
- February in figures.
- Be my spam Valentine.
- The geographical distribution of spam sources.
- Malicious attachments in email.
- Phishing.
- Conclusion.
February in figures
- The percentage of spam in email traffic was up 12.8 percentage points compared with January and averaged 71.1%.
- The percentage of phishing emails remained unchanged compared with January and averaged 0.003%
- In February, malicious files were found in 2.6% of all emails – a decrease of 0.2 percentage points.
Be my spam Valentine
In February, English-language spam traffic was inundated with offers for flowers from so-called partner programs.
Contrary to our expectations, no Valentine-related spam with malicious attachments was registered in February.
Spammers use various tricks to attract the attention of recipients. In February, the Valentine theme was exploited even in mass mailings that weren’t offering any presents or services related to February 14. For example, we came across several spam emails with the subject ‘Find your Valentine’ advertising the services of dating agencies. The emails not only contained image spam showing photos of ‘lonely hearts’ and a field to search for your ‘other half’ but also standard text messages about a potential partner and a link to the dating site. Sometimes the link to the site led to a completely unrelated page – yet another trick spammers use to promote their goods and services.
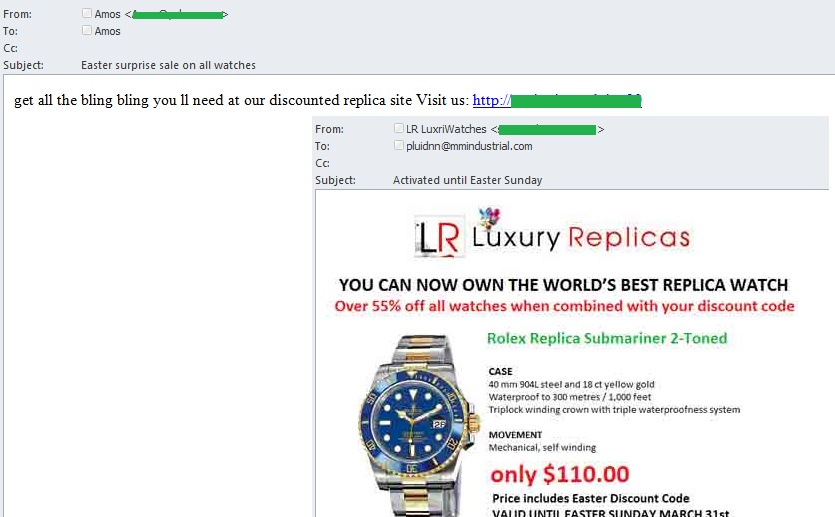
As expected, the Easter theme was also used by spammers to attract attention to various adverts. At the beginning of February we registered several mass mailings offering fake designer goods with subjects that contained some sort of reference to Easter.
These sorts of emails were restricted to English-language spam.
The geographical distribution of spam sources
In February, the US (16.9%) topped the rating of the leading sources of spam worldwide. The amount of spam sent from China halved and averaged 14.4% resulting in a drop to second place. Overall, the two countries produced 31.3% of global spam.
Sources of spam around the world by country
As was the case in January, South Korea came third accounting for 13.7% of all distributed spam, an increase of 6.9 percentage points. The Russian share (3.3%) fell 1.6 percentage points, resulting in a drop from 4th to 7th place. The Top 5 also includes Taiwan (5.1%) whose share grew more than threefold. In February, Germany’s contribution (2.1%) was up 1.2 percentage points pushing its rating up from 17th to 10th place.
Sources of spam in Europe by country
South Korea was the main source of spam sent to European users in February: the volume of junk email originating from that country grew 27.7 percentage points and averaged 50.9%. Last month’s leader China (3%) fell to 6th place in February with a considerable drop of 36.6 percentage points. Such significant changes in the share of spam produced by these two countries may be due to the fact that a group of spammers started distributing from a different botnet.
Although the US (9.2%) share decreased by 0.14 percentage points, it remained in 2nd place. Italy came 3rd, accounting for 5.3% of spam sent to European users.
Sources of spam by region
Asia remained the leading regional source of spam (50.4%). As in January, the Top 3 also included North America and Western Europe.
Malicious attachments in email
The share of spam in mail traffic continues to decrease. In February, malicious attachments were detected in 2.8% of emails, a drop of 0.2 percentage points from January.
Top 10 malicious programs spread via email in February 2013
In February, Trojan-Spy.html.Fraud.gen (11%) remained the most widespread malicious program carried by email despite the fact that its share decreased by 2.2 percentage points compared with January. It was followed by Trojan-Banker.HTML.Agent.p (7.8%). Both malicious programs appear in the form of HTML pages imitating registration forms of well-known banks or e-pay systems which are used by phishers to steal users’ credentials for online banking systems.
Interestingly, Backdoor.Win32.Androm.phh came 3rd. This family of backdoor programs allows malicious users to secretly control an infected computer, for example, to download and launch other malicious files that then send various data from the user’s computer, etc. Additionally, many computers infected by backdoors become part of a botnet.
In February, we detected 85 modifications of Backdoor.Win32.Androm. Their total share accounts for 12% of all malware spread via email. In most cases the backdoor was distributed in fake emails sent allegedly on behalf of Booking.com, DHL, British Airways, etc. The same method has been used in the past to distribute programs belonging to the ZeuS/Zbot family.
Trojan-Downloader.HTML.Iframe.ahh came 4th in the rating. These programs open web pages in a browser without the user’s knowledge and download malware to the computer or redirect the user to the sites of partner programs.
Distribution of email antivirus detections by country
Italy took the unenviable lead among the countries targeted most by malicious emails, unexpectedly pushing long-term leader the US into 2nd place. Italy’s share grew by 9.4 percentage points and averaged 14.4%. Noticeably, Italy was the country most often attacked by Trojan-Banker.HTML.Agent.p which came second in February’s Top 10 malicious programs.
There was little change to the percentages of the other countries in the rating.
Fake notifications from different financial organizations remain one of the most popular tools for distributing malware via email. For example, the criminals resort to the well-known scam of informing the user of a hacking incident which has resulted in the user’s bank account being blocked. To get more information about the incident the user is asked to open an email attachment.
In February’s email traffic we registered one such fake notification containing a zip archive containing the file FraudReport_acoountid_43753985724.exe. This malicious file is detected by Kaspersky Lab as one of the aforementioned Backdoor.Win32.Androm modifications.
One company name that is especially popular with the fraudsters is Google. In February, they launched a mass mailing that included the Google name notifying users that their rsum was under consideration. To avoid any confusion, the recipient was encouraged to open the attached file to check their resume was correct. The attachment was a zip archive containing the file Document.chm.exe. When it was opened a Trojan, detected by Kaspersky Lab as Trojan-Dropper.Win32.Typic.bea, started downloading malware designed to steal passwords and other confidential data on the user’s computer. To convince the recipient of the legitimacy of the email the fraudsters entered an apparently plausible address (resume-thanks@google.com) in the ‘From’ field and added the company logo.
Phishing
The percentage of phishing emails in total email traffic remained unchanged from January and averaged 0.003%.
The distribution of the Top 100 organizations targeted by phishers, by category*
*This rating is based on Kaspersky Lab’s anti-phishing component detections, which are activated every time a user attempts to click on a phishing link, regardless of whether the link is in a spam email or on a web page.
In February, there were no major changes to the Top 3 organizations targeted by phishers. Social networking sites continued to bear the brunt of phishing attacks, with their share growing inconsiderably (+0.8 percentage points) and averaging 38.8%. Search engines (16.9%) and Financial and e-pay organizations (12.3%) came 2nd and 3rd respectively.
Conclusion
In February, the proportion of spam in email traffic grew by 12.8 percentage points and accounted for 71.1% which is higher than the average share of spam in Q3 of 2012 (65.5%).
Since the beginning of 2013 there have been some significant changes to the sources of spam. In the first two months of the year the share of spam originating from China fell 19.9 percentage points. At the same time South Korea’s contribution grew by 11.9 percentage points. These changes are even more noticeable in the spam sent to European countries – China’s share dropped from 58.2% in December to 14.4% in February, while the amount of spam coming from South Korea grew from 5% to 51%. This may be due to a group of spammers changing the botnets used for spam distribution.
Phishing HTML pages topped the rating of malware spread via email. Users’ credentials entered on these pages are redirected to the scammers. One of these pages, detected as Trojan-Banker.HTML.Agent.p, was actively distributed in February, especially in Italy. As a result, the Trojan occupied 2nd place in the Top 10 malicious programs spread via email and Italy topped the rating of countries targeted most by malicious emails.
Contrary to expectations, no Valentine-related spam with malicious attachments was registered in 2013. However, the Valentine’s Day theme, along with that of Easter, was exploited by the spammers to attract attention to adverts for goods and services.






























Spam in February 2013