
It has become clear that the creator of the banking Trojan SpyEye have added plugin support to their code. In this new design, these plugins can be used by third parties to add extra functions to the core bot.
The plugins are DLLs stored in the bot’s configuration file. Among the core plugins created for SpyEye is customconnector. As its name implies, this supports the bot’s communications with the botnet C&C or its collector. The collector is a malicious server which receives data harvested from the victim’s computer; it can be distinct from the C&C server.
Since the creator of SpyEye has outsourced the botnet’s links to the C&C server, different SpyEye operators can create unique protocols governing communications between bot and server. Naturally, these protocols could make it more difficult to track the activity of SpyEye botnets. Despite this, cybercriminals have not, so far, rushed to take advantage of this opportunity: SpyEye’s old protocol in the basic customconnector.dll is still in use. Even so, we have recently spotted some changes related to this plugin.
Each plugin has a configuration file attached. If the plugin is customconnector.dll, its configuration file will be customconnector.dll.cfg. Cybercriminals can insert plain-text fragments into this config file containing settings for the plugin’s functions. Since customconnector.dll is a communication plugin, its config file has always identified the botnet’s C&C servers. The botnet operator could easily switch to a new C&C server by introducing the new URLs into the text file and updating the configuration file in the botnet.
Here is a sample configuration file:
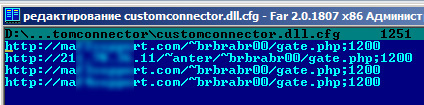
Figure 1. A configuration file for customconnector.dll
We can see several C&C URLs are identified in the configuration file. The bot tries to connect to these URLs one by one, looking for one which is currently active.
The diagram below shows how the plugin works on an infected computer:

Figure 2. How the customconnector plugin works
Let’s now look into the changes we have identified. Unsurprisingly, these are related to the tracker abuse.ch. SpyEye developer and botnet operators have repeatedly complained about this tracker. Abuse.ch promptly publishes the URLs of SpyEye botnets C&C servers and ISPs can block infected clients’ access to them. It is not too difficult to retrieve C&C addresses from SpyEye’s separate configuration file – the original is stored in the bot’s body. The configuration file is in essence a password-protected zip archive. The password and configuration file can be recovered from an infected computer’s memory. After this, the plugins’ configuration files – including customconnector.dll.cfg – are available from the archive; the C&C URLs are easy to find in customconnector.dll.cfg. This process can and should have been done automatically, because many new bots are unleashed every day. For now, the robots are working: C&C URLs are being published and blocked.
So, everything is fine, right? Unfortunately, we recently discovered out that the URLs published in the file customconnector.dll.cfg are fakes.
We have seen this before in ZeuS. Just like in ZeuS, the cybercriminals have left traces of the old method to confuse malware analysts. On the face of it, there’s nothing new, but in fact there are some changes. In some versions of customconnector.dll, the content of the plugin’s configuration file is simply ignored, while the URLs identified in the DLL are used. The function Init() contained in customconnector.dll assembles the real C&C URLs from fragments.

Figure 3. Text fragments in the DLL from which C&C URLs are put together

Figure 4. Putting the C&C URLs together from isolated fragments

Figure 5. The botnet’s real C&C URLs retrieved on the fly from the DLL
Cybercriminals are gradually starting to experiment with the opportunities offered by the customconnector plugin. So far the communication protocol is not customizable, but cybercriminals have started using it to conceal the botnet’s C&C URLs from the tracker and from malware analysts. Of course, they will not stop at this, but luckily it costs money to develop new functions. We will keep our fingers crossed that we can detect any new tricks quickly and make it unprofitable for cybercriminals to keep making constant changes to the protocol used for communication between the bot and the C&C server.




















SpyEye vs. Tracker