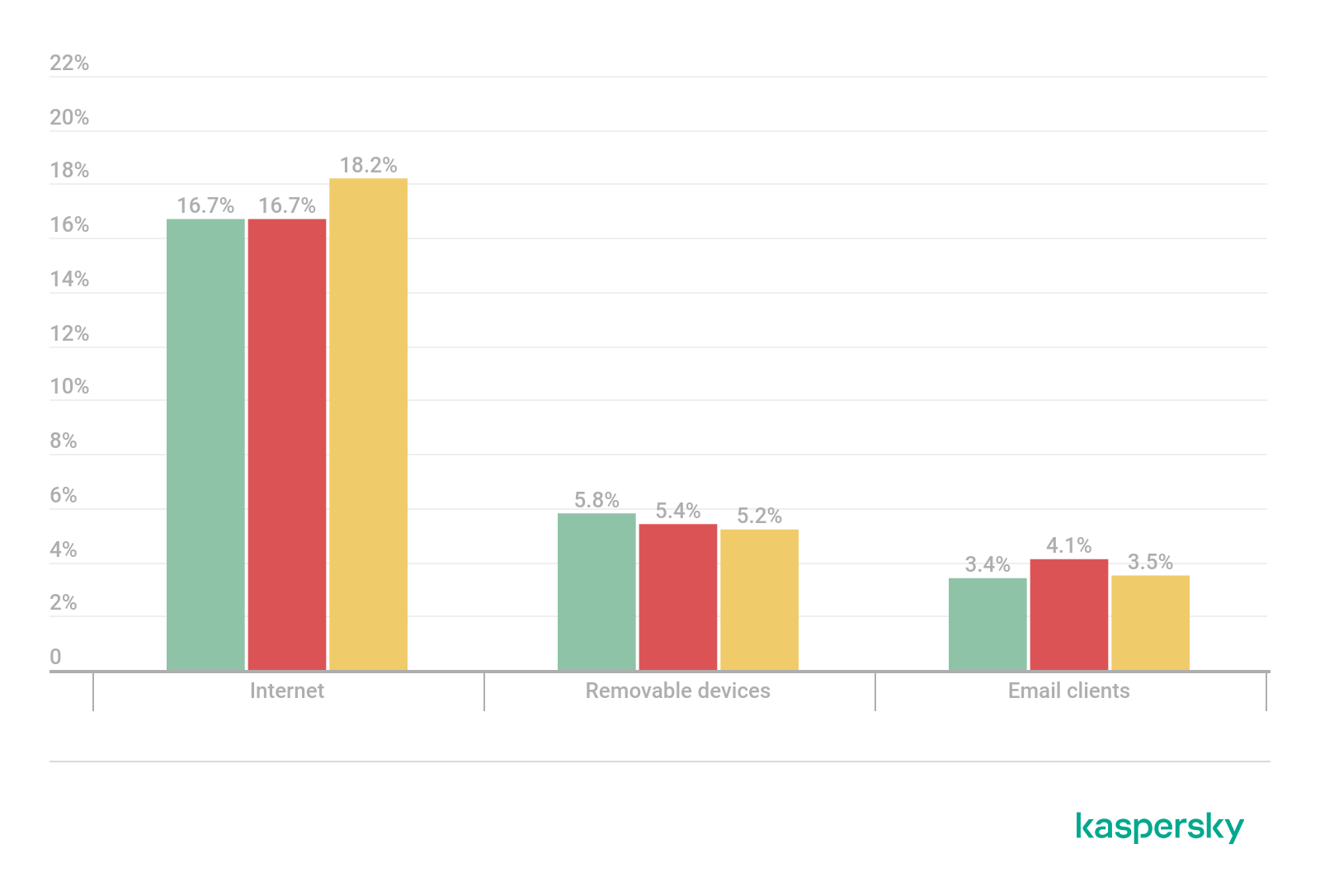
Percentage of ICS computers on which malicious objects from various sources were blocked (download)
- Threats from the internet were blocked on 18.2% of ICS computers
- (+1.5 p.p.).
In H1 2021, the largest increases in this indicator were observed in Belarus (+12.2 p.p.), Ukraine (+8 p.p.) and Russia (+6.7 p.p.)
Russia led the regional rankings with 27.6%.
Belarus leads in the country rankings with 32.8%.
Percentage of ICS computers on which malicious objects from the internet were blocked, by region (download)
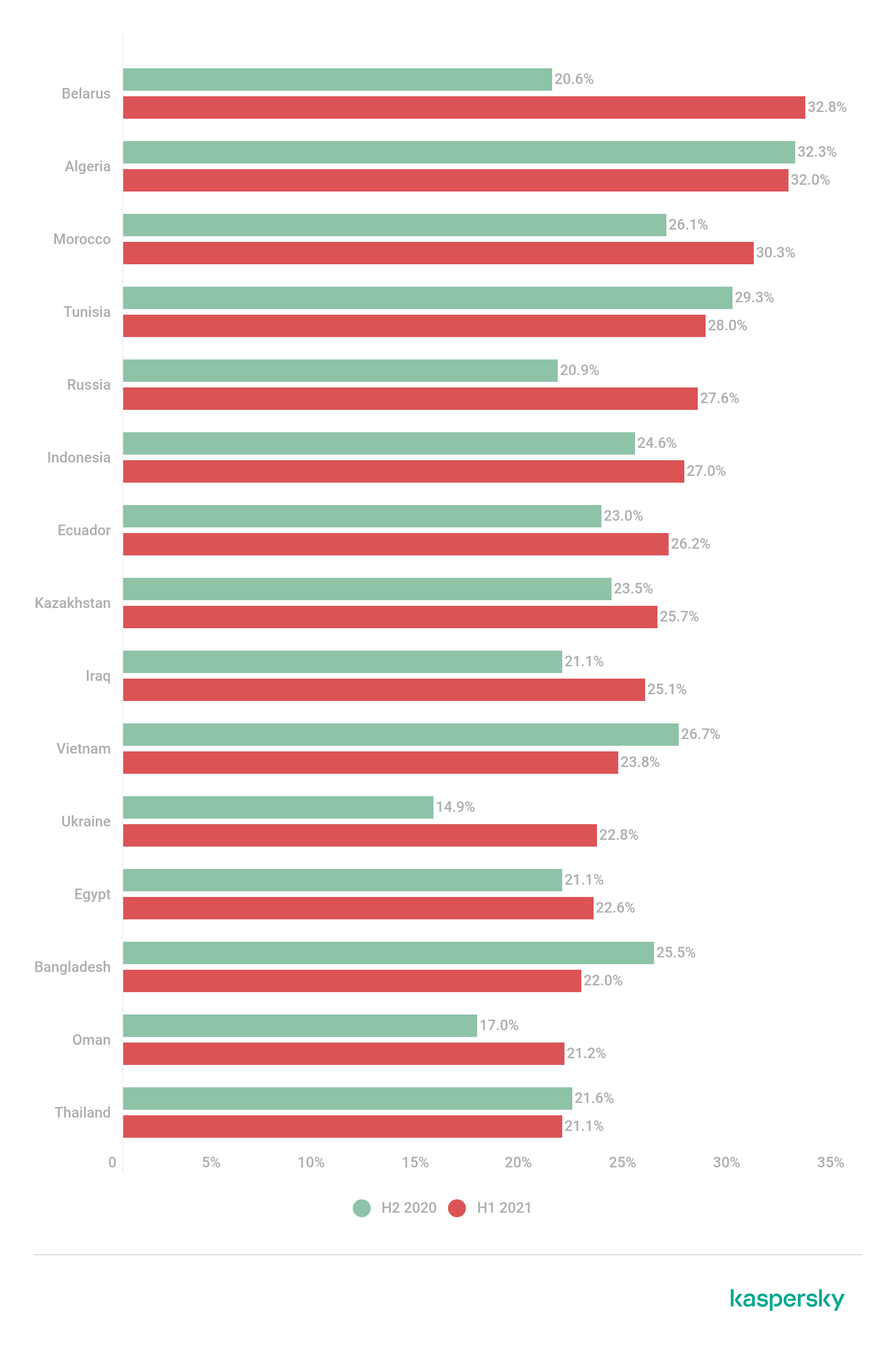
Top 15 countries and territories with the highest percentages of ICS computers on which internet threats were blocked in H1 2021 (download)
- Threats arriving via removable media were blocked on 5.2% of ICS computers (-0.2 p.p.), which continued a downward trend that began in H2 2019.
Africa leads noticeably in the regional rankings with 15.6%. In H1 2021, the percentage of ICS computers on which threats were blocked when removable media were connected decreased in Asian regions.Algeria leads among individual countries with 24%.
Regions ranked by percentage of ICS comuters on which malware was blocked when removable media was connected in H1 2021 (download)

Fifteen countries and territories with the largest percentage of ICS computers on which malware was blocked when removable media was connected in H1 2021 (download)
- Malicious email attachments were blocked on 3.4% of ICS computers (-0.6 p.p.).
Southern Europe ranked the highest with 6.4%. The only region where the percentage increased was Australia and New Zealand (+1.3 p.p.).Bangladesh led among individual countries with 8.8%.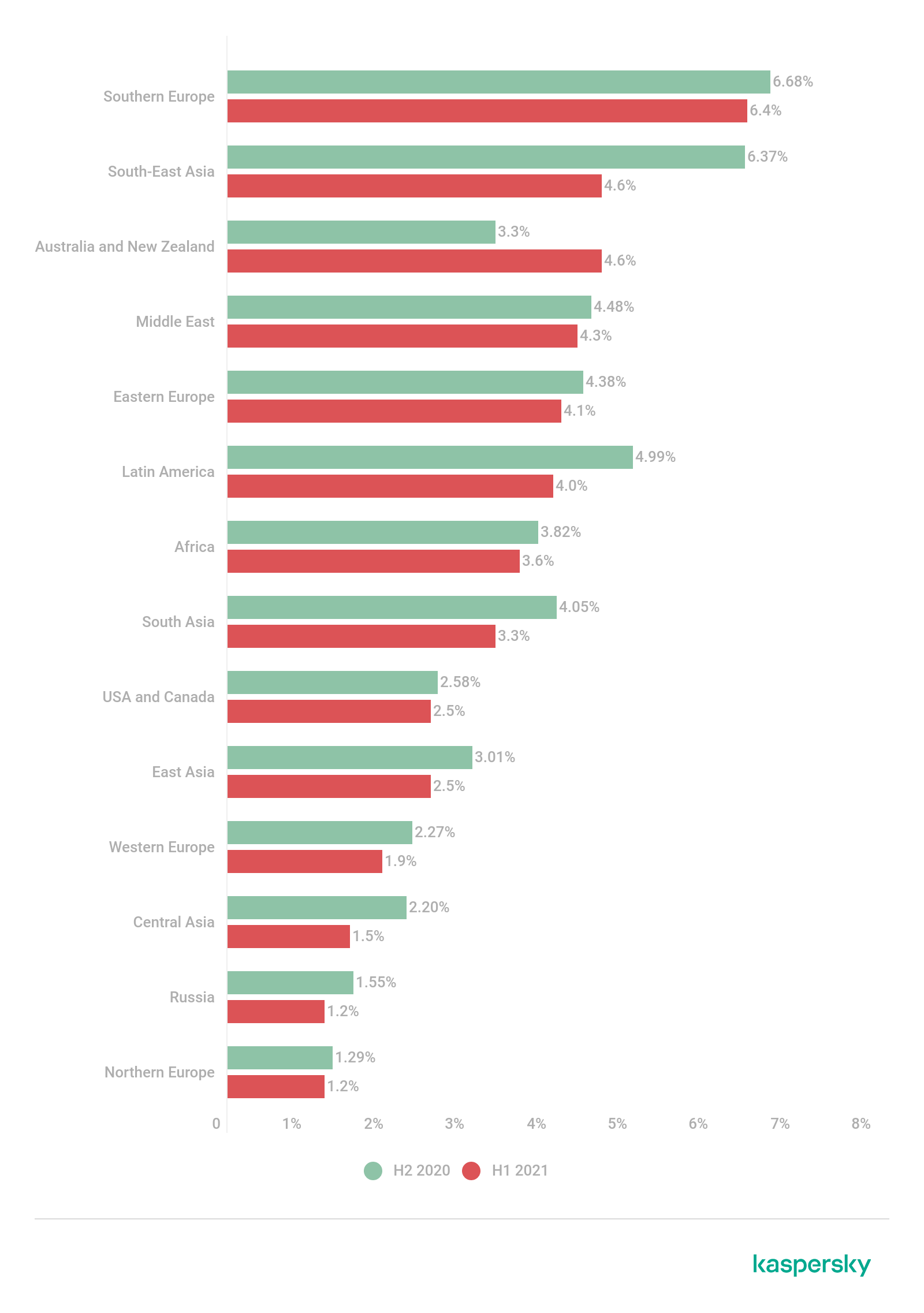
Regions ranked by percentage of ICS computers on which malicious email attachments were blocked in H1 2021 (download)

Top 15 countries with the highest percentages of ICS computers on which malicious email attachments were blocked in H1 2021 (download)
The variety of malware detected
In H1 2021, Kaspersky security solutions blocked more than 20.1 thousand malware variants from 5,150 families in ICS environments.
- Denylisted internet resources were the main threat source and were blocked on 14% of ICS computers.
Threat actors use malicious scripts on various media resources and sites hosting pirated content. These scripts redirect users to websites that spread spyware and/or cryptocurrency miners. The percentage of computers where this type of threats was blocked has grown since 2020. - Malicious scripts and redirects (JS and HTML) were blocked on 8.8% of ICS computers (+0.7 p.p.).
Australia and New Zealand (+3.8 p.p.), as well as Russia (+4.4 p.p.) saw a noticeable growth in the percentage of computers where malicious scripts used for downloading spyware were blocked. - Spyware (backdoors, trojan spies and keyloggers) were blocked on 7.4% of ICS computers (+0.4 p.p.).
This figure was highest in East Asia (14.3%), Africa (13.4%) and Southeast Asia (11.2%). - Ransomware was blocked on 0.40% of ICS computers (-0.1 p.p.)
This figure was highest in East Asia with 0.82%.In the Middle East, we saw an increase in the percentage of computers on which worms (+0.4 p.p.) and ransomware (+0.3 p.p.) were blocked.

Percentage of ICS computers on which malicious objects from various categories were blocked (download)
-
The full report is available on the Kaspersky ICS CERT website.
Threat landscape for industrial automation systems in H1 2021






















LAKHDARI ABDERRAHMANE
THANK’s