
Cyberattackers often view small and medium-sized businesses (SMBs) as easier targets, assuming their security measures are less robust than those of larger enterprises. In fact, attacks through contractors, also known as trusted relationship attacks, remain one of the top three methods used to breach corporate networks. With SMBs generally being less protected than large enterprises, this makes them especially attractive to both opportunistic cybercriminals and sophisticated threat actors.
At the same time, AI-driven attacks are becoming increasingly common, making phishing and malware campaigns easier to prepare and quickly adapt, thus increasing their scale. Meanwhile, cybersecurity regulations are tightening, adding more compliance pressure on SMBs.
Improving your security posture has never been more critical. Kaspersky highlights key attack vectors every SMB should be aware of to stay protected.
How malware and potentially unwanted applications (PUAs) are disguised as popular services
Kaspersky analysts have used data from the Kaspersky Security Network (KSN) to explore how frequently malicious and unwanted files and programs are disguised as legitimate applications commonly used by SMBs. The KSN is a system for processing anonymized cyberthreat-related data shared voluntarily by opted-in Kaspersky users. For this research, only data received from the users of Kaspersky solutions for SMBs were analyzed. The research focused on the following applications:
- ChatGPT
- Cisco AnyConnect
- Google Drive
- Google Meet
- DeepSeek
- Microsoft Excel
- Microsoft Outlook
- Microsoft PowerPoint
- Microsoft Teams
- Microsoft Word
- Salesforce
- Zoom
Between January and April 2025 alone, nearly 8,500 SMB users encountered cyberattacks in which malware or PUAs were disguised as these popular tools.
Among the detected threats, the highest number (1652) of unique malicious and potentially unwanted files mimicked Zoom, the widely used video conferencing platform. This accounted for nearly 41% of all unique files detected, a 14-percentage point increase compared to 2024. Microsoft Office applications remained frequent targets for impersonation: Outlook and PowerPoint each accounted for 16%, Excel for nearly 12%, while Word and Teams made up 9% and 5%, respectively.
Share of unique files with names mimicking the nine most popular legitimate applications in 2024 and 2025 (download)
A comparison of the threat landscape in 2024 and 2025 reveals a clear shift: with the growing popularity of AI services, cyberattackers are increasingly disguising malware as various AI tools. According to our analysis, the number of unique malicious files mimicking ChatGPT grew by 115%, reaching 177 in the first four months of 2025. This contributed to a three-percentage-point increase in the tool’s share among the most mimicked applications. DeepSeek, a large language model launched only in 2025, has immediately appeared on the list of impersonated tools.
Another cybercriminal tactic to watch for in 2025 is the growing use of collaboration platform brands to trick users into downloading or launching malware and PUAs. As mentioned above, the share of threats disguised as Zoom increased by 14 percentage points, reaching 1652 unique files, while Microsoft Teams and Google Drive saw increases of over three and one percentage points, respectively, with 206 and 132 cases. This pattern likely reflects the normalization of remote work and geographically distributed teams, which has made these platforms integral to business operations across industries.
Attackers are clearly leveraging the popularity and credibility of these services to increase the success rate of their campaigns.
| Malicious file names mimicking popular services | 2024 | 2025 | 2025 vs 2024 |
| Zoom | 26.24% | 40.86% | 14.62 p.p. |
| Microsoft Teams | 1.84% | 5.10% | 3.25 p.p. |
| ChatGPT | 1.47% | 4.38% | 2.9 p.p. |
| DeepSeek | 0 | 2.05% | – |
| Google Drive | 2.11% | 3.26% | 1.15 p.p. |
The total number of unique malicious and unwanted files imitating legitimate applications slightly declined year-over-year, from 5,587 in 2024 to 4,043 in 2025.
Main types of threats affecting the SMB Sector, 2025 (download)
The top threats targeting SMBs in 2025 included downloaders, Trojans, and adware.
Leading the list are downloaders, potentially unwanted applications designed to install additional content from the internet, often without clearly informing the user of what’s being downloaded. While not inherently malicious, these tools are frequently exploited by attackers to deliver harmful payloads to victims’ devices.
Trojans ranked next. These are malicious programs that carry out unauthorized actions such as deleting, blocking, modifying, or copying data, or disrupting the normal operation of computers and networks. Trojans are among the most prevalent forms of malware, and cyberattackers continue to use them in a wide range of malicious campaigns.
Adware also made the top three list. These programs are designed to display advertisements on infected computers or substitute a promotional website for the default search engine in a browser. Adware often comes bundled with freeware or shareware, effectively serving as the price for using the free software. In some cases, Trojans silently download and install adware onto the victim’s machine.
Among other common types of threats were DangerousObject, Trojan-Dropper, Backdoor, Trojan-Downloader, HackTool, Trojan-PSW, and PSW-Tool. For instance, we recently identified a campaign involving a Trojan-Downloader called “TookPS“, which was distributed through fake websites imitating legitimate remote access and 3D modeling software.
How scammers and phishers trick victims into giving up accounts and money
We continue to observe a wide range of phishing campaigns and scams targeting SMBs. Attackers aim to steal login credentials for various services, from delivery platforms to banking systems, or manipulate victims into sending them money.
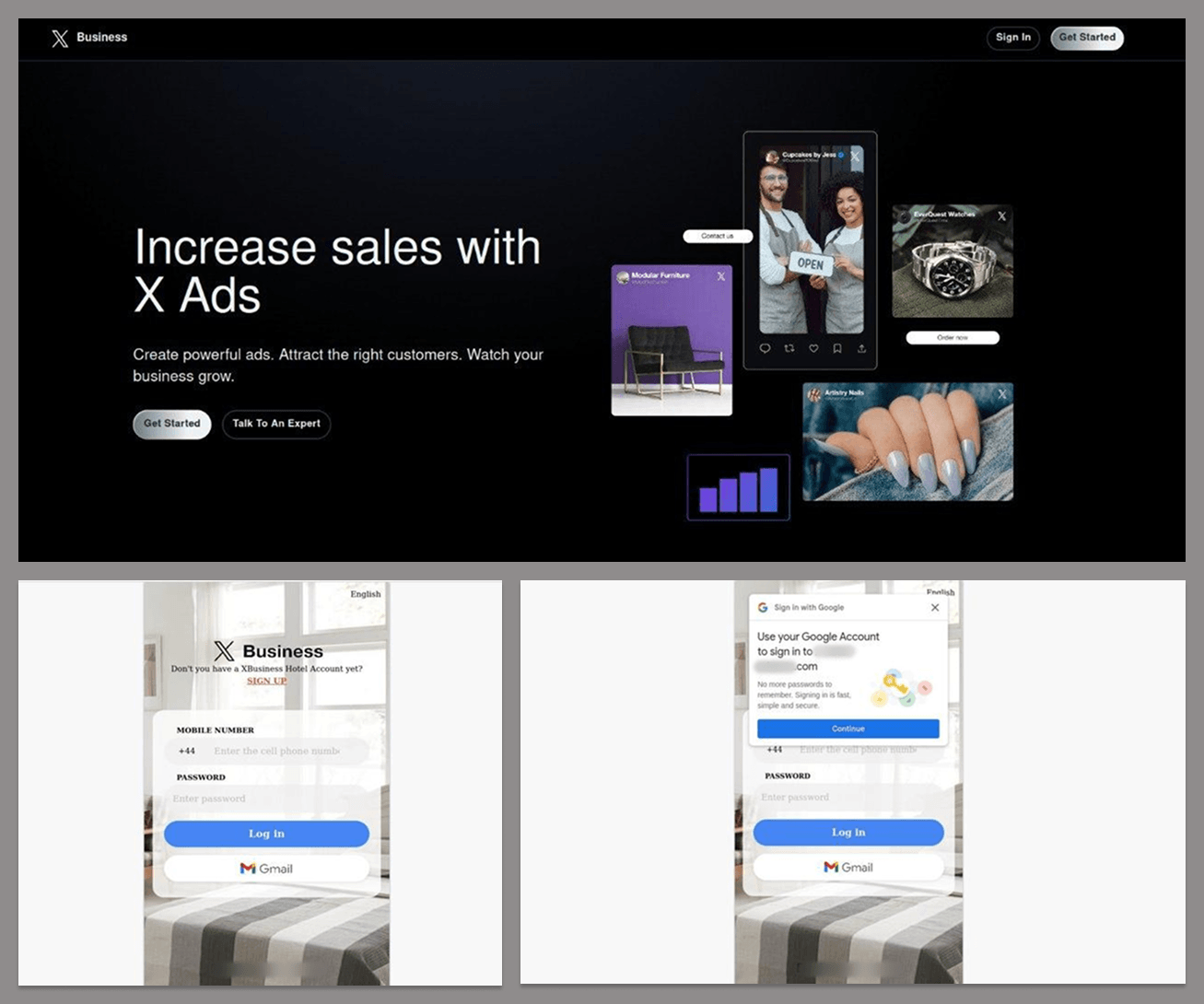
To do this, cyberattackers use a variety of lures, often imitating landing pages from brands commonly used by SMBs. One example is a phishing attempt targeting Google business accounts. The bait lures victims with the promise of promoting their company on X. It requires them to first log in to a dedicated platform using their Google account with credentials that will end up in cyberattackers’ hands.
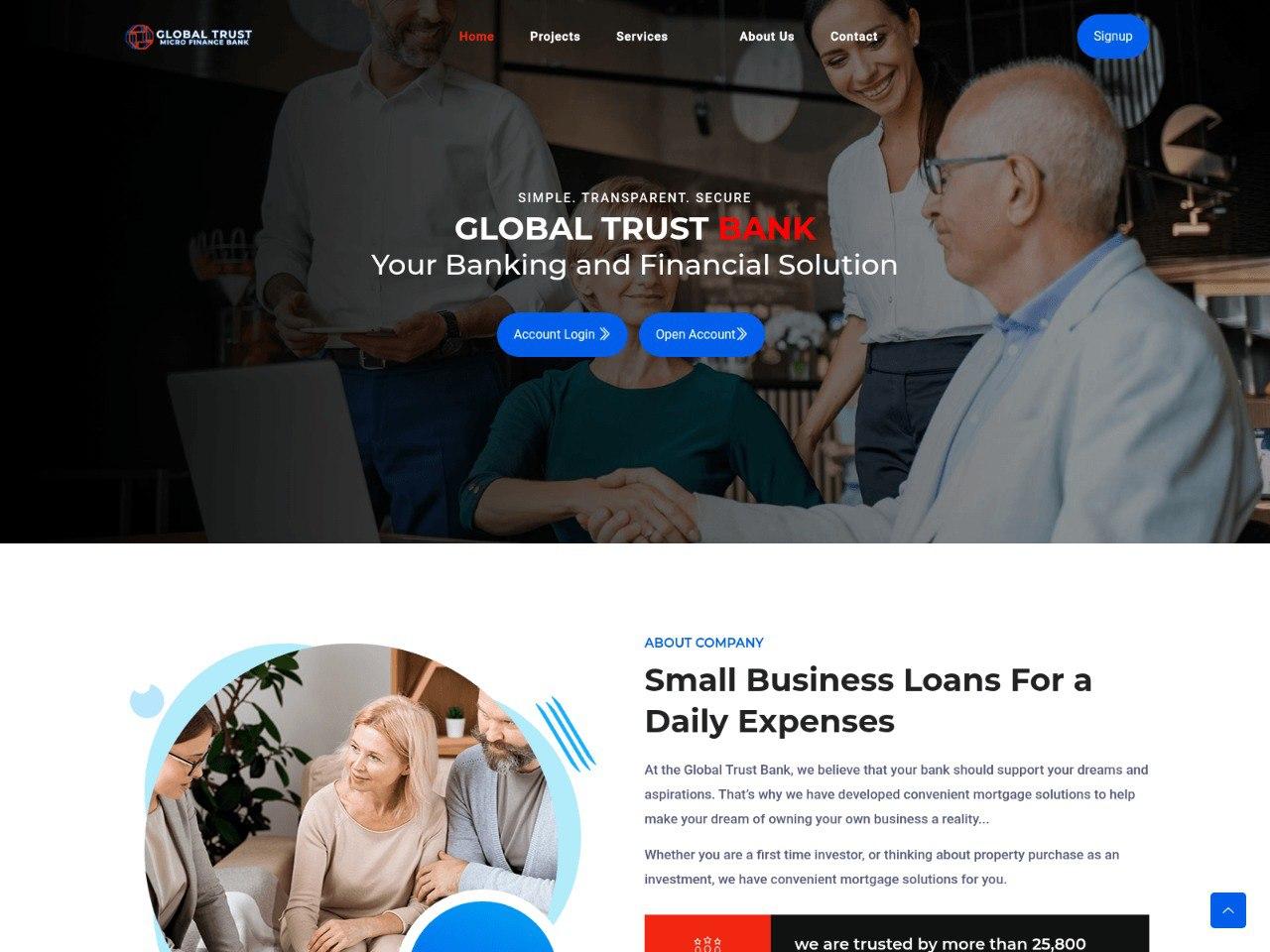
Another fake landing page impersonated a bank that offered business loans: a “Global Trust Bank”. Since legitimate organizations with that name exist in multiple countries, this phishing attempt may have seemed believable. The attackers tried to lure users with favorable business loan terms – but only after victims submitted their online banking credentials, giving the criminals access to their accounts.
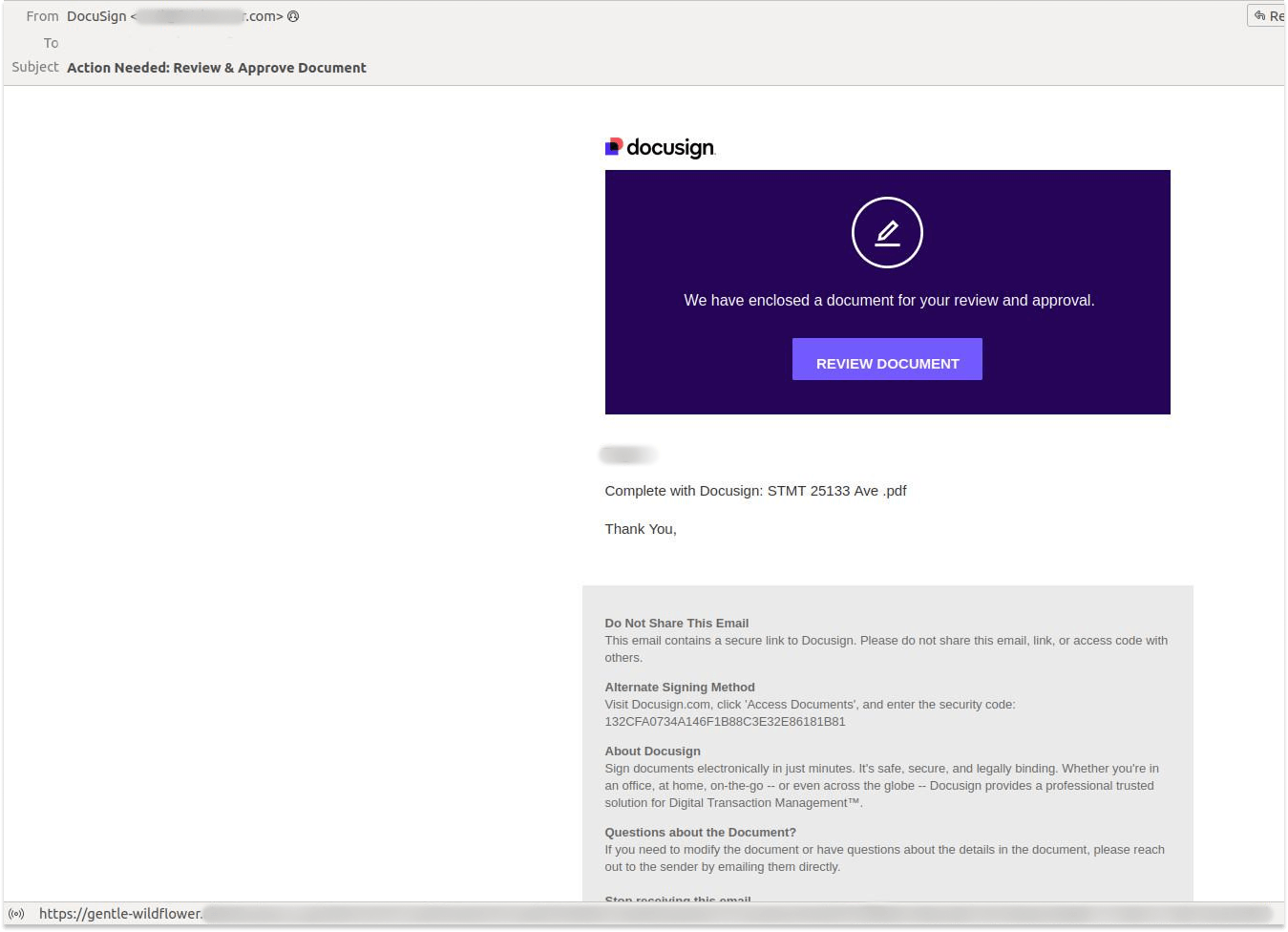
We also saw a range of phishing emails targeting SMBs. In one recent case detected by our systems, the attacker sent a fake notification allegedly from DocuSign, an electronic document-signing service.
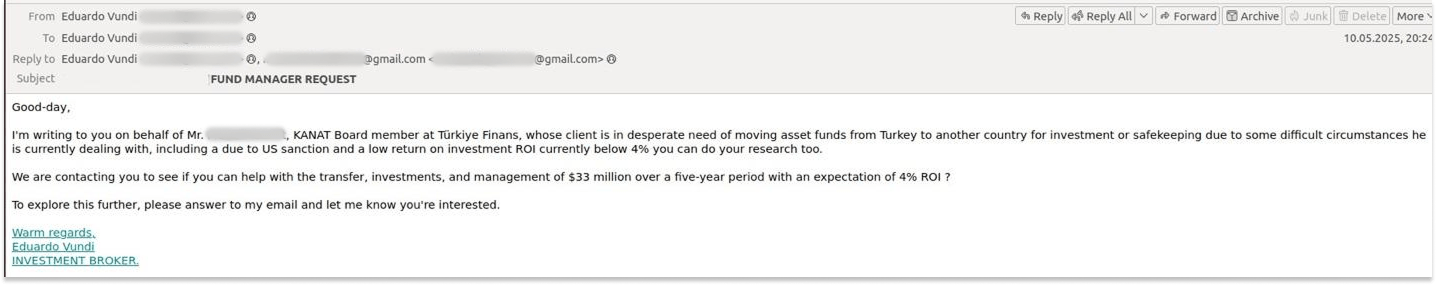
SMBs can even find themselves targeted by classic Nigerian scams. In one recent example, the sender claimed to represent a wealthy client from Turkey who wanted to move $33 million abroad to allegedly avoid sanctions, and invited the recipient to handle the funds. In Nigerian scams, fraudsters typically cajole money. They may later request a relatively small payment to a manager or lawyer compared to the amount originally promised.
Beyond these threats, SMBs are bombarded daily with hundreds of spam emails. Some promise attractive deals on email marketing or loans; others offer services like reputation management, content creation, or lead generation. In general, these offers are crafted to reflect the typical needs of small businesses. Not surprisingly, AI has also made its way into the spam folder – with offers to automate various business processes.
We have also seen spammers offering dubious deals like purchasing a database of over 400,000 businesses for $100, supposedly to be used for selling the company’s B2B products, or manipulating reviews on a review platform.
Security tips
SMBs can reduce risks and ensure business continuity by investing in comprehensive cybersecurity solutions and increasing employee awareness. It is essential to implement robust measures such as spam filters, email authentication protocols, and strict verification procedures for financial transactions and the handling of sensitive information.
Another key step toward cyber resilience is promoting awareness about the importance of comprehensive security procedures and ensuring they are regularly updated. Regular security training sessions, strong password practices, and multi-factor authentication can significantly reduce the risk of phishing and fraud.
It is also worth noting that searching for software through search engines is an insecure practice, and should be prohibited in the organization. If you need to implement new tools or replace existing ones, make sure they are downloaded from official sources and installed on a centralized basis by your IT team.
Cybersecurity Action Plan for SMBs
- Define access rules for corporate resources such as email accounts, shared folders, and online documents. Monitor and limit the number of individuals with access to critical company data. Keep access lists up to date and revoke access promptly when employees leave the company. Use cloud access security brokers to monitor and control employee activities within cloud services and enforce security policies.
- Regularly back up important data to ensure the preservation of corporate information in case of emergencies or cyberincidents.
- Establish clear guidelines for using external services and resources. Create well-defined procedures for coordinating specific tasks, such as implementing new software, with the IT department and other responsible managers. Develop short, easy-to-understand cybersecurity guidelines for employees, with a special focus on account and password management, email protection, and safe web browsing. A well-rounded training program will equip employees with the knowledge they need and the ability to apply it in practice.
- Implement specialized cybersecurity solutions that provide visibility and control over cloud services, such as Kaspersky Next.





















AI and collaboration tools: how cyberattackers are targeting SMBs in 2025