
Quarterly highlights
The corporate sector
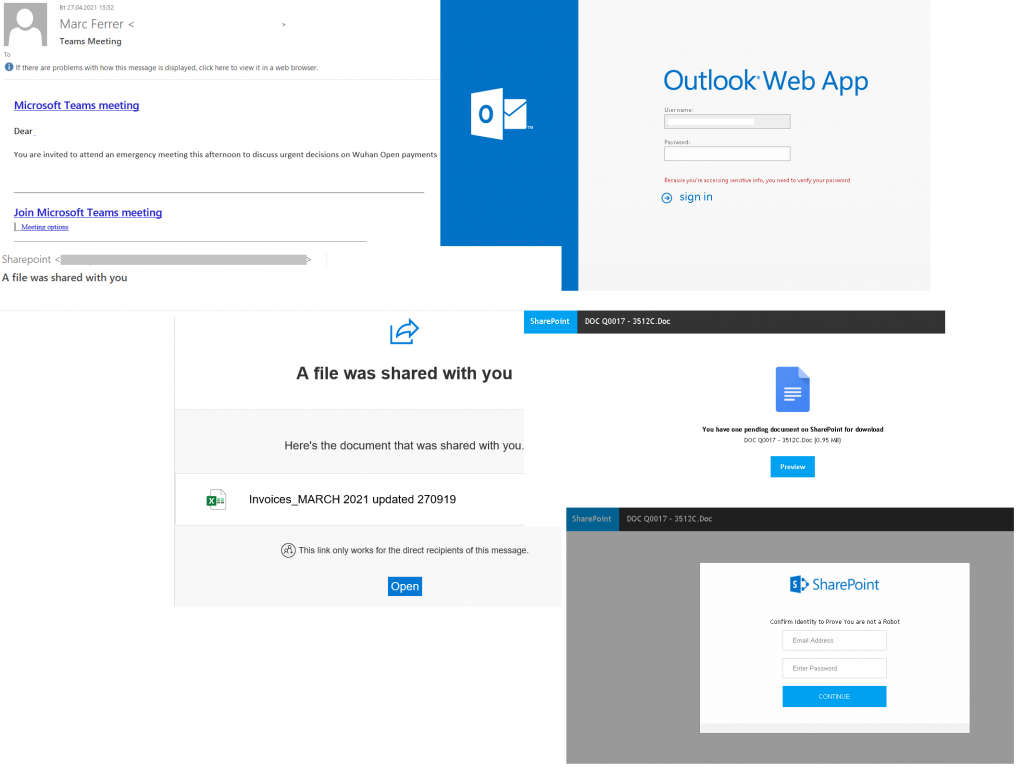
In Q2 2021, corporate accounts continued to be one of the most tempting targets for cybercriminals. To add to the credibility of links in emails, scammers imitated mailings from popular cloud services. This technique has been used many times before. A fake notification about a Microsoft Teams meeting or a request to view an important document traditionally takes the victim to a phishing login page asking for corporate account credentials.
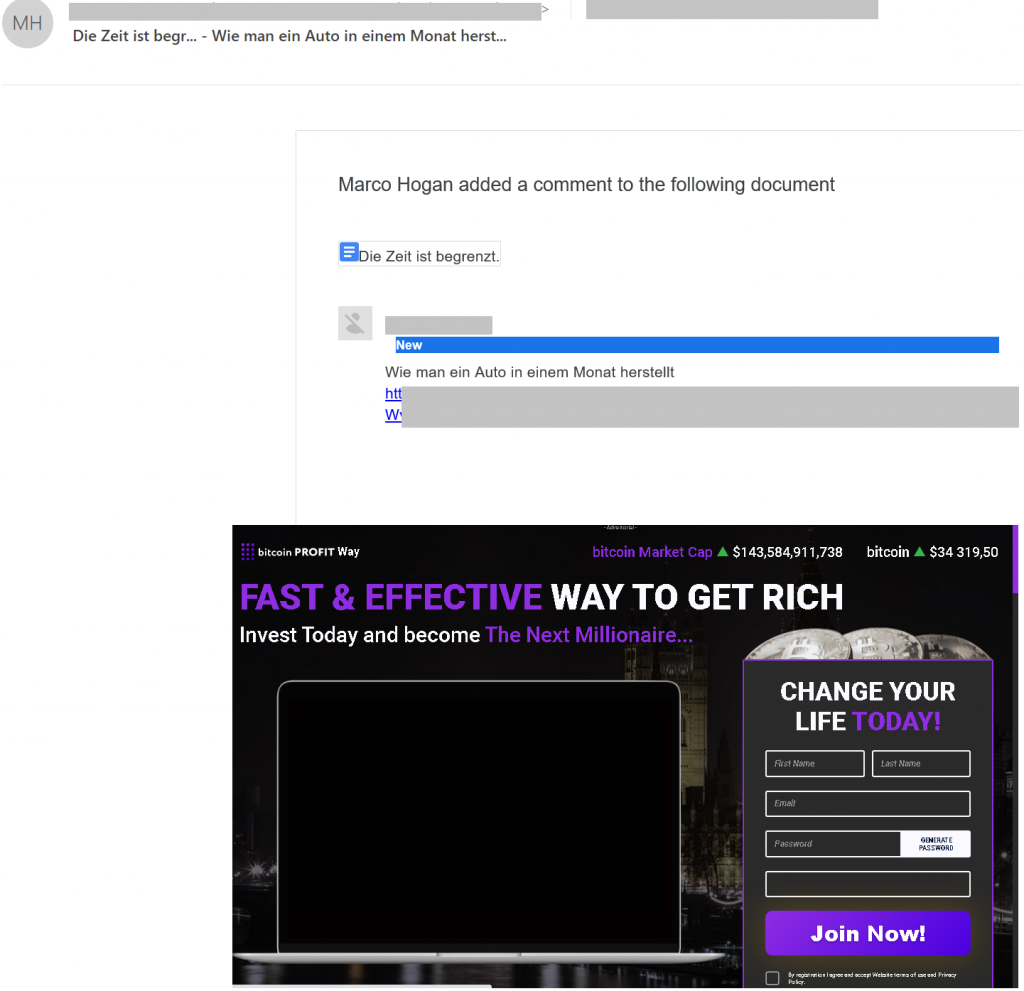
Cybercriminals also faked emails from cloud services in schemes aimed at stealing not accounts but money. We saw, for example, spoofed messages about a comment added to a document stored in the cloud. The document itself most likely did not exist: at the other end of the link was the usual recipe for making a fast buck online by investing in Bitcoin or a similarly tempting offer. Such “offers” usually require the victim to pay a small amount upfront to claim their non-existent reward.
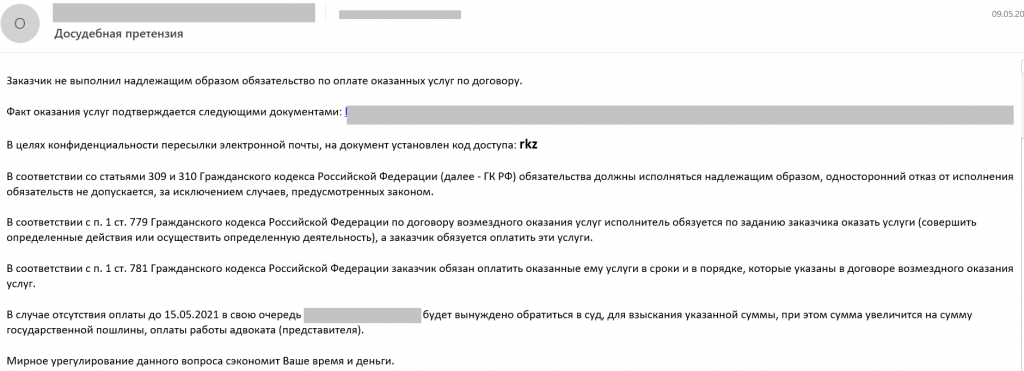
In addition to various cloud-related emails, we blocked messages disguised as business correspondence and containing links to malware. In particular, an email threatening legal action claimed that the victim had not paid for a completed order. To resolve the issue amicably, the recipient was asked to review the documents confirming the order completion and to settle the bill by a certain date. The documents were supposedly available via the link provided and protected by a special code. In fact, the file named “Договор №8883987726 от 10.10.2021.pdf.exe” (Agreement #8883987726 of 10.10.2021.pdf.exe) that the victim was asked to download was a malicious program known as Backdoor.Win32.RWS.a.
COVID-19 compensation fraud
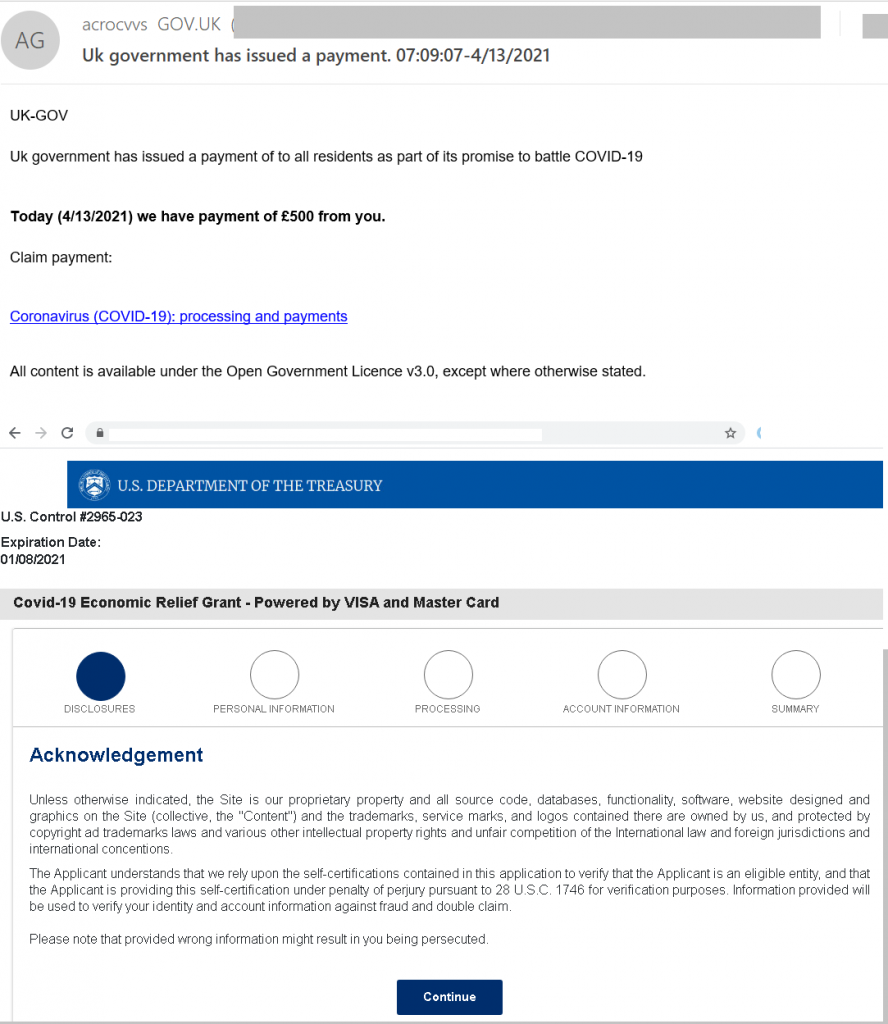
In Q2 2021, scammers continued to exploit the theme of pandemic-related compensation. This time, offers of financial assistance were mostly sent in the name of government agencies. “The UK Government” and “the US Department of the Treasury” were ready to pay out special grants to all-comers. However, attempts to claim the promised handout only led to monetary loss or compromised bank card details. It goes without saying that the grants did not materialize.
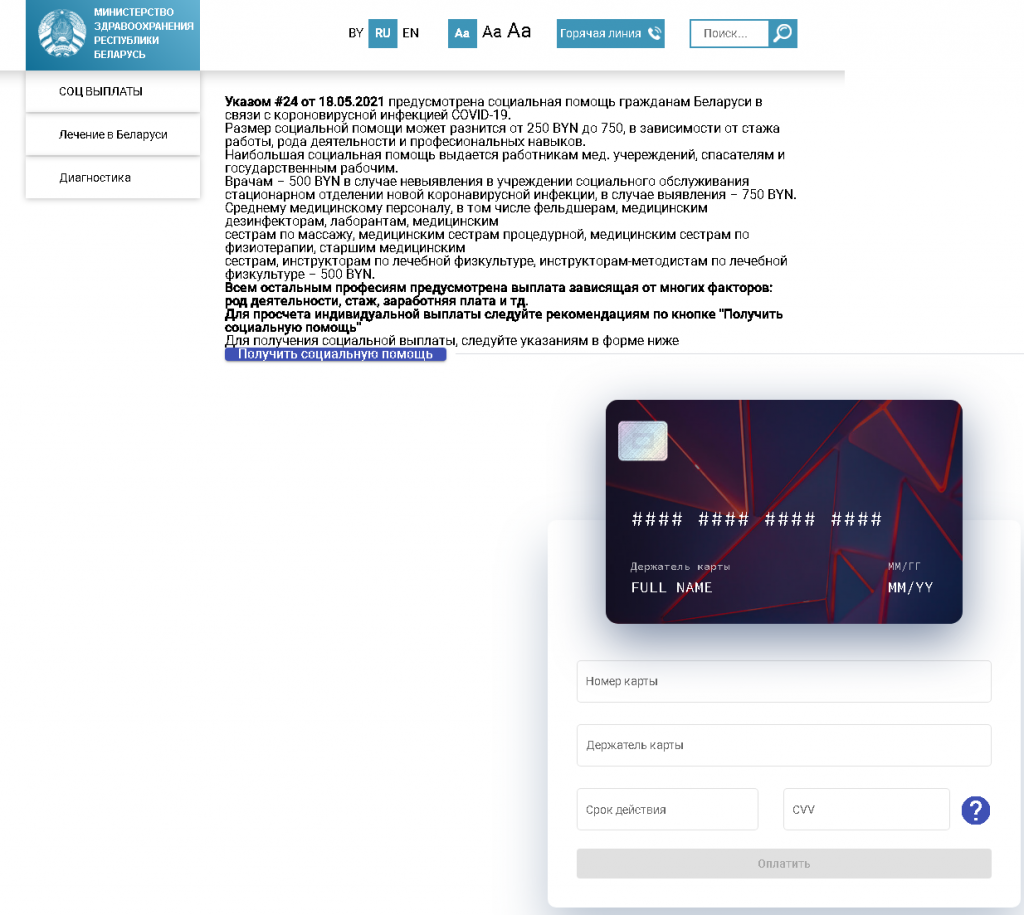
It was bank card details, including CVV codes, that were the target of a gang of cybercriminals who created a fake informational website about social assistance for citizens of Belarus. To make the pages look official, the scammers described in detail the system of payouts depending on the applicant’s line of work and other conditions. The information bulletin issued in the name of the Belarus Ministry of Health clearly spelled out the payment amounts for medical staff. Workers in other fields were invited to calculate their entitled payout by clicking the Get Social Assistance button. This redirected the visitor to a page with a form for entering bank card details.
Parcel scam: buy one, get none
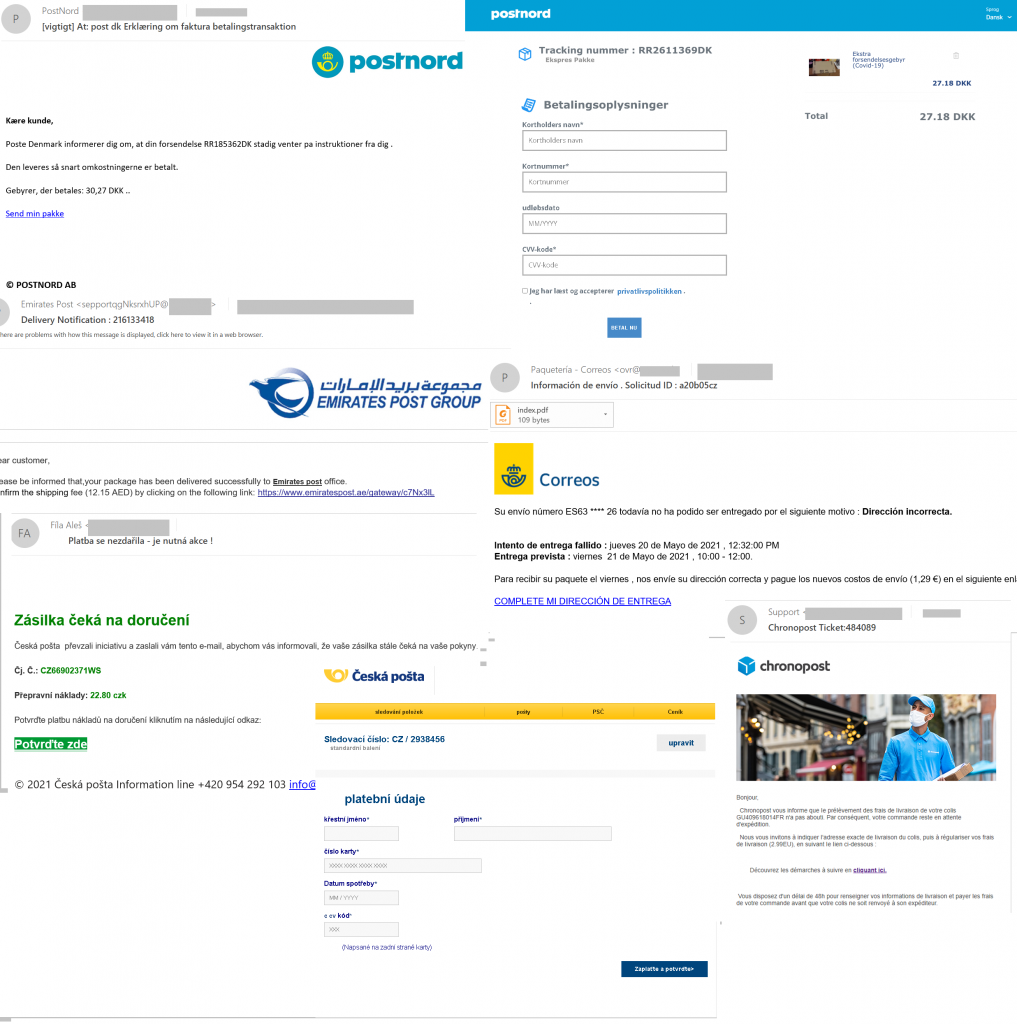
Unexpected parcels requiring payment by the recipient remained one of the most common tricks this past quarter. Moreover, cybercriminals became more adept at localizing their notifications: Q2 saw a surge in mass mailings in a range of languages. The reason for the invoice from the “mail company” could be anything from customs duties to shipment costs. When trying to pay for the service, as with compensation fraud, victims were taken to a fake website, where they risked not only losing the amount itself (which could be far higher than specified in the email), but also spilling their bank card details.
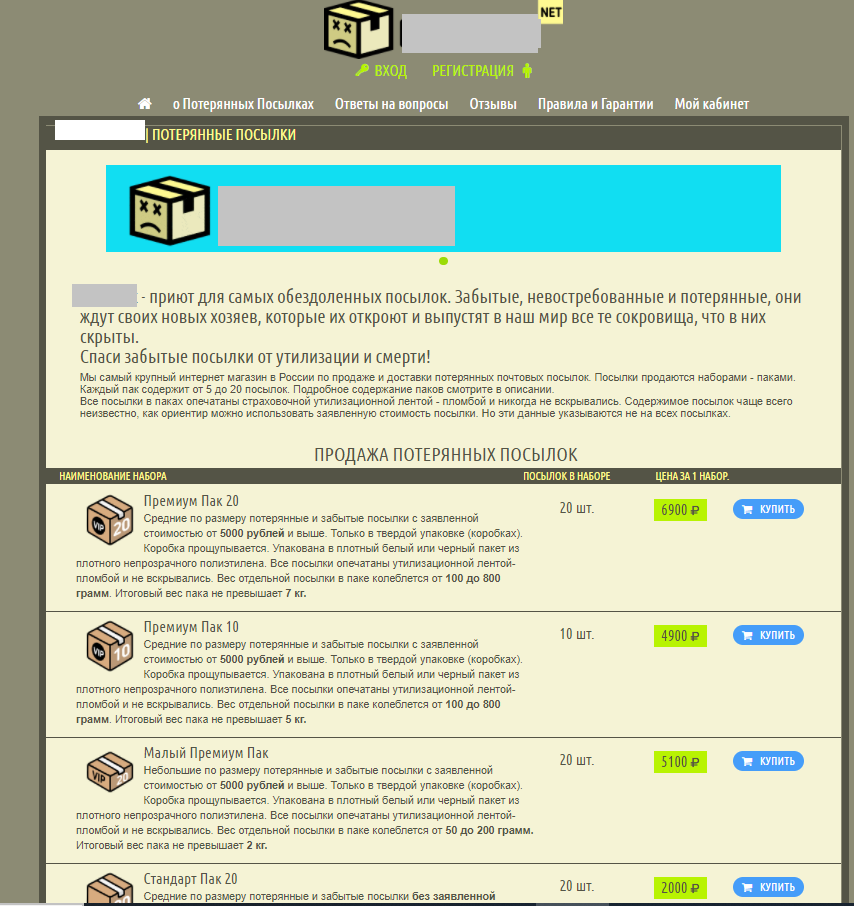
Mailed items were the focus of one other fraudulent scheme. Websites appeared offering people the chance to buy out others’ parcels that for some reason could not reach the intended recipients. The “service” was positioned as a lottery — the buyer paid only for the weight of the parcel (the bigger it was, the higher the price), and its contents were not disclosed. To find out what was inside, the lucky owner of the abandoned parcel had to wait for it to arrive at the specified address. Which it didn’t. According to the mail company Russian Post, when the storage period expires, registered items (parcels, letters, postcards, EMS items) are sent to the return address at the sender’s expense. If the sender does not collect the returned item within the storage period, it is considered “unclaimed” and stored for a further six months, after which it is destroyed. In other words, ownerless parcels are not sold. Therefore, any offer to buy them is evidently a scam.
New movies: pay for the pleasure of not watching
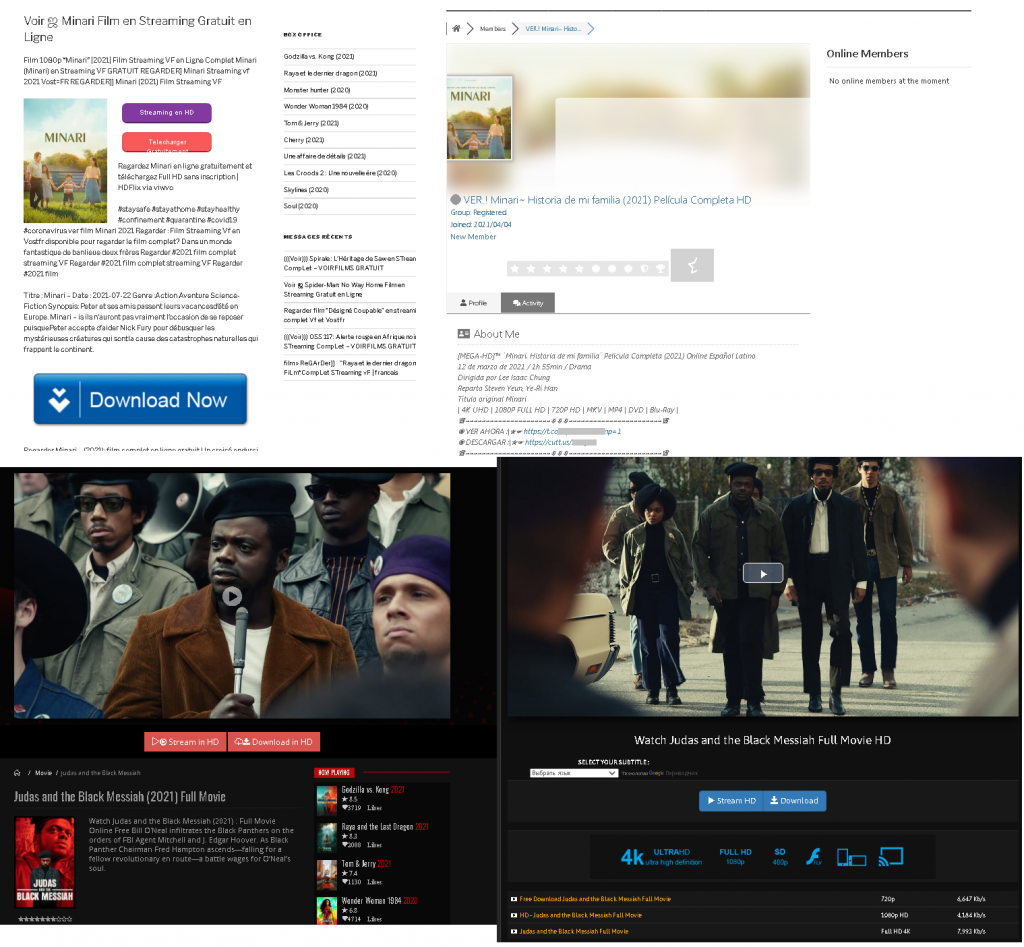
Late April saw the annual Oscars ceremony in Hollywood. Movies nominated for an Academy award naturally attract public as well as cybercriminal attention. As a consequence, fake websites popped up offering free viewings and even downloads of Oscar contenders. After launching a video, the visitor of the illegal movie theater was shown several clips of the film (usually taken from the official trailer), before being asked to pay a small subscription fee to continue watching. However, after payment of the “subscription” the movie screening did not resume; instead the attackers had a new bank account to play with.
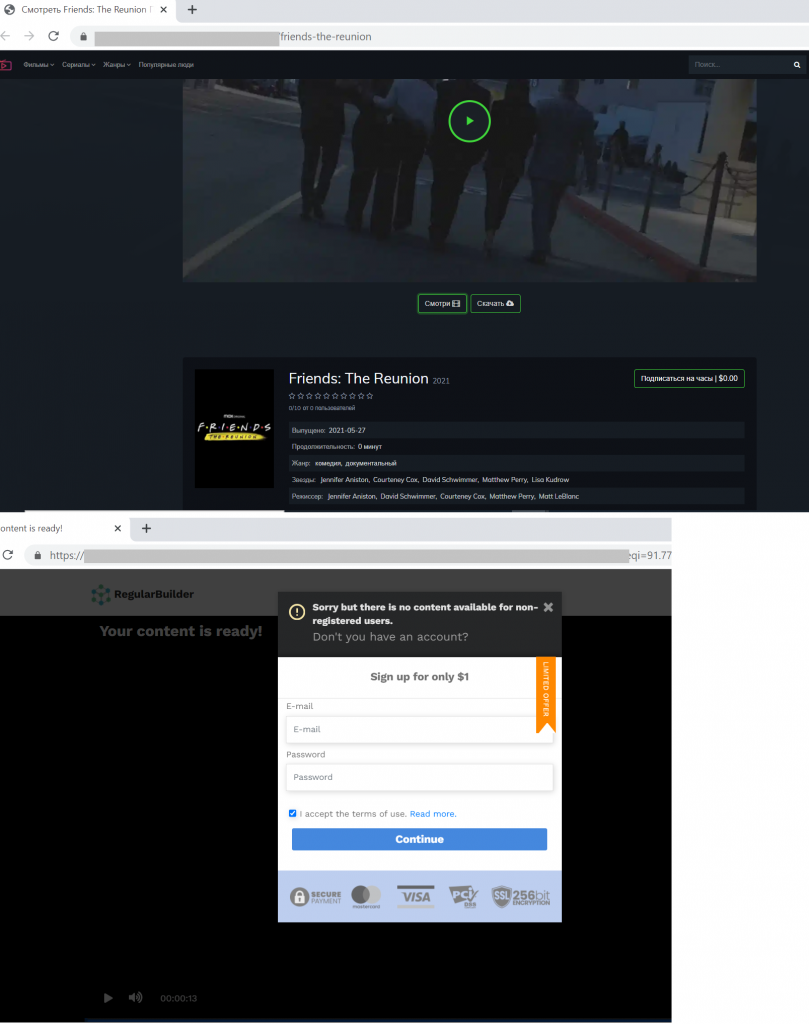
In fact, almost any big-budget movie is accompanied by the appearance of fake websites offering video or audio content long before its official release. Kaspersky found fake sites supposedly hosting Friends: The Reunion, a special episode of the popular sitcom. Fans who tried to watch or download the long-awaited continuation were redirected to a Columbia Pictures splash screen. After a few seconds, the broadcast stopped, replaced by a request to pay a nominal fee.
Messenger spam: WhatsApp with that?
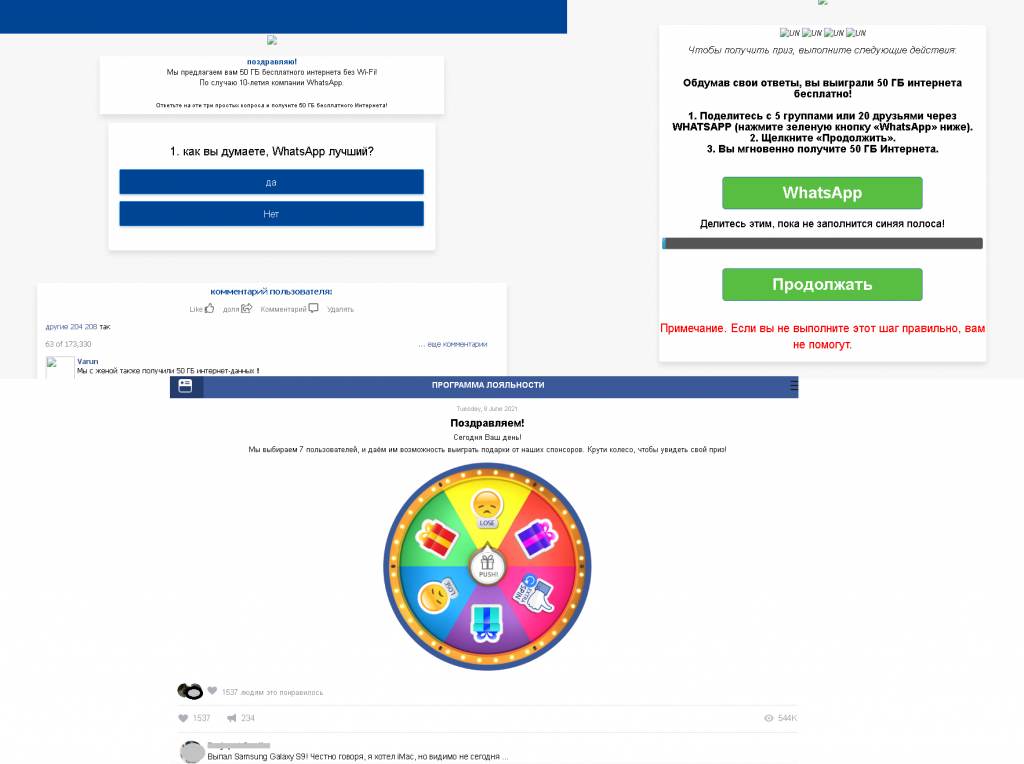
In messenger-based spam, we continued to observe common tricks to get users to part with a small amount of money. Victims were asked, for example, to take a short survey about WhatsApp and to send messages to several contacts in order to receive a prize. Another traditional scam aims to persuade the user that they are the lucky winner of a tidy sum. Both scenarios end the same way: the scammers promise a large payout, but only after receiving a small commission.
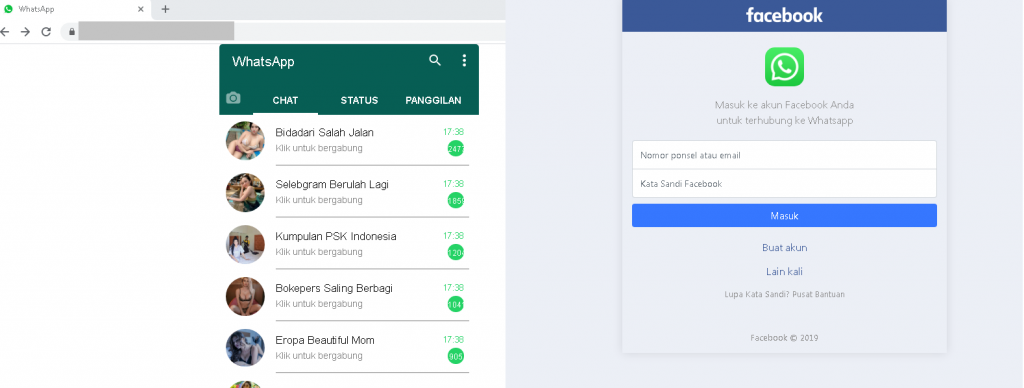
WhatsApp was bought by Facebook in 2014. In early 2021, the two companies’ symbiotic relationship became a hot topic in connection with WhatsApp’s new privacy policy, allowing the messenger to exchange user information with its parent company. Cybercriminals took advantage of the rumor mill about the two companies. They set up fake websites inviting users to a WhatsApp chat with “beautiful strangers”. But when attempting to enter the chat room, the potential victim landed on a fake Facebook login page.
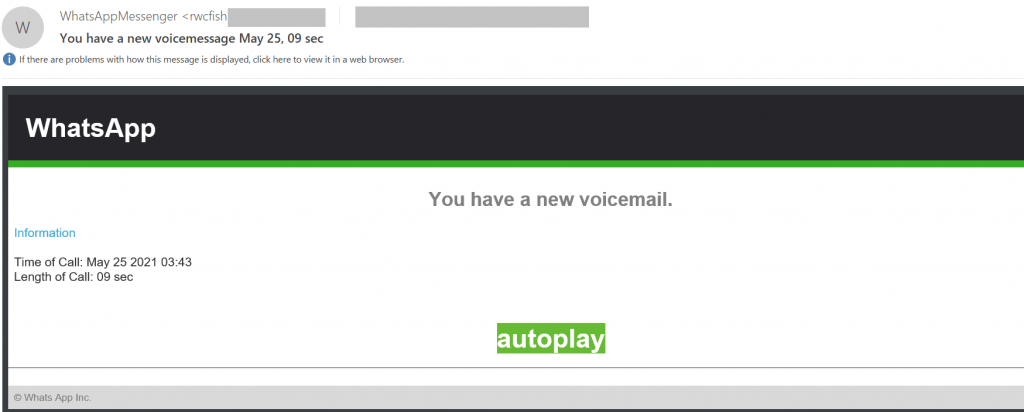
Emails with a link pointing to a fake WhatsApp voice message most likely belong to the same category. By following it, the recipient risks not only handing over their personal data to the attackers, but also downloading malware to their computer or phone.
Investments and public property scams
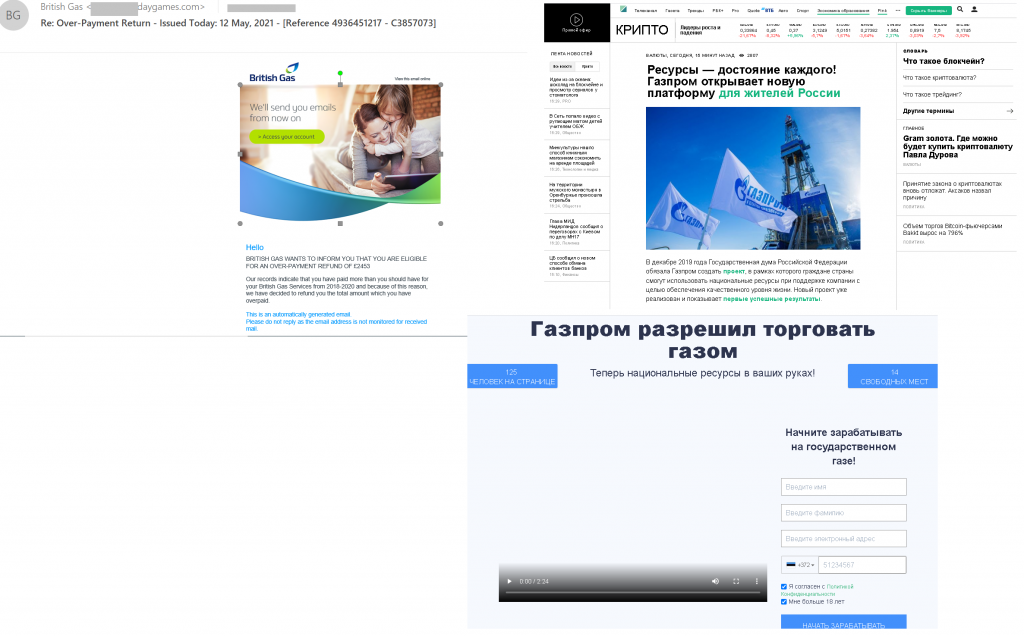
Offers of quick earnings with minimal effort remain one of the most common types of fraud. In Q2 2021, cybercriminals diversified their easy-money schemes. Email recipients were invited to invest in natural resources (oil, gas, etc.) or cryptocurrency secured by these resources. The topic of gas surfaced also in more conventional compensation scams. To make their offers more credible, cybercriminals used the brands of large companies. Having accepted investments, the scammers and their sites quickly disappeared along with the victims’ money.
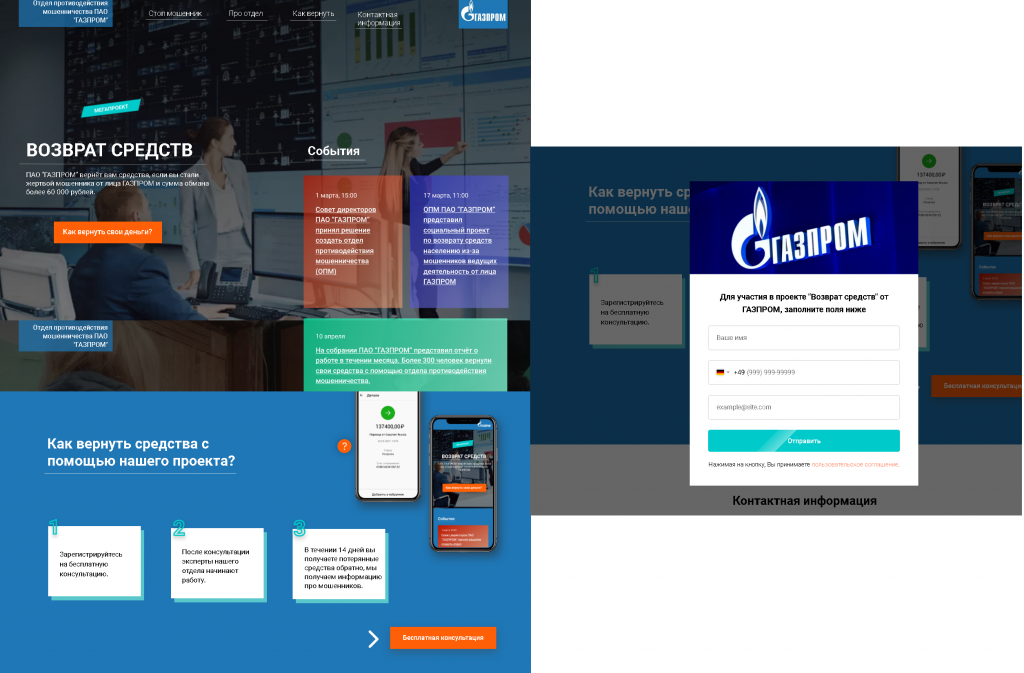
For more suspicious minds, the cybercriminals set up a fake Gazprom anti-fraud website, where they posed as company employees, promising to compensate victims’ losses. The cybercriminals claimed that those who had paid more than 60,000 rubles were entitled to compensation; however, the attacks were not targeted. Most likely, the scammers were counting on users being curious about whether they could claim compensation. Naturally, the help of the “anti-fraudsters” was not without strings attached, despite the advertised free consultation. “Clients” who filled out the form were asked to pay a small fee for the refund, whereupon the “consultants” vanished without compensating so much as a dime.
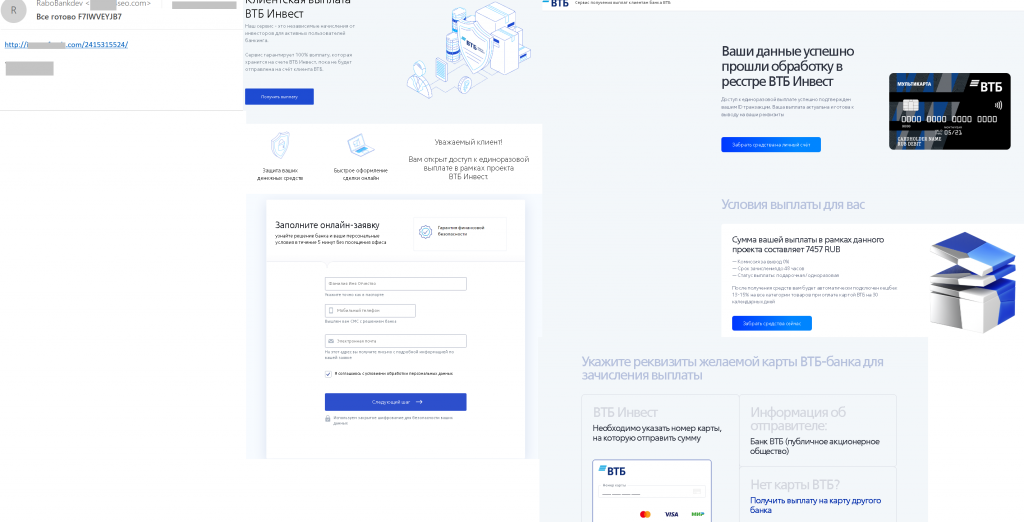
Another high-earning scam cited client payouts under VTB Invest, VTB Bank’s digital asset management solution. Using the bank’s logos, the fraudsters offered “active banking users” the opportunity to receive “payout from investors.” After filling out the application form, indicating name, phone number and email, the potential victim saw a message stating that they are to receive a certain amount of money. Although the cybercriminals assured that no commission was payable, to receive the “payout” the applicant was required to provide bank card details or deposit a small sum, ostensibly to verify the account. In other words, it was the usual scheme in a different wrapper.
Statistics: spam
Proportion of spam in mail traffic
After a prolonged decline, the share of spam in global mail traffic began to grow again in Q2 2021, averaging 46.56%, up 0.89 p.p. against the previous reporting period.
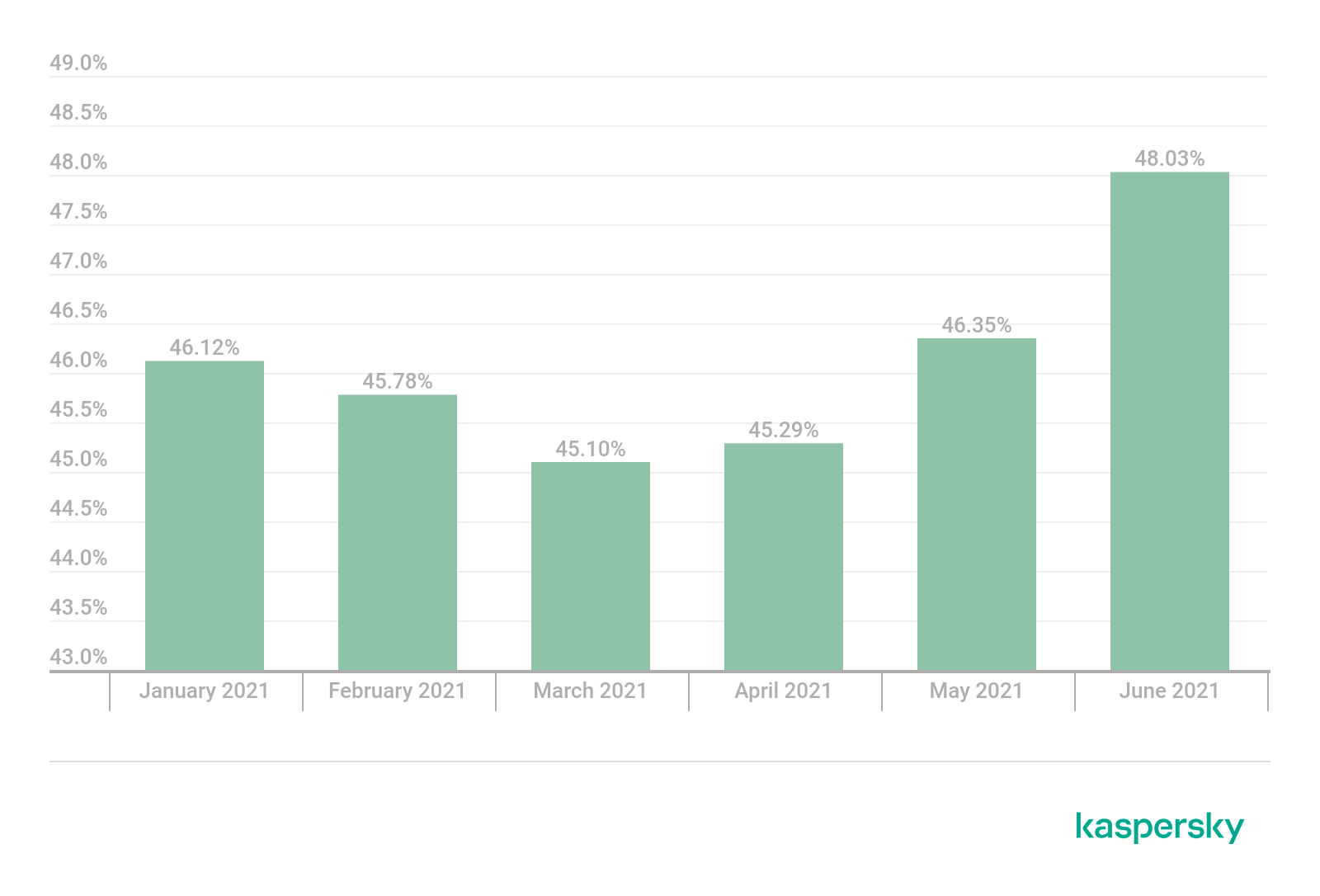
Share of spam in global mail traffic, Q1 and Q2 2021 (download)
Source of spam by country
The TOP 10 spam-source countries remained virtually unchanged from the first quarter. Russia (26.07%) is still in first place, its share having increased by 3.6 p.p., followed by Germany (13.97%) and the US (11.24%), whose contribution to the global flow of spam decreased slightly. China (7.78%) remains in fourth position.

Source of spam by country, Q2 2021 (download)
Malicious mail attachments
Mail Anti-Virus blocked 34,224,215 malicious attachments in Q2, almost 4 million fewer than in the first three months of 2021.

Number of Mail Anti-Virus triggerings, Q1 and Q2 2021 (download)
Malware families
In Q2, Trojans from the Badun family (7.09%) were the most common malicious attachments in spam, with their share increased by 1.3 p.p. These malicious programs, disguised as electronic documents, are often distributed in archives. In contrast, Agesla Trojans (6.65%), which specialize in stealing credentials, shed 2.26 p.p. and dropped to second place. The Taskun family (4.25%), which exploits Windows Task Scheduler, rounds out the TOP 3. These Trojans, like Badun, are gaining popularity.
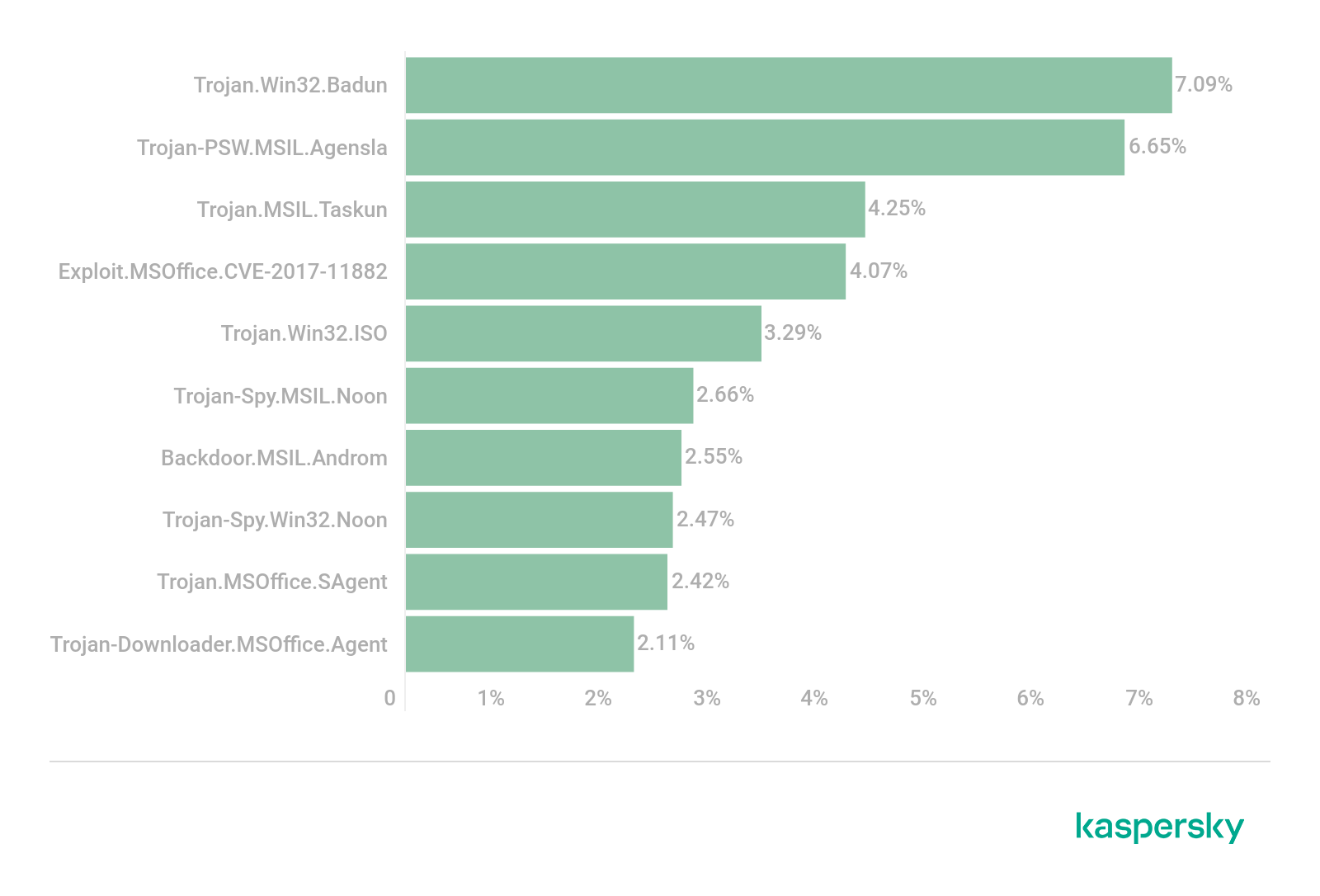
TOP 10 malware families in mail traffic, Q2 2021 (download)

TOP 10 malicious attachments, Q2 2021 (download)
Countries targeted by malicious mailings
More than anywhere else, Kaspersky solutions blocked malicious attachments on user devices in Spain (9.28%). The share of this country grew slightly against Q1 2021, adding 0.54 p.p. Second place was retained by Italy (6.38%), despite losing 1.21 p.p. Germany (5.26%) and Russia (5.82%) swapped places in Q2, while the UAE (5.36%) remained fourth, its share practically unchanged.

Countries targeted by malicious spam, Q2 2021 (download)
Statistics: phishing
In phishing terms, Q2 2021 was fairly uneventful. The Anti-Phishing system detected and blocked 50,398,193 attempted redirects, with only 3.87% of our users encountering such phishing links.
Geography of phishing attacks
Looking at the share of users by country on whose devices the Anti-Phishing system was triggered, we see that Brazil (6.67%), which lost first place last quarter, is back at the top. It didn’t get far ahead from Israel (6.55%) and France (6.46%), which topped the Q1 list.
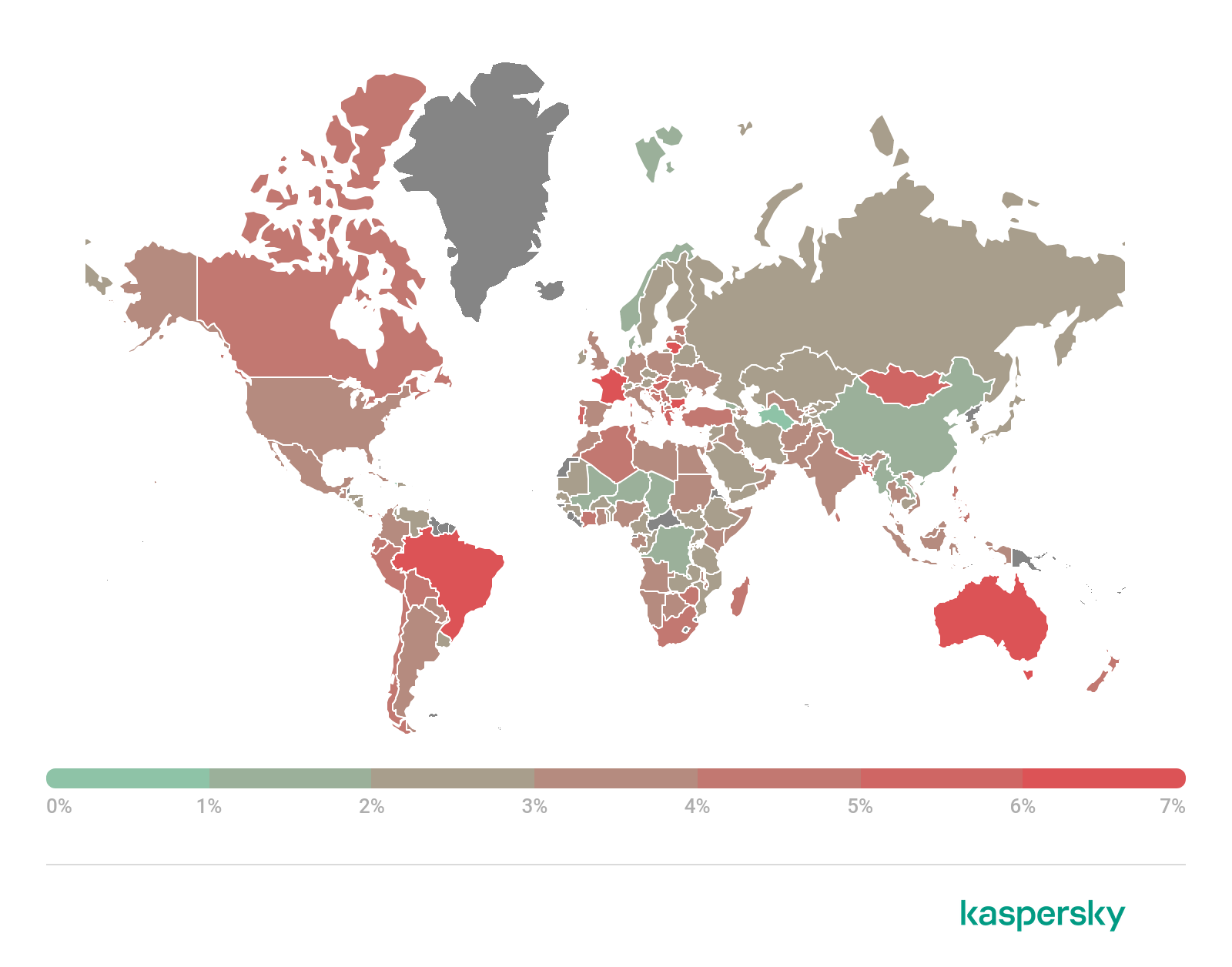
Geography of phishing attacks, Q2 2021 (download)
Top-level domains
The traditional leader among top-level domain zones used by cybercriminals to post phishing pages is COM (31.67%). The ORG domain (8.79%) moved up to second place, pushing XYZ (8.51%) into third.
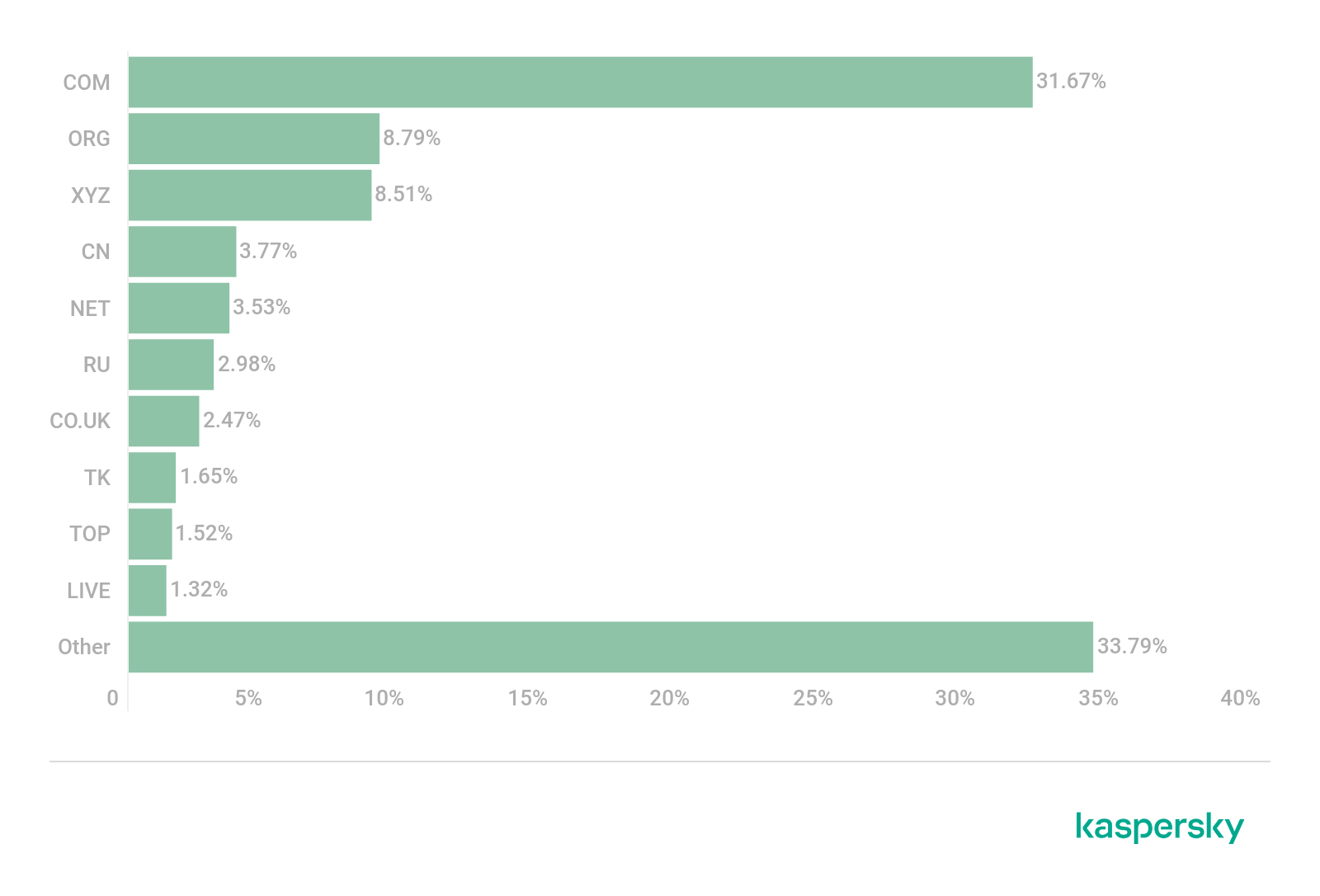
Top-level domain zones most commonly used for phishing, Q2 2021 (download)
Organizations under attack
The rating of organizations targeted by phishers is based on the triggering of the deterministic component in the Anti-Phishing system on user computers. The component detects all pages with phishing content that the user has tried to open by following a link in an email message or on the web, as long as links to these pages are present in the Kaspersky database.
For the first time since the start of the pandemic, online stores (19.54%) vacated the first line in the ranking of organizations most often used by cybercriminals as bait. Global internet portals (20.85%) stepped in as this quarter’s leader. Moreover, the share of both categories increased relative to Q1: by 3.77 and 5.35 p.p., respectively. Third place belongs to banks (13.82%), which gained 3.78 p.p. in Q2.

Distribution of organizations whose users were targeted by phishers, by category, Q2 2021 (download)
Conclusion
In Q2, as we expected, cybercriminals continued to hunt for corporate account credentials and exploit the COVID-19 theme. A curious takeaway was the spike in investment-related activity. On the whole, however, the quarter did not deliver any surprises.
As for Q3 forecasts, the share of cyberattacks on the corporate sector is likely to stay the same. This is because remote working has established a firm foothold in the labor market. Also, the COVID-19 topic is unlikely to disappear from spam. And if the current crop of vaccination and compensation scams weren’t enough, fraudsters could start utilizing newly identified strains of the virus to add variety and nowness to their schemes. What’s more, during the vacation season, pandemic or not, we expect an increase in demand for intercity and international travel; as a result, the risk of encountering fake websites when buying tickets or booking accommodation will rise. Lastly, we will likely see waves of tourist-targeted attacks during major sporting occasions, such as the Olympic Games in Japan. Such events are always accompanied by thematic spam.


















Spam and phishing in Q2 2021