
In China telecom fraud has become an increasingly common crime. Last year there were more than 170,000 telecom fraud cases, causing the loss of over $12.5 billion. The fraudsters usually call their victims and trick them into transferring cash to a criminal gang via an ATM. But recently a new breed of telecom fraud, which combines phishing sites and backdoor Trojans, has emerged.
Last week the police from the Dongcheng sub-branch of Beijing’s Public Security Bureau asked us to help investigate a telecom fraud case. The victim was defrauded of $100,000. After our investigation, the fraudsters’ tactics were laid bare.
So how does the scam work? How was the victim deceived?
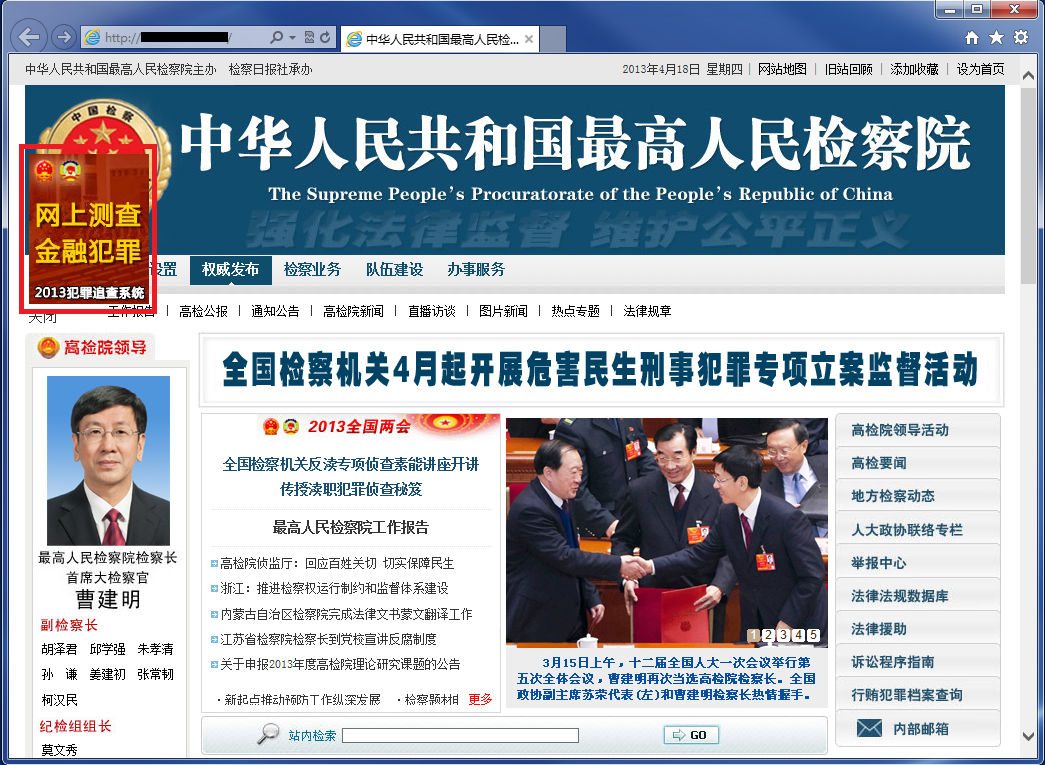
First you get a call from a ‘public prosecutor’ saying that you are implicated in a financial crime and you must help with the investigation. Of course, you deny everything, but the ‘public prosecutor’ advises you to check if you are listed in an official database as a suspected criminal. To do this, they tell you to visit the “Supreme Procuratorate’s” website, which is, of course, a phishing site:
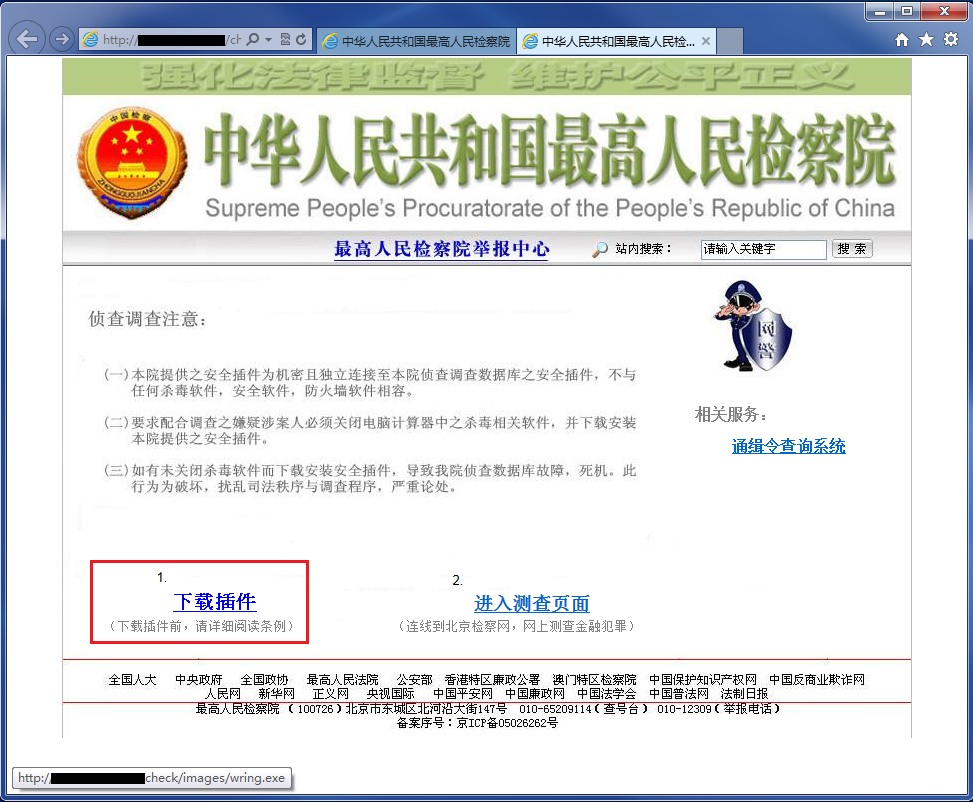
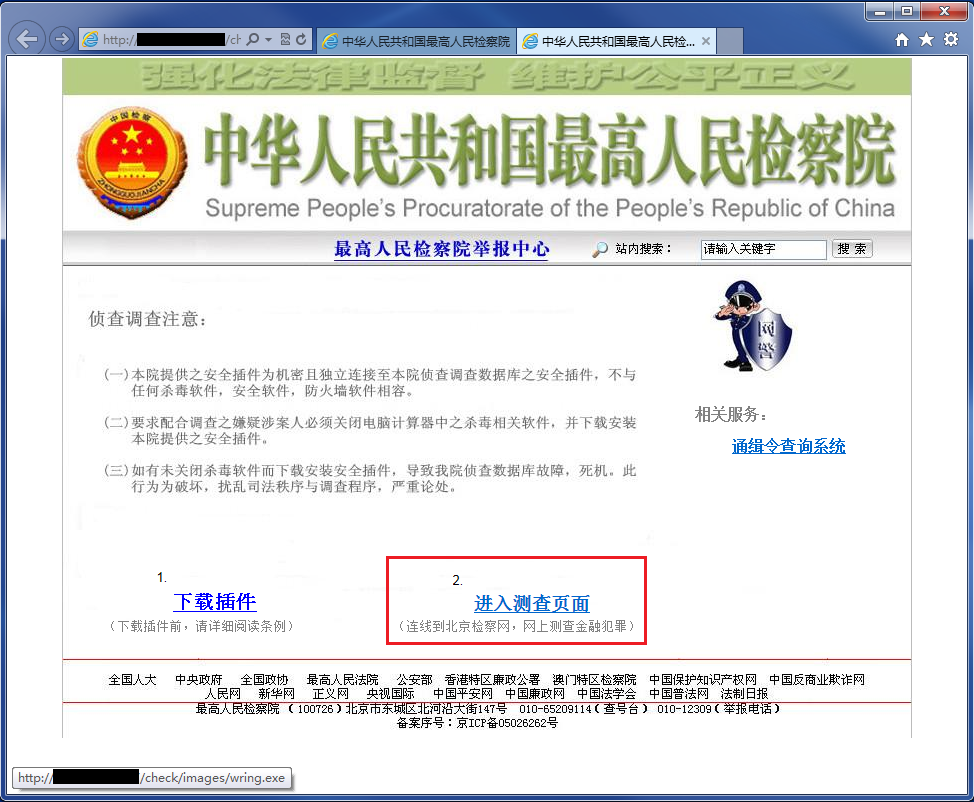
Next they will ask you to check if you are really listed as a criminal by checking your information in the “online finance crime database”. This database, of course, is highly confidential and can only be accessed after downloading and running a “plugin”:
To access the ‘online finance crime database’ you need to download and run a ‘plugin’
That alleged plugin is, in fact, a customized teamviewer application:
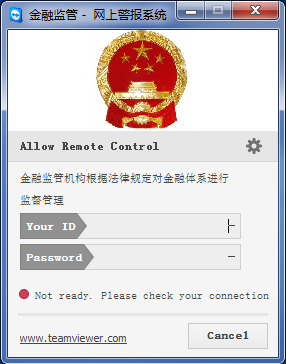
Once launched, it puts your computer under their complete control. They can use your machine for any operation, just like it was their own. But even this is not enough, though: they still can’t get their hands on your money. So they lead you to the next step.
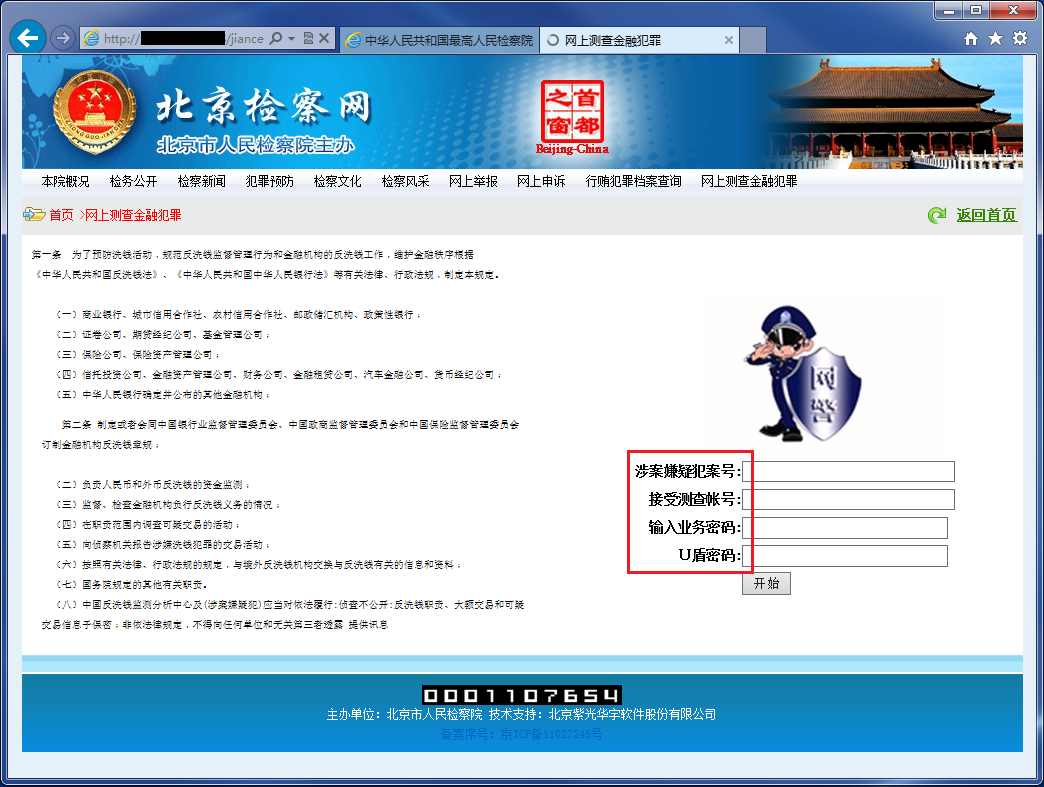
With the “plugin” running successfully, they will tell you to check the database. For this you need to visit an investigation web page.
Visit the webpage in which you can query the crime database
On this web page, before getting to the crime database, you need to input your bank account number, account passwords and – most importantly – your USB key.
It may not seem unreasonable to provide banking details to help investigate a suspected financial crime – but all of that sensitive data is immediately harvested by the fraudsters. With account numbers, passwords, USB keys and that teamviewer “plugin” tool, the gang now has everything it needs to steal your money.
You need to provide your bank account information to query the crime database
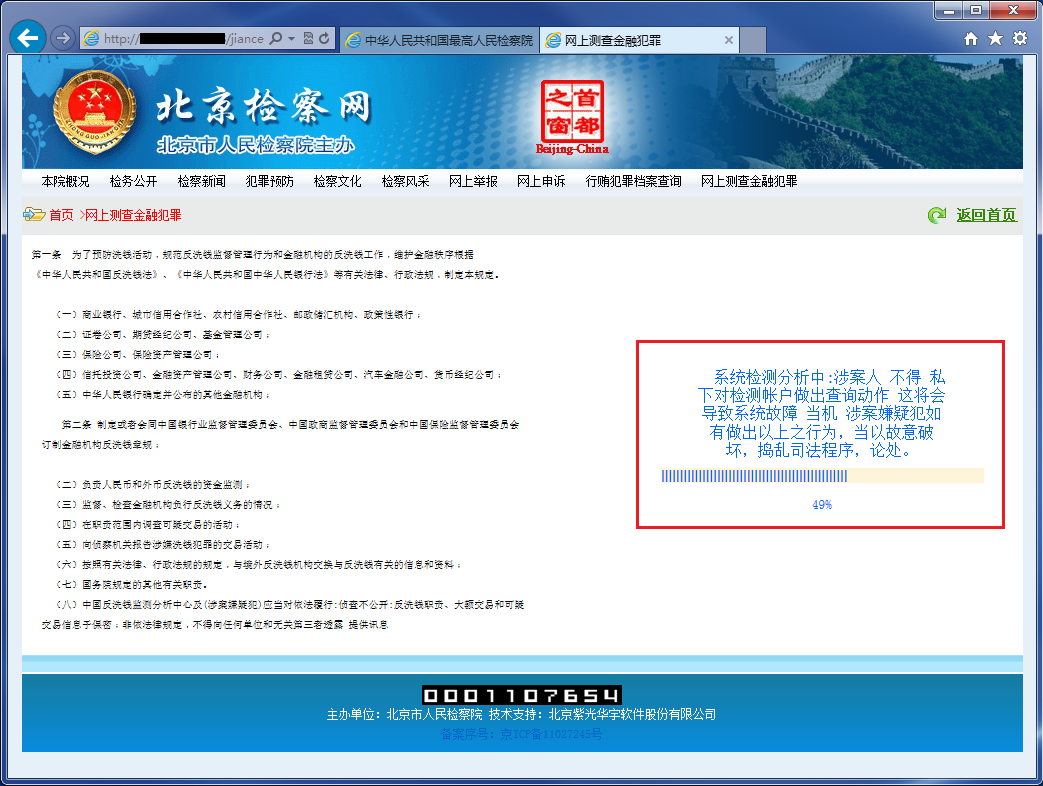
After clicking the start button, a new web page appears saying that the investigation is in progress. This screen masks the start of the money transfer out of your online bank accounts. To stop you from interrupting the theft, you are warned not to interfere with the ‘investigation’ because it may cause the system to crash resulting in the victim facing yet more criminal charges.
The money transfer can be completed within seconds. By the time you realize you’ve been tricked, the criminals have already said their farewells and jumped into their virtual getaway car.
Telecom fraud cases are very difficult to crack. Once transferred, the money is immediately divided among several other accounts and then laundered by buying various virtual assets. It can be almost impossible to follow exactly where the money goes. The telephone call which started it all can also be hard to trace if the number is concealed. Finally, the fraudsters typically work in several different countries, often far away from the scene of the crime, making it hard for a single national law enforcement agency to bring them to justice.



















Telecom fraud – phishing and Trojans combined