
Quarterly highlights
Targeted attacks
The second quarter often saw phishers resort to targeted attacks, especially against fairly small companies. To attract attention, scammers imitated email messages and websites of companies whose products or services their potential victims could be using.
The scammers did not try to make any of the website elements appear credible as they created the fake. The login form is the only exception. One of the phishing websites we discovered even used a real captcha on that form.
The main pretext that scammers use to prompt the target to enter their information is offering an online catalog that purportedly only becomes available once the target provides the login and password to their email account.
In one instance, phishers used Microsoft Sway, the service for creating and sharing presentations, to hunt for logins and passwords for corporate accounts. The user was offered to view presentations belonging to another company in the same industry by following a link and entering the login and password for their work email account.
A fake website can be recognized by its design. The workmanship is often rough, and the chunks of information on the various pages are disjointed due to being pulled from diverse sources. Besides, pages like that are created on free hosting websites, as cybercriminals are not prepared to invest too much money in the fakes.
A targeted phishing attack may lead to serious consequences: after gaining access to an employee’s mailbox, cybercriminals can use it for further attacks on the company itself, or its employees or partners.
Waiting for your package: keeping your data secure and your computer, clean
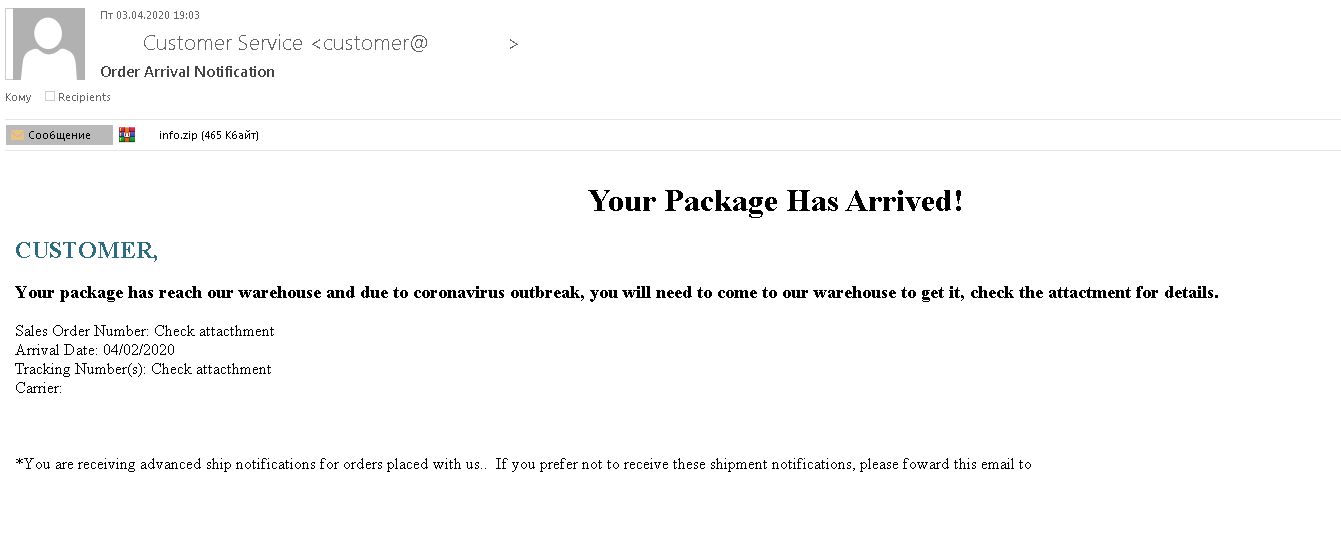
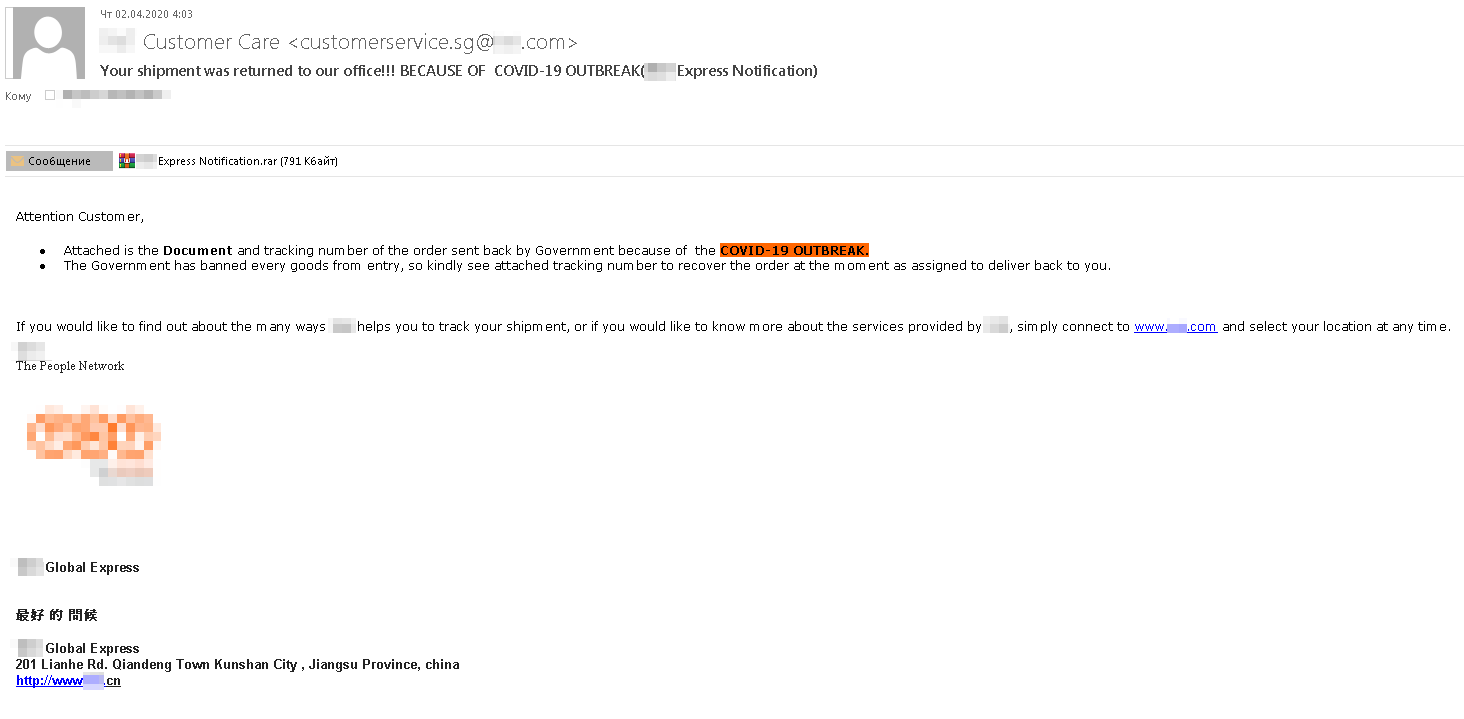
As the pandemic reached its peak, mail service between countries became complicated and delivery times noticeably increased. Organizations responsible for delivery of letters and parcels rushed to notify recipients about all kinds of possible delays and hiccups. This is exactly the type of email messages that scammers started to imitate: the target was offered to open the attachment to find out the address of the warehouse with the package that had failed to reach them.
Another, relatively original, trick employed by cybercriminals was a message containing a miniature image of a postal receipt. The scammers expected the curious recipient to take the attachment, which was an ACE archive despite its name containing “jpg”, for the real thing and open it. The mailshots we detected used this as a method of spreading the Noon spyware. The scam can only be detected if the email client displays the full names of attachments.
In another fraudulent scheme, the target was to told that their order could not be dispatched due to a restriction on mailing of certain types of goods, but the processing of the package would be resumed once the restrictions were lifted. All required documents and a new tracking number could purportedly be found in the attached archive. In reality, the attachment contained a copy of the Androm backdoor, which opened remote access to the victim’s computer.
Scammers posing as courier service employees sent out email warning that packages could not be delivered due to failure to pay for the shipping. The “couriers” accepted codes for prepaid cards issued by Paysafecard as payment. These cards range from €10 to €100 and can be used in stores that accept this payment method. The victim was offered to email a €50 card code – incidentally, an activity that the payment system’s rules explicitly forbid. The cybercriminals chose this payment method for a reason: blocking or revoking a Paysafecard payment is next to impossible.
Banking phishing amid a pandemic
Banking phishing attacks in the second quarter of the year often employed emails that offered borrowers various pandemic-related discounts and bonuses. Accessing the benefits involved downloading a file with a manual or following a link. As a result, the scammers could access the user’s computer, personal data or credentials for various services, depending on the scheme.
The COVID-19 theme was present, too, in the widely known fake bank emails informing customers that their accounts had been blocked, and that they needed to enter their login and password on a special page to get back their access.
The pandemic saw the revival of a more-than-a-decade-old scheme, in which scammers sent victims emails offering to open the attachment to get the details of a low-rate loan. This time, the rate reduction was linked to the pandemic.
Taxes and exemptions
The beginning of the second quarter is the time for submitting tax forms in many countries. This year, tax authorities in some countries reduced the tax burden or exempted citizens from paying taxes. Scammers naturally grabbed the opportunity: mailshots we detected reported that the government had approved a compensation payout, and claiming it involved following a link to the tax agency’s website, which, unsurprisingly, proved to be fake. Some of the email messages were not too well crafted, and looking closely at the From field was all it took to detect a fake.
More ingenious scammers made up a whole legend: in an email presented as being from the IRS (United States Internal Revenue Service), they said there was a $500,000 “pandemic payment”, authorized jointly by the UN and the World Bank, that could be transferred to the recipient if it had not been for a woman named Annie Morton. The lady, the email said, had showed up at an IRS office carrying a warrant for the payment. She purportedly said that the intended recipient had succumbed to COVID-19, and she was the one to receive the $500,000. The message insisted that the victim contact a certain IRS employee – and not any other, so as to avoid a mistake – to prove that they were alive.
Subsequent steps would most likely be identical to the well-known inheritance scam, where the victim would be offered to pay for the services of a lawyer, who would then disappear with the advance money. One might guess that instead of the advance, the scammers would ask for a fee for executing papers that would prove the victim was still alive.
Getting refunded and losing it all
Tax refunds are not the only type of aid that states have been providing to individuals and companies distressed by the pandemic. And not the only type the scammers have been using. Thus, Brazilians were “allowed” not to pay their energy bills, and all they had to do was register on a website by following a link in an “email from the government”. The hyperlink had an appearance designed to trick the user into thinking that they were being redirected to a government portal, whereas in reality, the victim had a trojan installed on their computer, which downloaded and then ran another trojan, Sneaky.
Personal information leak is another hazard faced by those who risk registering for “compensation” on a suspicious website. For example, one mailshot offered individuals aged over seventy to go to a website and fill out a form, which contained fields for the last name, first name, gender, mailing address and SSN (social security number, for US citizens).
Identifying a fake email is easy. One just needs to take a closer look at the From field and the subject, which appears odd for an official email.
Once the target filled out the entire form, they were redirected to the official Web page of the World Health Organization’s COVID-19 Solidarity Response Fund, a real organization, to give a donation. This helped the scammers to create an illusion that the questionnaire was official and to build a vast database containing the details of individuals over seventy years of age.
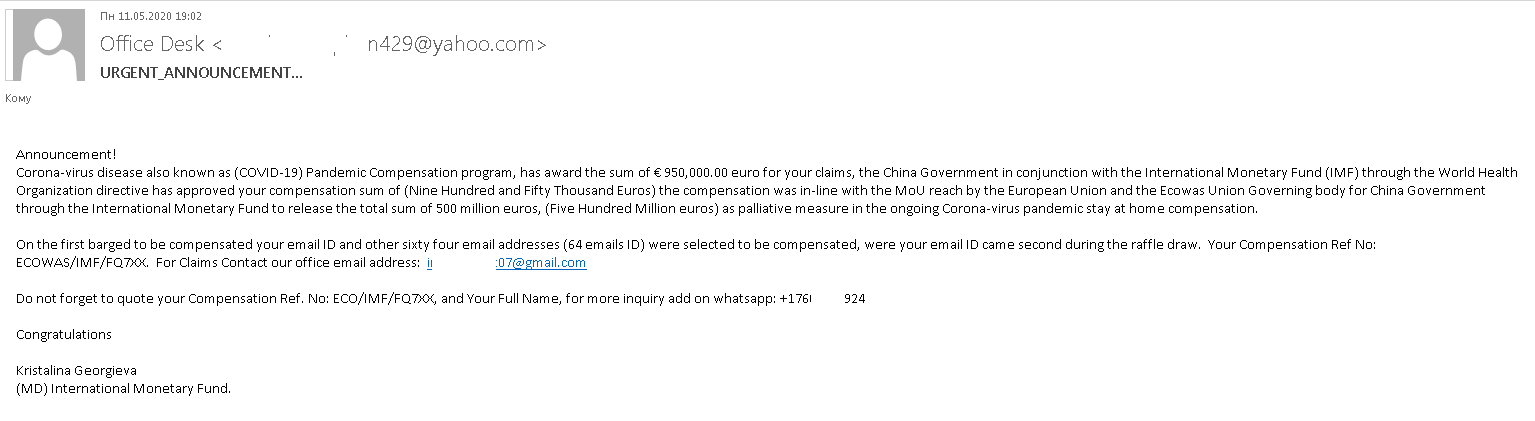
Fake emails promising government compensations carried one more threat: instead of getting paid, the victim risked losing their own money to the cybercriminals. Thus, a fake email from the International Monetary Fund announced that the recipient and sixty-four other “lucky” individuals had been selected to receive compensations from a five-hundred-million-dollar fund set up by the IMF, China and the European Union for supporting victims of the pandemic. Getting €950,000 was a matter of contacting the IMF office at the address stated in the message. Subsequent events followed the lottery-scam script: getting the money required paying a commission first.
Fake HR: getting dismissed by professional spammers
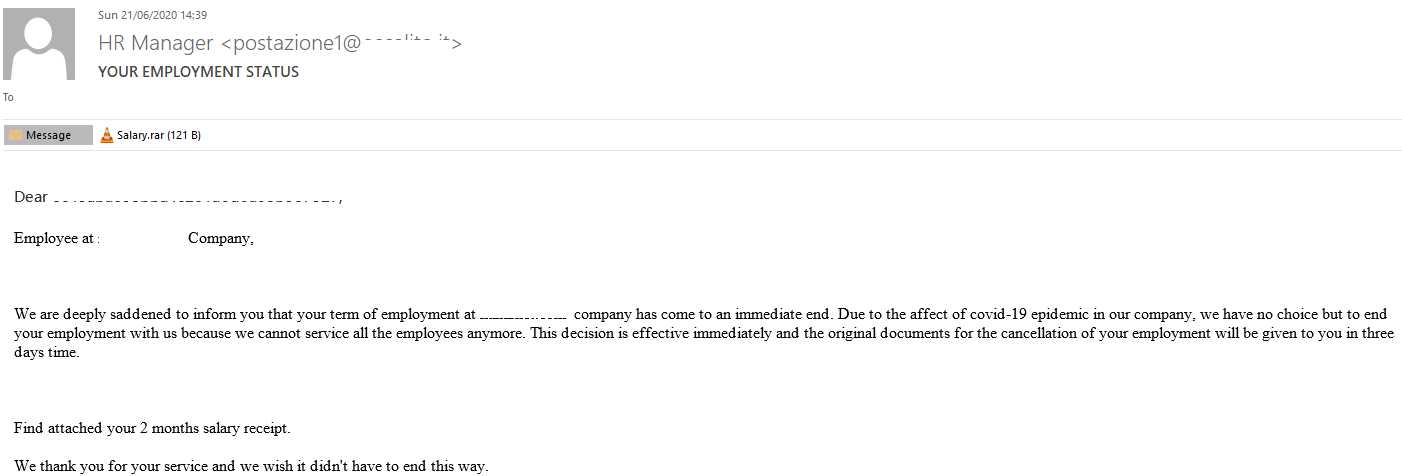
The pandemic-related economic downturns in several countries caused a surge in unemployment, an opportunity that cybercriminals were quick to take advantage of. One mailshot, sent in the name of the US Department of Labor, offered looking at the latest changes to the parental leave and sick leave laws. The sender said these laws had been amended following the adoption of the coronavirus relief act, and all details on the amendments were available in the attachment. What the attachment really contained was Trojan-Downloader.MSOffice.SLoad.gen, a trojan mostly used for downloading and installing ransomware.
Another way scammers “surprised” potential victims was dismissal notices. The employee was informed that the company had been forced to discharge them due to the pandemic-induced recession. The dismissal “followed the book”, in that the attachment, according to the author of the email, contained a request form for two months’ worth of pay. Needless to say, the victim only found malware attached.
Your data wanted, now
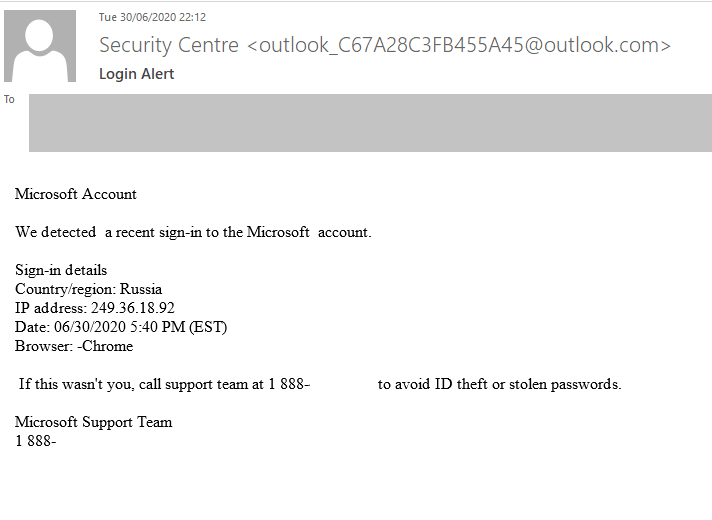
The share of voice phishing in email traffic rose noticeably at the end of Q2 2020. One mailshot warned of a suspicious attempt at logging in to the target’s Microsoft account, originating in another country, and recommended that the target contact support by phone at the supplied number. This spared the scammers the need to create a large number of fake pages, as they tried to get all the information they needed over the phone.
An even less conventional way of obtaining personal data could be found in emails that offered subscription to COVID-19 updates, where the target only needed to verify their email address. Besides personal data theft, forms like this can be used for collecting mailbox usage statistics.
Statistics: spam
Proportion of spam in email traffic
Proportion of spam in global email traffic, Q1 2020 – Q2 2020 (download)
In Q2 2020, the largest share of spam (51.45 percent) was recorded in April. The average percentage of spam in global email traffic was 50,18%, down by 4.43 percentage points from the previous reporting period.
Proportion of spam in Runet email traffic, Q1 2020 – Q2 2020 (download)
The Russian segment of the World Wide Web presents the opposite picture, with the end of the quarter accounting for the larger share of spam: spam peaked in June as it reached 51.23 percent. The quarterly average was 50.35 percent, 1.06 p.p. lower that the first quarter’s average.
Sources of spam by country
Countries where spam originated in Q2 2020 (download)
The composition of the top five Q1 2020 spam leaders remained unchanged in the second quarter. Russia kept the lead with 18.52 percent, followed by Germany with 11.94 percent, which had overtaken the US, now third with 10.65 percent. France (7.06 percent) and China (7.02 percent) remained fourth and fifth, respectively.
Sixth was the Netherlands (4.21 percent), closely followed by Brazil (2.91 percent), Turkey (2.89 percent), Spain (2.83 percent) and lastly, Japan (2.42 percent).
Spam email size
Spam email size, Q1 – Q2 2002 (download)
The share of extra small emails kept going down, dropping by 8.6 p.p. to 51.30 percent in Q2 2020. Emails between 5 KB and 10 KB decreased slightly (by 0.66 p.p.) compared to the previous quarter, to 4.90 percent. Meanwhile, the share of spam messages within the range of 10 KB to 20 KB rose by 4.73 p.p. to 11.09 percent. The share of larger messages between 100 KB and 200 KB in the second quarter fell by 1.99 p.p. to 2.51 percent compared to Q1 2020.
Malicious attachments: malware families
Number of Mail Anti-Virus triggerings, Q1 2020 – Q2 2020 (download)
Our security solutions detected a total of 43,028,445 malicious email attachments in Q2 2020, an increase of six and a half million year-on-year.
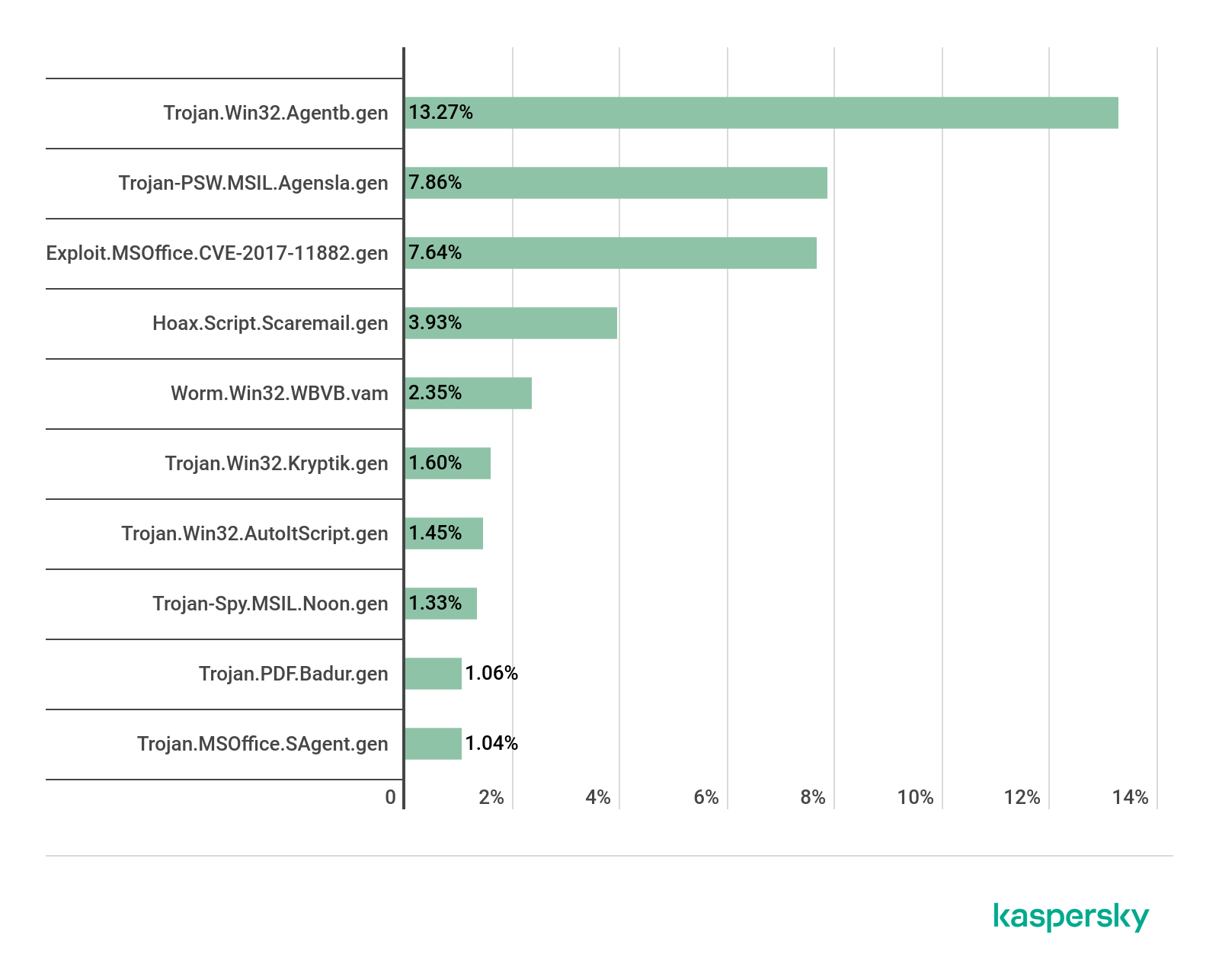
TOP 10 malicious attachments in mail traffic, Q2 2020 (download)
Trojan.Win32.Agentb.gen (13.27 percent) was the most widespread malware in email attachments in the second quarter of the year, followed by Trojan-PSW.MSIL.Agensla.gen (7.86 percent) in second place and Exploit.MSOffice.CVE-2017-11882.gen (7.64 percent) in third place.
TOP 10 malware families in mail traffic, Q2 2020 (download)
The most widespread malware family in the second quarter, as in the previous one, was Trojan.Win32.Agentb (13.33 percent), followed by Trojan-PSW.MSIL.Agensla (9.40 percent) and Exploit.MSOffice.CVE-2017-11882 (7.66 percent).
Countries targeted by malicious mailshots
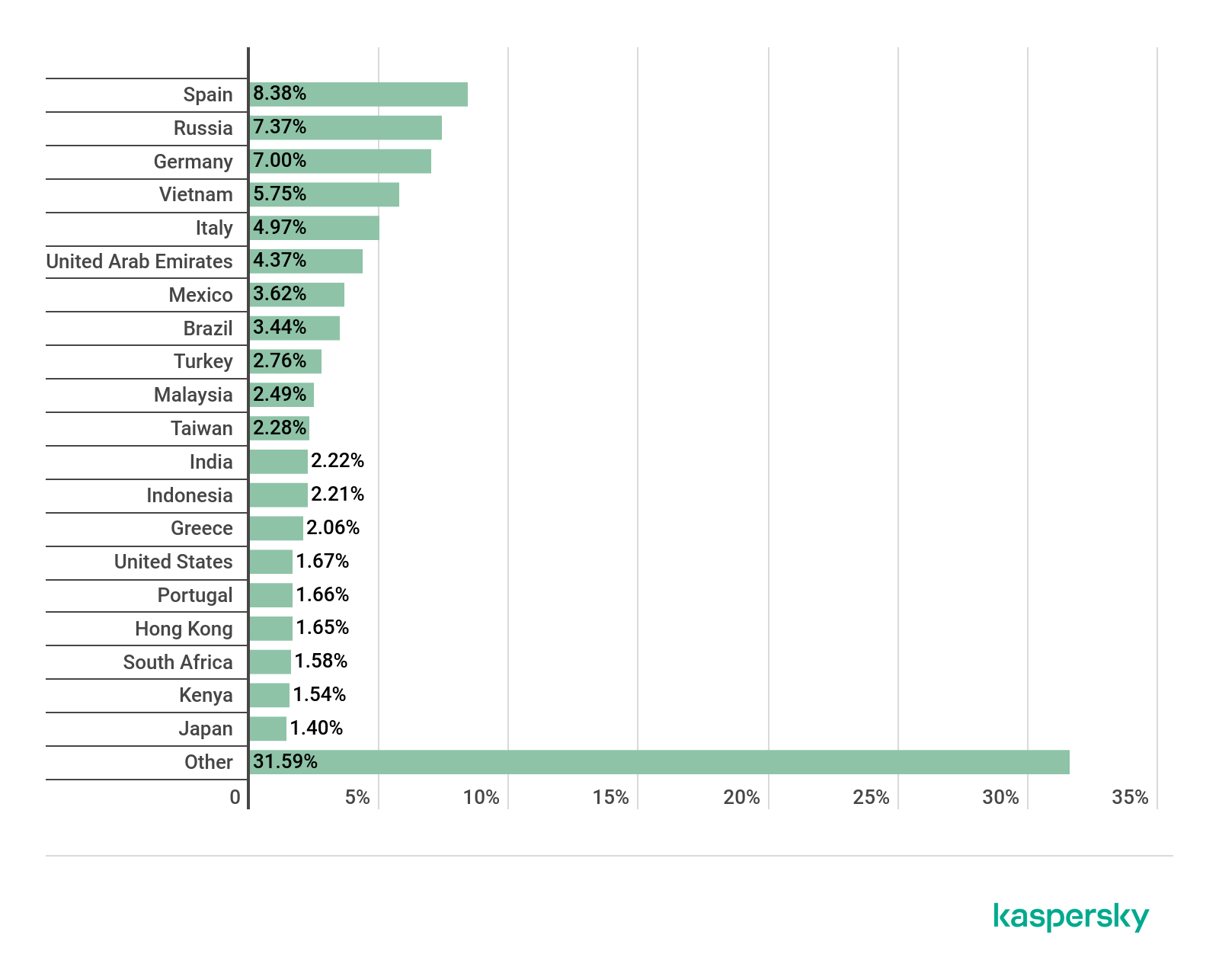
Distribution of Mail Anti-Virus triggerings by country, Q2 2020 (download)
Spain (8.38%) took the lead in Mail Anti-Virus triggerings in Q2 2020, just as in Q1 2020. Second came Russia with 7.37 percent of attacks, and third came Germany with 7.00 percent.
Statistics: phishing
Kaspersky Anti-Phishing helped to prevent 106,337,531 attempts at redirecting users to phishing Web pages in Q2 2020, a figure that is almost thirteen million lower than that for the first quarter. The share of unique attacked users accounted for 8.26 percent of the total Kaspersky users in the world, with 1,694,705 phishing wildcards added to the system database.
Attack geography
Venezuela was traditionally the country with the largest share of users attacked by phishers (17.56 percent).
Geography of phishing attacks, Q2 2020 (download)
Portugal was 4.05 p.p. behind with 13.51 percent, closely followed by Tunisia with 13.12 percent.
| Country | %* |
| Venezuela | 17.56% |
| Portugal | 13.51% |
| Tunisia | 13.12% |
| France | 13.08% |
| Brazil | 12.91% |
| Qatar | 11.94% |
| Bahrain | 11.88% |
| Guadeloupe | 11.73% |
| Belgium | 11.56% |
| Martinique | 11.34% |
*Share of users on whose computers Anti-Phishing was triggered out of all Kaspersky users in the country
Top-level domains
Starting with this quarter, we have decided to maintain statistics on top-level domains used in phishing attacks. Quite predictably, COM led by a huge margin, with 43.56 percent of the total number of top-level domain names employed in attacks. It was followed by NET (3.96 percent) and TOP (3.26 percent). The Russia-specific RU domain took fourth place with 2.91 percent, followed by ORG with 2.55 percent.
Top-level domains most popular with phishers, Q2 2020 (download)
Organizations under attack
The rating of attacks by phishers on different categories of organizations is based on detections by Kaspersky Anti-Phishing component. This component detects pages with phishing content that the user tried to access by following email or Web links, regardless of how the user got to the page: by clicking a link in a phishing email or in a message on a social network, or after being redirected by a malicious program. When the component is triggered, a banner is displayed in the browser warning the user about a potential threat.
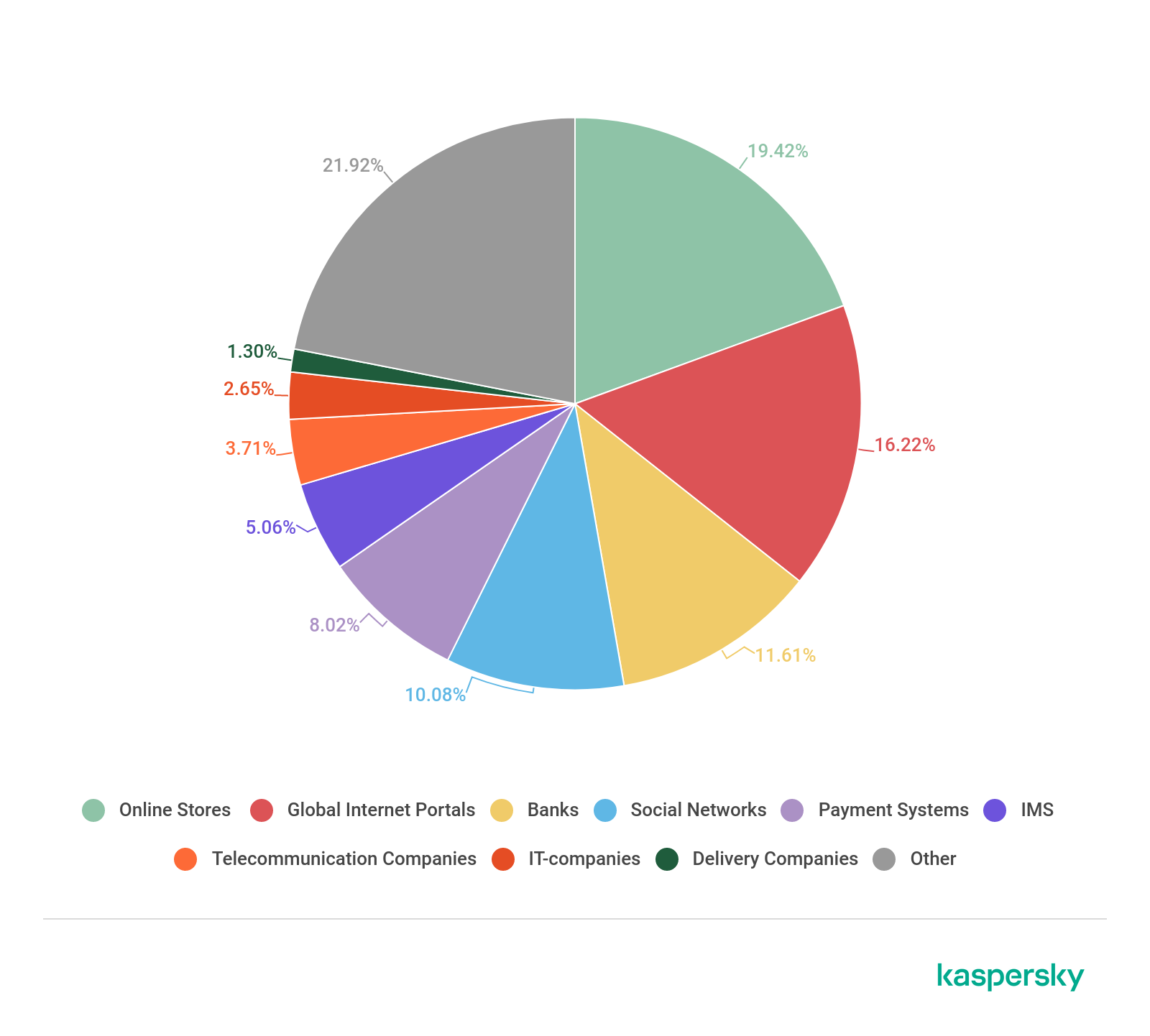
As in the first quarter, the Online Stores category accounted for the largest share of phishing attacks, its share increasing by 1.3 p.p. to 19.42 percent. Global Web Portals again received the second-largest share of attacks, virtually unchanged at 16.22 percent. Banks (11.61 percent) returned to third place, pushing Social Networks (10.08 percent) to fourth place.
Distribution of organizations subjected to phishing attacks by category, Q2 2020 (download)
Conclusion
In our summary of the first quarter, we hypothesized that COVID-19 would remain spammers’ and fishers’ key theme in the future. That is exactly what happened: seldom did a mailshot fail to mention the pandemic as phishers added relevance to their tried and tested schemes and came up with brand-new ones.
The average share of spam in global email traffic in Q2 2020 dropped by 4.43 p.p. to 50.18 percent compared to the previous reporting period, and attempts to access phishing pages amounted to 106 million.
First place in the list of spam sources in Q2 went to Russia with a share of 18.52 percent. Our security solutions blocked a total of 43,028,445 malicious email attachments, with the most widespread “email-specific” malware family being Trojan.Win32.Agentb.gen, which infected 13.33 percent of the total email traffic.











































Spam and phishing in Q2 2020