
Recently, vulnerabilities in Adobe products have come to pose a major threat, and the number of infections which they cause overtook those resulting from vulnerabilities in Windows or Internet Explorer long ago.
The latest zero-day vulnerability was identified yesterday and grabbed the attention of AV researchers right way, with PDF files with a marked Chinese connection appearing in the wild.
One of these files was called “Cao Chang-Ching The CPP made eight mistang Urumuqi incident_mm.pdf”. The events of the past few days in the Chinese town of Urumqui, where local residents clashed with police, made the news around the world, so it’s no surprise to see this topic being used to spread malicious programs.
The files didn’t contain the traditional JavaScript exploit, which had been the case with previous PDF vulnerabilities. However, when the PDF file is opened two files called temp.exe and suchost.exe appear in the system: clearly there’s some sort of exploit at work here, and one which will work even on the most recent, patched version of Adobe Reader.
More detailed analysis showed that an SWF object – a flash clip – was inserted into the PDF file. Flash clips are also products of the Adobe company and are watched with Adobe Flash. The vulnerability which had been identified was actually in Adobe Flash Player version 9 and 10, and not in Adobe Reader! This is what initially confused researchers analysing the PDF files and their format. The vulnerability uses heap spray and be exploited both when a specially crafted PDF file is opened and when sites are visited.
There’s indirect evidence which leads us to believe that this variant of the exploit was created at the beginning of July (either the 2nd or the 9th) and has probably already been used in a number of targeted attacks.
The samples we analysed install two malicious programs: Trojan.Win32.PowerPointer (modifications .h and .i) and Trojan-Downloader.Win32.Agent (modifications cjll and cjoc).
Prior to detection being added to our databases, these were still proactively detected using heuristic technologies as HEUR:Trojan.Generic.
Detection for the malicious PDF files was added to our antivirus databases yesterday evening as Exploit.SWF.Agent.br and .bs.
Adobe has officially confirmed the existence of the zero-day vulnerability and has promised to release a patch by July 30th.
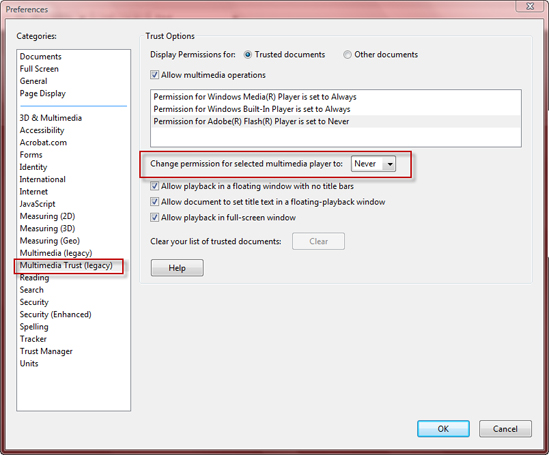
However, as the promised release is a week away, we recommend you disable the use of Flash in Acrobat Reader and embedded objects in the browser.
In Adobe Reader, go to Edit > Preferences Settings >Multimedia Trust -> Permission for Adobe Flash Player -> in Adobe Reader and choose “Never” or “Prompt”:





















SWF, PDF – it’s all Adobe