
The year in figures
- 47.27% of all emails sent worldwide and 48.57% of all emails sent in the Russian web segment were spam
- 36.18% of all spam emails were sent from Russia
- Kaspersky Mail Anti-Virus blocked 125,521,794 malicious email attachments
- Our Anti-Phishing system thwarted 893,216,170 attempts to follow phishing links
- Chat Protection in Kaspersky mobile solutions prevented more than 60,000 redirects via phishing links from Telegram
Phishing and scams in 2024
Phishing for travelers
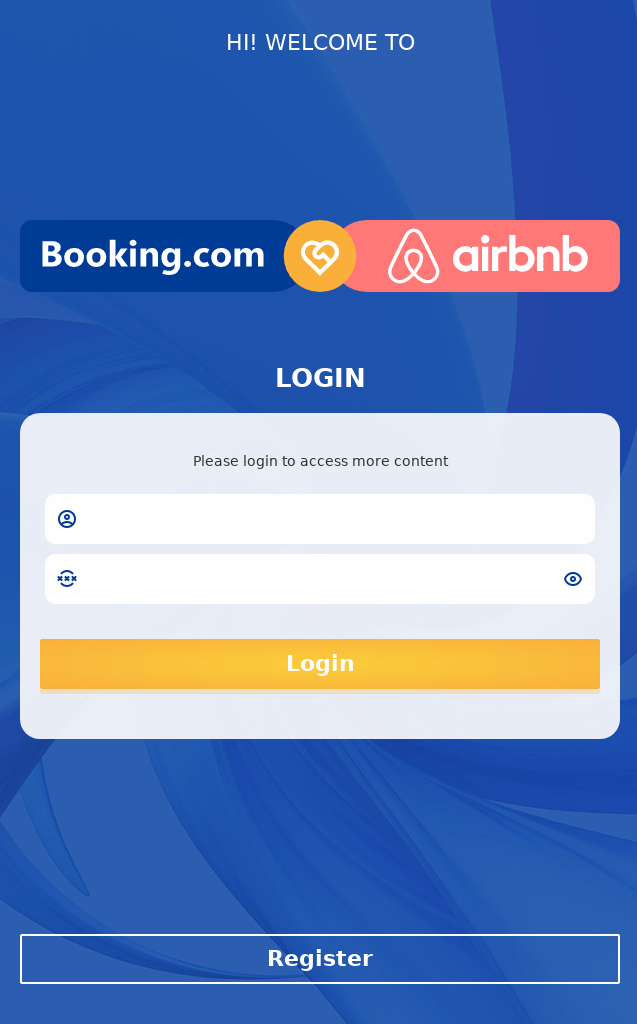
In 2024, cybercriminals targeted travel enthusiasts using fake hotel and airline booking websites. In one simple scheme, a fraudulent site asked users to enter their login credentials to complete their booking — these credentials ended up in criminal hands. Sometimes, the fake login form appeared under multiple brand names at once (for example, both Booking and Airbnb).
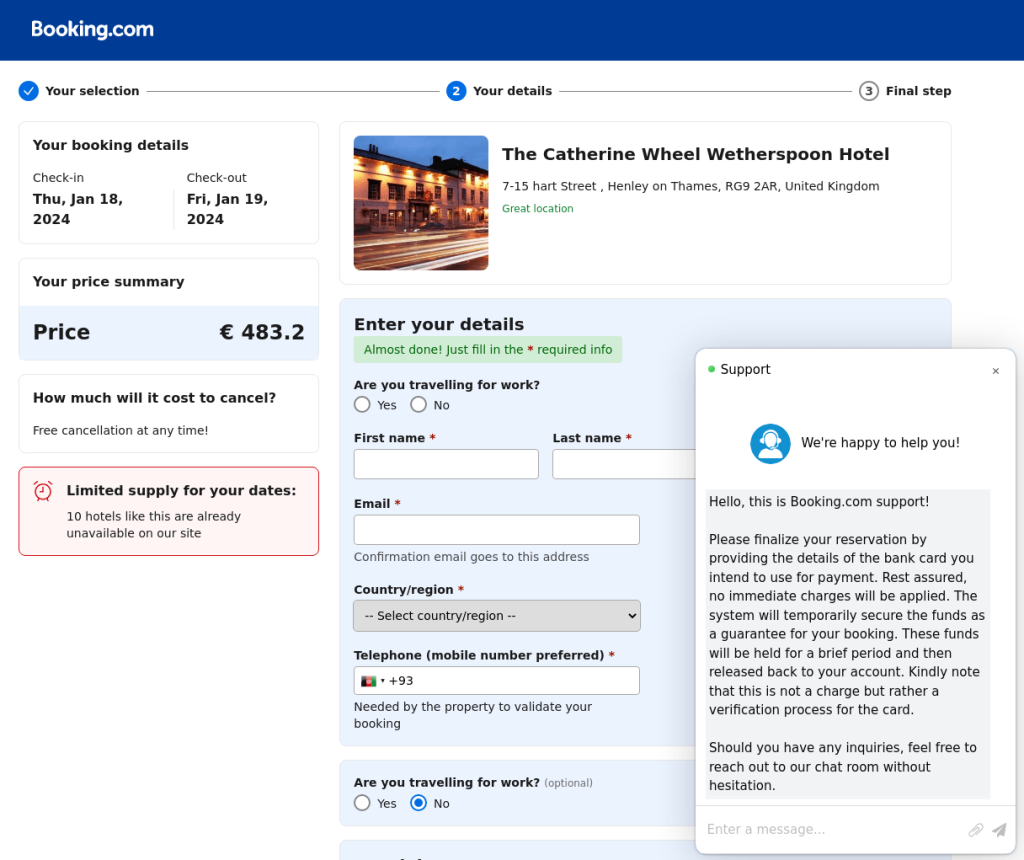
Another scheme involved a more sophisticated fake site, where users could even select the purpose of their trip (business or leisure). To complete the booking, the scammers requested bank card details, claiming that a certain sum would be temporarily blocked on the account to verify the card’s authenticity. Legitimate booking services regularly request payment details, so the victim may not suspect anything in this case. To rush users into entering their data carelessly, on the phishing page, the scammers displayed warnings about dwindling accommodation availability and an imminent payment deadline for the booking. If the victim entered their data, the funds were not frozen but went straight into the criminals’ pockets.
Cyberthreats in the travel sector affected not only tourists but also employees of travel agencies. By gaining access to a corporate account, criminals could conduct financial transactions on behalf of employees and gain access to large customer databases.
Fake accommodation sites often sent messages to property owners, telling them to log in to “manage their property.” This scheme targeted people renting out their homes through online booking platforms.
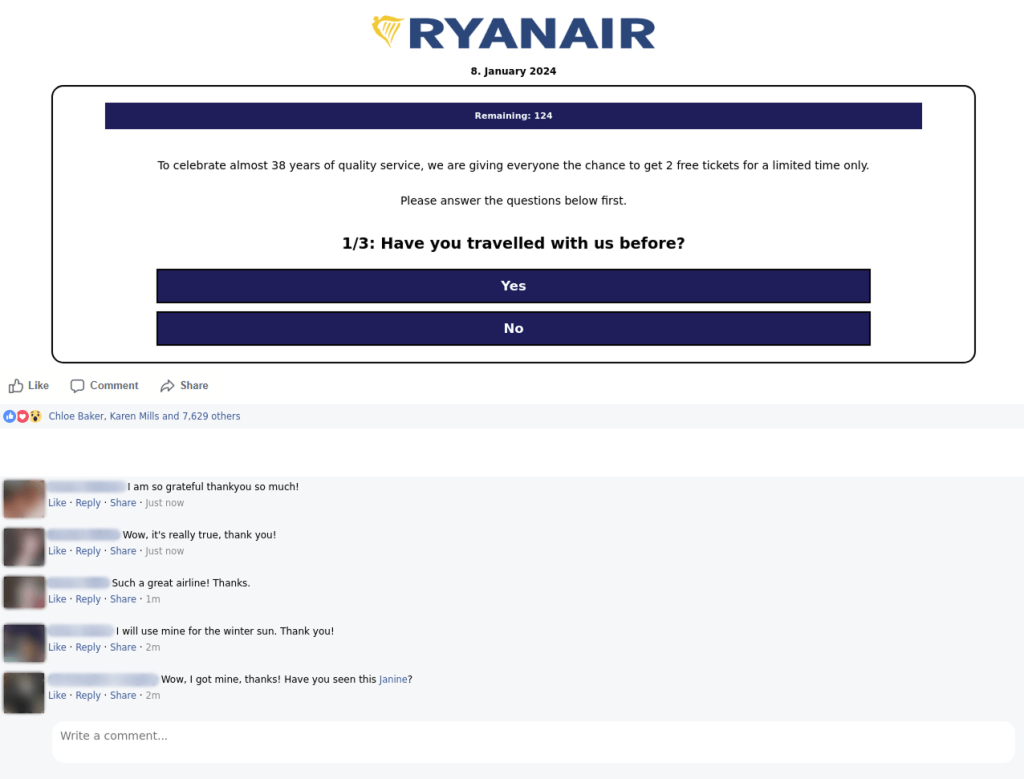
Other scam pages featured surveys, offering respondents gifts or prize draws for participating. In this case, victims risked both their credentials and their money. Such fake giveaways are a classic scam tactic. They are often timed to coincide with a significant date for the travel industry or a specific company. For example, the screenshot below shows an offer to take part in a giveaway of airline tickets to celebrate Ryanair’s birthday.
After completing the survey, users may be asked to share the offer with a certain number of contacts, and then pay a small fee to receive the expensive gift. Of course, these prizes are non-existent.
Trapped in social networks
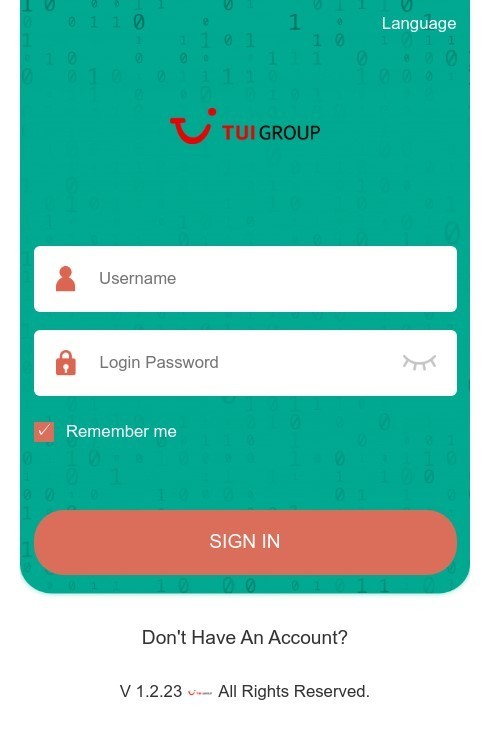
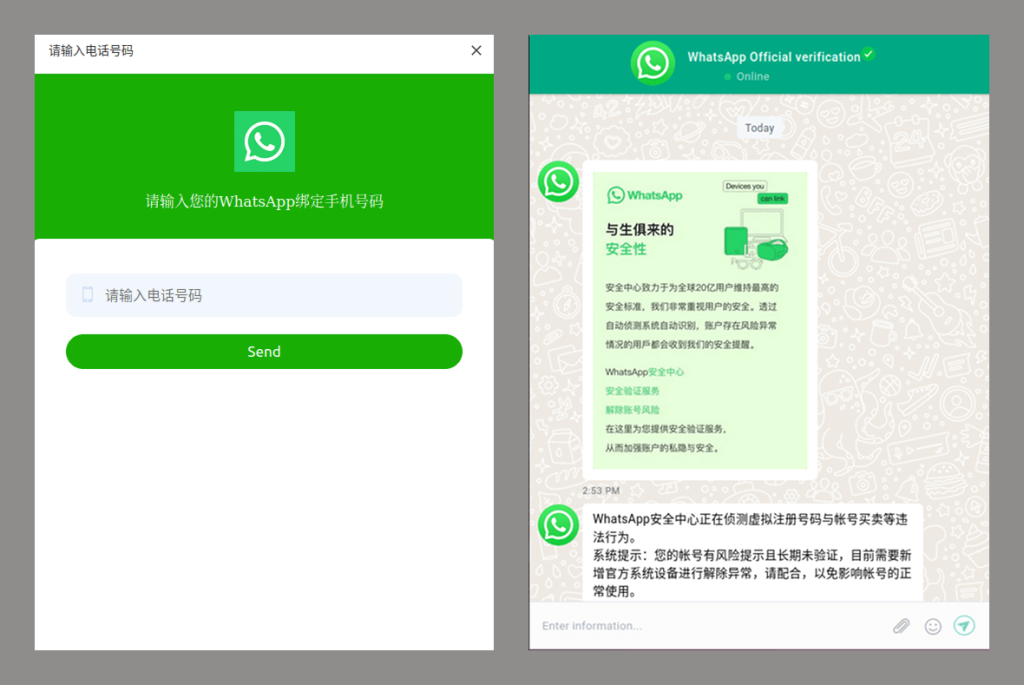
To steal credentials for social media and messenger accounts, scammers used another classic technique: asking users to verify themselves. In one scheme, the victim was redirected to a website that completely replicated WhatsApp’s design. The user entered their phone number and login code, handing their credentials straight over to the cybercriminals.
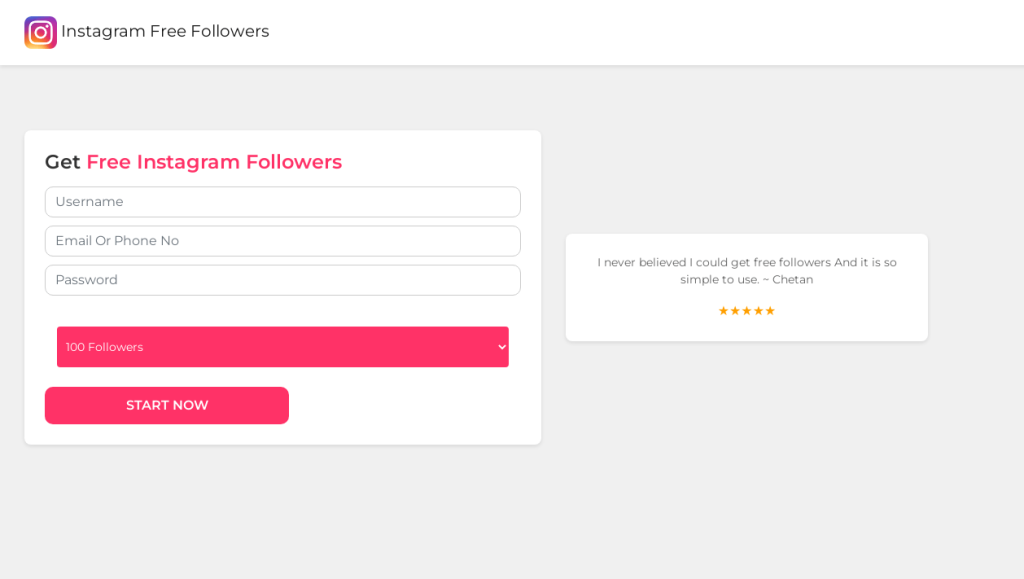
Beyond verification scams, fraudsters also lured victims with attractive offers. For example, in the screenshot below, the victim is promised free Instagram followers.
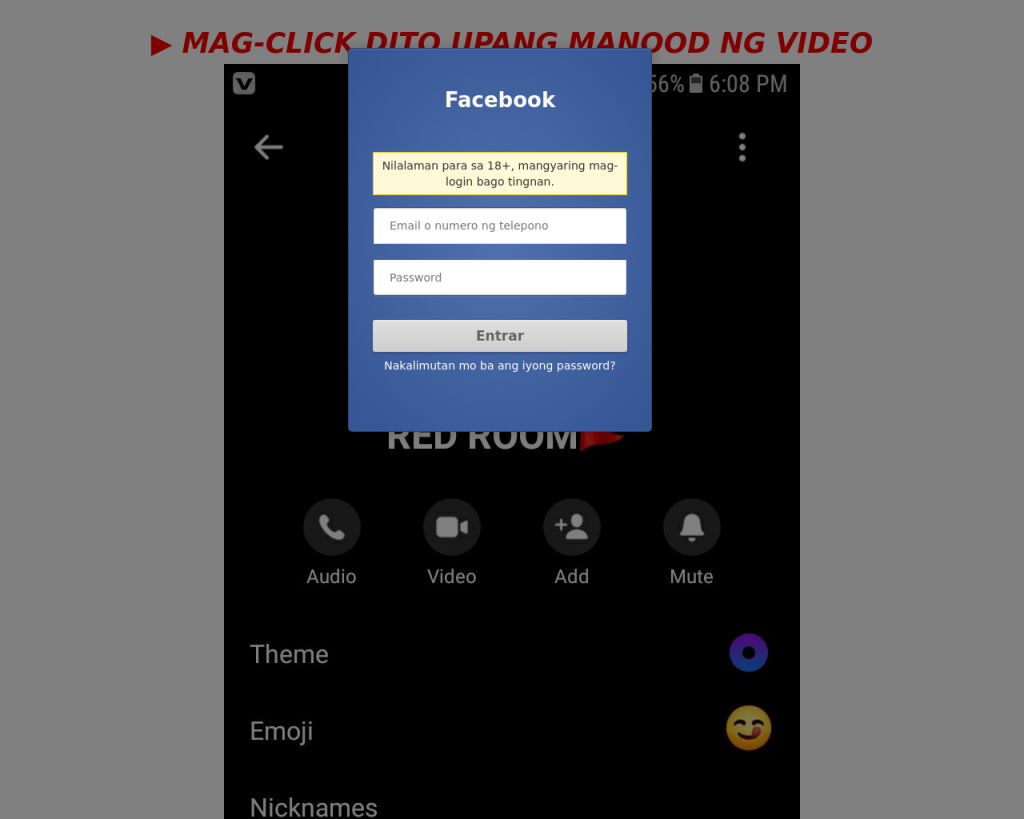
Some cybercriminals also used the promise of adult content to lure victims into entering their credentials in a fake authorization form.
Other scammers took advantage of Facebook and Instagram being owned by the same company. On a fraudulent page, they claimed to offer a service that allowed users to find Instagram profiles by entering their Facebook login and password.
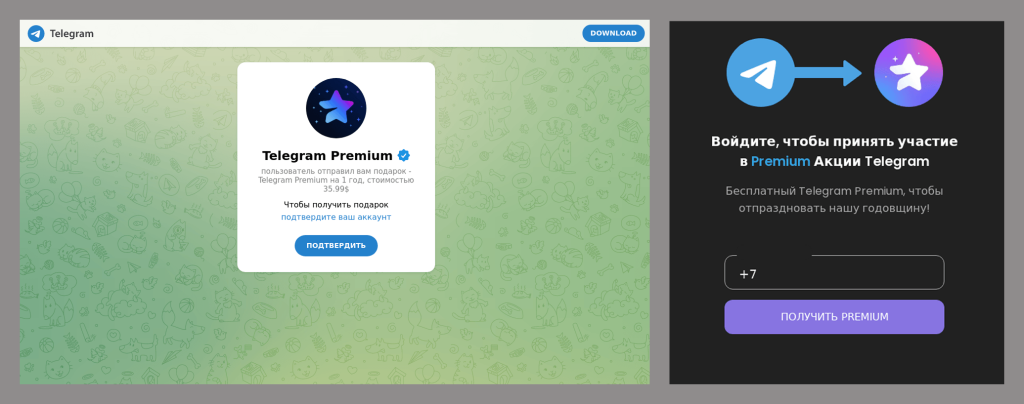
Some scams offered users a surprise “gift” — a free Telegram Premium subscription. To enable the messenger’s premium features, the victim only had to enter their phone number and a one-time code on a fraudulent website.
Some fake social media and messenger pages were designed not to steal login credentials but to install malware on victims’ devices. Taking advantage of the popularity of Facebook Lite for Android, scammers offered users a “more advanced official version”, claiming it had extra features missing in the original app. However, instead of an upgraded app, users downloaded malware onto their devices.
Similarly, installing a supposedly free Telegram client with an activated Premium subscription often led to downloading malware.
Social media business services were increasingly used as a pretext for credential theft, as they play a key role in developing and promoting businesses and are directly linked to financial operations. Cybercriminals tricked Telegram channel owners into logging in to a phishing platform imitating the official Telegram Ads tool, thereby stealing their Telegram credentials. To make the scam more convincing, the attackers detailed how Telegram advertising works and promised millions of ad views per month.
TikTok users have also been targeted. TikTok Shop allows sellers to list curated products—items featured in videos—for potential buyers to find and purchase. Scammers created fake TikTok Shop pages to steal seller credentials, potentially leading to both reputational and financial damage.
In another case, fraudsters informed Facebook fan page owners of unusual activity in their accounts. Potential victims were prompted to check their profile by entering their login credentials into a phishing form.
Cryptocurrency: don’t mistake scams for real deals
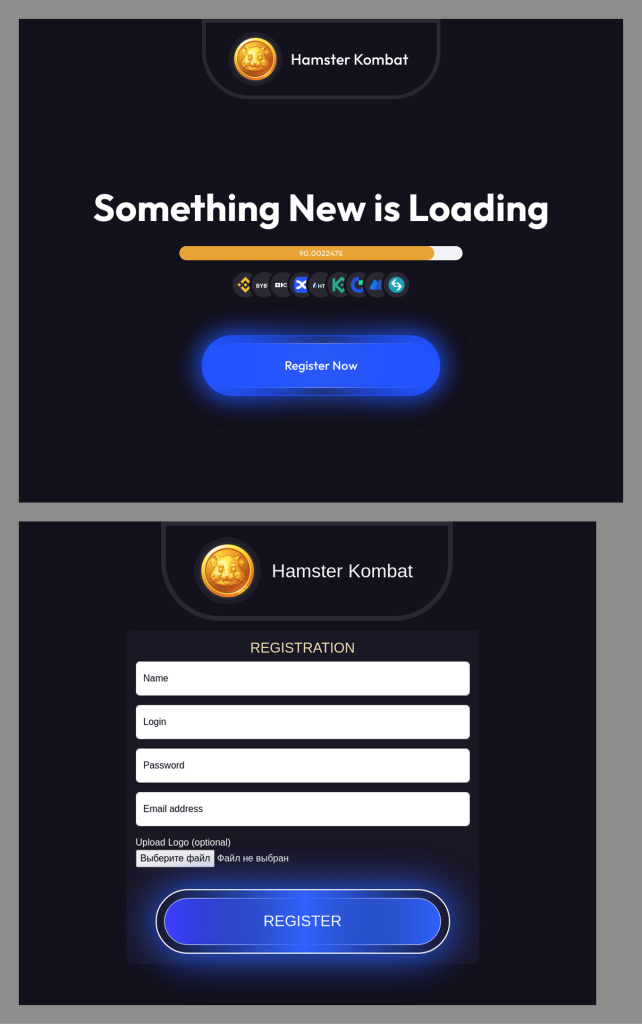
One of last year’s most sensational stories was the cryptocurrency game Hamster Kombat. This clicker game, simulating the creation of a crypto exchange in a gamified format, quickly attracted a massive audience. Players eagerly awaited the moment when the in-game coins could be exchanged for real virtual currency. But while the official listing was delayed, the fraudulent schemes wasted no time.
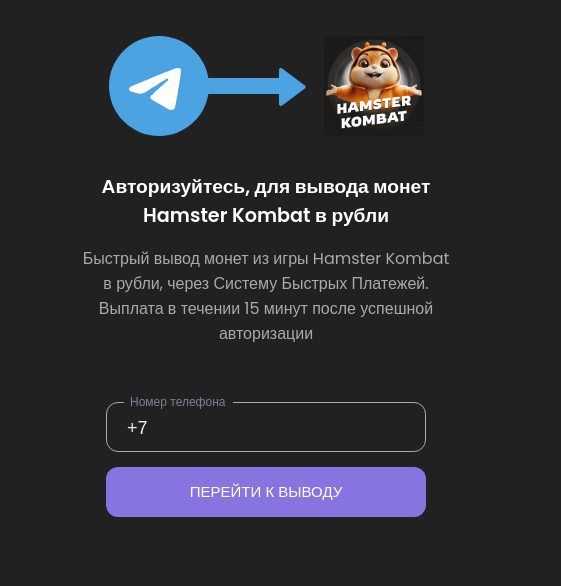
Fraudsters claimed to offer cash-out services for in-game coins by converting them into rubles. To withdraw money, criminals claimed, users just had to log in through a fake Telegram page.
The growing anticipation for the new cryptocurrency’s market launch was frequently exploited by cybercriminals to steal seed phrases from crypto wallets. Scammers announced an early token sale, requiring users to log in through a fake page to participate. Of course, there was no mention of such promotions on official resources.
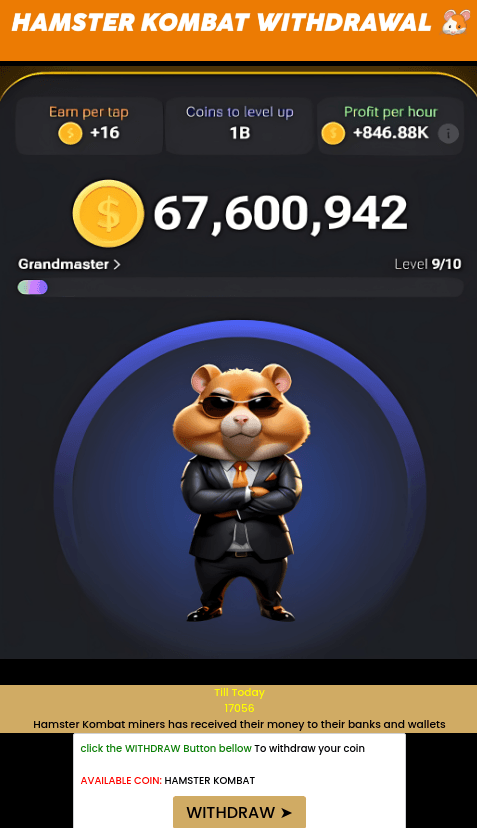
The popularity of Hamster Kombat was also abused in scam schemes. For example, users were offered access to a crypto wallet supposedly containing a significant sum in virtual coins. To claim it, the unsuspecting victims had to share information about the “opportunity” with a certain number of contacts in messaging apps. Having made their potential victim an accomplice in spreading false information, the scammers demanded a small commission for the withdrawal and disappeared with the stolen money.
A more elaborate scam also aimed to trick users into paying a “commission”, but with a slightly different approach. First, visitors to the page were asked to register to learn about some new activity related to Hamster Kombat.
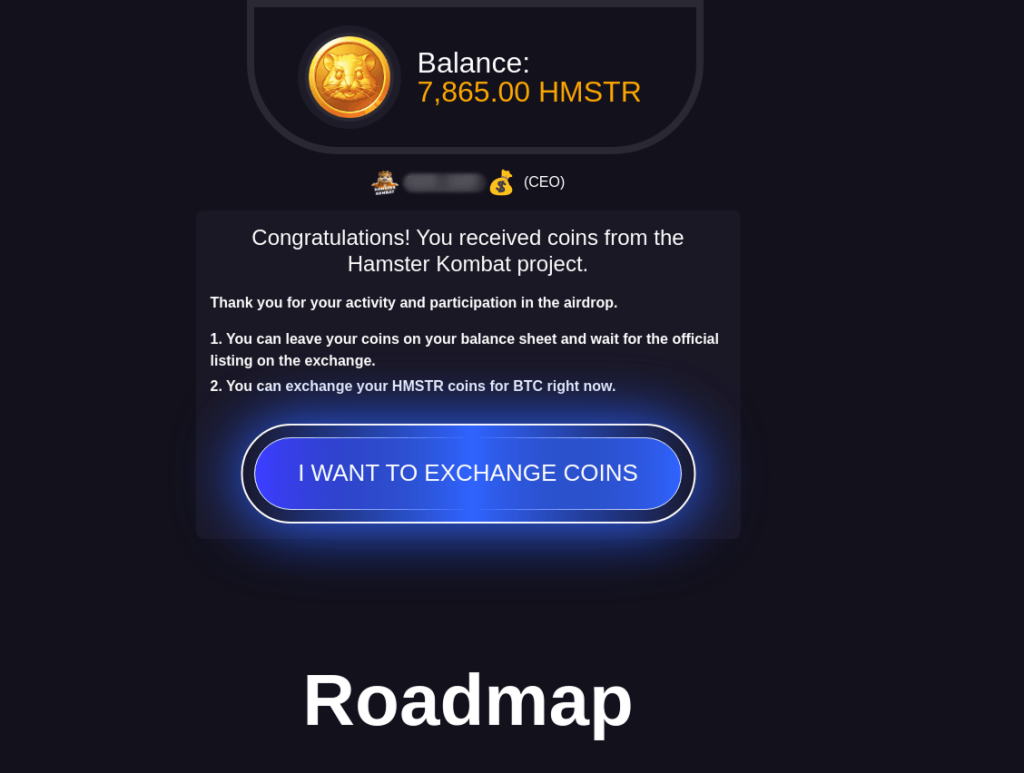
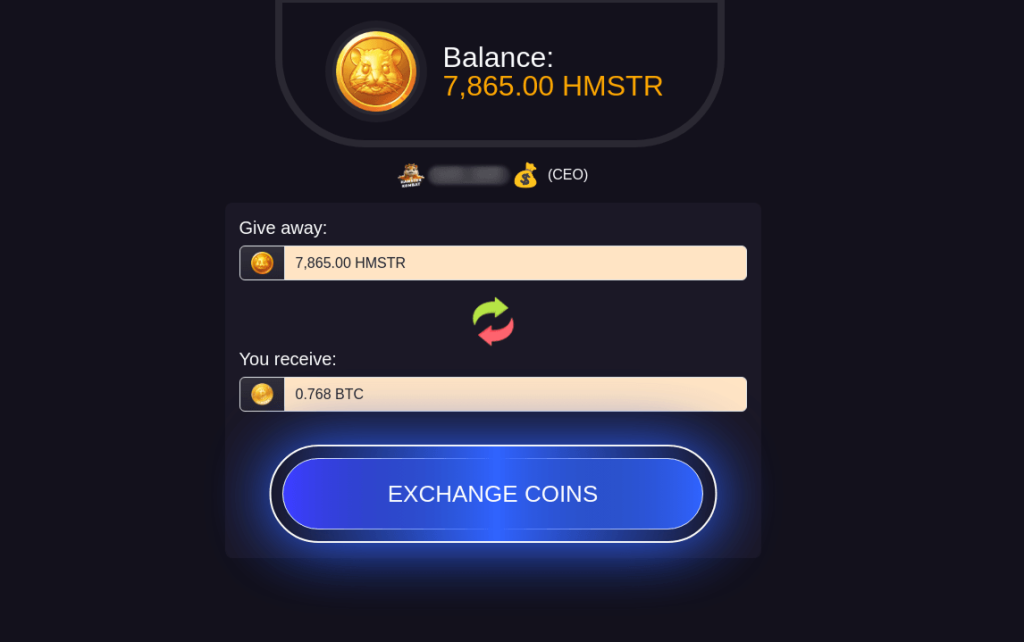
Once registered, they were suddenly informed of having won a large amount of the HMSTR cryptocurrency supposedly as part of an experiment conducted on the platform. Exploiting uncertainty around the token’s listing, scammers urged victims to bypass the official trading launch and exchange their in-game currency for Bitcoin immediately.
To make it more convincing, the page displayed an exchange rate at which the “prize” would be converted.
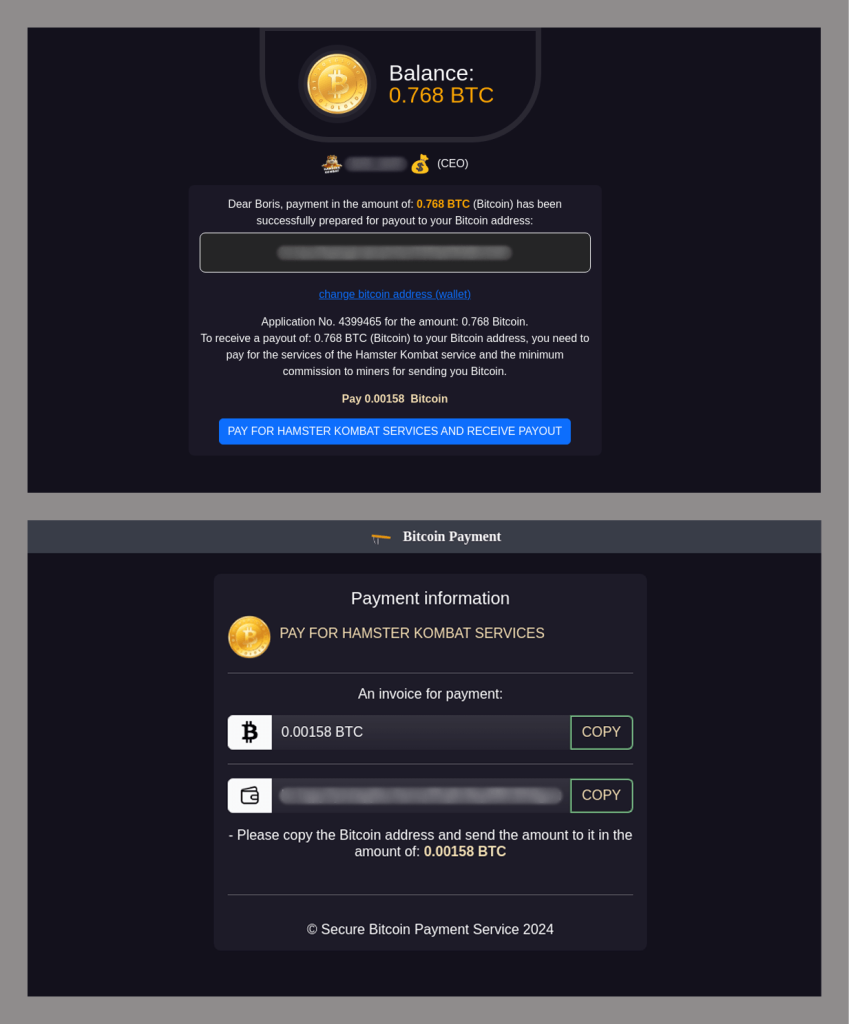
However, after clicking the “Exchange coins” button, users were prompted to pay a commission for the service.
Everyone who paid this fee lost their money and received no Bitcoin.
Phishing attacks also targeted TON wallet users. In this case, scammers lured victims with promises of bonuses, requiring them to link their crypto wallets on fraudulent websites.
TON cryptocurrency was also used as bait in scam schemes. In a classic scenario, users were promised a quick way to earn digital currency. Fraudsters advertised a cloud mining service that allegedly generated high profits without any effort. After registering, unsuspecting users could monitor their “earnings” but had to pay a commission in cryptocurrency to withdraw funds.
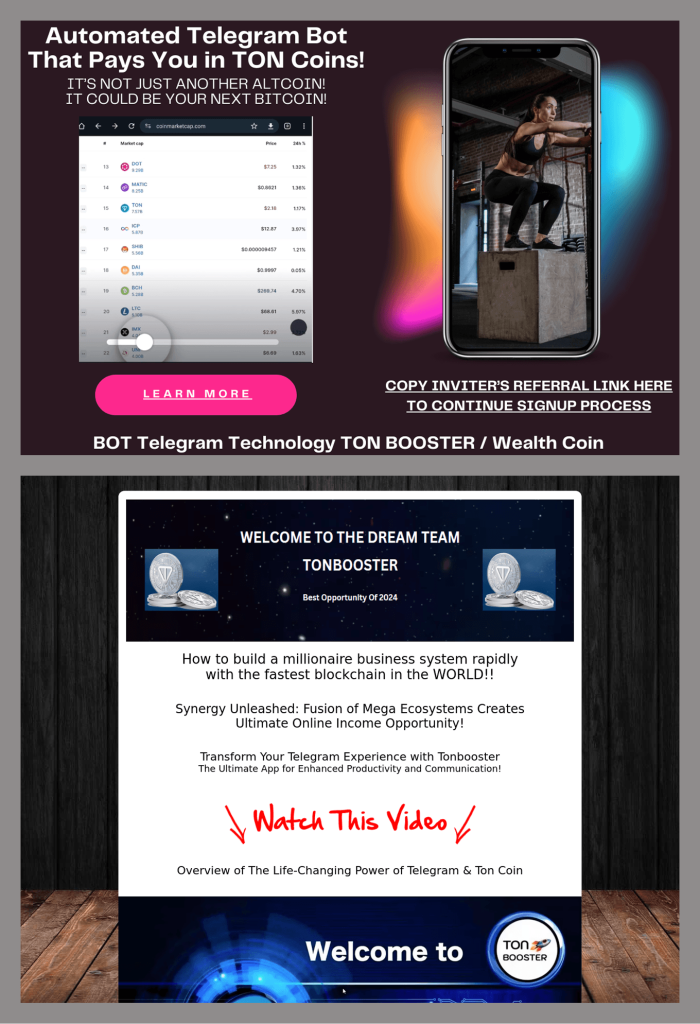
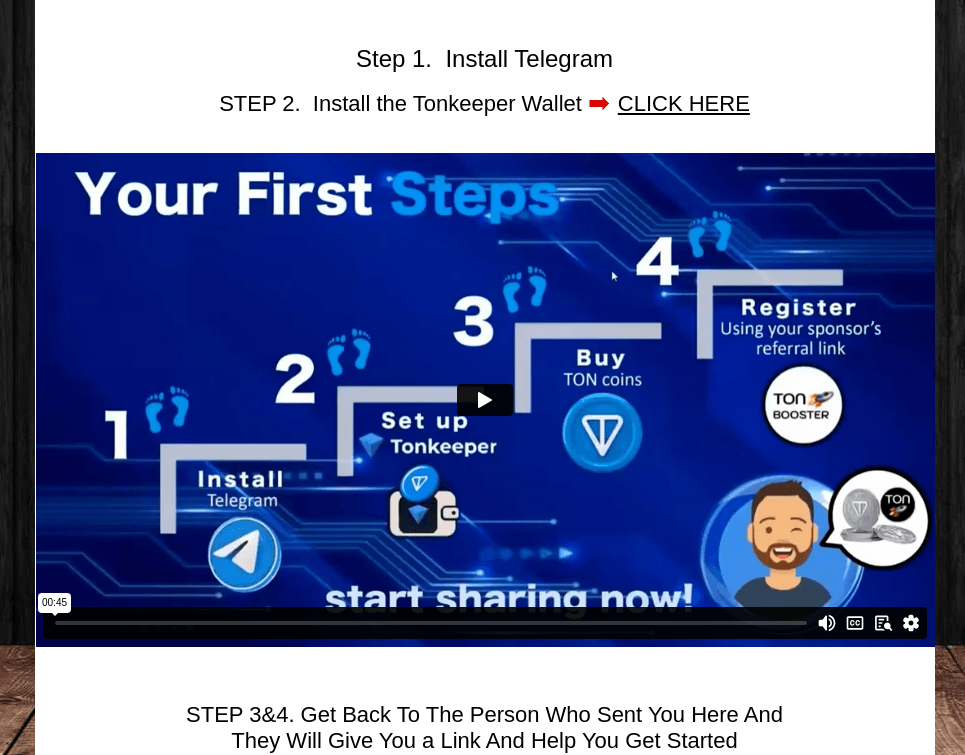
Another “profitable” crypto scam resembled a Ponzi scheme: victims were required to recruit at least five new participants into the program—without receiving any money, of course. The scam site mimicked an online earning platform.
Visitors were instructed to install Telegram and use an unofficial bot to activate a crypto wallet where profits would supposedly be deposited.
According to the instructions, users then had to buy Toncoin and register in the program through a referral link from another participant. The scam worked by enticing people to make a small investment in the hopes of making big profits—the victims used their own funds to purchase the cryptocurrency for registration. But as with any pyramid scheme, only those at the top profited, while everyone else was left with nothing but empty dreams.
All or nothing: multipurpose phishing
Victims of phishing frequently included bank clients and users of government service portals. In such schemes, users first received a notification that they needed to update their account credentials. Cybercriminals used various communication channels to contact their victims: email, text messages, and chats in messaging apps. The victims were then led to fake sites where they were asked to provide their personal data. First, they entered their personal login credentials on the organization’s website.
Next, they were prompted to provide their email account credentials. The scammers also attempted to collect identity document details and other data, including the bank card PIN code.
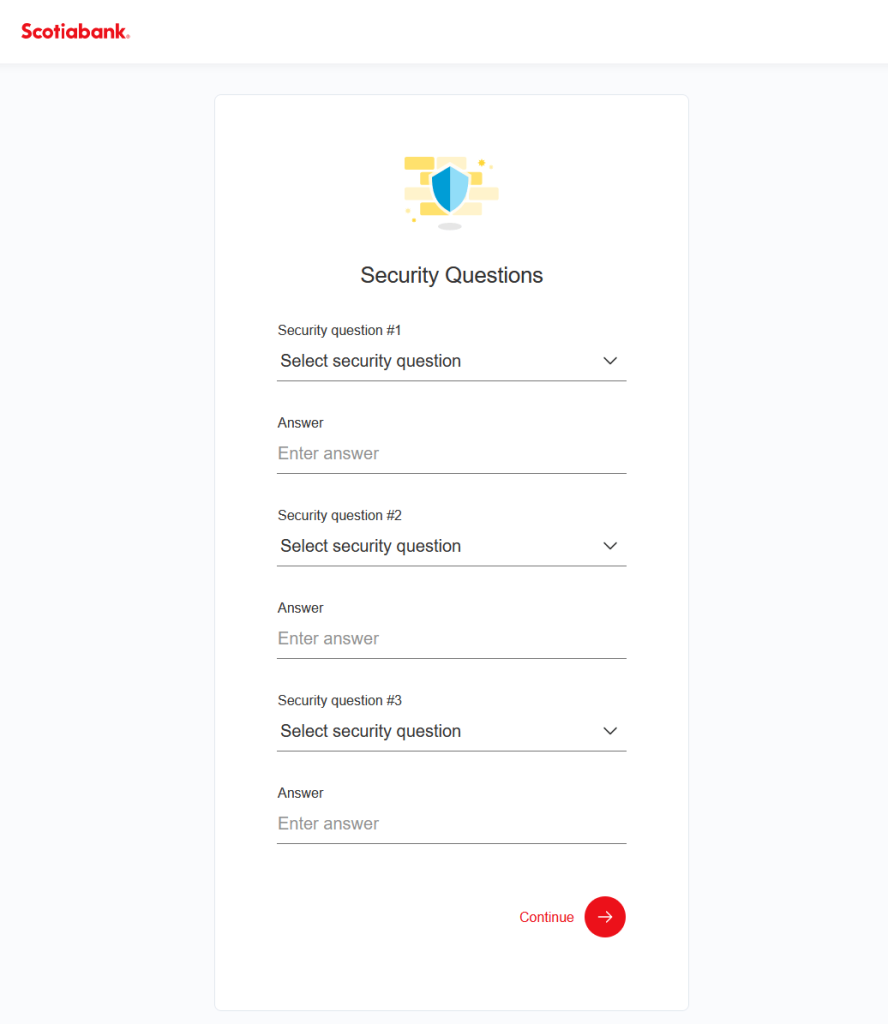
Additionally, these phishing forms requested answers to security questions commonly used for additional verification in banking transactions.
This way, the cybercriminals gained full access to the victim’s account. Even the PIN code could be useful for the scammers in gaining access to the account. Security questions served as an extra safeguard for fraudsters in case the bank’s security service detected suspicious activity.
False idols
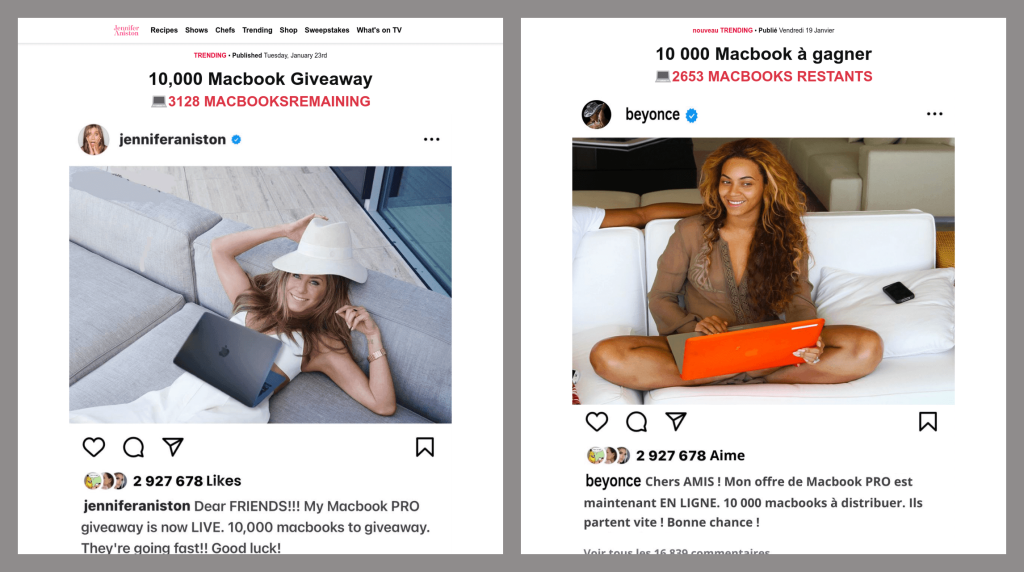
Phishing schemes also exploited the images of real people. For example, users browsing YouTube could stumble upon ad videos of celebrities announcing giveaways for their fans. Clicking the link in such a video led users to a page containing a post supposedly from the celebrity’s social media account, explaining how to claim the prize. However, when attempting to collect the “winnings”, visitors were asked to pay a small commission—insignificant compared to the value of the “gift.” Needless to say, those who paid the fee lost their money. The prize never existed, and the video was nothing more than a deepfake.
Spam in 2024
Scams
Token giveaway scam
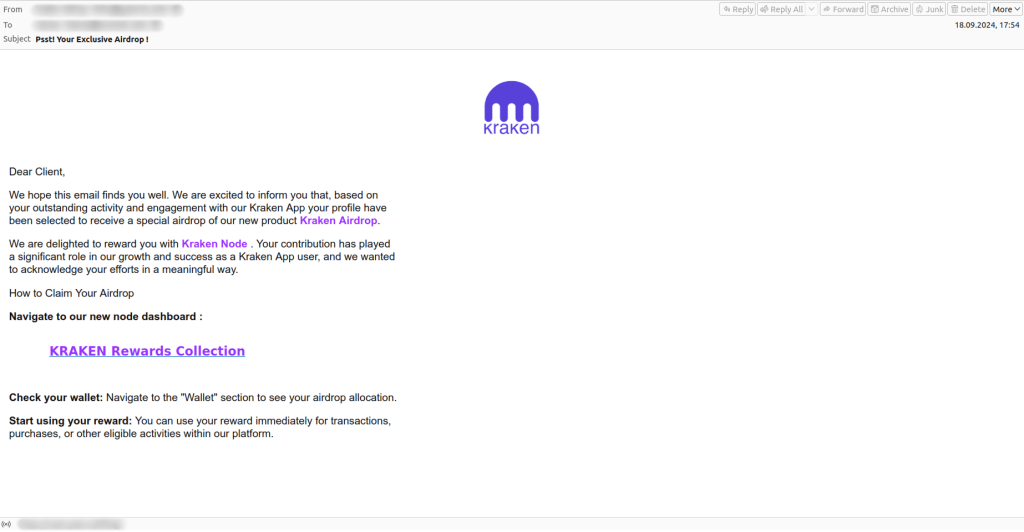
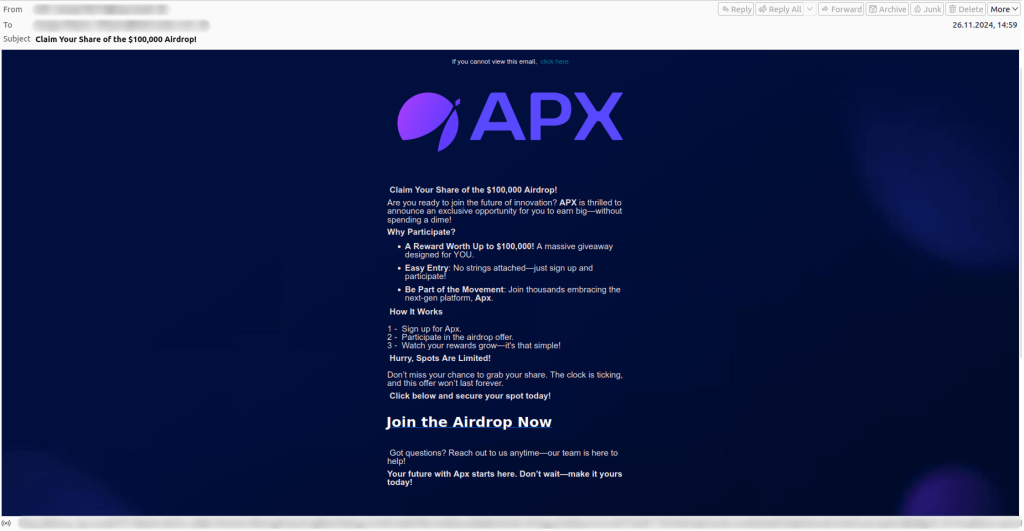
Throughout the year, we frequently encountered emails announcing fake cryptocurrency airdrops, allegedly from teams of well-known crypto projects. The recipients, referred to as the platform’s “most valuable users,” were invited to participate in an “exclusive” event as a thank you for their loyalty and exceptional engagement.
New users unfamiliar with cryptocurrency were lured in with a unique opportunity to take part in the token giveaway and win a large sum—all they had to do was register on the platform, which was, of course, fake.
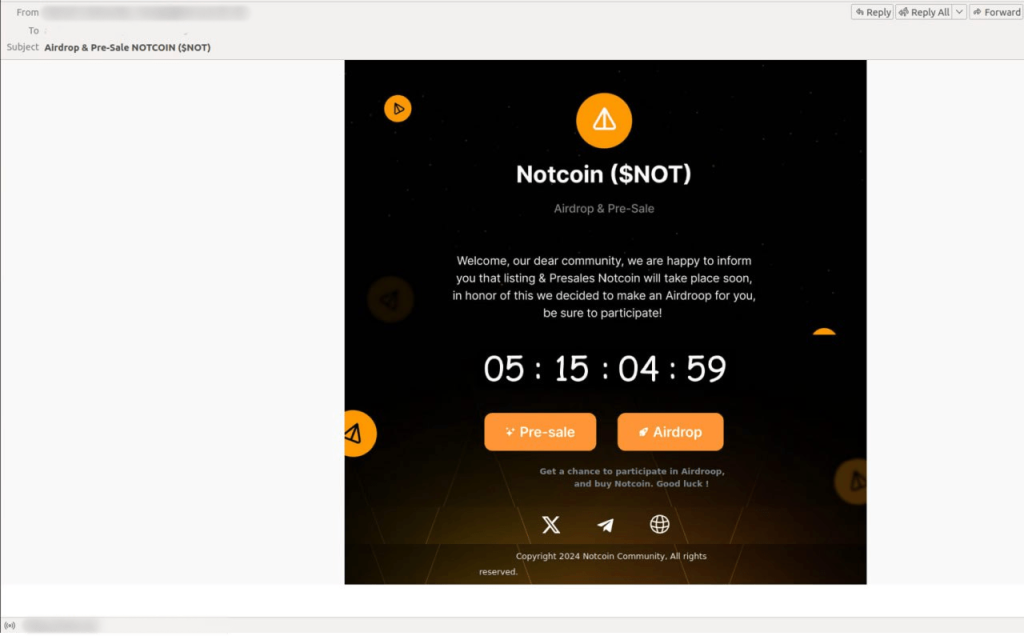
Scammers in 2024 closely monitored cryptocurrency market news. For example, in the spring, ahead of Notcoin’s upcoming listing, scam messages appeared featuring countdown timers, urging potential victims to participate in an airdrop allegedly arranged just for them.
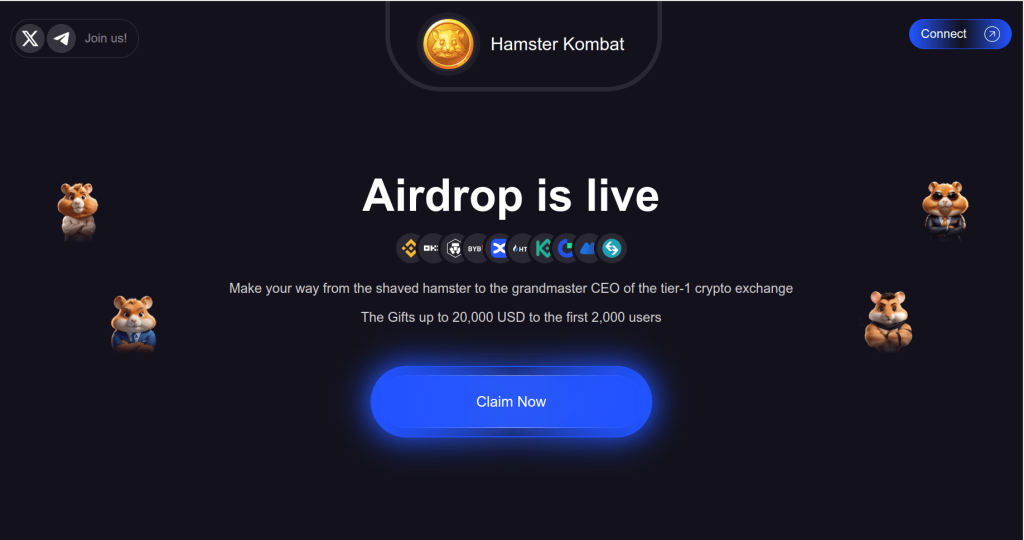
Scam emails also targeted users of the cryptocurrency game Hamster Kombat, popular among Russian-speakers. Players eagerly awaited the HMSTR token listing, which was repeatedly postponed—a delay that scammers were quick to exploit. In the fall of 2024, they began sending emails pretending to be from the Hamster Kombat team, promising generous cash prizes if victims clicked a link to a fake game site.
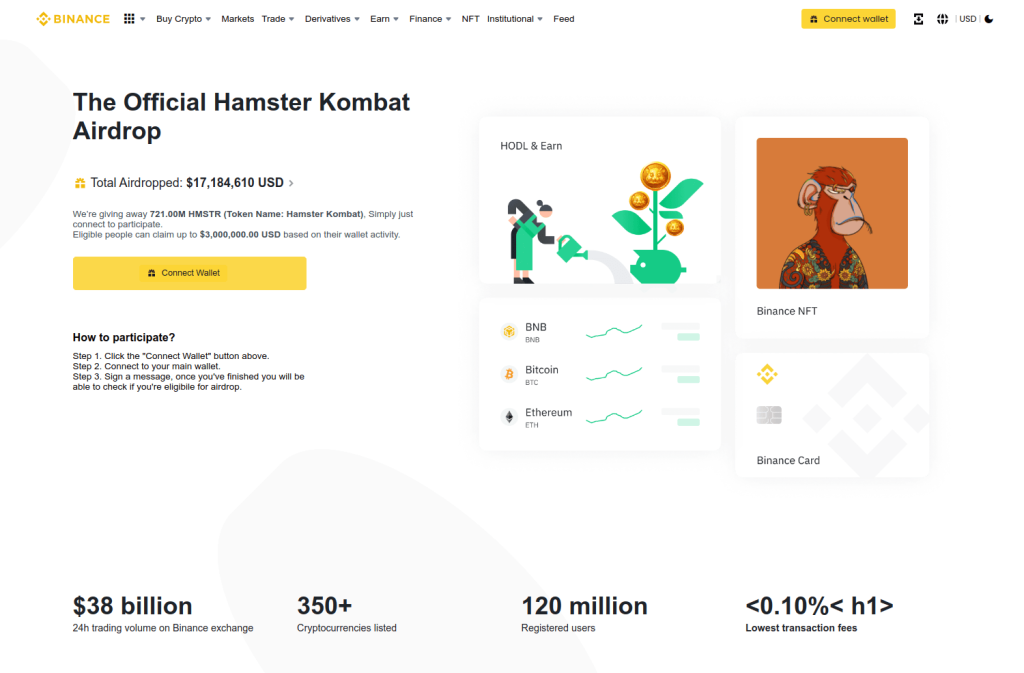
Similar offers were distributed via a fraudulent website mimicking a major cryptocurrency exchange. In both cases, to claim the coveted tokens, victims had to link their cryptocurrency wallets.
“Nigerian” scam
In 2024, the Nigerian scam remained popular among spammers. Furthermore, fraudsters used both time-tested and trending themes to deceive victims. Cybercriminals employed various tricks and manipulations to engage with email recipients, with the ultimate goal of extracting money.
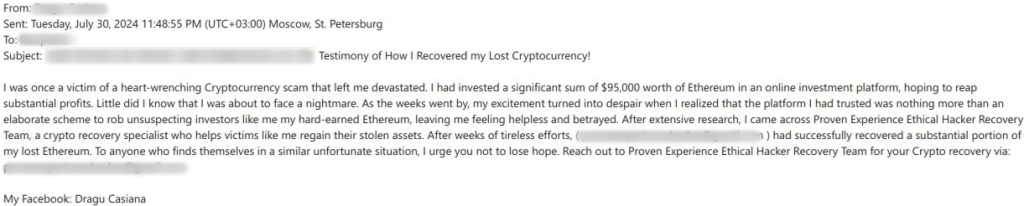
Most often, users were lured into classic schemes: fraudsters posed as terminally ill wealthy individuals seeking a worthy heir, lottery winners eager to share their prize, or investors offering opportunities in a promising business. Sometimes, to evade suspicion, scammers “rescued” their victims from other fraudsters and offered to compensate them for any financial losses. For example, in the summer of 2024, we came across an interesting case where an alleged victim of crypto fraud suggested that fellow sufferers contact a group of noble hackers for help recovering lost cryptocurrency.
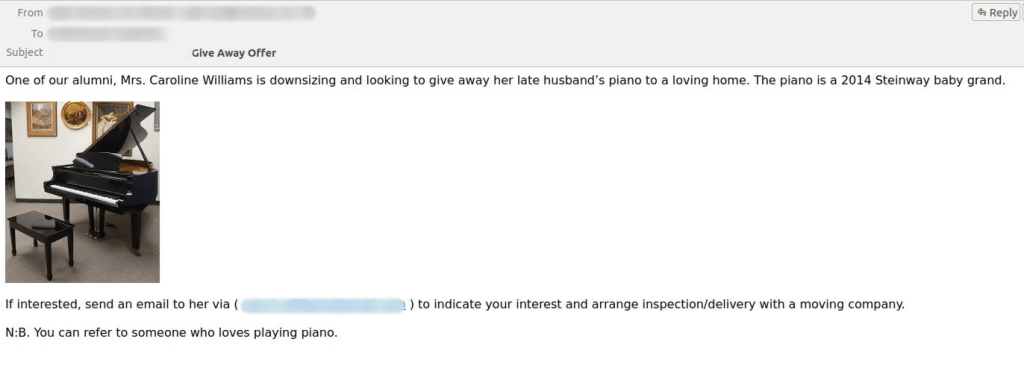
Some scam offers were quite unexpected, as they didn’t promise vast riches, and, therefore, might not attract such a wide audience. In mid-to-late 2024, we saw scam emails claiming to be looking for new owners for pianos due to relocation or the previous owner’s passing.
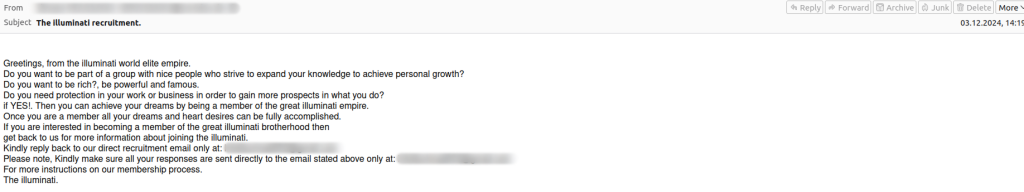
We also encountered even more creative scam narratives. For example, an email allegedly sent from a secret society of Illuminati promising to share their wealth, power and fame if the recipients agree to join their grand brotherhood.
Other “Nigerian” scam emails capitalized on current news events. Thus, the most talked-about event of 2024, the US presidential election, significantly influenced the types of scams we saw. For example, one scam email claimed that the recipients were incredibly lucky to be eligible to receive millions of dollars from Donald Trump’s foundation.
Scam in the Russian segment
Last year, the Russian segment of the internet was not spared from mass scam mailings. We frequently encountered schemes mimicking investment projects of major banks, promising users easy earnings and bonuses. Fraudsters also sent out emails with promotional offers from home appliance and electronics stores. Customers were informed of huge discounts on sales that were supposedly about to end.
The links in such emails led to fraudulent websites that looked identical to legitimate online stores but stood out with extremely low prices. After paying for their desired items, customers lost their money, as orders were never actually placed.
Beyond electronics, scammers also offered other discounted products. In one such campaign, users received an email advertising a sneaker store selling popular models at affordable prices.
Judging by the technical headers of the emails, both the sneaker store and electronics store promotions were sent by the same fraudsters.
Additionally, we came across emails offering recipients to apply for debit or credit cards under favorable conditions. Unlike the electronics and shoe sale scams, these messages were legitimate referral programs from major banks, which enterprising spammers tried to monetize. Technically, such emails are not scams, as their links lead to real banking websites, and recipients do not face any risks. However, senders profit from registrations via the referral program. Nevertheless, we do not recommend clicking links from unknown senders, as seemingly harmless emails from a referral platform could be phishing or scam messages.
Emails with malicious links and attachments
Password-protected archives
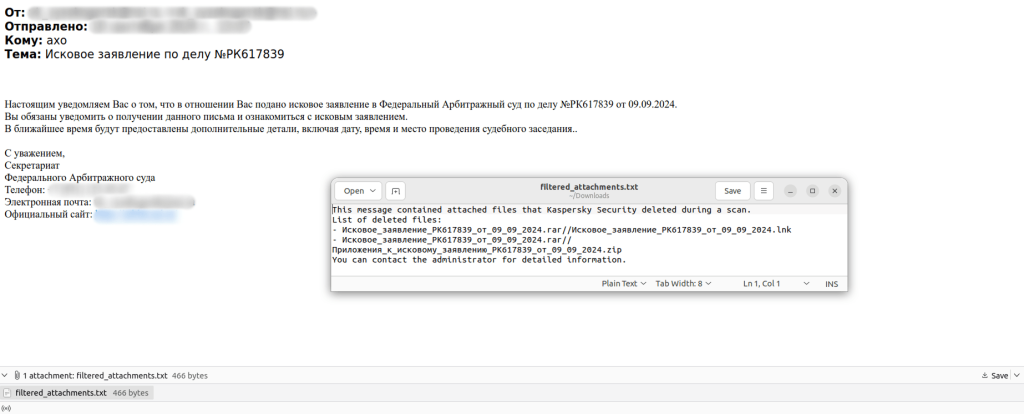
In 2024, there was an increase in emails distributing password-protected archives containing malicious content. Sometimes, these files were included not as attachments but via download links, which also required a password. Presumably, this was the attackers’ attempt to bypass email security filters. Typically, the archive password was mentioned in the email text, and sometimes in the attachment’s filename. Notably, fraudsters often disguised malicious archives or links as files with other extensions, such as PDF, XLS, or DOC.
Since April 2024, we have been recording similar distributions of files with the double extension .PDF.RAR, targeting employees of Russian companies in the government, financial, manufacturing, and energy sectors.
We assume that these messages were sent from compromised email accounts of the recipients’ business partners. Some emails contained real correspondence, to which attackers replied with an email containing the malware. All the emails we examined in this campaign were unique. The attackers likely crafted messages to closely mimic the style of the compromised business partner.
Similar messages containing malicious files were also found in other languages. However, unlike campaigns targeting Russian-speaking users, these had more general themes—attachments were disguised as invoices, commercial offers, supply orders, tender schedules, court notices, and other documents.
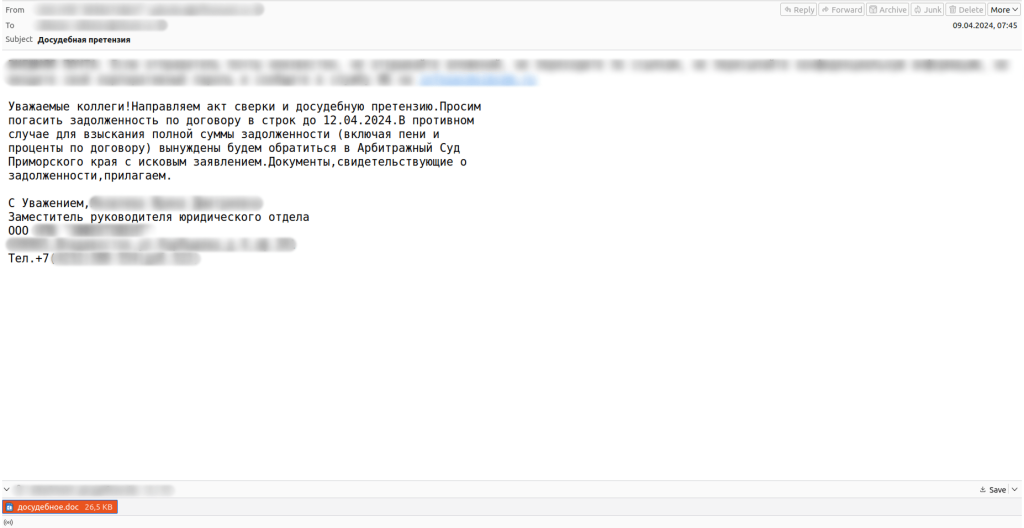
Pre-trial claims and lawsuits
Last year, attackers frequently threatened legal action to convince victims to click dangerous links or open malicious attachments. These messages primarily targeted Russian companies but were also observed in other languages. Typically, fraudsters posed as business partners, demanding debt repayment; otherwise, they “would be forced to take the matter to arbitration court.” In one such campaign, pre-trial claims in attachments were .DOC files containing VBA scripts. These scripts established connections with command servers and downloaded, saved, and executed malicious files on the victim’s device. Kaspersky’s products detect this payload with the verdict HEUR:Trojan-Downloader.MSOffice.Sload.gen.
In some cases, cybercriminals gave no reason for their legal threats but instead attempted to shock victims with an already “filed” lawsuit to pressure them into opening the attachment. Of course, it contained malware.
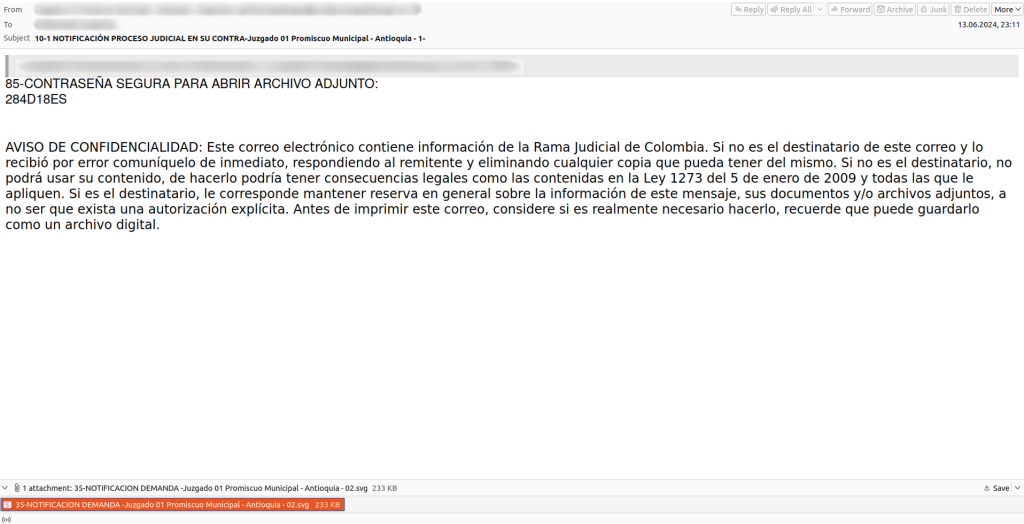
Emails with malicious SVG files
According to our observations, the past year saw a rise in the distribution of malicious SVG files. Disguised as harmless images, these files contained scripts that downloaded and installed additional malware on the victim’s device. (Our solutions detect these scripts as Trojan.Script.Agent.sy and Trojan.Script.Agent.qe.) The emails we encountered were written in Spanish and posed as fake legal case notifications and court summons. The text included a password for opening the attached file.
Threats to businesses
Fake deals
A special category of emails that users complained about in 2024 was requests for quotation from suspicious senders. These emails were sent either from free email addresses or recently created domains. Attackers signed the emails with the names of large companies, included links to their websites, and sometimes even used official company logos. These emails followed a uniform template: the “buyers” briefly introduced themselves, expressed interest in the recipient’s products, and requested a catalog or price list. Interestingly, the fraudsters did not seem to care about the type of goods involved.
If the recipient responded, events could unfold in two ways. In some cases, after receiving a reply to the initial seemingly legitimate request, the fraudsters sent malicious attachments or links in the next email.
In another scenario, the “buyers” engaged in further correspondence with their “potential partner”—the victim—discussing details and insisting on their conditions, including post-payment and requiring the seller to cover customs duties. This meant that the supplier bore all the risks of delivery and could lose their goods without receiving any payment.
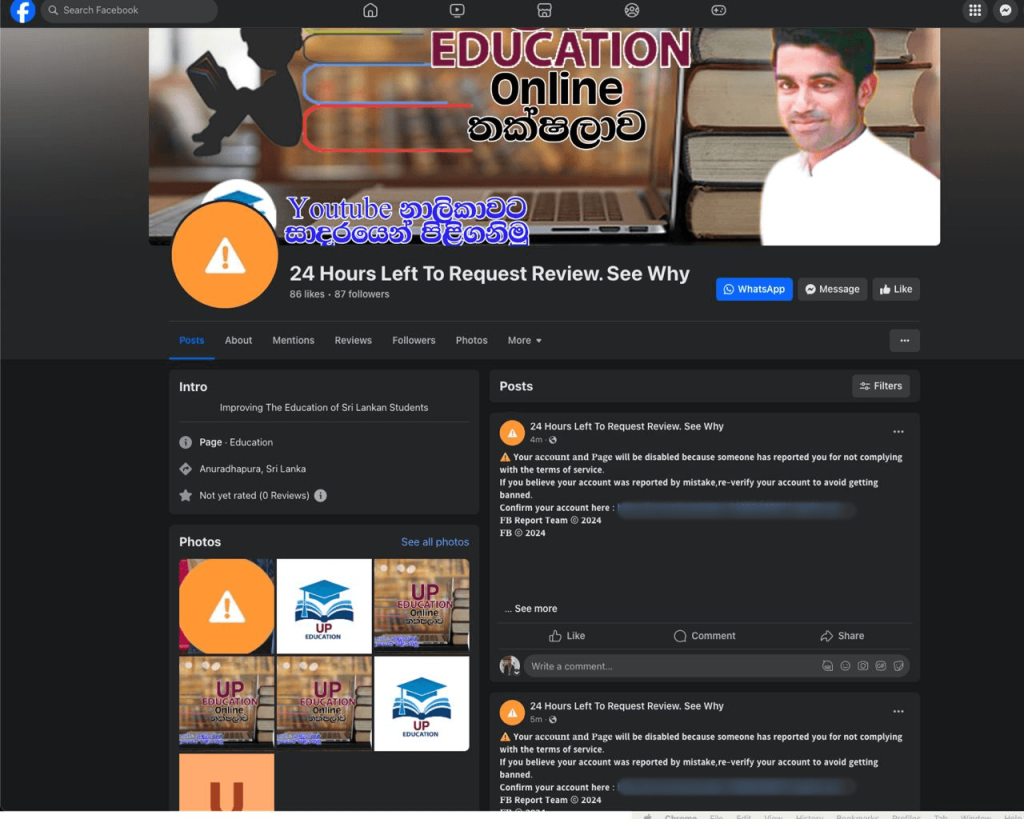
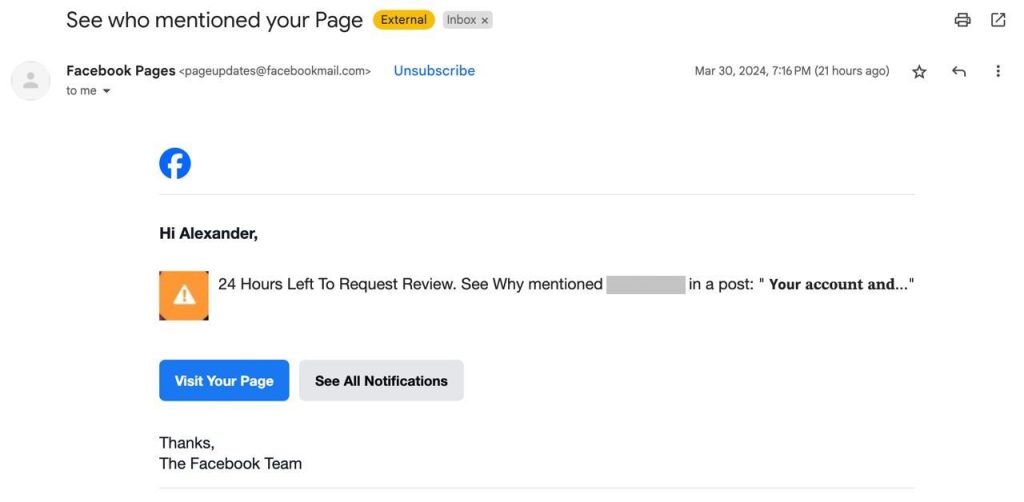
In the spring of 2024, we discovered an interesting phishing email scheme that leveraged legitimate Facebook notifications. The service sent entirely legitimate emails to users mentioned in threatening posts. The attackers used compromised Facebook accounts, renamed to “24 Hours Left To Request Review. See Why,” and changed the profile picture to an icon featuring an orange exclamation mark.
Then, the fraudsters created posts on these pages tagging the business accounts of potential victims. The tagged users received notifications from the alarmingly-named pages.
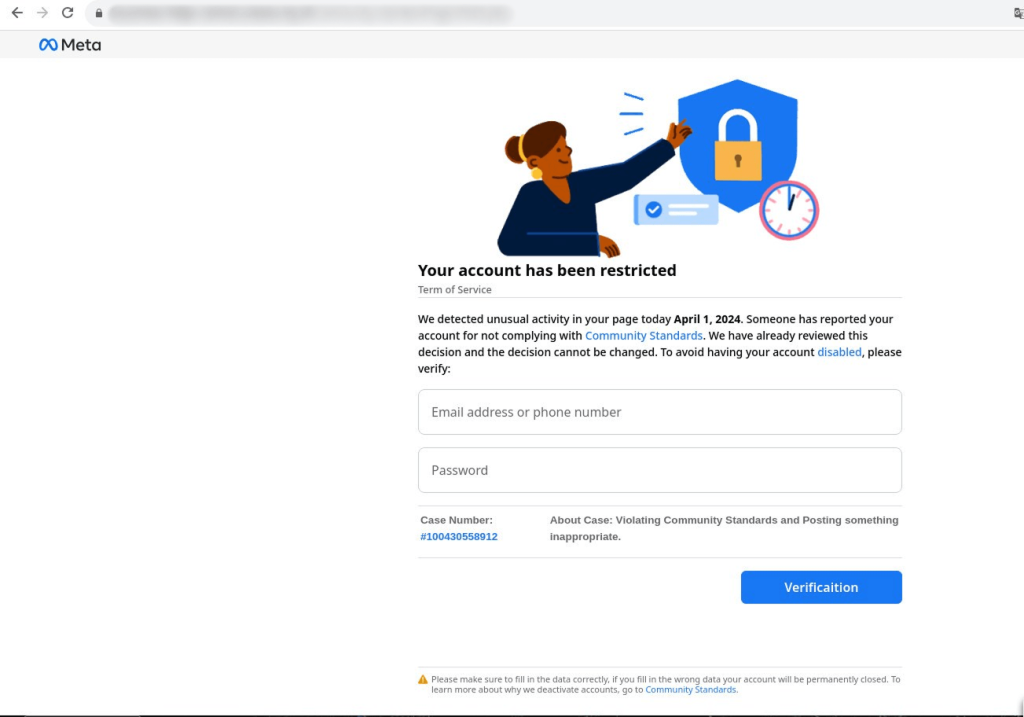
These posts contained more details than the emails: victims were warned about an impending account ban due to a complaint from another user. To dispute the ban for violating service terms, the recipient of the “notification” was required to follow a phishing link from the post—leading to a fake site with Meta logos that requested Facebook login credentials.
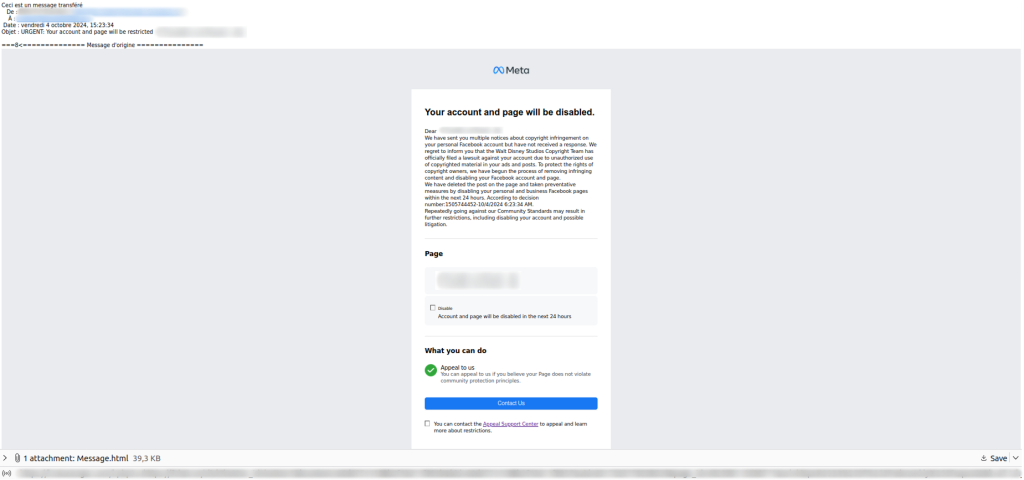
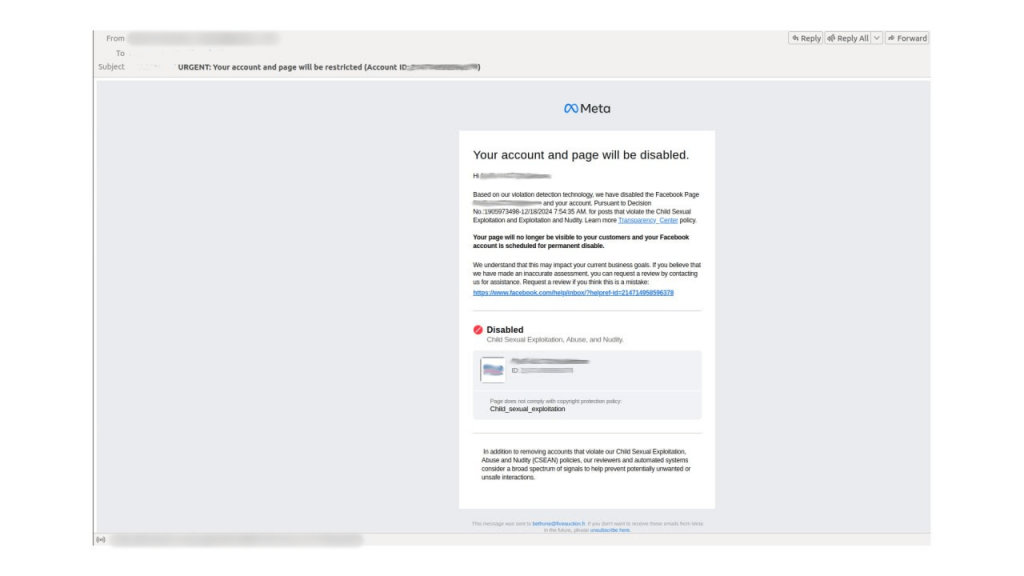
We also found phishing emails containing legitimate Facebook links in October 2024, but this time without using the platform’s infrastructure. These emails contained notifications of lawsuits for copyright infringement and the removal of unlawful posts from the recipient’s profile. The target was warned that their personal and business pages would be blocked within 24 hours, pressuring them to take hasty and careless action.
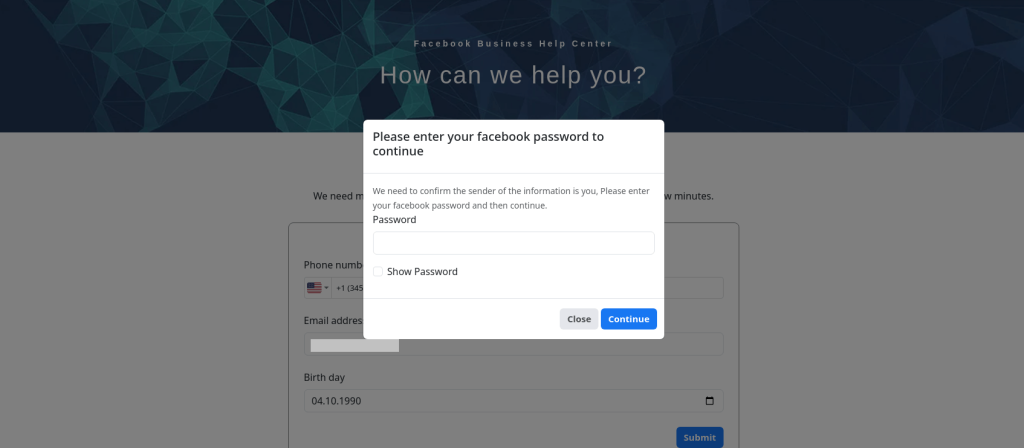
However, they were immediately offered the chance to appeal by contacting the “Appeal Support Center.” The link in the email led to a phishing site disguised as Meta’s support service, where the victim was also asked to enter their profile password. To make the phishing link more convincing, a legitimate mechanism for redirecting users to external Facebook resources was used.
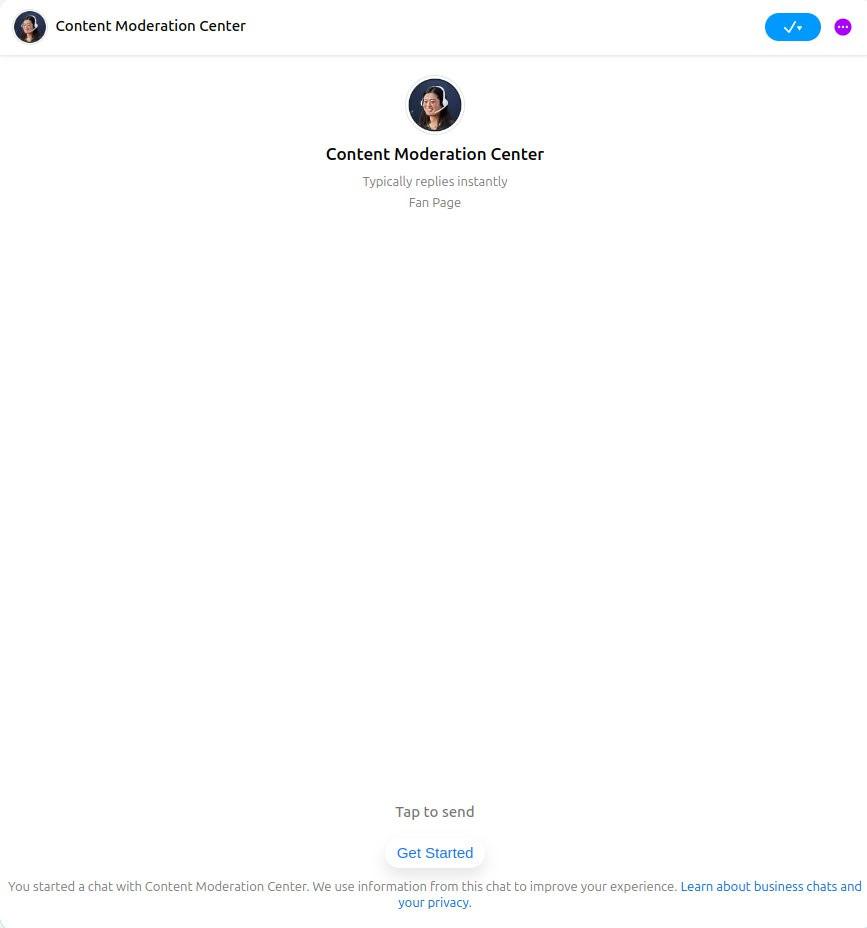
At the end of 2024, we noticed an email campaign targeting companies promoting their business pages on Facebook. These emails mimicked official Meta for Business notifications and threatened to block the user’s account and business page for violating the platform’s rules and community policies.
To dispute these accusations, the fraudsters urged the profile owners to click a link to contact “Facebook support” in a legitimate messenger. However, in reality, the victim was communicating with the owner of a fan page called “Content Moderation Center,” imitating an official support service employee. The scam could have been identified by the “Fan Page” label in the chat, though it was easy to miss.
News agenda
In 2024, scammers continued to exploit news agenda in spam campaigns.
During the UEFA Euro 2024 football championship in Germany, emails began to appear offering merchandise with UEFA EURO 2024 logos.
After Pavel Durov’s arrest in Paris, we noticed English-language messages calling for donations to supposedly fund his legal defense.
In the fall of last year, a scam campaign began circulating, offering not-yet-released MacBook Pro M4 devices at low prices or even for free. The links in these emails led to fake websites imitating major marketplaces.
Before Black Friday, we recorded a surge in spam offering exclusive discounts. The links in these messages lured victims to sites disguised as marketplaces, electronics stores, and financial institutions.
B2B spam campaigns
Online promotion services
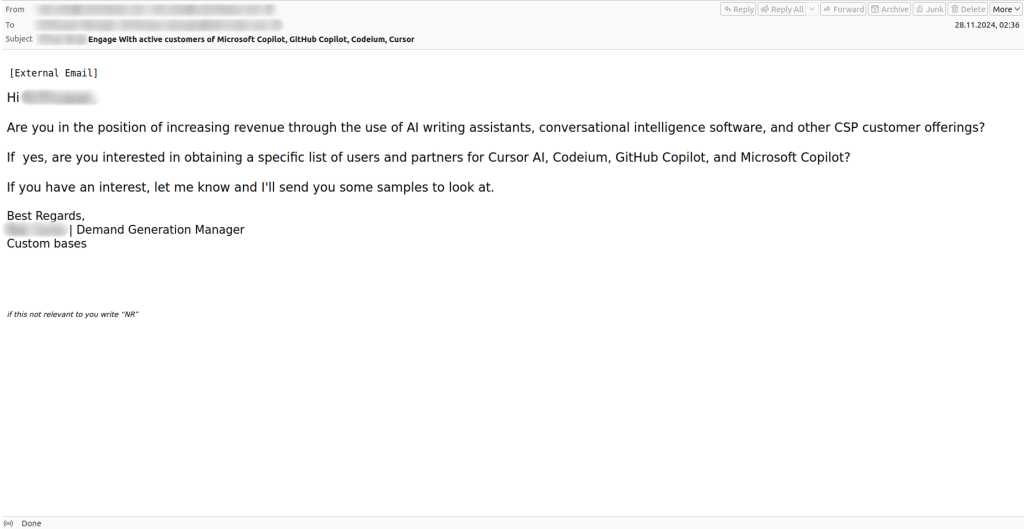
One of the most common categories of spam email in 2024, complained of frequently by our corporate clients, was commercial offers for online promotion. Users were offered services such as creating or redesigning websites, setting up SEO tools, and purchasing databases with potential client contacts and other information. Other advertised services included guest post placement with backlinks to the client’s site, writing positive reviews, removing negative reviews, and creating personalized email campaigns. While these messages are not malicious or fraudulent, they are mass-distributed and unsolicited, causing inconvenience to users. The popularity of this type of spam is likely driven by the development of digital marketing tools and the search for new clients for small- and medium-sized businesses amid growing online competition.
Buying likes and followers on social media
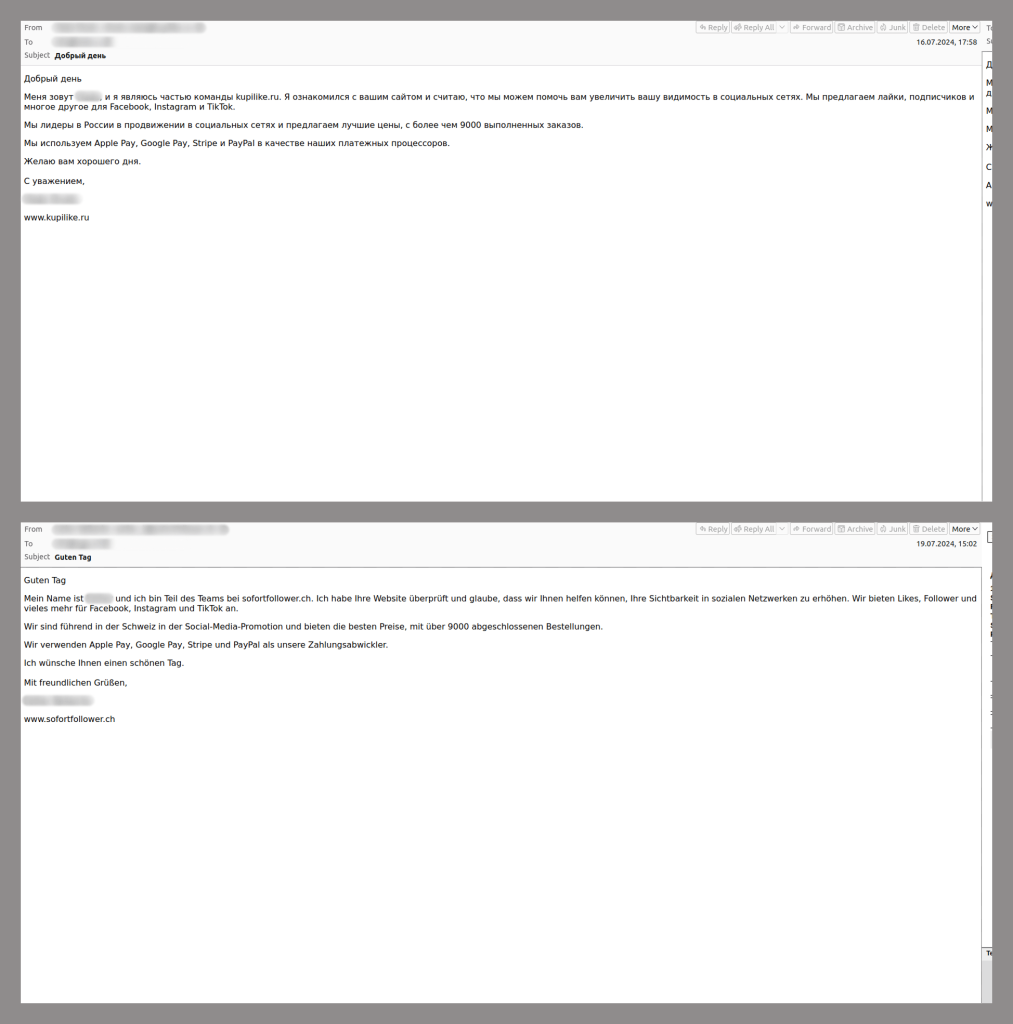
We also frequently encountered business offers for the online promotion of company accounts on social media. Spammers sell fake likes and followers. They often pose as employees of real social media marketing firms, claiming to be industry leaders. At the end of their emails, the spammers included a link to a marketing platform and payment options for their services. One such campaign, which we observed throughout the past year and is still active, stood out due to the variety of languages used in the emails and the diversity of domain names. With these tactics, the spammers aimed to reach a global audience.
AI in B2B emails
The growing popularity of neural networks has led companies to actively integrate AI into their business processes. We assume that clients of such organizations, in turn, are drawn to service offers that incorporate neural networks. As a natural consequence of this trend, AI-driven solutions began appearing in spam campaigns advertising online marketing services.
Spammers emphasized using AI, particularly ChatGPT, to perform various business tasks. We identified the following themes in these emails:
- Attracting website traffic
- Creating advanced lead generation strategies
- Developing unique approaches tailored to a brand’s identity
- Producing and publishing content
- Launching personalized multi-channel marketing campaigns
- Creating custom videos for YouTube channels
Other topics also appeared in spam emails, but they all shared the same goal—enhancing business processes and attracting potential clients.
Another particularly popular category of spam related to neural networks was advertising online events. Last year, we encountered numerous examples of emails promoting webinars about the promising capabilities and practical applications of AI in business operations.
Targeted phishing in 2024
In 2024, two main trends were observed in targeted phishing:
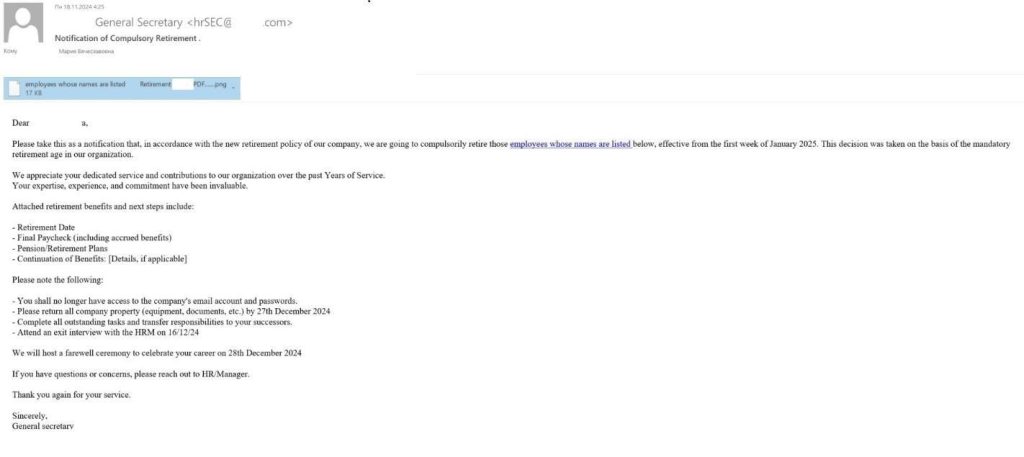
- Notifications on behalf of a company’s HR department. Employees were asked to fill out or sign a document, such as a vacation schedule, accessible via a link in an email. Sometimes, instead of routine requests, attackers resorted to more extravagant tactics—such as inviting employees to check if they were on a list of staff to be dismissed.
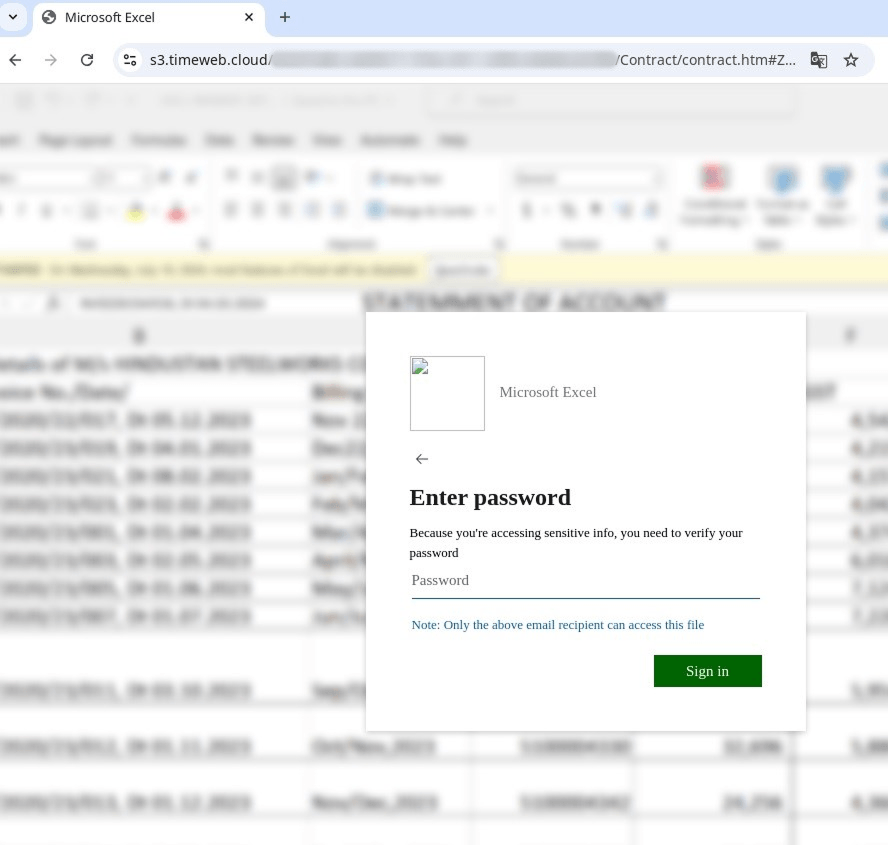
In all these cases, the common factor was that clicking the link led the employee to a phishing login page instead of the actual corporate portal. Most often, attackers targeted Microsoft accounts, though some phishing forms mimicked internal corporate resources.
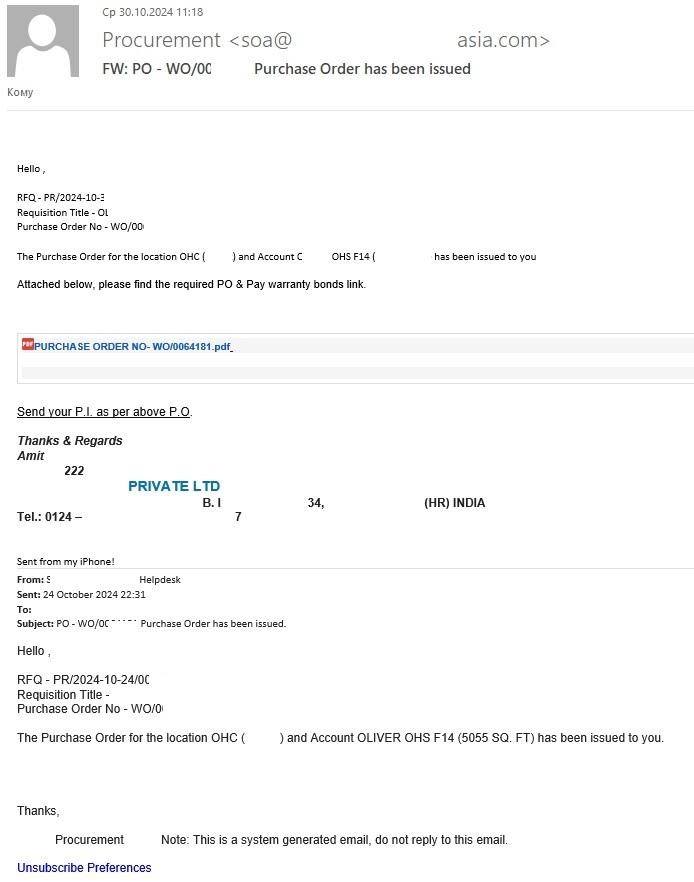
- Emails from a seller to a buyer, or vice versa. One common scheme involved a buyer or seller asking the victim to review an offer or respond to questions about product delivery and required specifications. These emails contained attached documents that actually concealed phishing links.
When attempting to open the attachment, the user was redirected to a phishing page. As in the previous case, these fake forms harvested Microsoft credentials and corporate account logins.
Statistics: phishing
The number of phishing attacks in 2024 increased compared to the previous year. Kaspersky solutions blocked 893,216,170 attempts to follow phishing links—26% more than in 2023.
Number of Anti-Phishing triggerings, 2024 (download)
Map of phishing attacks
Users from Peru (19.06%) encountered phishing most often. Greece (18.21%) ranked second, followed by Vietnam (17.53%) and Madagascar (17.17%). They are closely followed by Ecuador (16.90%), Lesotho (16.87%) and Somalia (16.70%). The final places in the TOP 10 are occupied by Brunei (16.55%), Tunisia (16.51%) and Kenya (16.38%).
| Country/territory | Share of attacked users* |
| Peru | 19.06 |
| Greece | 18.21 |
| Vietnam | 17.53 |
| Madagascar | 17.17 |
| Ecuador | 16.90 |
| Lesotho | 16.87 |
| Somalia | 16.70 |
| Brunei | 16.55 |
| Tunisia | 16.51 |
| Kenya | 16.38 |
* Share of users who encountered phishing out of the total number of Kaspersky users in the country/territory, 2024
Top-level domains
The most common domain zone hosting phishing sites remains the COM zone (29.78%)—its popularity has increased one and a half times compared to 2023. In second place is the XYZ domain (7.10%), which ranked fifth last year, followed by TOP (6.97%), which retained its position in the top ten. Next, with a slight margin from each other, are the ONLINE (4.25%) and SITE (3.87%) domain zones, where phishing sites were less actively hosted last year. The Russian RU domain (2.23%) and the global NET domain (2.02%) are in sixth and seventh place, respectively. Following them are CLICK (1.41%) and INFO (1.35%)—the year before, these zones were not frequently used. Closing the top ten is another national domain: UK, with a share of 1.33%.
Most frequent top-level domains for phishing pages, 2024 (download)
Organizations targeted by phishing attacks
The rating of organizations targeted by phishers is based on the detections of the deterministic component in the Anti-Phishing system on user computers. The component detects all pages with phishing content that the user has tried to open by following a link in an email message or on the web, as long as links to these pages are present in the Kaspersky database.
In 2024, the highest number of attempts to access phishing links blocked by Kaspersky solutions was associated with pages imitating various web services (15.75%), surpassing global internet portals (13.88%), which held the top position in 2023. The third and fourth positions in last year’s top ten also swapped places: banks moved ahead (12.86%), overtaking online stores at 11.52%. Attackers were also interested in social media (8.35%) and messengers (7.98%): attacks targeting them strengthened their positions in the ranking. For websites imitating delivery services, we observed a decline in phishing activity (6.55%), while the share of payment systems remained unchanged at 5.82%. Also included in the list of the most frequently targeted organizations were online games (5.31%) and blogs (3.75%).
Distribution of organizations targeted by phishers, by category, 2024 (download)
Statistics: spam
Share of spam in email traffic
In 2024, spam emails accounted for 47.27% of the total global email traffic, an increase of 1.27 p.p. compared to the previous year. The lowest spam levels were recorded in October and November, with average shares dropping to 45.33% and 45.20%, respectively. In December, we observed a seemingly slight upward trend in junk emails, resulting in the fourth quarter of the year being the calmest. Spam activity peaked in the summer, with the highest number of emails recorded in June (49.52%) and July (49.27%).
Share of spam in global email traffic, 2024 (download)
In the Russian internet segment, the average spam share exceeded the global figure, reaching 48.57%, which is 1.98 p.p. higher than in 2023. As in the rest of the world, spammers were least active at the end of the year: in the fourth quarter, 45.14% of emails were spam. However, unlike global trends, in Runet, we recorded four months during which the spam share exceeded half of all traffic: March (51.01%), June (51.53%), July (51.02%), and September (51.25%). These figures identified the third quarter as the most active, with a share of 50.46%. December was the calmest month, and interestingly, despite spam levels being generally high or the same in Russia, the number of spam emails in December was lower than the global figure: 44.56%.
Share of spam in Runet email traffic, 2024 (download)
Countries and territories where spam originated
We continue to observe an increase in the share of spam sent from Russia—from 31.45% to 36.18%. The United States and mainland China, which held second and third place last year, swapped positions, with China’s share increasing by 6 p.p. (17.11%) and the US share decreasing by 3 p.p. (8.40%). Kazakhstan, which entered the top twenty for the first time last year, rose from eighth to fourth place (3.82%), pushing Japan (2.93%) down, and causing Germany, previously in fifth place, to drop one position with a share of 2.10%. India’s share slightly decreased, but the country moved up two positions from last year to seventh place. Conversely, the amount of spam sent from Hong Kong more than doubled (1.75%), allowing this territory to take eighth place in the top twenty. Next come Brazil (1.44%) and the Netherlands (1.25%), whose shares continued to decline.
TOP 20 countries and territories where spam originated in 2024 (download)
Malicious email attachments
In 2024, Kaspersky solutions detected 125,521,794 attempts to open malicious email attachments, ten million fewer than the previous year. Interestingly, one of the peaks in email antivirus detections occurred in April—in contrast to 2023, when this month had the lowest malicious activity. In January and December, we observed a relative decrease in detections, while increases were noted in spring and autumn.
Number of email antivirus detections, 2024 (download)
The most common malicious email attachments were Agensla stealers (6.51%), which ranked second last year. Next were Badun Trojans (4.51%), which spread in archives disguised as electronic documents. The Makoob family moved from eighth to third place (3.96%), displacing the Noon spyware (3.62%), which collects browser passwords and keystrokes. The malicious Badur PDFs, the most common attachments in 2023, dropped to fifth place with a 3.48% share, followed by phishing HTML forms from the Hoax.HTML.Phish family (2.93%). Next in line were Strab spyware Trojans (2.85%), capable of tracking keystrokes, taking screenshots, and performing other typical spyware actions. Rounding out the top ten were SAgent VBS scripts (2.75%), which were not as actively used last year, the Taskun family (2.75%), which maintained its previous share, and PDF documents containing phishing links, Hoax.PDF.Phish (2.11%).
TOP 10 malware families distributed as email attachments, 2024 (download)
The list of the most widespread malware reflects trends similar to the distribution of families, with a few exceptions: the Hoax.HTML.Phish variant of malicious HTML forms dropped two positions (2.20%), and instead of a specific Strab Trojan sample, the top ten included the ISO image Trojan.Win32.ISO.gen, distributed via email (1.39%).
TOP 10 malicious programs distributed as email attachments, 2024 (download)
Countries and territories targeted by malicious mailings
In 2024, users in Russia continued to face malicious email attachments more frequently than other countries, although the share of email antivirus detections in this country decreased compared to last year, to 11.37%. China ranked second (10.96%), re-entering the top twenty after several years. Next came Spain (8.32%), Mexico (5.73%), and Turkey (5.05%), which dropped one position each with a slight decline in malicious attachments. Switzerland (4.82%) took sixth place, appearing in the ranking for the first time. Following them were Vietnam (3.68%), whose share declined, and the UAE (3.24%), which strengthened its position in the ranking. Also among frequent targets of malicious spam were users from Malaysia (2.99%) and Italy (2.54%).
TOP 20 countries and territories targeted by malicious mailings, 2024 (download)
Conclusion
Political and economic crises will continue to provide new pretexts for fraudulent schemes. In some cases presented in the 2024 report, we can observe the “greed” of cybercriminals: the use of two different company brands on the same page; a credible fake of a resource aimed not at stealing credentials but at stealing money; comprehensive questionnaires that can lead not only to loss of access to funds but also to identity theft. Such multi-layered threats may become a new trend in phishing and scam attacks.
We continue to observe major news events being exploited in spam campaigns that promise easy earnings and discounted goods or services. The growing user interest in artificial intelligence tools is actively being leveraged by spammers to attract an audience, and this trend will undoubtedly continue.


























Spam and phishing in 2024