
- March in figures
- Spam in the spotlight
- The geographical distribution of spam sources
- Malicious attachments in email
- Phishing
- Conclusion
March in figures
- The percentage of spam in email traffic was down 1 percentage point compared with February and averaged 70.1%
- The percentage of phishing emails doubled compared with February, reaching 0.006%
- In March, malicious files were found in 4% of all emails, an increase of 1.2 percentage points
Spam in the spotlight
In March there was a fall in the amount of spam which focused on upcoming holidays. However, we still spotted mailings trying to exploit St. Patrick’s Day, Easter and Mother’s Day, which is traditionally celebrated in May. The spammers did not ignore the big political news of the month, the death of Venezuela’s president Hugo Chavez.
Holiday spam
In March, the Internet was flooded with numerous mass mailings dedicated to Easter. This holiday was often mentioned in English-language messages advertising replicas of designer goods and weight-loss pills, as well as in fraudulent emails. As a holiday gift spammers even offered a discount on investor databases.
St. Patrick’s Day, celebrated on March 17 in many countries, was marked by spammers offering advice on advertising campaigns and discounts for producing plastic cards. All these mailings were designed in a festive style: bright green shamrocks were prominent throughout.
In March, the “flower” partner programs were still popular with the spammers. These mass mailings were related to Easter and Mother’s Day.
“Nigerian letters” and events in Venezuela
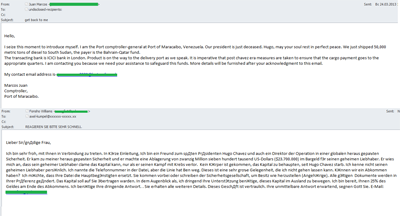
One of the major political events of March was the demise of the President of Venezuela. Hugo Chavez was at the head of his country for 14 years and was a notoriously controversial figure in the political world. The buzz surrounding his death does not abate. Already in the beginning of March, we registered the so-called “Nigerian letters” in English and German exploiting interest in events in Venezuela.
One of the fraudulent emails was sent on behalf of a Venezuelan seaport chief who allegedly asked for help in collecting the money he had got from the sale of diesel fuel to Southern Sudan. In their first email the scammers did not offer the victim any specified sum of money for his help, their goal at the initial stage was to provoke the recipient’s interest and make him respond to the email. In further correspondence the victim was offered a reward.
Yet another mass mailing was sent supposedly on behalf of the head of security and a close friend of Hugo Chavez. As always, “Nigerian” fraudsters have imagination: this mythical “friend” has access to the money which the late president kept in his secret lover’s bank account, and will give up 25% of the loot to anyone who can help get the cash out of the country.
The scammers’ main goal in both cases is to involve users in correspondence in order to extort money from them, typically under the pretext of paying for financial services required to transfer the mythical millions.
The geographical distribution of spam sources
In March, China (25.8%) remained the leading source of spam worldwide. The amount of spam sent from the US increased very slightly (17.3%) placing this country 2nd in the rating. Overall, these two countries produced 43% of global spam.
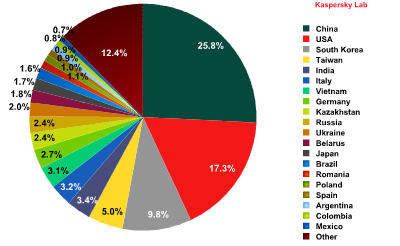
Sources of spam around the world by country
As in February, South Korea (9.8%) came third, despite a 3.8 percentage point fall in its share. Taiwan (5%) and India (3.4%) maintained their positions in the rating. Russia (2,4%) moved down from 7th to 10th place (-1 percentage point). Meanwhile, Germany was up 1 percentage point and climbed from February’s 10th place to 8th with 2.7% of all distributed spam.
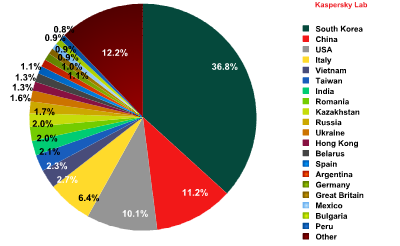
Sources of spam in Europe by country
South Korea was the main source of spam sent to European users in March (36.8%), although its share fell by 13 percentage points. China’s contribution grew significantly and averaged 11.2%, moving it to 2nd position.
The US moved down to 3rd place with 10.1% of all spam distributed in Europe. Italy gained 1.1 percentage points and came 4th with 6.4% of spam sent to European users.
Asia (54.1%) remained the leading source of spam by region. As in February, the Top 3 also included North America (17.8%) and Eastern Europe (10.2%). They are followed by Western Europe which produced 9.4% of all spam.
Malicious attachments in email
In March, malicious attachments were detected in 4% of emails, an increase of 1.2 percentage points from February.
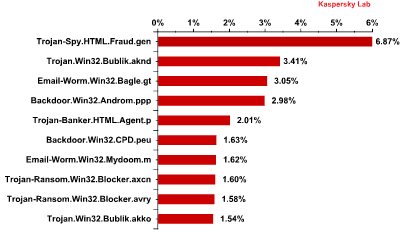
Top 10 malicious programs spread via email in March 2013
In March, Trojan-Spy.html.Fraud.gen (6.9%) remained the most widespread malicious program carried by email despite the fact that its share decreased by 4.1 percentage points compared with February. This malicious program appears in the form of HTML pages imitating the registration forms of well-known banks or e-pay systems which are used by phishers to steal user credentials for online banking systems.
Trojan.win32.Bublik.aknd came 2nd in the rating. This malicious program harvests user passwords for FTP, email services credentials and certificates from infected computers. It can scour forms in Mozilla Firefox and Google Chrome in search of saved logins and passwords before forwarding the data it finds to the fraudsters.
Third place is occupied by Email-Worm.Win32.Bagle.gt. Mail worms are a constant feature in the Top 10 as their main functionality is to self-proliferate to addresses in the victim’s address book. The Bagle family worms can also contact the command center and download other malicious programs onto a user’s computer.
March’s Top 10 also included malicious programs belonging to the Trojan-Ransom family, which are designed to extort money from users to regain access to the OS or applications (usually the user is required to send a paid sms). We detected the Trojan-Ransom.Win32.Blocker modifications which block the work of the operating system and display a banner containing the conditions for unblocking on the desktop. We would like to remind the users that they should not be blackmailed into paying money to these cybercriminals. At any time they may use our free solution: http://support.kaspersky.com/us/viruses/solutions?qid=208285998.
Distribution of email antivirus detections by country
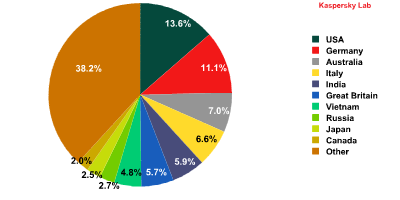
Distribution of email antivirus detections by country
Italy’s (6.6%) unexpected surge in February did not last long. In March the US (13.6%) regained its leadership. Interestingly, in addition to password stealers Trojan-Spy.html.Fraud.gen and Trojan.win32.Bublik.aknd the US users also received many other members of the password-targeted Trojan-PSW.Win32.Tepfer family. Germany’s share remained unchanged from February accounting for 11.1% which saw it come 2nd again. It is followed by Australia (7%) which contribution grew by 1.3 percentage points as it moved from 5th to 3rd place. There was little change to the percentages of the other countries in the rating.
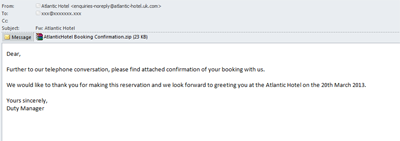
After a short lull, the scammers distributing malware via email resumed sending fake notifications of the popular online booking services. In March, we registered a new mass mailing spread allegedly on behalf the Atlantic Hotel booking service: the supposed hotel manager informed the recipient that his arrival was welcome on March 20, 2013.
The assumption is that a curious recipient will open the attached file to check out the booking confirmation number, and in doing so will run the executable file AtlanticHotel Booking Confirmation.doc.exe. This infects the computer with malware detected by Kaspersky Lab as Trojan-Ransom.Win32.Blocker.awbi., which was designed to extort money or financial information from the users.
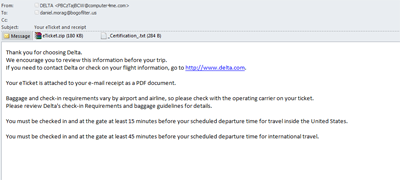
The fraudsters also spread emails with malicious attachments containing fake airline confirmation notices. For example, emails sent on behalf of the Delta.com online booking service first thanked the recipient for choosing Delta and further informed him that baggage and check-in requirements might vary by airport and airline encouraging the user to open the attached e-ticket and read it carefully.
In fact the attachment contained the executable file eTicket and Receipt.pdf.exe detected by Kaspersky Lab as Backdoor.Win32.ZAccess.bmdt. This malicious software is used by the fraudsters to get remote access to the victim’s computer in order to steal personal information, include the computer to the botnet, etc.
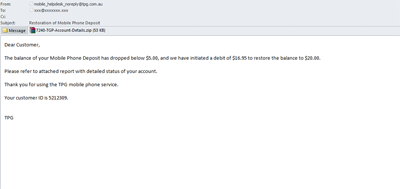
In March, in addition to fake airline and hotel confirmation notices, the scammers used the name of Australian telecommunication company TPG Telecom to cheat users. The fake notification informed the recipient that his mobile phone balance was below $5. However the company had automatically restored the balance to $20 initiating a debit of $16.95. In order to get more detailed information on the status of the account, the user was invited to open the attached file.
The attached zip archive contained TGP-Account-Details.doc.exe detected by Kaspersky Lab as the Trojan spyware Trojan-Spy.Win32.Zbot.jqye. This is one the famous ZeuS modifications designed to steal confidential user data.
Phishing
The percentage of phishing emails in total email traffic doubled from February and averaged 0.006%.
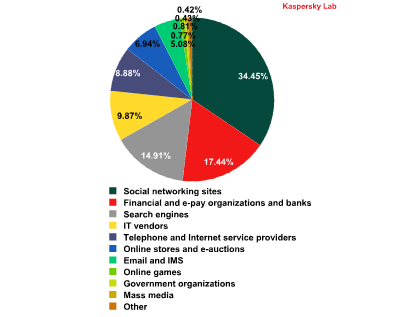
The distribution of the Top 100 organizations targeted by phishers, by category*
*This rating is based on Kaspersky Lab’s anti-phishing component detections, which are activated every time a user attempts to click on a phishing link, regardless of whether the link is in a spam email or on a web page.
In March, Social networking sites continued to be the most attractive target for phishing attacks though their share fell 4.3 percentage points and averaged 34.5%. The Top 3 also included Financial and e-pay organizations (17.4%) and Search engines (14.9%) which came 2nd and 3rd respectively.
IT vendors remained in 4th position (9.9%). They were followed by Telephone and Internet service providers (8.9%) whose share grew 3.5 percentage points as this category moved two steps up from 7th to 5th place.
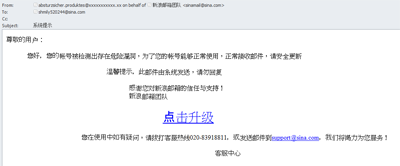
In March, we received an interesting Chinese-language phishing email sent allegedly by the famous Chinese Internet resource sina.com.cn. The phishers resorted to a popular scam: the user’s account is poorly protected and to ensure data security the recipient should click the link and update the account information. Not surprisingly, the link led to the fake page where the user was asked to enter his login and password to access his account. As a result, his personal data fell prey to the fraudster and the stolen account could be then used for distributing spam on behalf of the victim.
Interestingly, the phishers themselves invited the user to write or to call the technical support service in case of any doubt or questions. This trick is often used to reassure the recipient of the legitimacy of the email.
Conclusion
In March, the total amount of spam decreased slightly. Spammers continued to exploit the holiday theme for advertising various products and services. In April, we expect to see an overall reduction in the amount of holiday spam, although there is likely to be a round of Russian-language Easter spam. “Nigerian letters” exploiting interest in the events in Venezuela were a noticeable trend in March’s spam flows.
As in February, the United States and China dominated the worldwide distribution of spam. In March, these two countries produced about 43% of spam. The list of countries that send spam to Europe saw significant changes: South Korea lost 13% of its contribution but maintained its leading position. Now its share accounts for about one third of the total amount of all spam mailings.
In March, the list of the most widespread malicious programs distributed via email was diverse: messages with phishing attachments carried backdoors, worms, Trojans and even ransomware. However, Trojan-Spy.html.Fraud.gen remained the most popular.
The number of phishing emails doubled but the Top 3 organizations most often attacked by phishers saw no significant changes. as last month, about one third of all attacks targeted the users of social networking sites. Search engines and Financial and e-pay organizations and banks came 2nd and 3rd in the rating.





















Spam in March 2013